Cryptographic Keys 101: What They Are & How They Secure Data - Hashed Out by The SSL Store™
Por um escritor misterioso
Last updated 11 abril 2025

Cryptographic keys, in combination with an encryption algorithm, disguise data (encryption) so only a special key can access it (decryption).

Best Password Manager Security & Data Protection

Network 101 Cheat Sheet, PDF, Denial Of Service Attack

Cryptography/SSL 101 #2: Cryptographic hash functions

The SSL Store: ACME Protocol: What it is and how it works 05/31
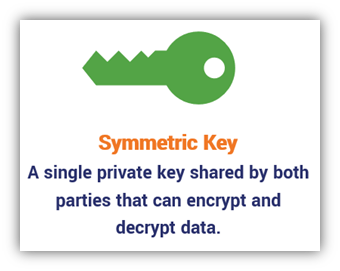
Cryptographic Keys 101: What They Are & How They Secure Data

What Is a Hash Function in Cryptography? A Beginner's Guide

The SSL Store: Taking a Closer Look at the SSL/TLS Handshake 04/30

An Overview of Cryptography
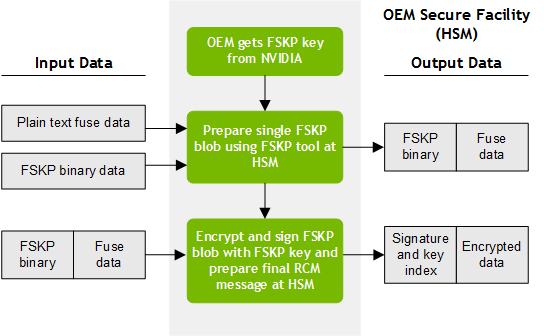
Factory Secure Key Provisioning
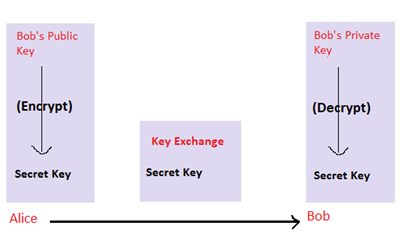
Cryptography 101 with SSL

20 Generative AI, ChatGPT & Deepfake Statistics You Should Know
Recomendado para você
-
 10 Uses for Keys - This Old House11 abril 2025
10 Uses for Keys - This Old House11 abril 2025 -
 Key Photos, Images and Pictures11 abril 2025
Key Photos, Images and Pictures11 abril 2025 -
 Rad Replacement Keys11 abril 2025
Rad Replacement Keys11 abril 2025 -
 Wicked Keys11 abril 2025
Wicked Keys11 abril 2025 -
 Types of keys - All Locks11 abril 2025
Types of keys - All Locks11 abril 2025 -
 Key Cutting Key Copy Checker - FobToronto11 abril 2025
Key Cutting Key Copy Checker - FobToronto11 abril 2025 -
 Global Link Replacement Keys11 abril 2025
Global Link Replacement Keys11 abril 2025 -
 Car key - Wikipedia11 abril 2025
Car key - Wikipedia11 abril 2025 -
 Keys-on-Tap Key Management System For Automotive Dealers – Harcor Security Seals11 abril 2025
Keys-on-Tap Key Management System For Automotive Dealers – Harcor Security Seals11 abril 2025 -
 All About Do Not Duplicate Keys - Door Locks Direct11 abril 2025
All About Do Not Duplicate Keys - Door Locks Direct11 abril 2025
você pode gostar
-
 Jogo Vamos Desenhar - Figuras Vazadas - Babebi - Outros Jogos - Magazine Luiza11 abril 2025
Jogo Vamos Desenhar - Figuras Vazadas - Babebi - Outros Jogos - Magazine Luiza11 abril 2025 -
HELLSING ULTIMATE: VOLUMES 9 & 10 (BLU-RAY/DVD COMBO) - GTIN/EAN/UPC 704400091049 - Cadastro de Produto com Tributação e NCM - Cosmos11 abril 2025
-
 Zombs io — Play for free at11 abril 2025
Zombs io — Play for free at11 abril 2025 -
 New Video: Big Sean x Migos “Sacrifices” - Rap Radar11 abril 2025
New Video: Big Sean x Migos “Sacrifices” - Rap Radar11 abril 2025 -
 Barcode Scanning Basics: Keep Your MARK System Clean11 abril 2025
Barcode Scanning Basics: Keep Your MARK System Clean11 abril 2025 -
feck Fandom11 abril 2025
-
 The Unofficial Grancrest Senki OST Download – Anime Vestige11 abril 2025
The Unofficial Grancrest Senki OST Download – Anime Vestige11 abril 2025 -
 sudoku solver11 abril 2025
sudoku solver11 abril 2025 -
 Chess Piece Gijinkas from FPS Chess (White Piece Version) : r11 abril 2025
Chess Piece Gijinkas from FPS Chess (White Piece Version) : r11 abril 2025 -
 FREE TAB) Hikaru Nara - Goose House, Fingerstyle Guitar11 abril 2025
FREE TAB) Hikaru Nara - Goose House, Fingerstyle Guitar11 abril 2025