Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Last updated 26 abril 2025

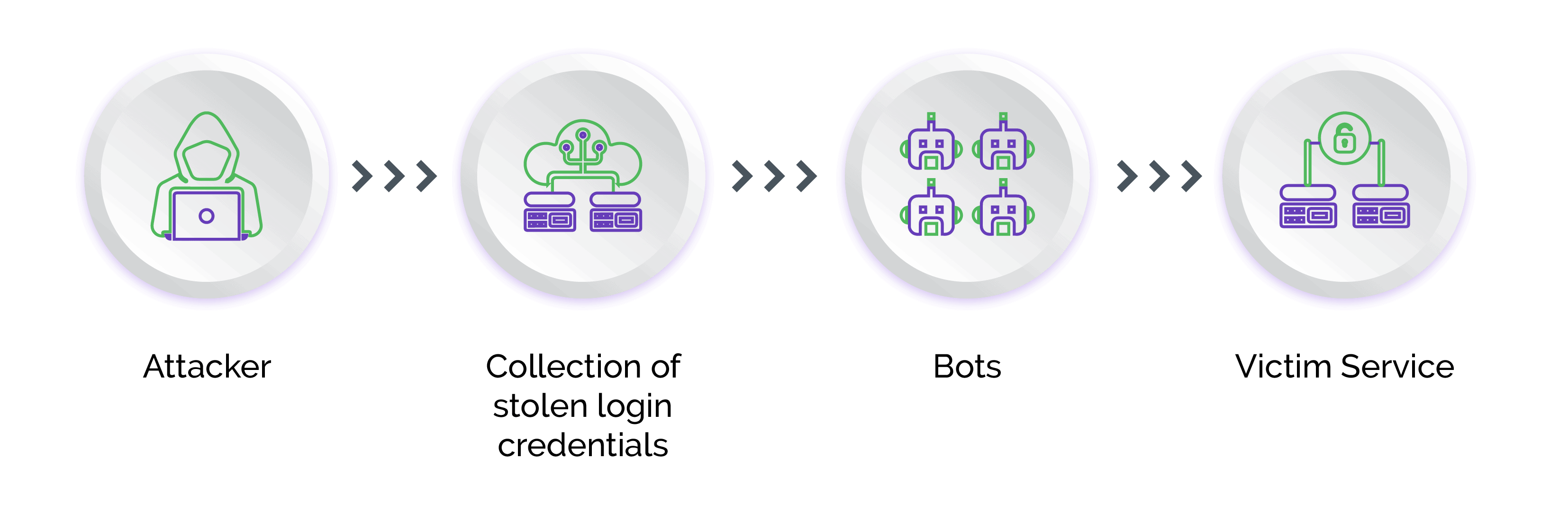
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..
Email Compromise with Credential Stuffing Attack Tools
What Is Credential Stuffing?
The State of Credential Stuffing and the Future of Account Takeovers.
How Residential Proxies and CAPTCHA-Solving Services Become Agents of Abuse - Security News - Trend Micro IE
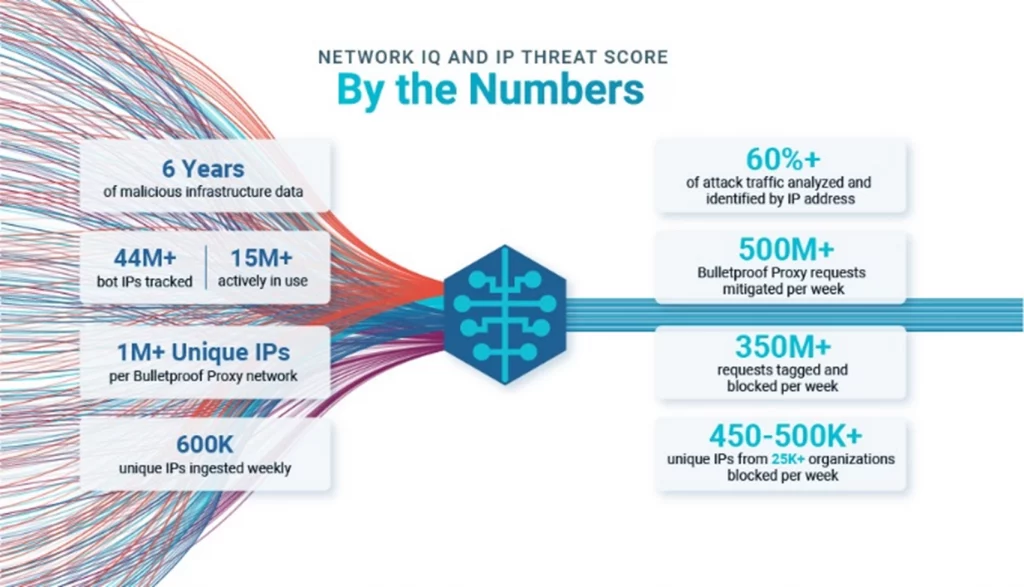
FBI Warning on Credential Stuffing & Residential Proxies is Good News – Bad News - Security Boulevard
Cracking Tools that Automate Credential Stuffing & ATO
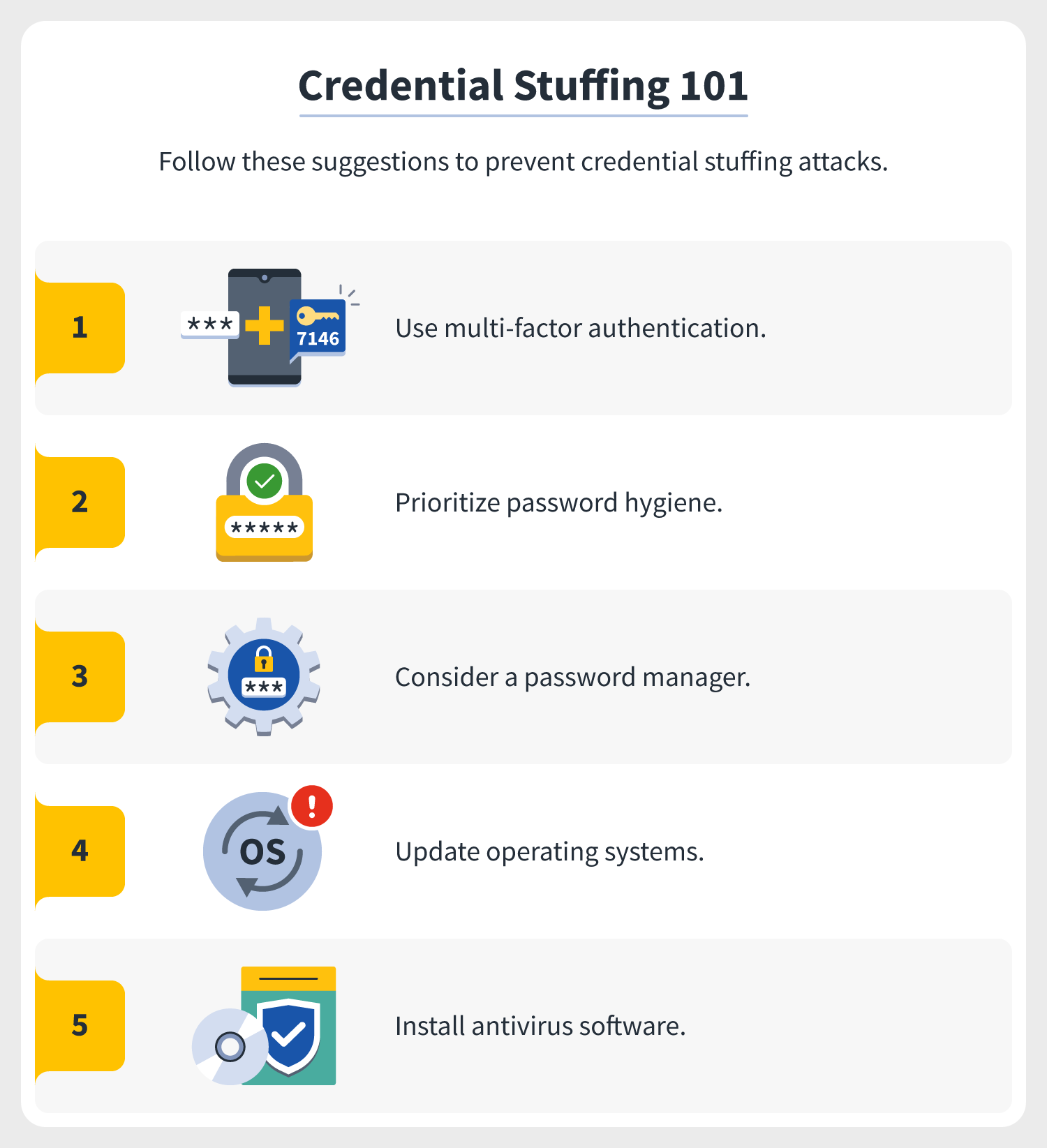
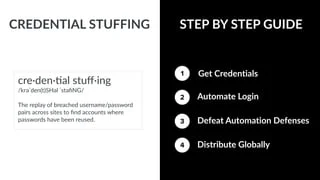
Credential stuffing simplified + attack protection tips

Email Compromise with Credential Stuffing Attack Tools

Skiplagging, CAPTCHA vs Bots, Scraper Bots
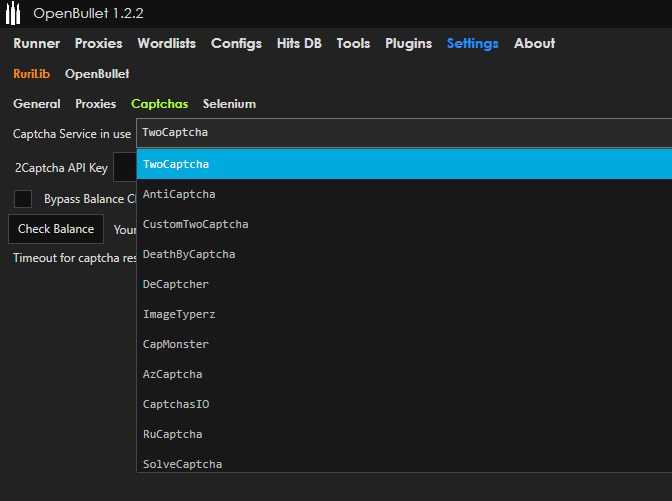
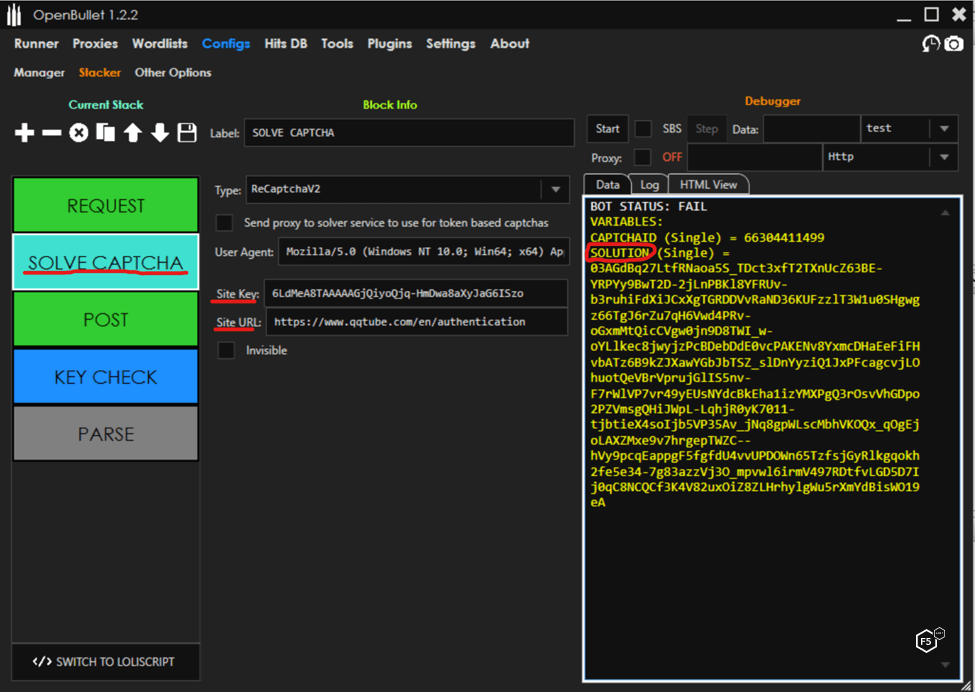
How Cybercriminals Abuse OpenBullet for Credential Stuffing

ReCAPTCHA Alternative: How to Stop Bad Bots For Good
Recomendado para você
-
ipgrabber · GitHub Topics · GitHub26 abril 2025
-
 How to Find Someone's IP Address on PS426 abril 2025
How to Find Someone's IP Address on PS426 abril 2025 -
ip-finder · GitHub Topics · GitHub26 abril 2025
-
How to trace IP in Kali Linux using IP-Tracer Tool - GeeksforGeeks26 abril 2025
-
 IP Address Tracker - IP Tracker (Free Trial)26 abril 2025
IP Address Tracker - IP Tracker (Free Trial)26 abril 2025 -
Find the IP Address of my Website, Server and Domain26 abril 2025
-
 Track That IP-Server Locator on the App Store26 abril 2025
Track That IP-Server Locator on the App Store26 abril 2025 -
 How to Find the IP Address of a Skype User (with Pictures)26 abril 2025
How to Find the IP Address of a Skype User (with Pictures)26 abril 2025 -
Someone sent me a link that had an IP grabber on it, I wanted to26 abril 2025
-
![Xbox IP Finder How to Pull IPs on Xbox? [2023 Update] - MiniTool](https://www.partitionwizard.com/images/uploads/2022/08/xbox-ip-finder-thumbnail.jpg) Xbox IP Finder How to Pull IPs on Xbox? [2023 Update] - MiniTool26 abril 2025
Xbox IP Finder How to Pull IPs on Xbox? [2023 Update] - MiniTool26 abril 2025
você pode gostar
-
Produtos em promoção na Montink26 abril 2025
-
 $45 Nintendo eShop Gift Card [Digital Code26 abril 2025
$45 Nintendo eShop Gift Card [Digital Code26 abril 2025 -
 VOCÊ PRECISA CONHECER ESSE JOGO DE BARALHO - ZETEMA26 abril 2025
VOCÊ PRECISA CONHECER ESSE JOGO DE BARALHO - ZETEMA26 abril 2025 -
 Undertale Pixel Art, Sprite, Sans, Digital Art, Cartoon png26 abril 2025
Undertale Pixel Art, Sprite, Sans, Digital Art, Cartoon png26 abril 2025 -
 June 2023 Calendar Desktop Wallpaper Background26 abril 2025
June 2023 Calendar Desktop Wallpaper Background26 abril 2025 -
Jojo's Bizarre Adventure Shitposting26 abril 2025
-
Vamos Jogar RPG ? Diálogos com a literatura, o leitor e a autoria - Google Books26 abril 2025
-
 Anime drawing Drawing by Sanchit Sharda - Fine Art America26 abril 2025
Anime drawing Drawing by Sanchit Sharda - Fine Art America26 abril 2025 -
Download Candy Crush Saga for android 9.026 abril 2025
-
 Free AI Blood Donation Poster Maker: Create AI-generated Blood Donation Poster Images, Videos & Animations26 abril 2025
Free AI Blood Donation Poster Maker: Create AI-generated Blood Donation Poster Images, Videos & Animations26 abril 2025