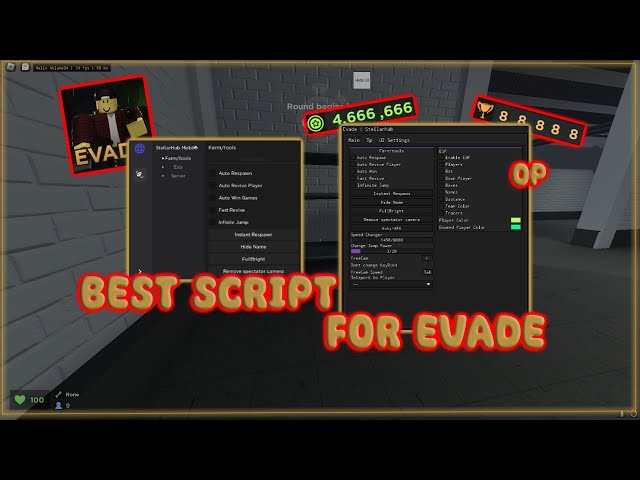
NEW BEST Evade SCRIPTS Mobile And Pc, ALL FEATURES
Por um escritor misterioso
Last updated 09 abril 2025

RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA
Main :: Causality Story Sequencer :: Hollywood Camera Work

Pen Test Certification Certified Penetration Testing (CPENT) Training

Best MSP Software 2023 - Definition, Features, Security - Acronis

COVID-19 increased censorship circumvention and access to sensitive topics in China

Evasive Jupyter Infostealer Campaign Showcases Dangerous Variant

Kronos Malware Reemerges with Increased Functionality
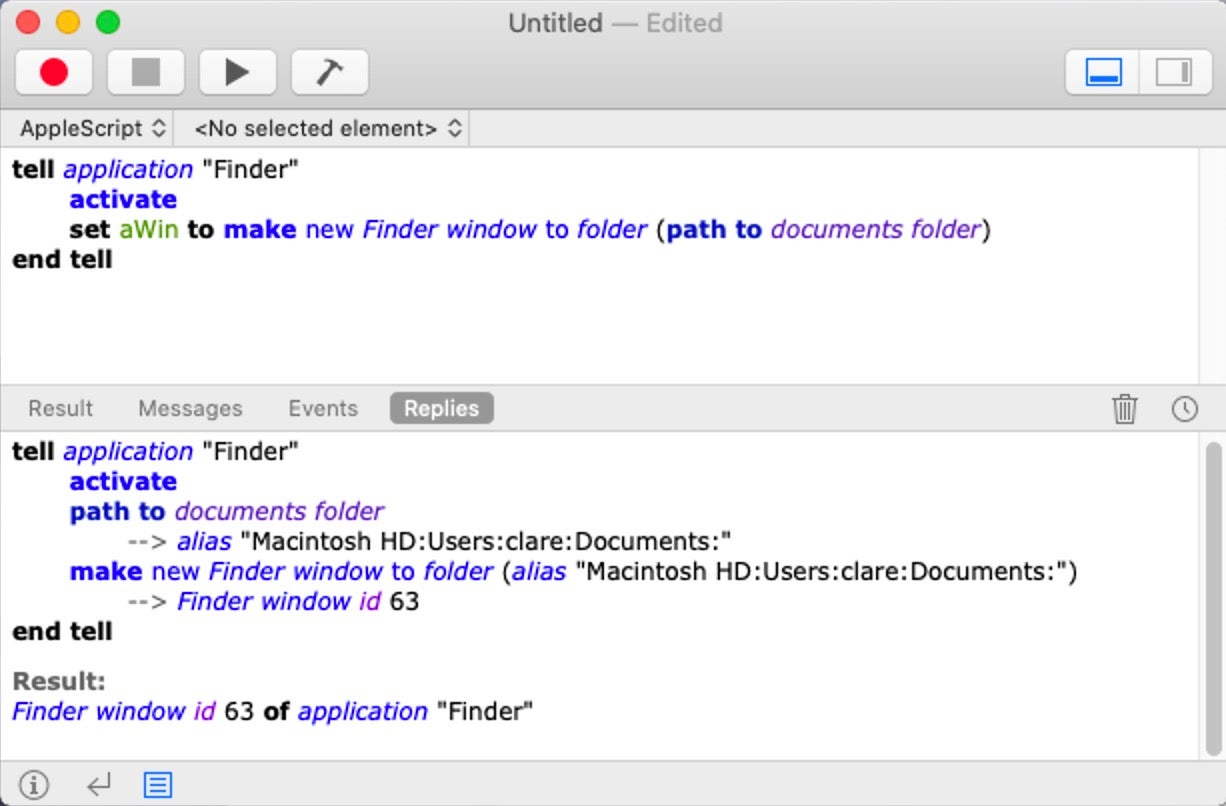
How AppleScript Is Used For Attacking macOS

Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them

BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis and Detection - SentinelOne

Flash Vulnerabilities & Exploits: An Information Security Primer

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability
Recomendado para você
-
Apollo Evade Mens Mountain Bike - S, M, L, XL Frames09 abril 2025
-
I love evade.#fyp#viral#evade#mobilegameplay #iloveevade, a+w+d evade09 abril 2025
-
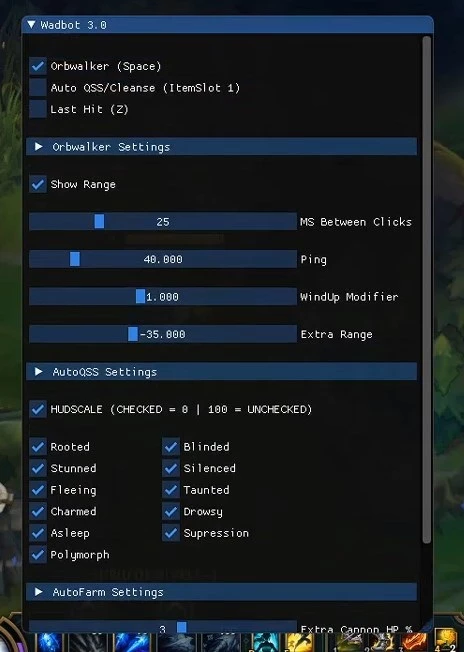 Script Legit Auto Farm, Evade, Combo - League Of Legends Lol - DFG09 abril 2025
Script Legit Auto Farm, Evade, Combo - League Of Legends Lol - DFG09 abril 2025 -
 The FDA Doesn't Care About Health Apps, So the Courts Stepped Up09 abril 2025
The FDA Doesn't Care About Health Apps, So the Courts Stepped Up09 abril 2025 -
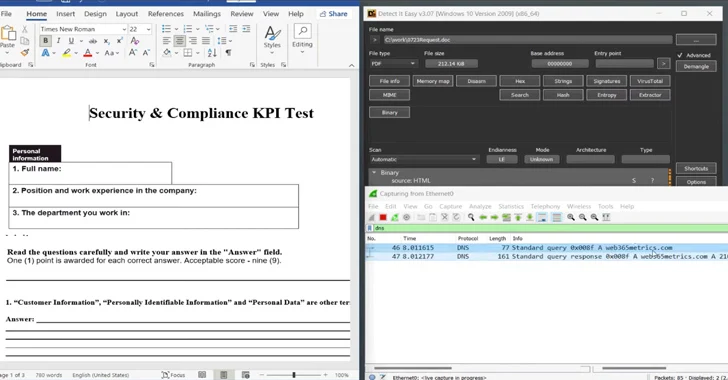 Beware of MalDoc in PDF: A New Polyglot Attack Allowing Attackers to Evade Antivirus09 abril 2025
Beware of MalDoc in PDF: A New Polyglot Attack Allowing Attackers to Evade Antivirus09 abril 2025 -
Evade GodMode, Speed, Fly, Gift Farm & more09 abril 2025
-
 how to be a mob in evade|TikTok Search09 abril 2025
how to be a mob in evade|TikTok Search09 abril 2025 -
New Cactus ransomware encrypts itself to evade antivirus09 abril 2025
-
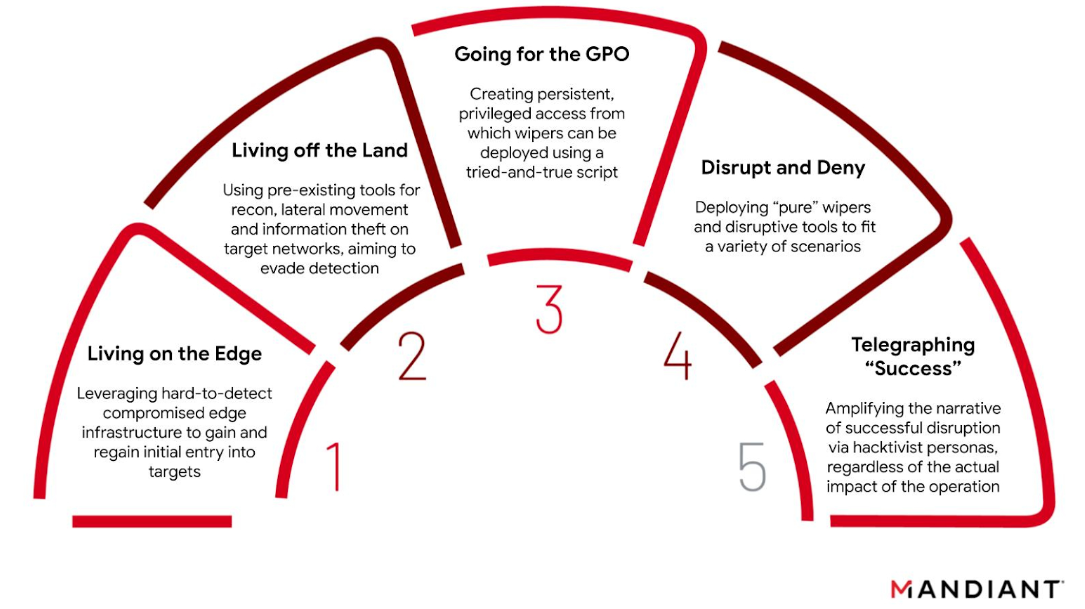 The GRU's Disruptive Playbook09 abril 2025
The GRU's Disruptive Playbook09 abril 2025 -
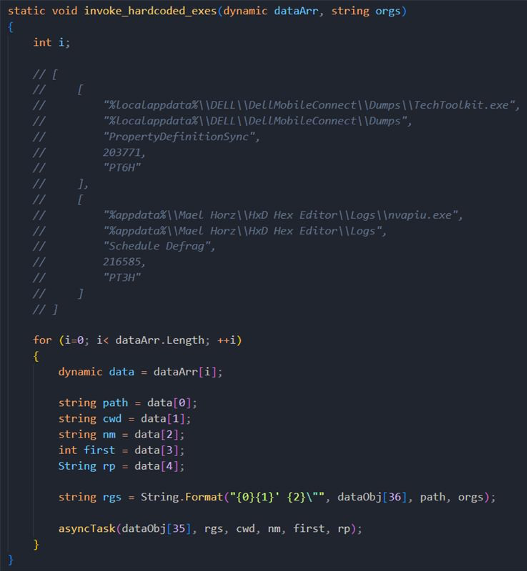 Buy, Sell, Steal, EvilNum Targets Cryptocurrency, Forex, Commodities09 abril 2025
Buy, Sell, Steal, EvilNum Targets Cryptocurrency, Forex, Commodities09 abril 2025
você pode gostar
-
 Ultimate Minecraft Mining Guide (1.20) Todos os minérios do jogo. - MMORPGPLAY09 abril 2025
Ultimate Minecraft Mining Guide (1.20) Todos os minérios do jogo. - MMORPGPLAY09 abril 2025 -
 Camiseta The Last of Us 2 Ellie Violão Costa09 abril 2025
Camiseta The Last of Us 2 Ellie Violão Costa09 abril 2025 -
 Churro – It's Spanish for Donut – Eatsward Bound09 abril 2025
Churro – It's Spanish for Donut – Eatsward Bound09 abril 2025 -
 Call of Duty Advanced Warfare is getting a 2025 sequel, leaker claims09 abril 2025
Call of Duty Advanced Warfare is getting a 2025 sequel, leaker claims09 abril 2025 -
 The World of Chess Boxing - Sidekick Boxing09 abril 2025
The World of Chess Boxing - Sidekick Boxing09 abril 2025 -
Triste Realidade09 abril 2025
-
South Park - TV Series09 abril 2025
-
 Why You Should Avoid Pawning Jewelry09 abril 2025
Why You Should Avoid Pawning Jewelry09 abril 2025 -
 ajiro shinpei and minakata ryuunosuke (summertime render) drawn by09 abril 2025
ajiro shinpei and minakata ryuunosuke (summertime render) drawn by09 abril 2025 -
 Brinquedo Educativo Jogo Do Inglês Em Madeira - Colorido - Maninho Artesanatos - 3391.109 abril 2025
Brinquedo Educativo Jogo Do Inglês Em Madeira - Colorido - Maninho Artesanatos - 3391.109 abril 2025





