Course, Breach and Attack Simulation Basics
Por um escritor misterioso
Last updated 06 abril 2025


Top 20 Breach and Attack Simulation (BAS) Vendors for 2022

Intro to Breach and Attack Simulation

Breach and Attack Simulation: Hack Yourself to a More Secure Future

What you need to know about Breach and Attack Simulation - Part 1 - Cyber Startup Observatory

Breach and Attack Simulation (BAS) Technologies, by George Fekkas

What is Breach and Attack Simulation, and How Does It Expose Your Cybersecurity Vulnerabilities?

Course, Breach and Attack Simulation Basics

Attack Simulation vs Attack Emulation: What's the Difference?
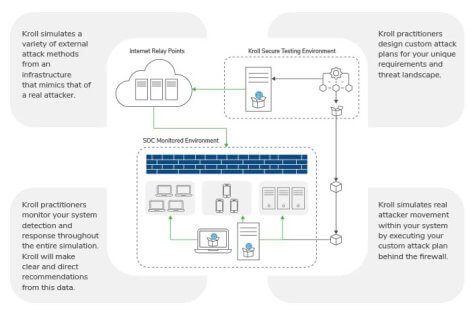
Breach and Attack Simulation (BAS), Data Breach Simulation
Recomendado para você
-
 Hacker Simulator: Free Trial on Steam06 abril 2025
Hacker Simulator: Free Trial on Steam06 abril 2025 -
 Code Typer - Hacking Simulator - APK Download for Android06 abril 2025
Code Typer - Hacking Simulator - APK Download for Android06 abril 2025 -
Hacker Teclado Pro - Prank App – Apps no Google Play06 abril 2025
-
 The Complete List of Hacker And Cybersecurity Movies06 abril 2025
The Complete List of Hacker And Cybersecurity Movies06 abril 2025 -
 SMS Attacks and Mobile Malware Threats06 abril 2025
SMS Attacks and Mobile Malware Threats06 abril 2025 -
Hacker Typer - Iceland, Professional Profile06 abril 2025
-
GEEK TYPER HACKING SIMULATOR, Hacking Prank, എല്ലാവർക്കും HACKER ആവാം, mobile app, GEEK TYPER HACKING SIMULATOR, Hacking Prank, എല്ലാവർക്കും HACKER ആവാം APP LINK :, By JATTIN JOSE06 abril 2025
-
 Wifi Password Hacker - Prank for Android - Download06 abril 2025
Wifi Password Hacker - Prank for Android - Download06 abril 2025 -
 how to use the Hacker Typer at Geek Prank. This Geek Typer is meant to simulate that you're hacking into a top secret g…06 abril 2025
how to use the Hacker Typer at Geek Prank. This Geek Typer is meant to simulate that you're hacking into a top secret g…06 abril 2025 -
 H.A.C.K. - A hacking simulation game where information is power06 abril 2025
H.A.C.K. - A hacking simulation game where information is power06 abril 2025
você pode gostar
-
 Kit 4 Beyblade Metal + 2 Lançador + Arena Batalha06 abril 2025
Kit 4 Beyblade Metal + 2 Lançador + Arena Batalha06 abril 2025 -
 Kenja no Mago Anime Gets New Trailer - Anime Herald06 abril 2025
Kenja no Mago Anime Gets New Trailer - Anime Herald06 abril 2025 -
 God of War Chains of Olympus, Detonado 100% Platina06 abril 2025
God of War Chains of Olympus, Detonado 100% Platina06 abril 2025 -
 Clemons' buzzer-beater lifts Camels in OT - Campbell University06 abril 2025
Clemons' buzzer-beater lifts Camels in OT - Campbell University06 abril 2025 -
 OreShura Fung's Personal Blog06 abril 2025
OreShura Fung's Personal Blog06 abril 2025 -
 Locações06 abril 2025
Locações06 abril 2025 -
 Significado de Elohim ⋆06 abril 2025
Significado de Elohim ⋆06 abril 2025 -
 Palpite Al-Ahly x Al-Ittihad - Mundial de Clubes - 15/1206 abril 2025
Palpite Al-Ahly x Al-Ittihad - Mundial de Clubes - 15/1206 abril 2025 -
 Mavin Mega M Gengar EX XY166 Shiny Black Star Promo Ultra Rare + Gengar EX 34/119 Holo06 abril 2025
Mavin Mega M Gengar EX XY166 Shiny Black Star Promo Ultra Rare + Gengar EX 34/119 Holo06 abril 2025 -
 11 Telegram Games To Play With Your Friends And Family In Singapore06 abril 2025
11 Telegram Games To Play With Your Friends And Family In Singapore06 abril 2025

