Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Por um escritor misterioso
Last updated 12 abril 2025

The Splunk Threat Research Team provides a deep dive analysis of the RedLine Stealer threat and shares valuable insights to help enable blue teamers to defend against and detect this malware variant.
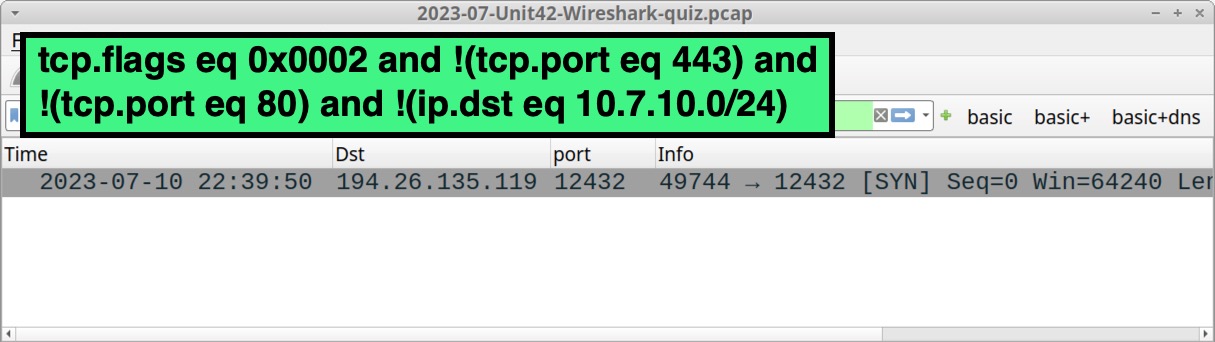
RedLine Stealer: Answers to Unit 42 Wireshark Quiz
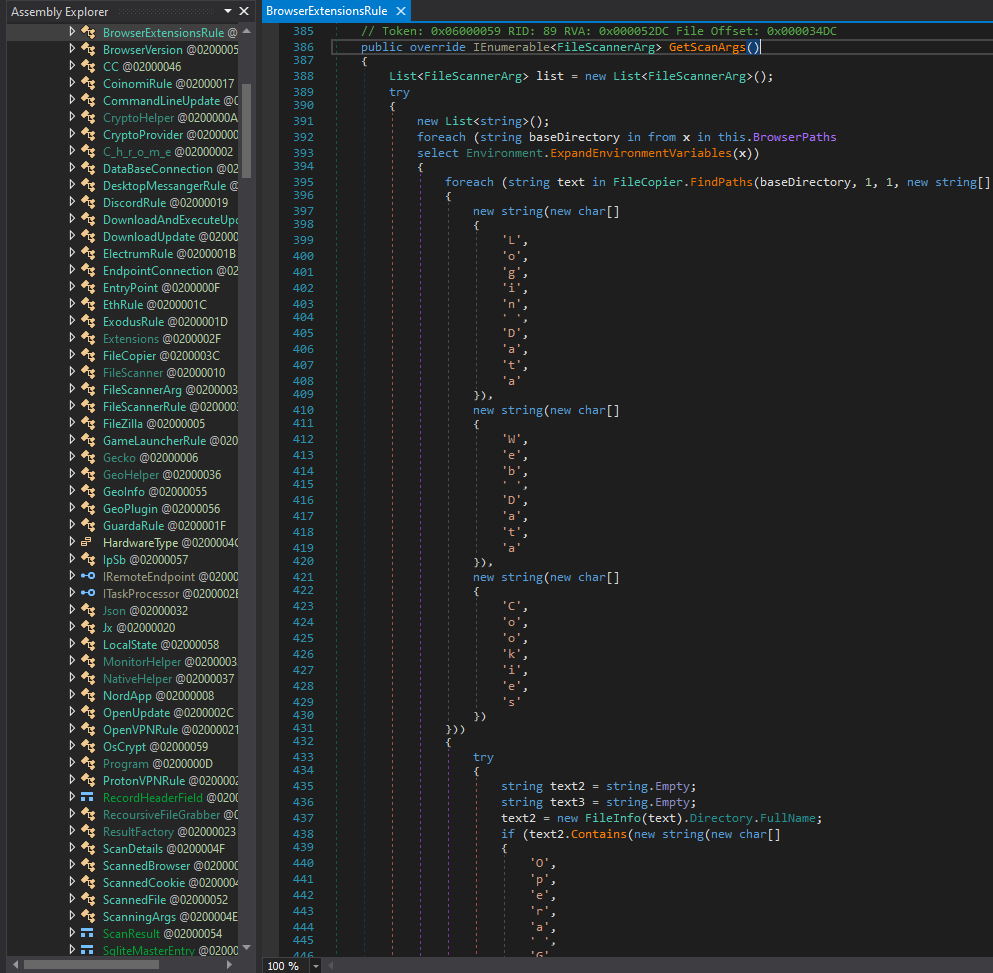
Redline Stealer Malware Static Analysis, by Aaron Stratton
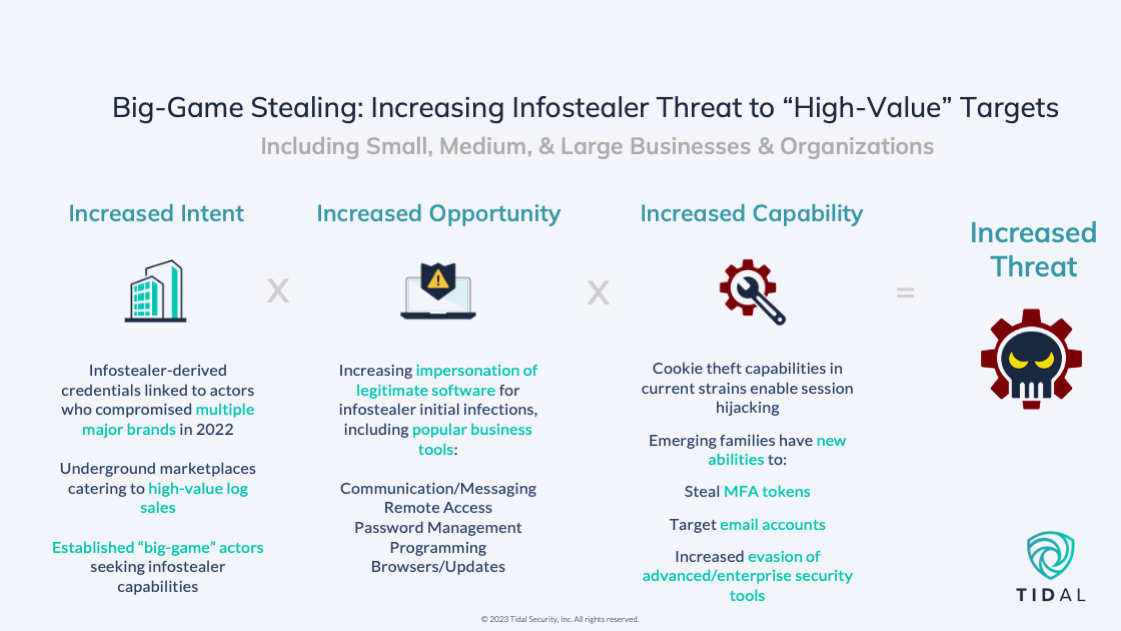
Big-Game Stealing (Part 1): The Infostealer Landscape & Rising Infostealer Threats to Businesses

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Cyble — A Deep-dive Analysis of RedLine Stealer Malware

Malicious AI Tool Ads Used to Deliver Redline Stealer

eSentire eSentire Threat Intelligence Malware Analysis: Redline…

SpyCloud

Security Researchers Disrupt RedLine Stealer Operations!

eSentire eSentire Threat Intelligence Malware Analysis: Redline…

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Redline Stealer Targeting Accounts Saved to Web Browser with Automatic Login Feature Included - ASEC BLOG
Recomendado para você
-
 Evade codes for December 202312 abril 2025
Evade codes for December 202312 abril 2025 -
 Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT12 abril 2025
Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT12 abril 2025 -
 Roblox Baby Simulator Codes (November 2023)12 abril 2025
Roblox Baby Simulator Codes (November 2023)12 abril 2025 -
 Evolution Evade Codes - Try Hard Guides12 abril 2025
Evolution Evade Codes - Try Hard Guides12 abril 2025 -
 Roblox Evolution Evade Codes (December 2023) - Pro Game Guides12 abril 2025
Roblox Evolution Evade Codes (December 2023) - Pro Game Guides12 abril 2025 -
 The Nerd Stash on X: Roblox Evade Codes (March 2023) #guide12 abril 2025
The Nerd Stash on X: Roblox Evade Codes (March 2023) #guide12 abril 2025 -
 Dodgy MFA Email Notice Uses QR Codes To Evade Detection12 abril 2025
Dodgy MFA Email Notice Uses QR Codes To Evade Detection12 abril 2025 -
 DragonSpark Attacks Evade Detection with SparkRAT and Golang12 abril 2025
DragonSpark Attacks Evade Detection with SparkRAT and Golang12 abril 2025 -
Swarajya on LinkedIn: “Academic Freedom” To Evade Accountability?12 abril 2025
-
 Roblox Dragon Adventures codes (December 2023): How to get free12 abril 2025
Roblox Dragon Adventures codes (December 2023): How to get free12 abril 2025
você pode gostar
-
 FIFA 19 Modo Survival: Perca um Jogador Sempre que Fizer um Gol12 abril 2025
FIFA 19 Modo Survival: Perca um Jogador Sempre que Fizer um Gol12 abril 2025 -
 When The BALLER Is BALLER - Roblox Meme12 abril 2025
When The BALLER Is BALLER - Roblox Meme12 abril 2025 -
 Danielle Cristina - Fidelidade - Ouvir todas as 14 músicas12 abril 2025
Danielle Cristina - Fidelidade - Ouvir todas as 14 músicas12 abril 2025 -
Claire's Mason City, IA12 abril 2025
-
 go to poki.com 1 Project by Cooing Spring12 abril 2025
go to poki.com 1 Project by Cooing Spring12 abril 2025 -
![metacritic on X: The Callisto Protocol [PS5 - 76] The Callisto Protocol gave me nightmares. It's the best horror game of the year, and a bright new contender in the survival](https://pbs.twimg.com/media/Fi8-bNUUcAAZ_2c.jpg) metacritic on X: The Callisto Protocol [PS5 - 76] The Callisto Protocol gave me nightmares. It's the best horror game of the year, and a bright new contender in the survival12 abril 2025
metacritic on X: The Callisto Protocol [PS5 - 76] The Callisto Protocol gave me nightmares. It's the best horror game of the year, and a bright new contender in the survival12 abril 2025 -
![Top 10 Best Multiplayer Android & iOS Games to play in 2022 [ Appstore]](https://i.ytimg.com/vi/d17K4IRGLjE/maxresdefault.jpg) Top 10 Best Multiplayer Android & iOS Games to play in 2022 [ Appstore]12 abril 2025
Top 10 Best Multiplayer Android & iOS Games to play in 2022 [ Appstore]12 abril 2025 -
 Download Rooms&Exits: Escape Room Games APK v2.16.0 For Android12 abril 2025
Download Rooms&Exits: Escape Room Games APK v2.16.0 For Android12 abril 2025 -
 Minecraft - Como plantar e cultivar Fungo do Nether - Critical Hits12 abril 2025
Minecraft - Como plantar e cultivar Fungo do Nether - Critical Hits12 abril 2025 -
 desenhos-colorir-patati-patata-0412 abril 2025
desenhos-colorir-patati-patata-0412 abril 2025

