MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA
Por um escritor misterioso
Last updated 18 abril 2025

INTRODUCTION In today’s ever-evolving cybersecurity landscape, the role of malware detection solutions has reached a critical juncture in safeguarding against

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Anna Koh on LinkedIn: #cybersecurityawarenessmonth #cyberthreats #safecyberhabits #defnceapp

Shadowpad Malware Report - CYFIRMA

Saurabh Lal on LinkedIn: CYFIRMA: Cybersecurity Dossier

Stealthy EX-22 post-exploitation tool linked to LockBit ransomware

Emotet resurgence: cross-industry campaign analysis
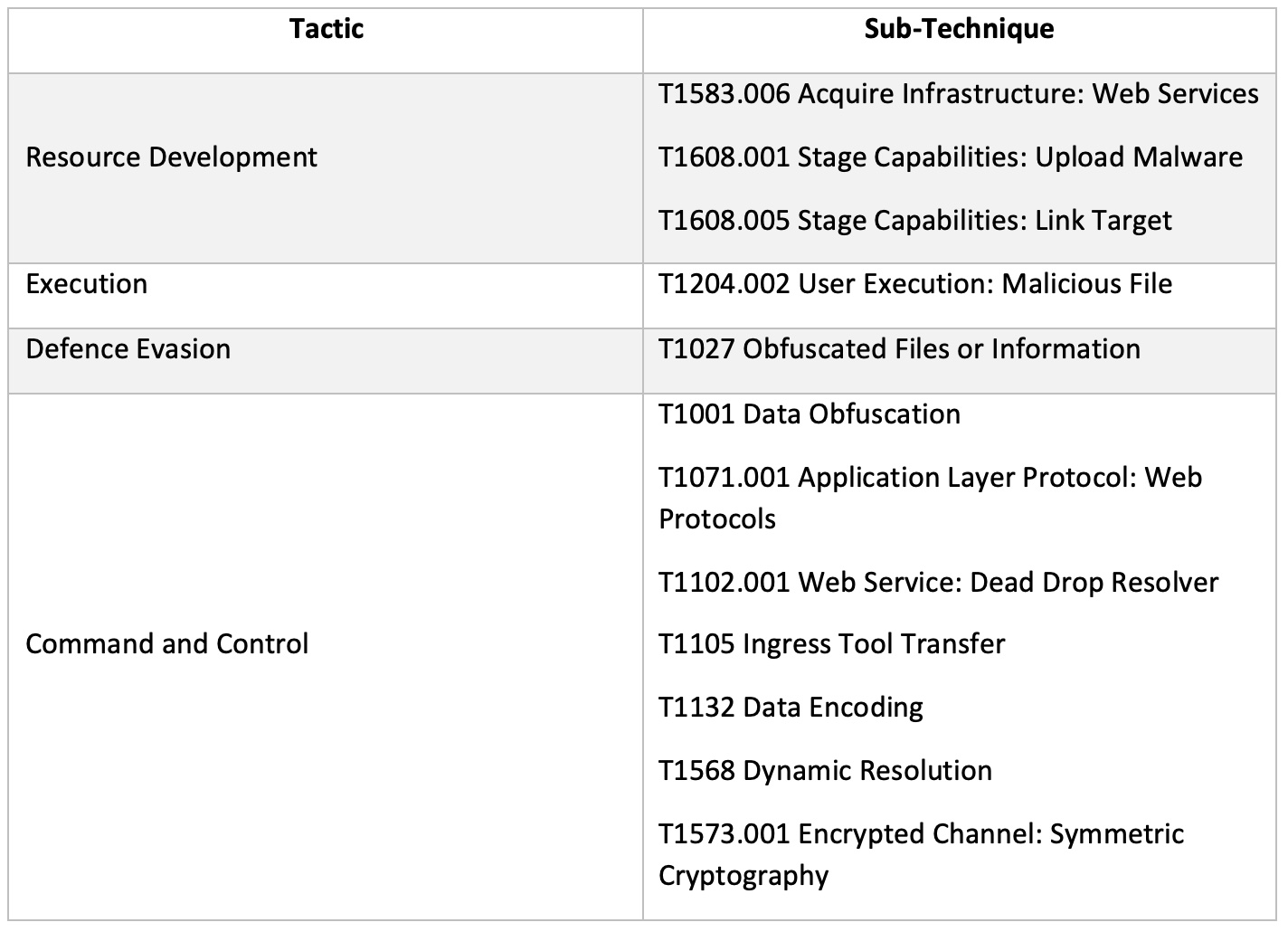
PrivateLoader: network-based indicators of compromise

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Saurabh Lal posted on LinkedIn

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Cyber Threat Intelligence Reports, Risk Research
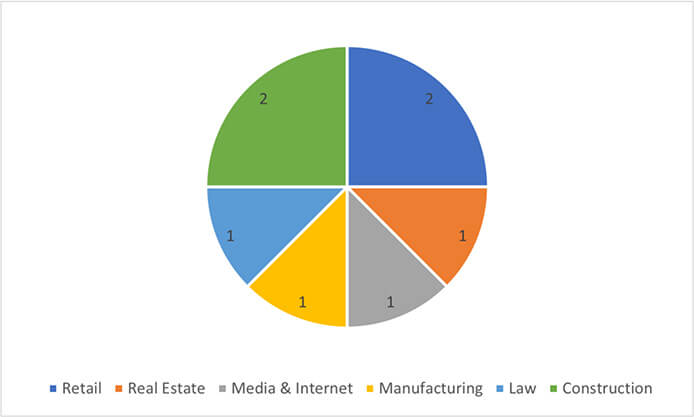
Weekly Intelligence Report - 29 Sep 2023 - CYFIRMA
Recomendado para você
-
 Evade - Xbox Controller Experience18 abril 2025
Evade - Xbox Controller Experience18 abril 2025 -
 Mutant septins evade exclusion by quality control if assembled into18 abril 2025
Mutant septins evade exclusion by quality control if assembled into18 abril 2025 -
 FinCEN discusses attempts by Russia to evade export controls - Caribbean News Global18 abril 2025
FinCEN discusses attempts by Russia to evade export controls - Caribbean News Global18 abril 2025 -
) US warns Chinese companies over efforts to evade export controls on Russia18 abril 2025
US warns Chinese companies over efforts to evade export controls on Russia18 abril 2025 -
 Loveland Products - Evade 4L Prodiamine - gal – Steve Regan Company18 abril 2025
Loveland Products - Evade 4L Prodiamine - gal – Steve Regan Company18 abril 2025 -
 Milton Friedman Quote: “By encouraging men to spy and report on one another, by making it in the private interest of large numbers of citizens t”18 abril 2025
Milton Friedman Quote: “By encouraging men to spy and report on one another, by making it in the private interest of large numbers of citizens t”18 abril 2025 -
 US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals18 abril 2025
US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals18 abril 2025 -
 Ngaba Authorities Pay for Information on Attempts to Evade Coronavirus Controls — Radio Free Asia18 abril 2025
Ngaba Authorities Pay for Information on Attempts to Evade Coronavirus Controls — Radio Free Asia18 abril 2025 -
 24 Guam National Football Stadium Stock Photos, High-Res Pictures, and Images - Getty Images18 abril 2025
24 Guam National Football Stadium Stock Photos, High-Res Pictures, and Images - Getty Images18 abril 2025 -
Binance Users in China, Elsewhere, Evade KYC Controls With Help of 'Angels': CNBC18 abril 2025
você pode gostar
-
 Kono Subarashii Sekai ni Shukufuku wo!, Kazuma Satō18 abril 2025
Kono Subarashii Sekai ni Shukufuku wo!, Kazuma Satō18 abril 2025 -
 Late Lance Reddick's Wife Reportedly Refutes His Cause Of Death18 abril 2025
Late Lance Reddick's Wife Reportedly Refutes His Cause Of Death18 abril 2025 -
 Far Cry 5 - Vector .45 at Far Cry 5 Nexus - Mods and Community18 abril 2025
Far Cry 5 - Vector .45 at Far Cry 5 Nexus - Mods and Community18 abril 2025 -
 Yukiteru Amano Yuki Future Diary Mirai Nikki Retro blue brown anime Design Poster for Sale by Raiden Designer Shop18 abril 2025
Yukiteru Amano Yuki Future Diary Mirai Nikki Retro blue brown anime Design Poster for Sale by Raiden Designer Shop18 abril 2025 -
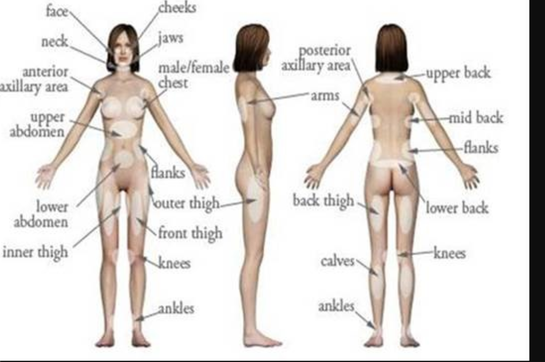 Where are your flanks located on the body? (Photo)18 abril 2025
Where are your flanks located on the body? (Photo)18 abril 2025 -
 Majutsushi Orphen - Release Order18 abril 2025
Majutsushi Orphen - Release Order18 abril 2025 -
 Convite Virtual Homem Aranha Desenho para Whatsapp - Quântica Studio18 abril 2025
Convite Virtual Homem Aranha Desenho para Whatsapp - Quântica Studio18 abril 2025 -
 Watch Dogs: Legion – Bloodline Expansion Out Now18 abril 2025
Watch Dogs: Legion – Bloodline Expansion Out Now18 abril 2025 -
 CABELO MASCULINO BONITO! Cuidados Básicos #HomensqueseCuidam18 abril 2025
CABELO MASCULINO BONITO! Cuidados Básicos #HomensqueseCuidam18 abril 2025 -
 Kurt Kunkle MBTI Personality Type: ESFP or ESFJ?18 abril 2025
Kurt Kunkle MBTI Personality Type: ESFP or ESFJ?18 abril 2025
