How to Prevent Port Scan Attacks? - GeeksforGeeks
Por um escritor misterioso
Last updated 09 abril 2025
A Computer Science portal for geeks. It contains well written, well thought and well explained computer science and programming articles, quizzes and practice/competitive programming/company interview Questions.

Security Devices and Software types to Detect Scans, secybr

What Is A Port Scan? How To Prevent Port Scan Attacks?
What Is Enumeration In Cybersecurity ?, by Enes Adışen

The 10 Major Java Security Vulnerability Types

PDF) Data Mining as a Technique for Healthcare Approach

Responding to network attacks with Suricata and Wazuh XDR

What is port scanning and how does it work?
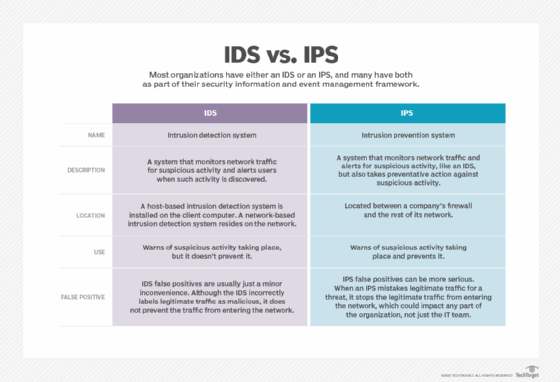
What is an Intrusion Prevention System (IPS)?

Implementing an intrusion detection and prevention system using software-defined networking: Defending against port-scanning and denial-of-service attacks - ScienceDirect
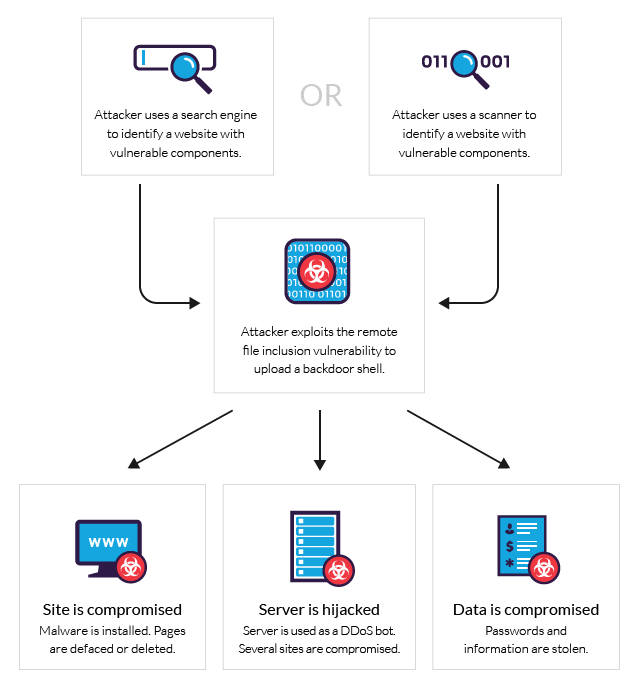
What is RFI, Remote File Inclusion Example & Mitigation Methods

Nmap Scans for Cyber Security and Penetration Testing - GeeksforGeeks
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi
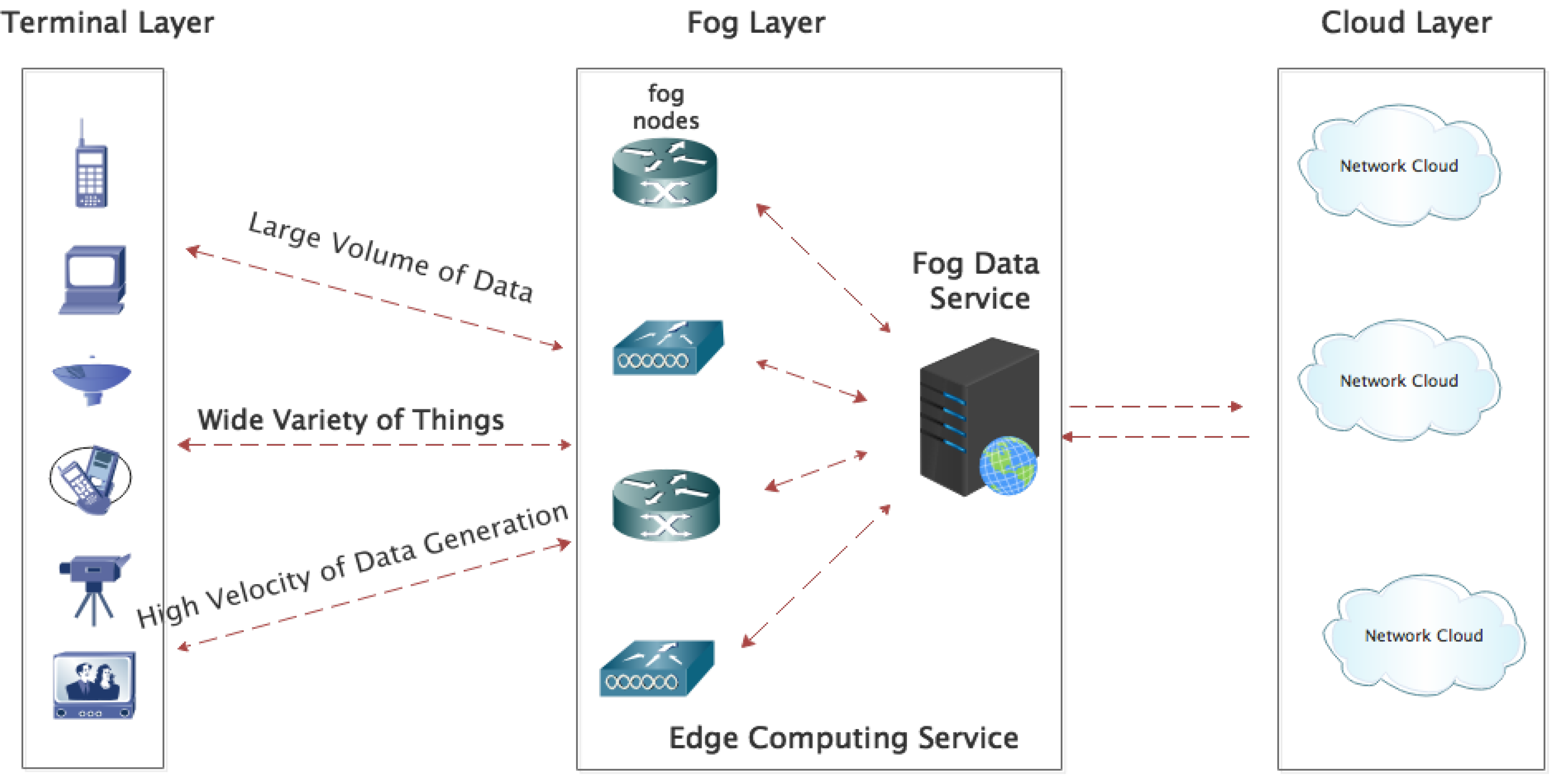
Electronics, Free Full-Text

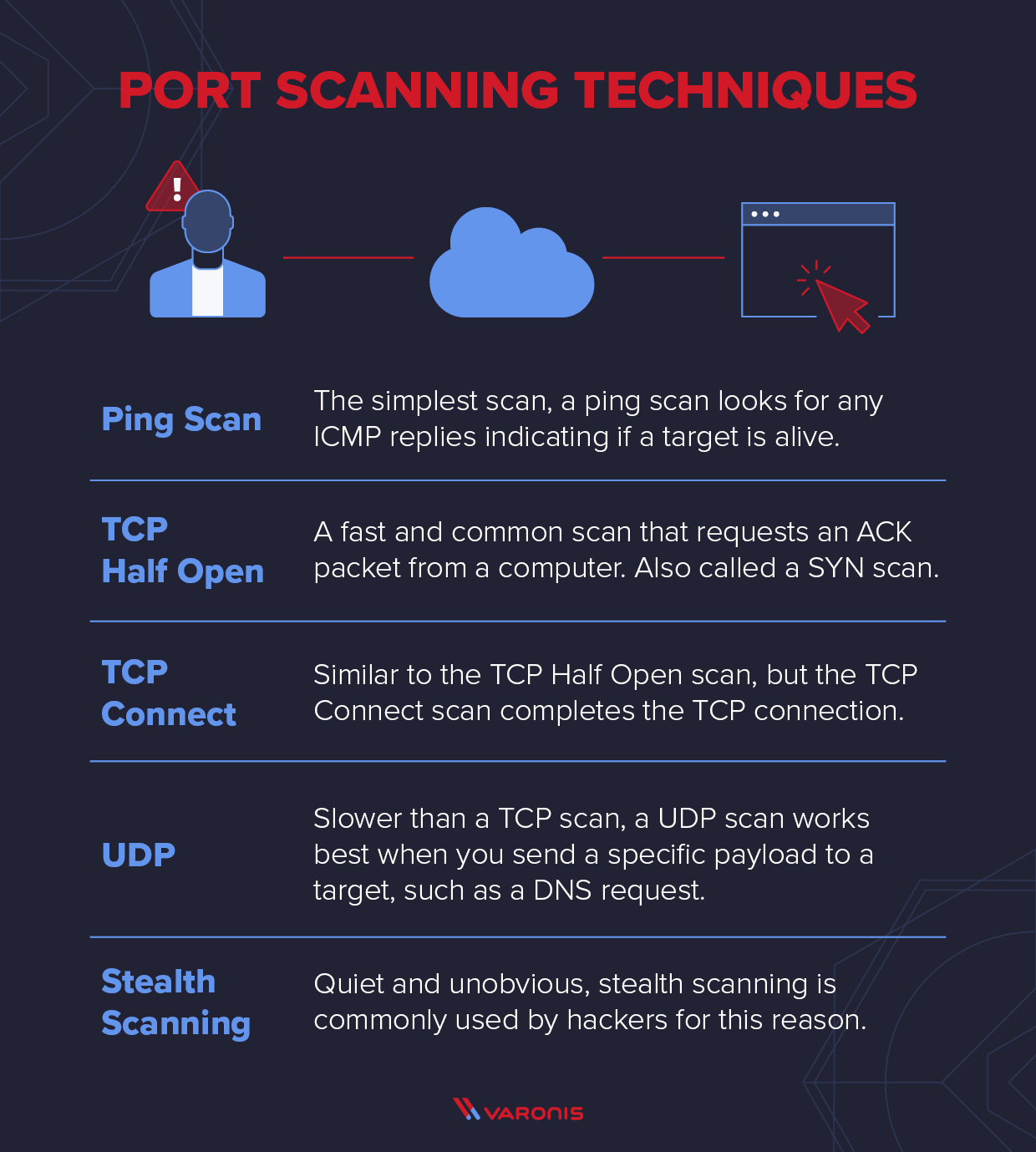
Port Scanning Techniques By Using Nmap - GeeksforGeeks
What is a Port Scanner and How Does it Work?
Recomendado para você
-
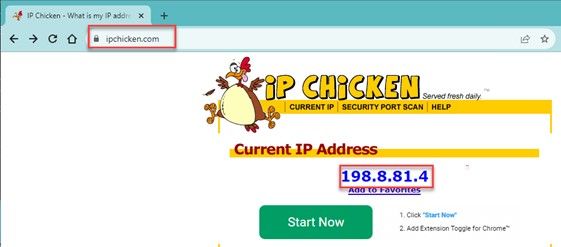
 Read own IP address and check anonymization09 abril 2025
Read own IP address and check anonymization09 abril 2025 -
 How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 abril 2025
How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 abril 2025 -
 8 Sites That Show Your IP Address –09 abril 2025
8 Sites That Show Your IP Address –09 abril 2025 -
USGPRO4: 'The gateway is unable to connect to the Internet' - but it is09 abril 2025
-
 What is port scanning and how does it work?09 abril 2025
What is port scanning and how does it work?09 abril 2025 -
 Malware analysis Malicious activity09 abril 2025
Malware analysis Malicious activity09 abril 2025 -
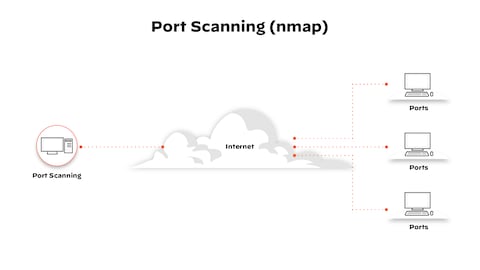 What is a Port Scan? - Palo Alto Networks09 abril 2025
What is a Port Scan? - Palo Alto Networks09 abril 2025 -
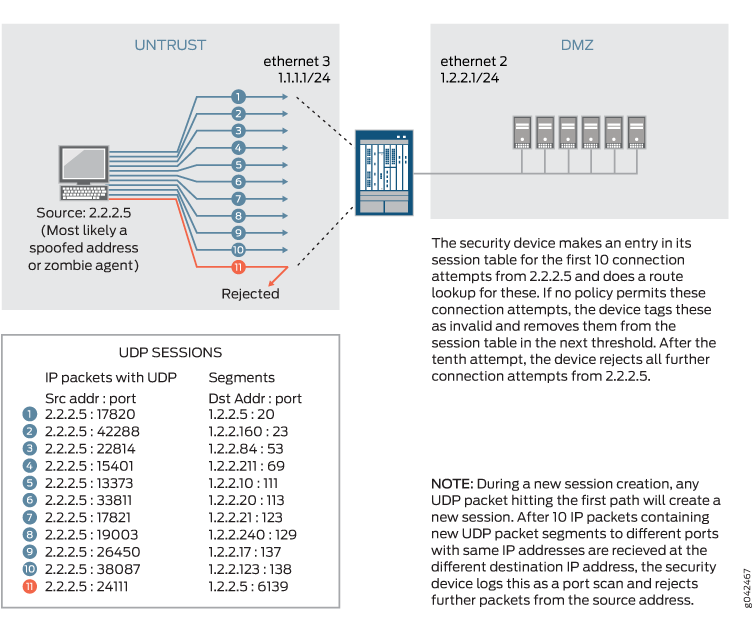 IP Address Sweep and Port Scan, Junos OS09 abril 2025
IP Address Sweep and Port Scan, Junos OS09 abril 2025 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 abril 2025
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 abril 2025 -
 Port Scanning Techniques: An Introduction09 abril 2025
Port Scanning Techniques: An Introduction09 abril 2025
você pode gostar
-
 MAKE PARA SHOWS E FESTAS MAQUIAGEM PARA FAZER *EM CASA09 abril 2025
MAKE PARA SHOWS E FESTAS MAQUIAGEM PARA FAZER *EM CASA09 abril 2025 -
 2023 Honda Civic Type R: Everything We Know About The 11th Gen Super Hot Hatch09 abril 2025
2023 Honda Civic Type R: Everything We Know About The 11th Gen Super Hot Hatch09 abril 2025 -
Need for Speed - PlayStation 4, PlayStation 409 abril 2025
-
 Green Metal Chess Set With Roman Empire Chess Pieces 13 Inch09 abril 2025
Green Metal Chess Set With Roman Empire Chess Pieces 13 Inch09 abril 2025 -
 cores Na Fila A09 abril 2025
cores Na Fila A09 abril 2025 -
 Garena Free Fire Brasil on X: A Kord é uma nova arma no servidor avançado! Ela tem mais dano e cadência de tiro ao abaixar ou deitar. Quer testar essa arma? O09 abril 2025
Garena Free Fire Brasil on X: A Kord é uma nova arma no servidor avançado! Ela tem mais dano e cadência de tiro ao abaixar ou deitar. Quer testar essa arma? O09 abril 2025 -
 TOP 7 Melhores Cursos para Concursos (Ranking 2023)09 abril 2025
TOP 7 Melhores Cursos para Concursos (Ranking 2023)09 abril 2025 -
 Why did the chicken cross the road? by DatJuanDesigner09 abril 2025
Why did the chicken cross the road? by DatJuanDesigner09 abril 2025 -
2023 Star wars wiki fandom Clone The09 abril 2025
-
Anime Trending - 86 EIGHTY-SIX Season 2 (2nd-Cour) - New09 abril 2025