Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 06 abril 2025

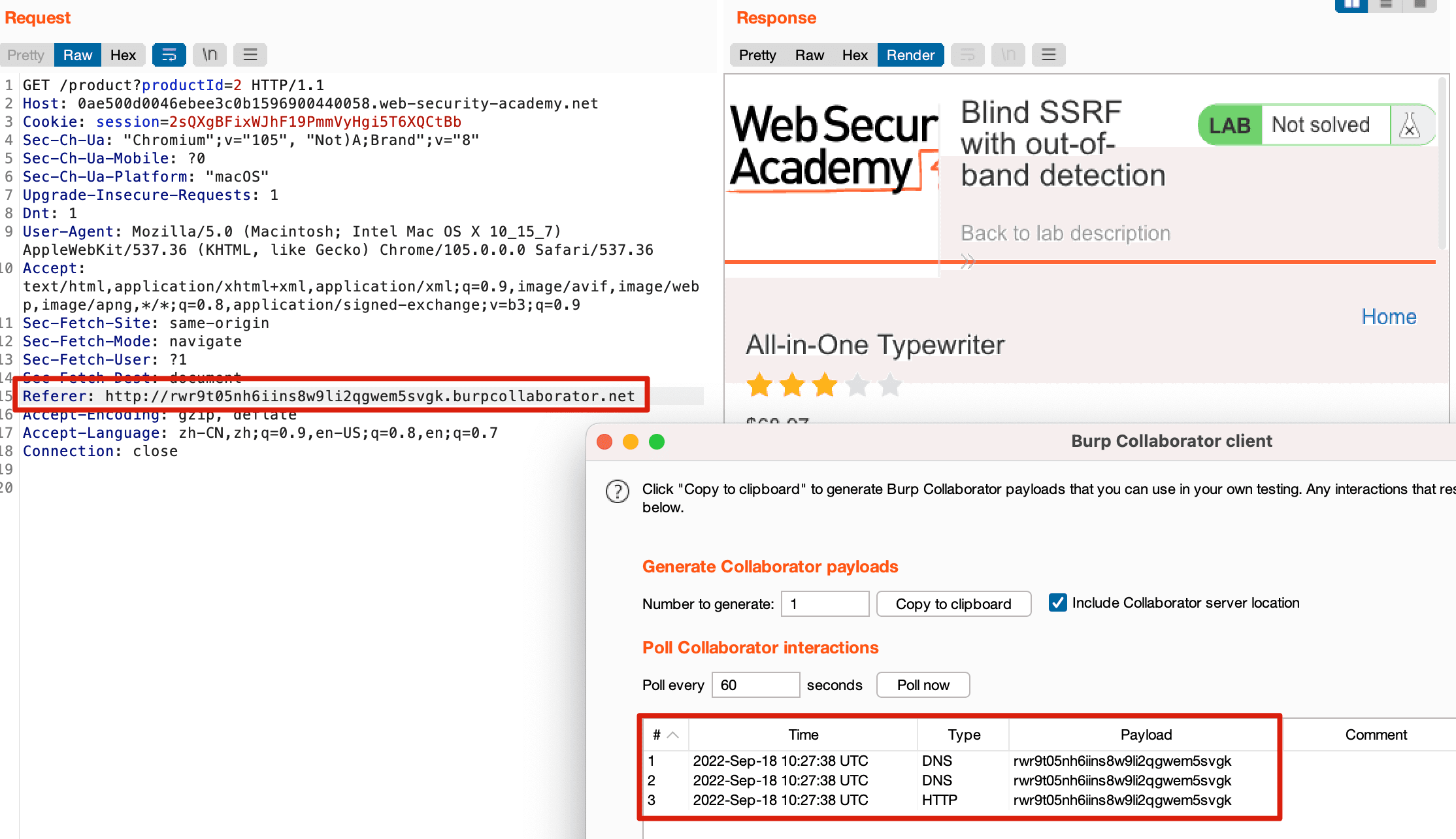
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Blind SSRF exploitation ❗️ - Wallarm

All labs Web Security Academy
Server Side Request Forgery · master · pentest-tools
PortSwigger之SSRF+XXE漏洞笔记- FreeBuf网络安全行业门户

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
Shivam Rai (@shivam24rai) / X
PayloadsAllTheThings/Server Side Request Forgery/README.md at

Blind SSRF with Shellshock exploitation (Video solution)

SSRF (Server-Side Request Forgery) - The Hacker Recipes

Free Cybersecurity & Hacking Training
Portswigger Web Security Academy Lab: Blind SSRF with
SSRF(服务器跨站请求伪造)基础知识- lca
Recomendado para você
-
 Shellshock (software bug) - Wikipedia06 abril 2025
Shellshock (software bug) - Wikipedia06 abril 2025 -
Lab Walkthrough - Shockin' Shells: ShellShock (CVE-2014-6271)06 abril 2025
-
 Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices06 abril 2025
Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices06 abril 2025 -
 Shellshock Vulnerability: What Mac OS X Users Need to Know - The Mac Security Blog06 abril 2025
Shellshock Vulnerability: What Mac OS X Users Need to Know - The Mac Security Blog06 abril 2025 -
 Shellshock – Find out if your mobile device is vulnerable - Zimperium06 abril 2025
Shellshock – Find out if your mobile device is vulnerable - Zimperium06 abril 2025 -
Hackers already exploiting Shellshock flaw06 abril 2025
-
 Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent06 abril 2025
Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent06 abril 2025 -
 Shellshock: What you need to know about the bug06 abril 2025
Shellshock: What you need to know about the bug06 abril 2025 -
.jpg&h=420&w=748&c=0&s=0) Privacy Commissioner warns business to fix Shellshock - Security - iTnews06 abril 2025
Privacy Commissioner warns business to fix Shellshock - Security - iTnews06 abril 2025 -
 Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog06 abril 2025
Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog06 abril 2025
você pode gostar
-
 COMO VENCER O NOVO DESAFIO DO CLASH OF CLANS - ESTRATÉGIA DA RAINHA DO XADREZ06 abril 2025
COMO VENCER O NOVO DESAFIO DO CLASH OF CLANS - ESTRATÉGIA DA RAINHA DO XADREZ06 abril 2025 -
![Ubisoft to go All-in on Assassin's Creed; 4 Game Projects Planned [RUMOR]](https://cdn.wccftech.com/wp-content/uploads/2023/02/assassins-creed-free-scaled.jpg) Ubisoft to go All-in on Assassin's Creed; 4 Game Projects Planned [RUMOR]06 abril 2025
Ubisoft to go All-in on Assassin's Creed; 4 Game Projects Planned [RUMOR]06 abril 2025 -
 Vc e a prace com a raven?06 abril 2025
Vc e a prace com a raven?06 abril 2025 -
 Upcoming MW3 campaign early access date has fans excited06 abril 2025
Upcoming MW3 campaign early access date has fans excited06 abril 2025 -
Stair Stringer Calculator for Android - App Download06 abril 2025
-
 Play Fortnite on RTX 30 Series06 abril 2025
Play Fortnite on RTX 30 Series06 abril 2025 -
 Perdemos dois pontos', define Abel após empate do Palmeiras no dérbi06 abril 2025
Perdemos dois pontos', define Abel após empate do Palmeiras no dérbi06 abril 2025 -
 Features - Plants vs. Zombies 2 - EA Official Site06 abril 2025
Features - Plants vs. Zombies 2 - EA Official Site06 abril 2025 -
 Minecraft pack! Cursors06 abril 2025
Minecraft pack! Cursors06 abril 2025 -
 Zorosan : u/Intelligent-Gas-554106 abril 2025
Zorosan : u/Intelligent-Gas-554106 abril 2025

