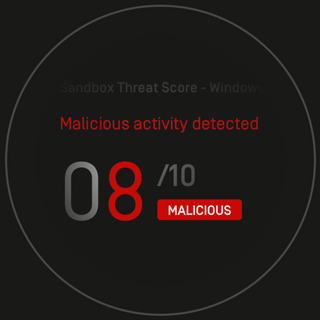
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 14 abril 2025

Malware Analysis: Steps & Examples - CrowdStrike
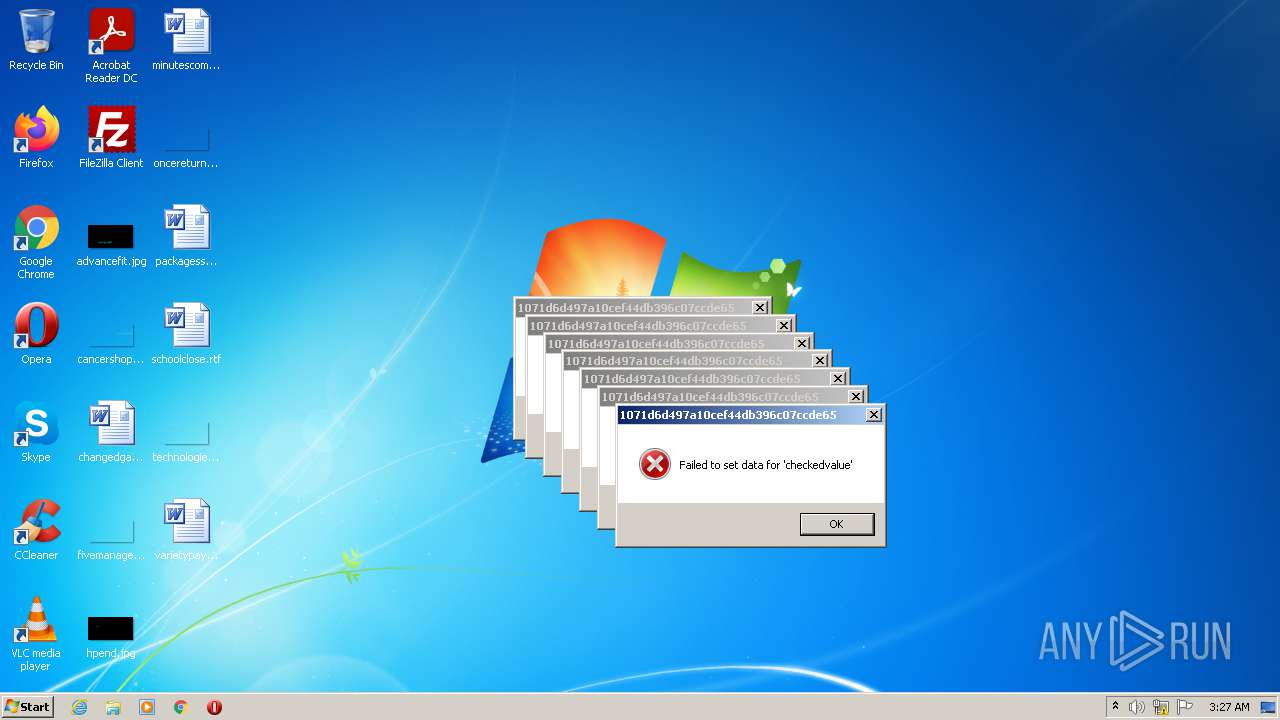
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

What is Malware? Definition, Types, Prevention - TechTarget

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Malware Analysis: Protecting Your Network from Cyber Attacks

How to Do Malware Analysis?
MetaDefender Cloud Advanced threat prevention and detection

Remediation and Malware Detection Overview

How to Analyze Malware's Network Traffic in A Sandbox

Mastering Malware Analysis
Recomendado para você
-
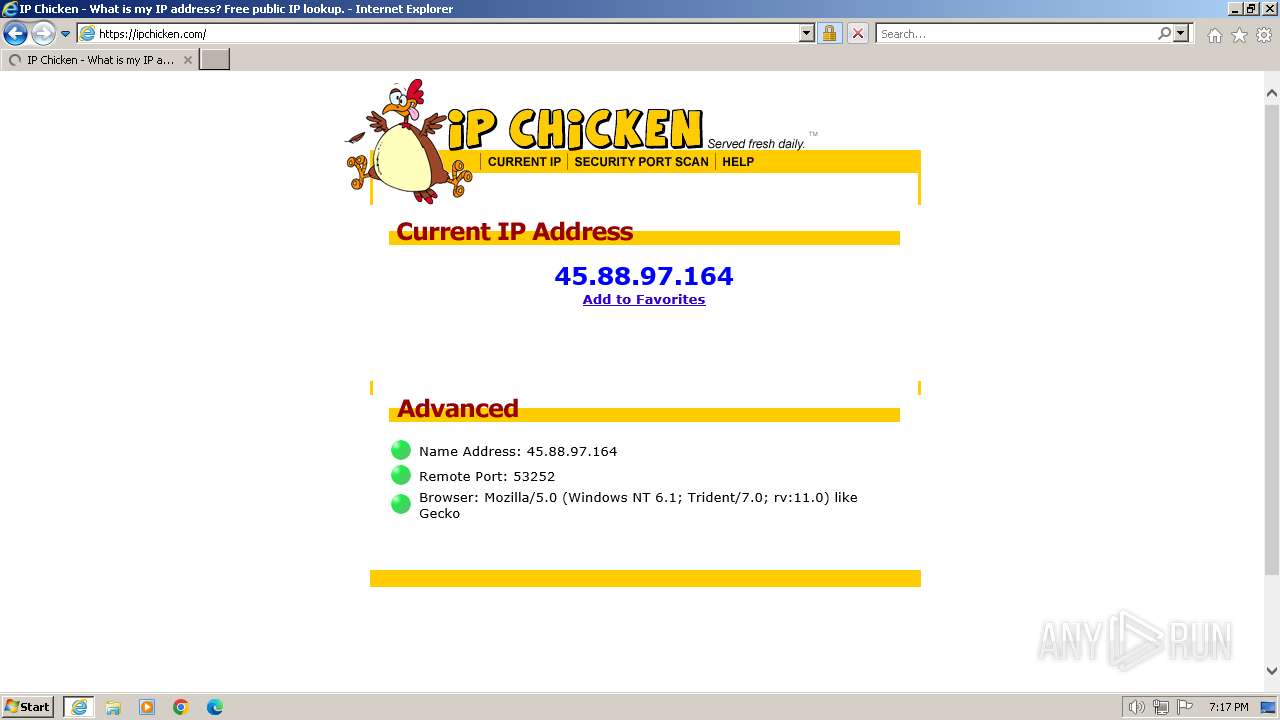
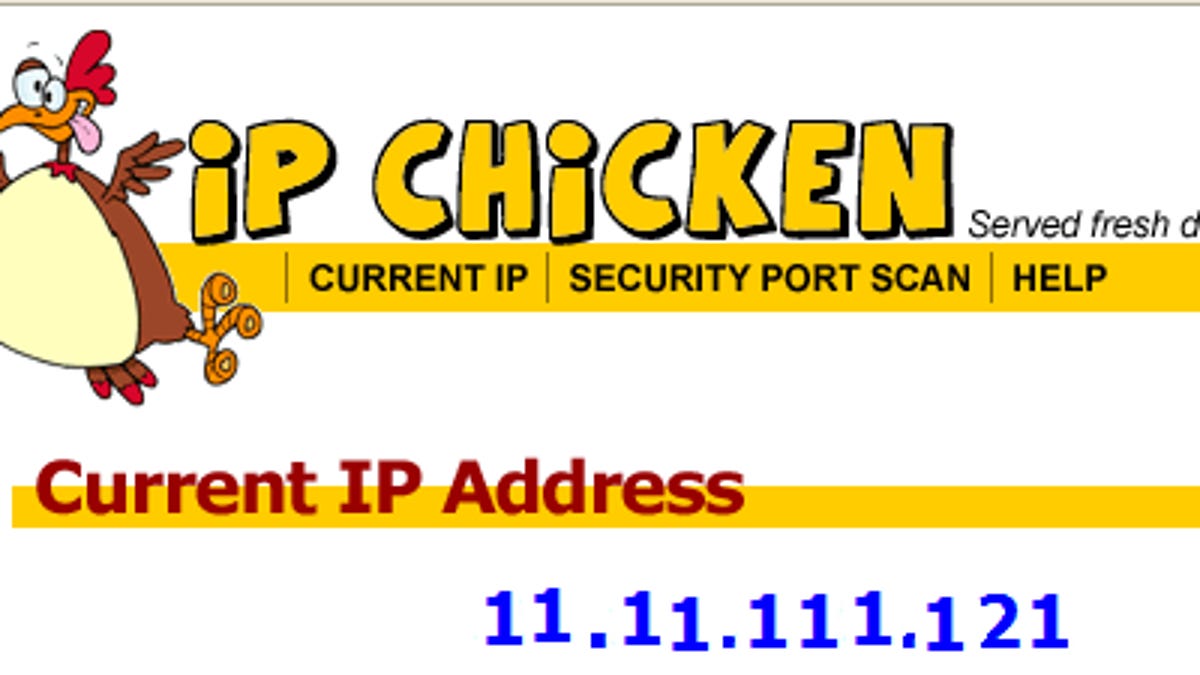 What does your IP address say about you? - CNET14 abril 2025
What does your IP address say about you? - CNET14 abril 2025 -
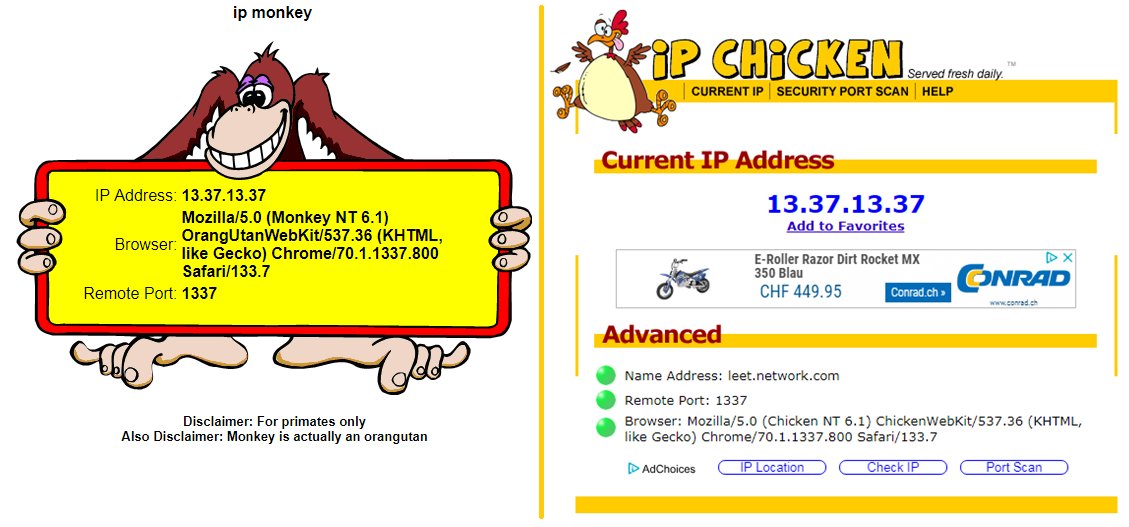 Pascal Gujer on X: / : not only showing your remote IP but also your remote port #ipchicken #ipmonkey #identification deanonymize within carrier-grade natted networks :sigh: / X14 abril 2025
Pascal Gujer on X: / : not only showing your remote IP but also your remote port #ipchicken #ipmonkey #identification deanonymize within carrier-grade natted networks :sigh: / X14 abril 2025 -
![Question] How to get around VPN blockers?](https://i.gyazo.com/f0c5d0d5b114f0d49954a16dd5112ac7.png) Question] How to get around VPN blockers?14 abril 2025
Question] How to get around VPN blockers?14 abril 2025 -
Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly14 abril 2025
-
174.218.138.250 is a publicly routable IP address is it not?14 abril 2025
-
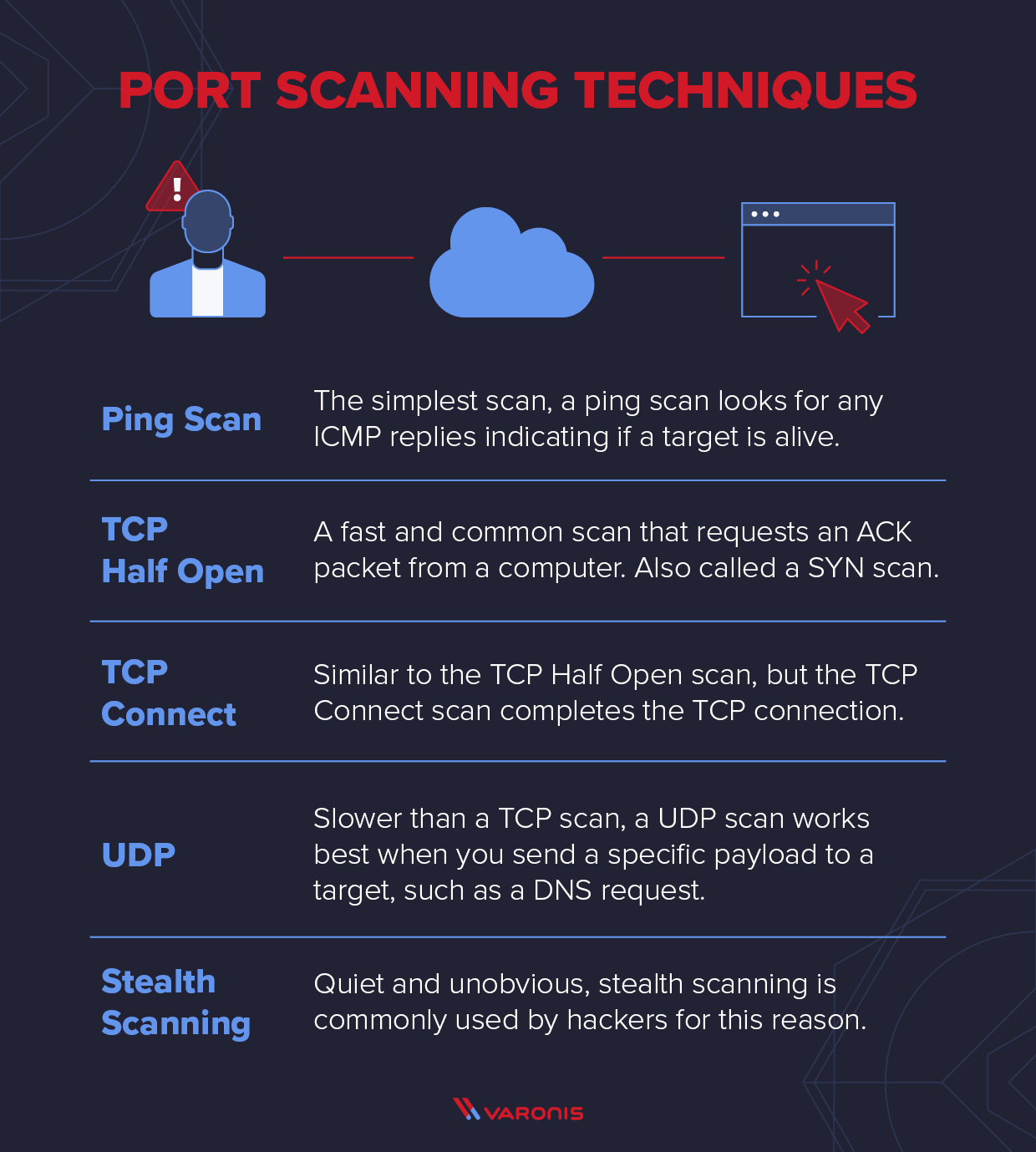 Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi14 abril 2025
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi14 abril 2025 -
 VyprVPN Review - Secure Personal VPN Service Review14 abril 2025
VyprVPN Review - Secure Personal VPN Service Review14 abril 2025 -
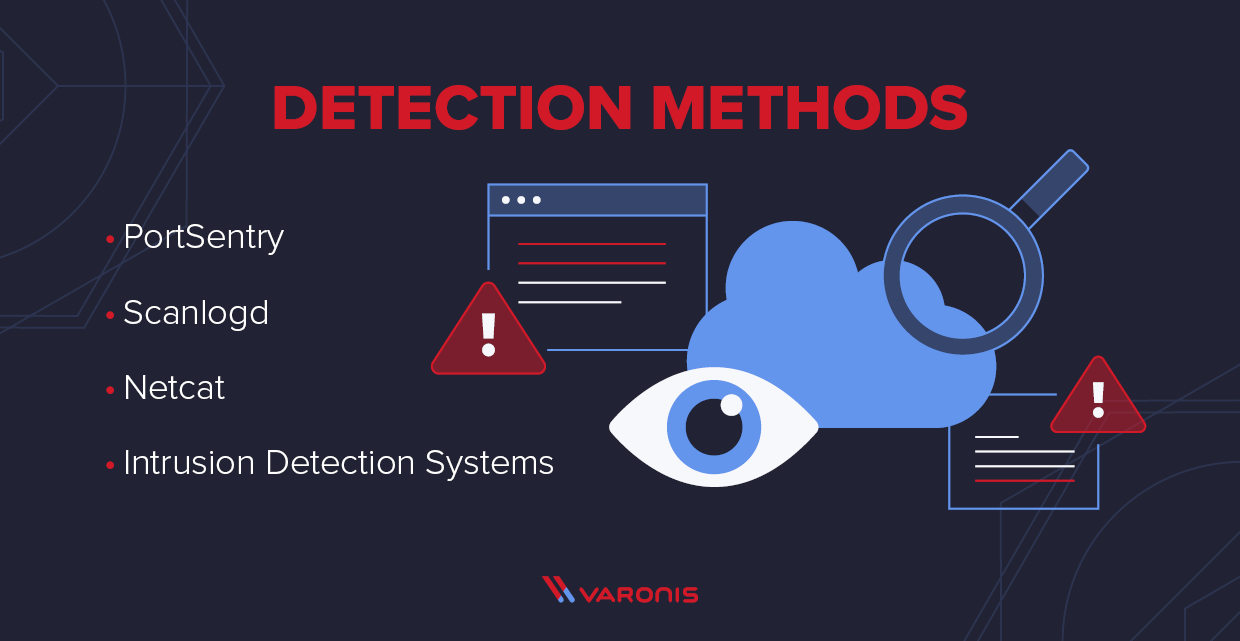 What is a Port Scanner and How Does it Work?14 abril 2025
What is a Port Scanner and How Does it Work?14 abril 2025 -
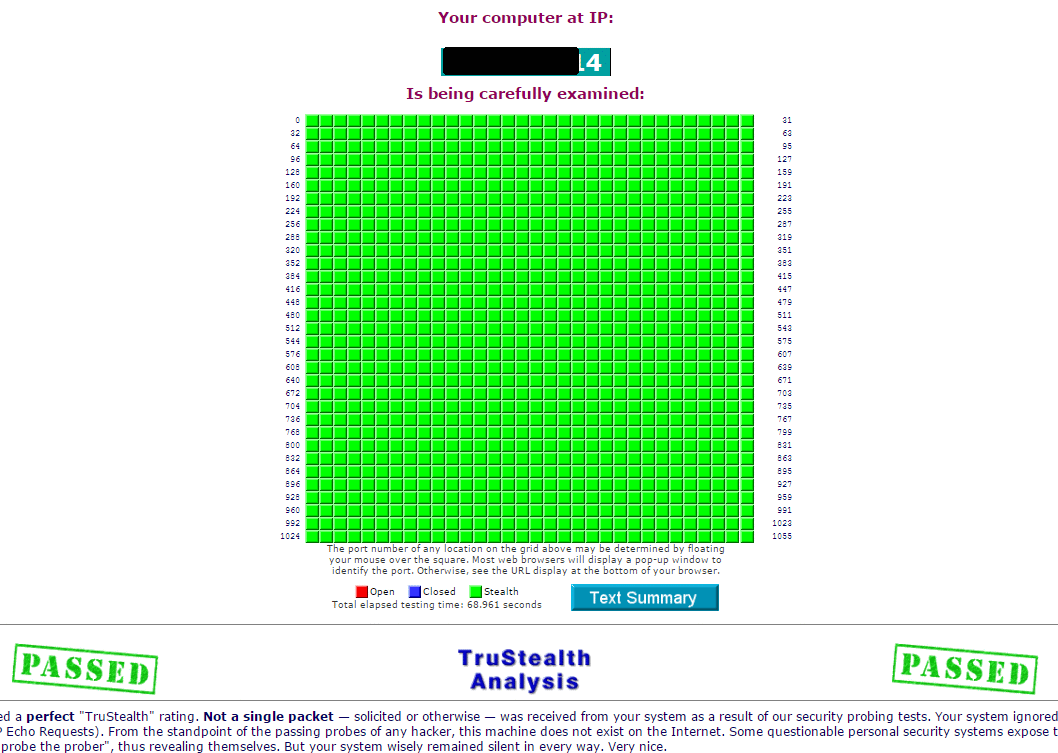 Test Your Router14 abril 2025
Test Your Router14 abril 2025 -
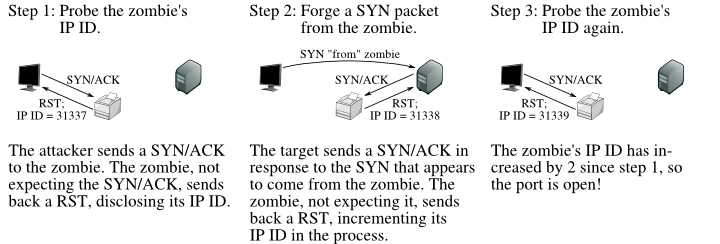 TCP Idle Scan (-sI) Nmap Network Scanning14 abril 2025
TCP Idle Scan (-sI) Nmap Network Scanning14 abril 2025
você pode gostar
-
Best Piece of Me” Project at Westside Evolved into a Community Puzzle14 abril 2025
-
 BUTTENBENDER - Aberturas em Madeira e PVC14 abril 2025
BUTTENBENDER - Aberturas em Madeira e PVC14 abril 2025 -
 Pokie GIFs14 abril 2025
Pokie GIFs14 abril 2025 -
 1,153,890 Tournament Images, Stock Photos, 3D objects, & Vectors14 abril 2025
1,153,890 Tournament Images, Stock Photos, 3D objects, & Vectors14 abril 2025 -
 Jogo de Ação – Kazaa Junior – Marvel – Spider-Man – De 2 a 4 Jogadores – Elka - RioMar Aracaju Online14 abril 2025
Jogo de Ação – Kazaa Junior – Marvel – Spider-Man – De 2 a 4 Jogadores – Elka - RioMar Aracaju Online14 abril 2025 -
 Esteira Musical do bebê do tamanho grande, Brinquedo do piano, Tocar música, Educação Infantil, Aprender Crianças14 abril 2025
Esteira Musical do bebê do tamanho grande, Brinquedo do piano, Tocar música, Educação Infantil, Aprender Crianças14 abril 2025 -
 Bridget from Guilty Gear strive by Darkcry221 on DeviantArt14 abril 2025
Bridget from Guilty Gear strive by Darkcry221 on DeviantArt14 abril 2025 -
 REACT: TOKYO REVENGERS 2 Temporada Episódio 1/QUE COMEÇO TRISTE!14 abril 2025
REACT: TOKYO REVENGERS 2 Temporada Episódio 1/QUE COMEÇO TRISTE!14 abril 2025 -
 The Joy Of Creation : Ignited Foxy Minecraft Skin14 abril 2025
The Joy Of Creation : Ignited Foxy Minecraft Skin14 abril 2025 -
SOMBO Trinkspiel Schach mit 32 Gläser, ca 35 x …14 abril 2025
![Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=2206849559462714)
