Malware analysis Malicious activity
Por um escritor misterioso
Last updated 25 abril 2025
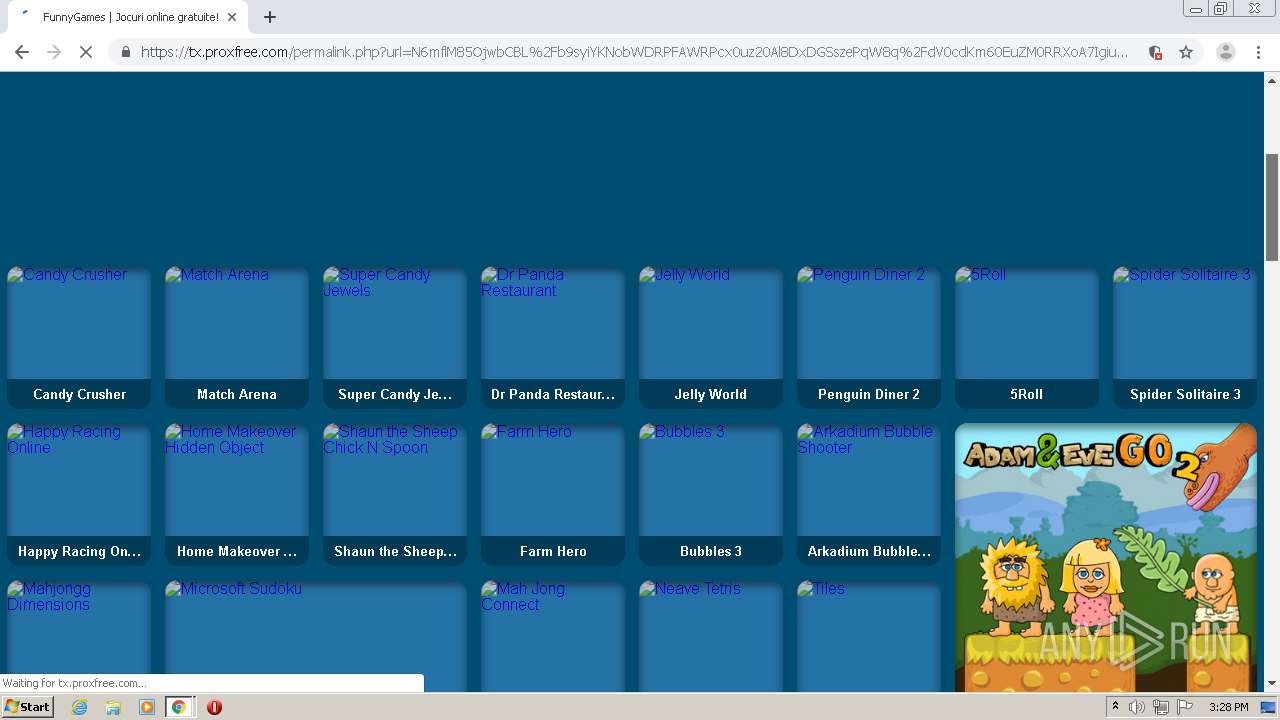

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
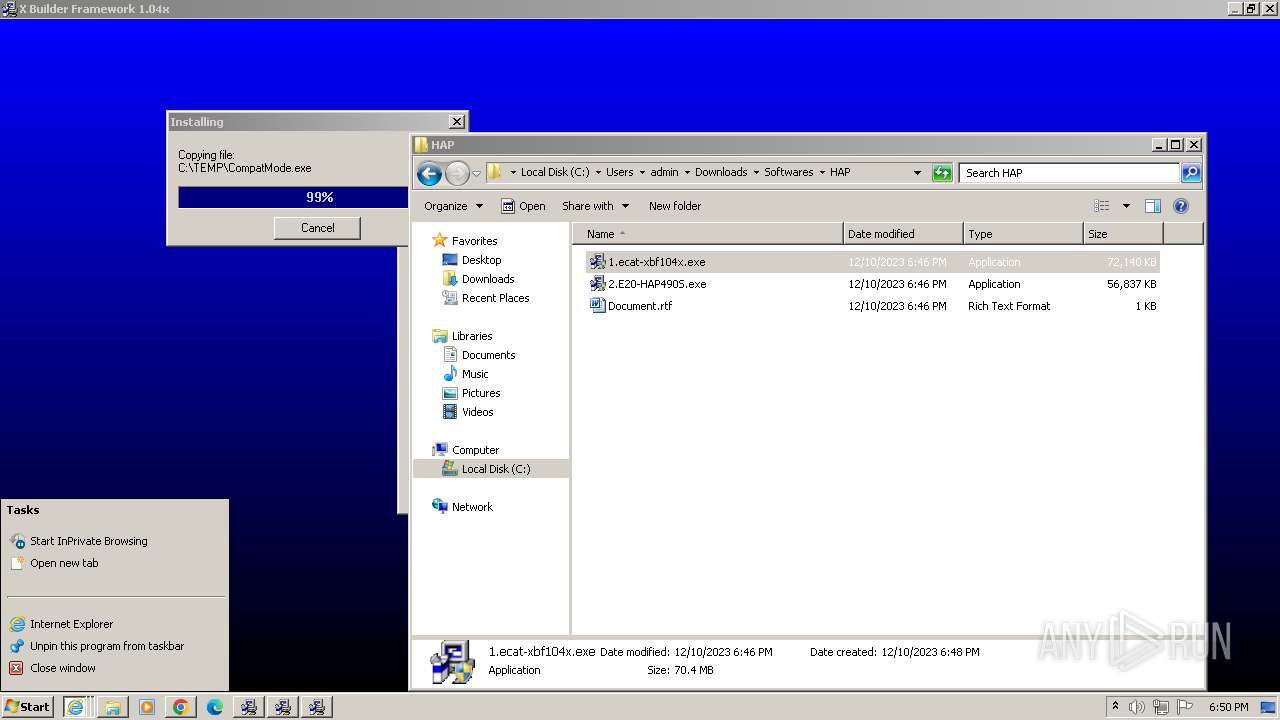
Malware analysis Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

How to Do Malware Analysis?

Endpoint Detection and Response, Free - What is EDR Security?

Malware analysis mykey_.rar Malicious activity

Website Security Checker, Malware Scan

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
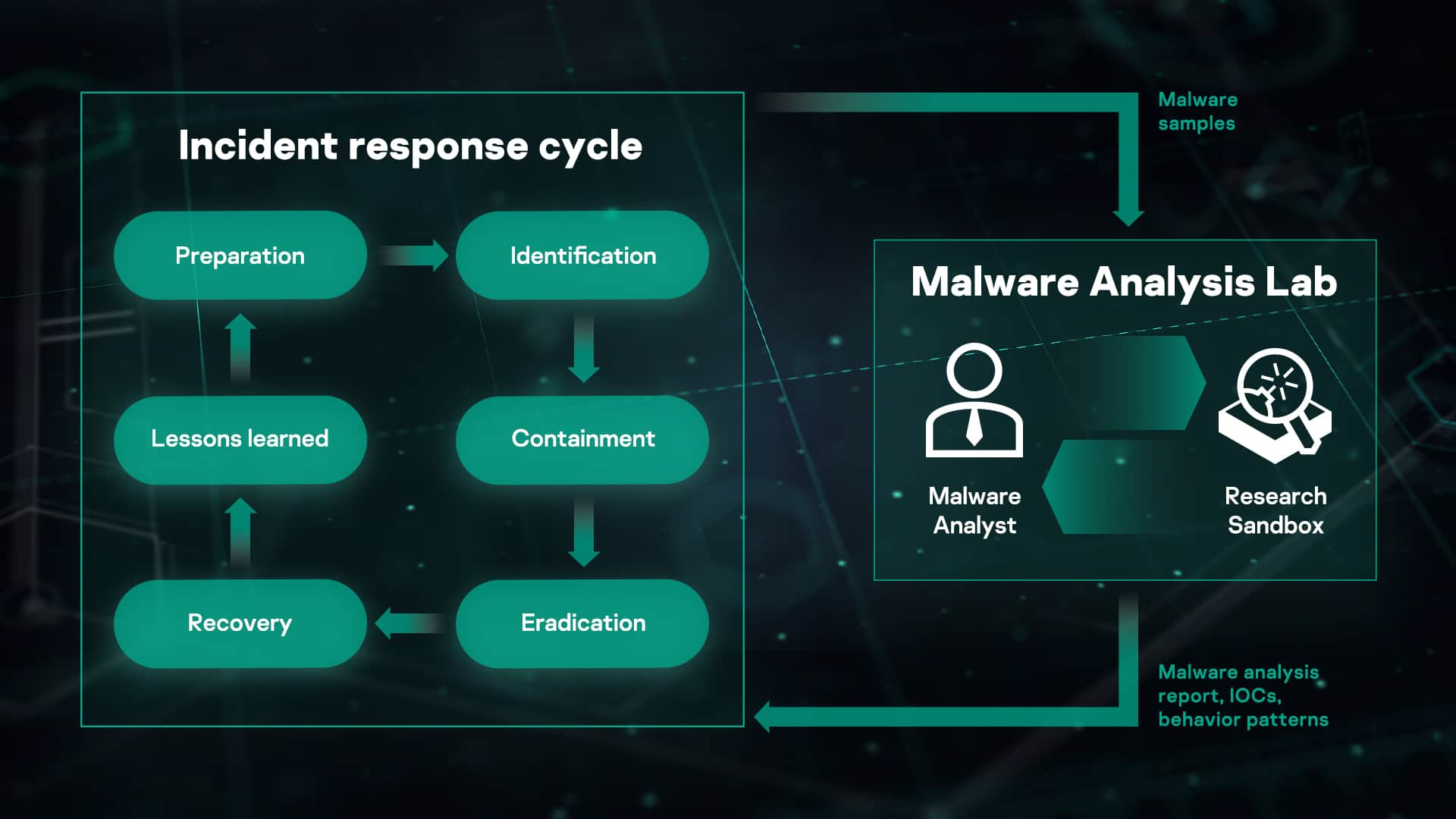
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

Cybersecurity Search Engine
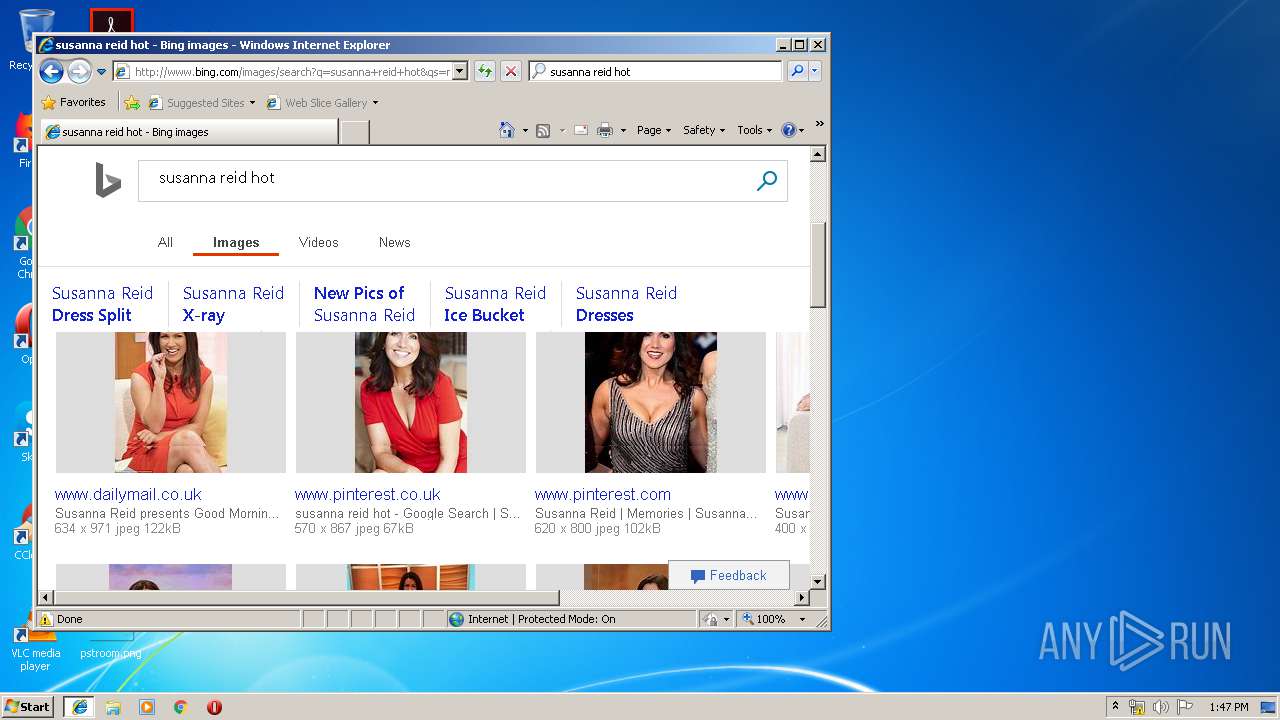
Malware analysis index.html Malicious activity
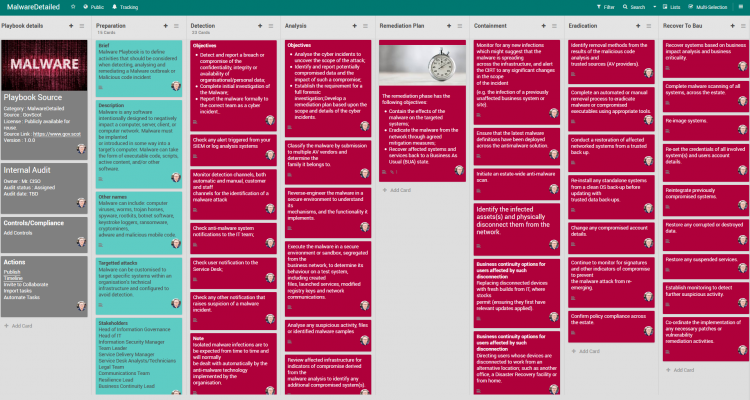
Playbook for Malware outbreak

How to Analyze Malware's Network Traffic in A Sandbox
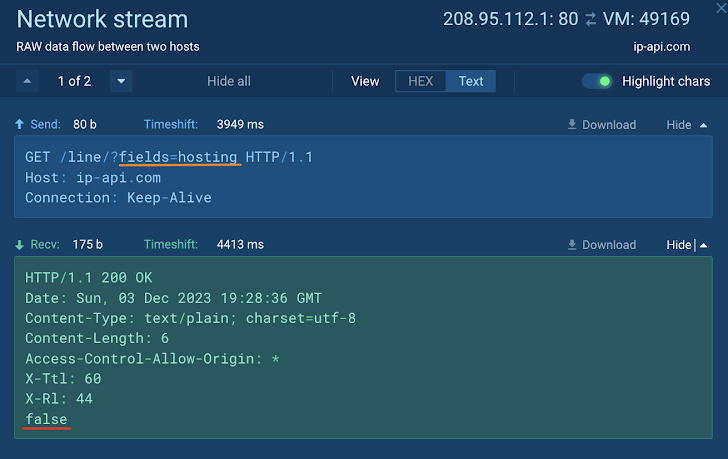
How to Analyze Malware's Network Traffic in A Sandbox

Dynamic malware analysis [34]
Recomendado para você
-
 BUBBLES 2 - Play Online for Free!25 abril 2025
BUBBLES 2 - Play Online for Free!25 abril 2025 -
 Bubbles 3 - Free Play & No Download25 abril 2025
Bubbles 3 - Free Play & No Download25 abril 2025 -
 Bubbles Antistress::Appstore for Android25 abril 2025
Bubbles Antistress::Appstore for Android25 abril 2025 -
 Bubble Hugs Gamer Coffee Mug 11oz White - Explore Grand Indoors - Funny Games Online Gamer Video Game Gaming Humor Computer Game Son Daughter Birthday : Home & Kitchen25 abril 2025
Bubble Hugs Gamer Coffee Mug 11oz White - Explore Grand Indoors - Funny Games Online Gamer Video Game Gaming Humor Computer Game Son Daughter Birthday : Home & Kitchen25 abril 2025 -
 How to access funnygames.org from any country25 abril 2025
How to access funnygames.org from any country25 abril 2025 -
 Pin on Acessórios iphone25 abril 2025
Pin on Acessórios iphone25 abril 2025 -
 Ramon van der Burgt - Graphic Designer25 abril 2025
Ramon van der Burgt - Graphic Designer25 abril 2025 -
 Premium Vector Children active games infographic with funny games round dances hopscotch board and catch up games descriptions vector illustration25 abril 2025
Premium Vector Children active games infographic with funny games round dances hopscotch board and catch up games descriptions vector illustration25 abril 2025 -
 ArtStation - Zombie Zalad University25 abril 2025
ArtStation - Zombie Zalad University25 abril 2025 -
 Tips and Links - Information on Safe Internet Use - Education25 abril 2025
Tips and Links - Information on Safe Internet Use - Education25 abril 2025
você pode gostar
-
 how to get new secret unit in anime adventure|TikTok Search25 abril 2025
how to get new secret unit in anime adventure|TikTok Search25 abril 2025 -
 Arvore De Natal Pinheiro Grande Simples Verde Nevada 1,80 Mt - DHS SHOP - Site Oficial25 abril 2025
Arvore De Natal Pinheiro Grande Simples Verde Nevada 1,80 Mt - DHS SHOP - Site Oficial25 abril 2025 -
 Mortal Kombat 1: Pacote de Kombate lança em novembro - Game Arena25 abril 2025
Mortal Kombat 1: Pacote de Kombate lança em novembro - Game Arena25 abril 2025 -
 11 Role-Play Scenarios to Help English Students Build a Story25 abril 2025
11 Role-Play Scenarios to Help English Students Build a Story25 abril 2025 -
 Blood II: The Chosen Box Shot for PC - GameFAQs25 abril 2025
Blood II: The Chosen Box Shot for PC - GameFAQs25 abril 2025 -
 Jojo's Bizarre Adventure's Title is Actually a Beatles Reference - IMDb25 abril 2025
Jojo's Bizarre Adventure's Title is Actually a Beatles Reference - IMDb25 abril 2025 -
 Dark Souls: Pickle Pee & 9 Other Extra Weird NPCs In The Series25 abril 2025
Dark Souls: Pickle Pee & 9 Other Extra Weird NPCs In The Series25 abril 2025 -
 SECADORES DE CABELO PARA SALÃO DE BELEZA25 abril 2025
SECADORES DE CABELO PARA SALÃO DE BELEZA25 abril 2025 -
 Dragon Ball Super: Super Hero - Western Release Dates Announced25 abril 2025
Dragon Ball Super: Super Hero - Western Release Dates Announced25 abril 2025 -
 Reminder: Get Horizon Zero Dawn for Free Until Tomorrow25 abril 2025
Reminder: Get Horizon Zero Dawn for Free Until Tomorrow25 abril 2025