Malware analysis Malicious activity
Por um escritor misterioso
Last updated 23 março 2025
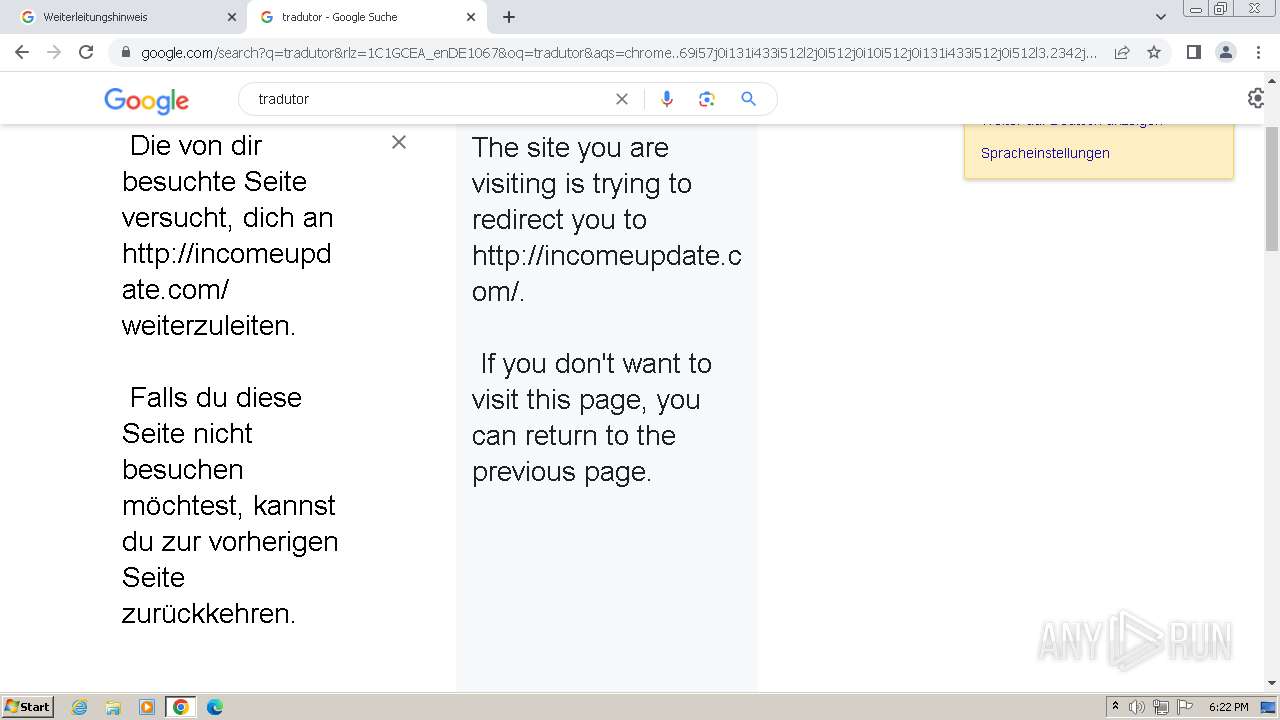

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Mastering Malware Analysis

What is Malware? Definition, Types, Prevention - TechTarget

Malware analysis mykey_.rar Malicious activity

Comprehensive Protection Strategies Against Cyber Threats

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
Most Common Malware Attacks

AV-TEST Confirms Skyhigh Security Service Edge Delivers Superior Threat Protection in All Test Categories
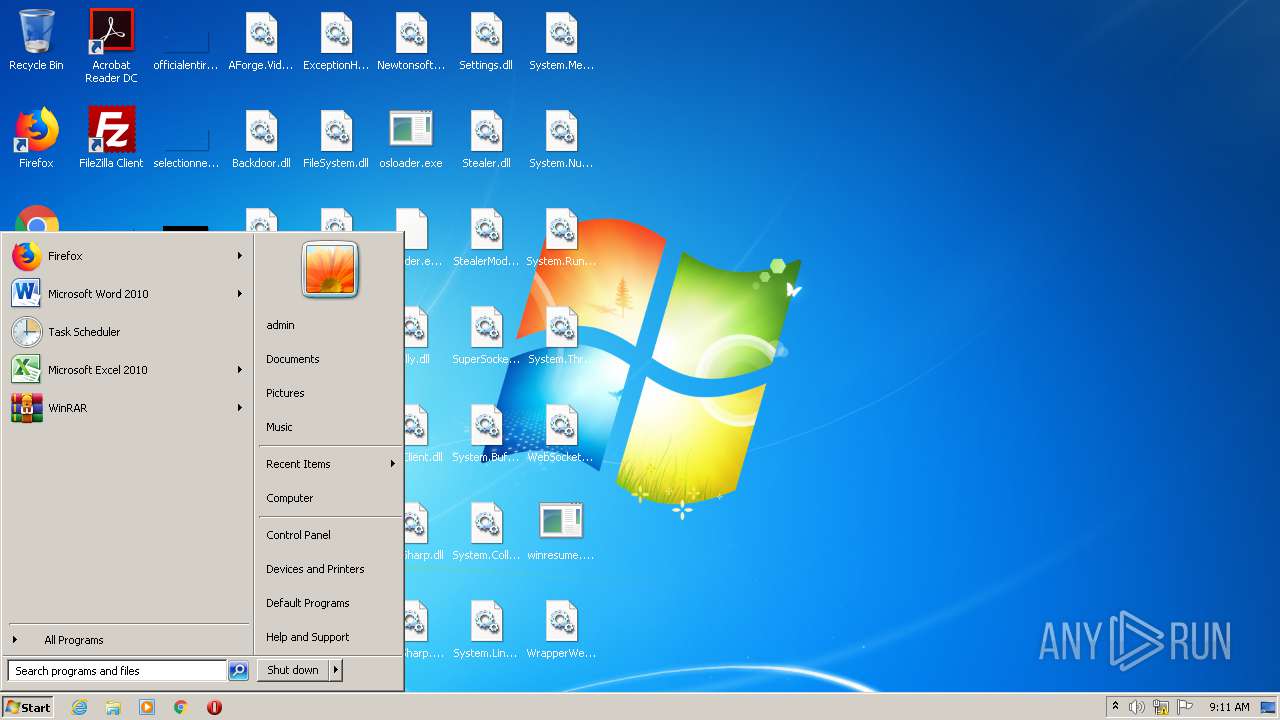
Malware analysis Release.zip Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
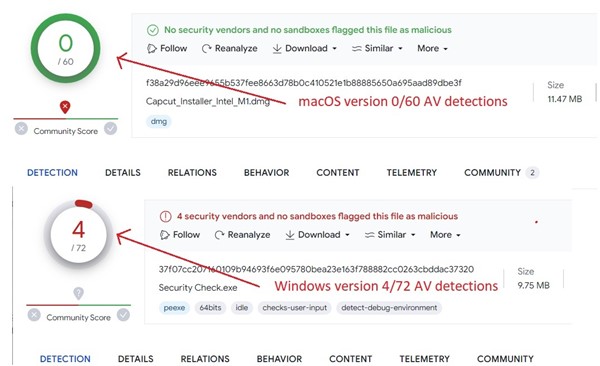
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Malware Analysis Framework v1.0

Malware Analysis: Steps & Examples - CrowdStrike
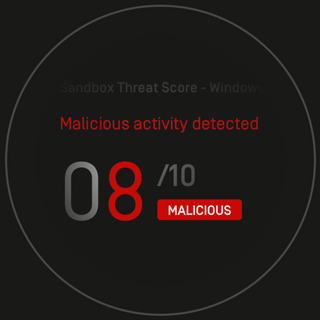
MetaDefender Cloud Advanced threat prevention and detection
Recomendado para você
-
 Google Translate - Wikipedia23 março 2025
Google Translate - Wikipedia23 março 2025 -
The Best App for Traveling the World Is Google Translate23 março 2025
-
 Google Translate - Desciclopédia23 março 2025
Google Translate - Desciclopédia23 março 2025 -
 Be you Google tradutor, Tradutor, Google23 março 2025
Be you Google tradutor, Tradutor, Google23 março 2025 -
 CapCut_promoting google drive application23 março 2025
CapCut_promoting google drive application23 março 2025 -
 15 Google Translate Fails That Will Make You Never Trust Computers Again23 março 2025
15 Google Translate Fails That Will Make You Never Trust Computers Again23 março 2025 -
 Is Google Translate good? See how the translation service works23 março 2025
Is Google Translate good? See how the translation service works23 março 2025 -
 Most Popular Google Searches: The Trending Topics on Google in 2023 - Traffic Radius23 março 2025
Most Popular Google Searches: The Trending Topics on Google in 2023 - Traffic Radius23 março 2025 -
Pesquisa por voz e tradutor de – Apps no Google Play23 março 2025
-
 Google Translate para Android - Download23 março 2025
Google Translate para Android - Download23 março 2025
você pode gostar
-
 Bolas De Bilhar Americano Ou Jogo De Bilhar De Snooker Qualquer Um Dos Vários Jogos Jogados Em Mesa Azul Foto de Stock - Imagem de colorido, relaxamento: 18893803023 março 2025
Bolas De Bilhar Americano Ou Jogo De Bilhar De Snooker Qualquer Um Dos Vários Jogos Jogados Em Mesa Azul Foto de Stock - Imagem de colorido, relaxamento: 18893803023 março 2025 -
 Netflix Music - Vinyl, CDs & Cassettes23 março 2025
Netflix Music - Vinyl, CDs & Cassettes23 março 2025 -
 Car Accident Dream - Meaning And Interpretation23 março 2025
Car Accident Dream - Meaning And Interpretation23 março 2025 -
 NOVO JOGO DE SOBREVIVÊNCIA E MUNDO ABERTO! - Winter Survival23 março 2025
NOVO JOGO DE SOBREVIVÊNCIA E MUNDO ABERTO! - Winter Survival23 março 2025 -
 João Afonso da Didáxis representa Famalicão no Campeonato Mundial de Jovens de xadrez » Fama Rádio e Televisão23 março 2025
João Afonso da Didáxis representa Famalicão no Campeonato Mundial de Jovens de xadrez » Fama Rádio e Televisão23 março 2025 -
 What Happens to Body if Someone Dies in Space? NASA Answered23 março 2025
What Happens to Body if Someone Dies in Space? NASA Answered23 março 2025 -
 Yaya Fushiguro (Yuragi-sou no Yuuna-san/Yuuna and the Haunted Hot23 março 2025
Yaya Fushiguro (Yuragi-sou no Yuuna-san/Yuuna and the Haunted Hot23 março 2025 -
 Tondemo Skill de Isekai Hourou Meshi Episode 11 English subtitles23 março 2025
Tondemo Skill de Isekai Hourou Meshi Episode 11 English subtitles23 março 2025 -
 Jogo Colors Bubble Shooter no Jogos 36023 março 2025
Jogo Colors Bubble Shooter no Jogos 36023 março 2025 -
 The Sims™ Mobile na App Store23 março 2025
The Sims™ Mobile na App Store23 março 2025