Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 07 abril 2025
Monitoring for indicators of ransomware attacks - Splunk Lantern
A Basic Malware Analysis Walkthrough, by Dan Crossley

How Malware Analysis Works - NetWitness Community - 669511
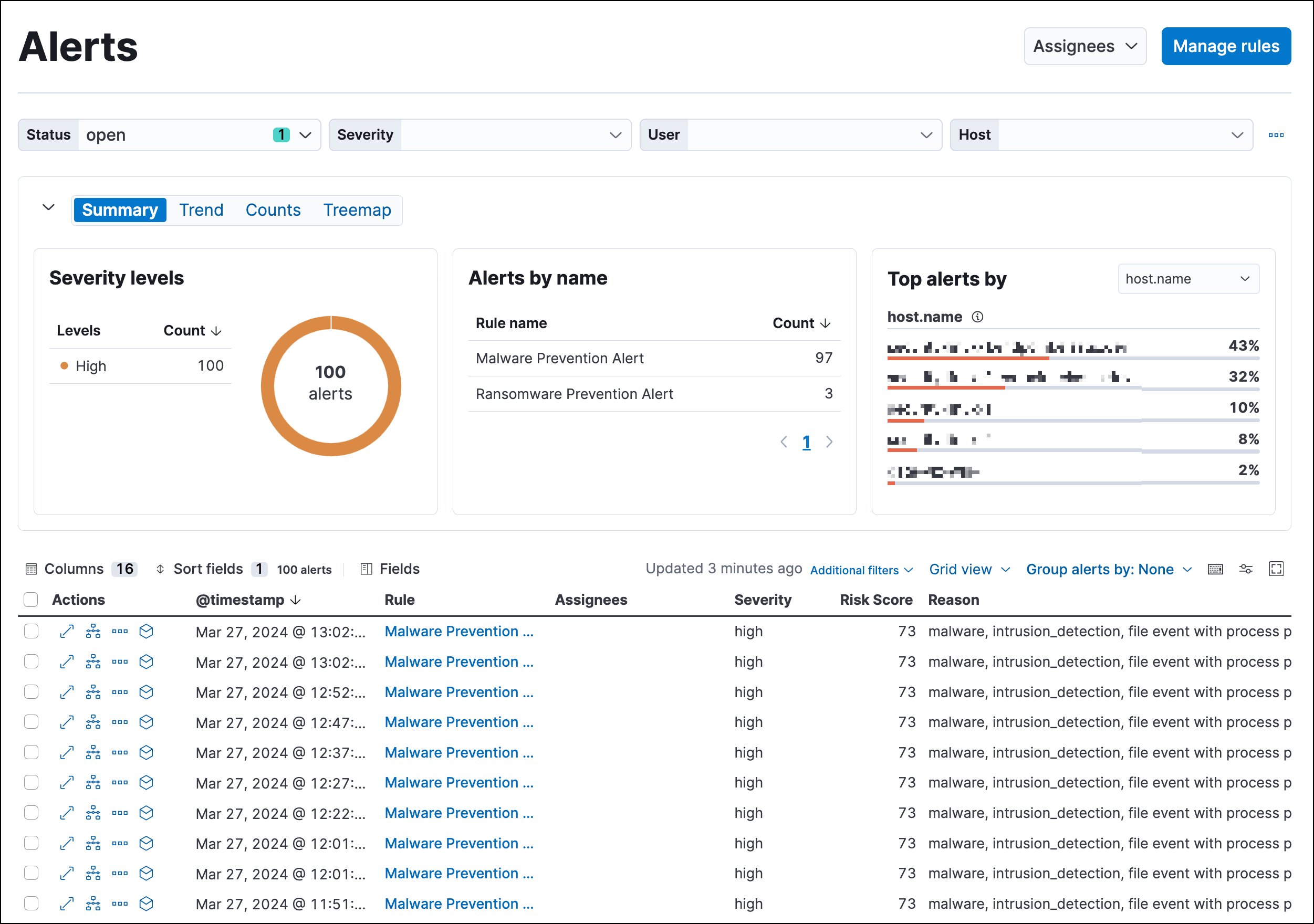
Detections and alerts, Elastic Security Solution [8.11]

Intro to Malware Analysis: What It Is & How It Works - InfoSec
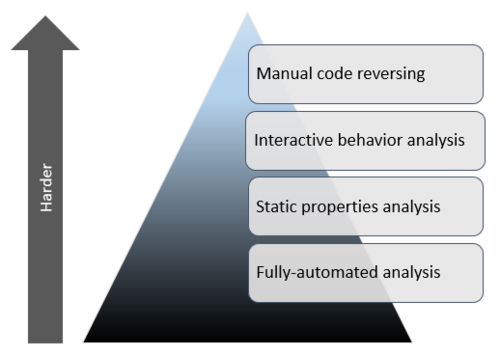
Mastering 4 Stages of Malware Analysis
The State of Malware Analysis
11 Best Malware Analysis Tools and Their Features
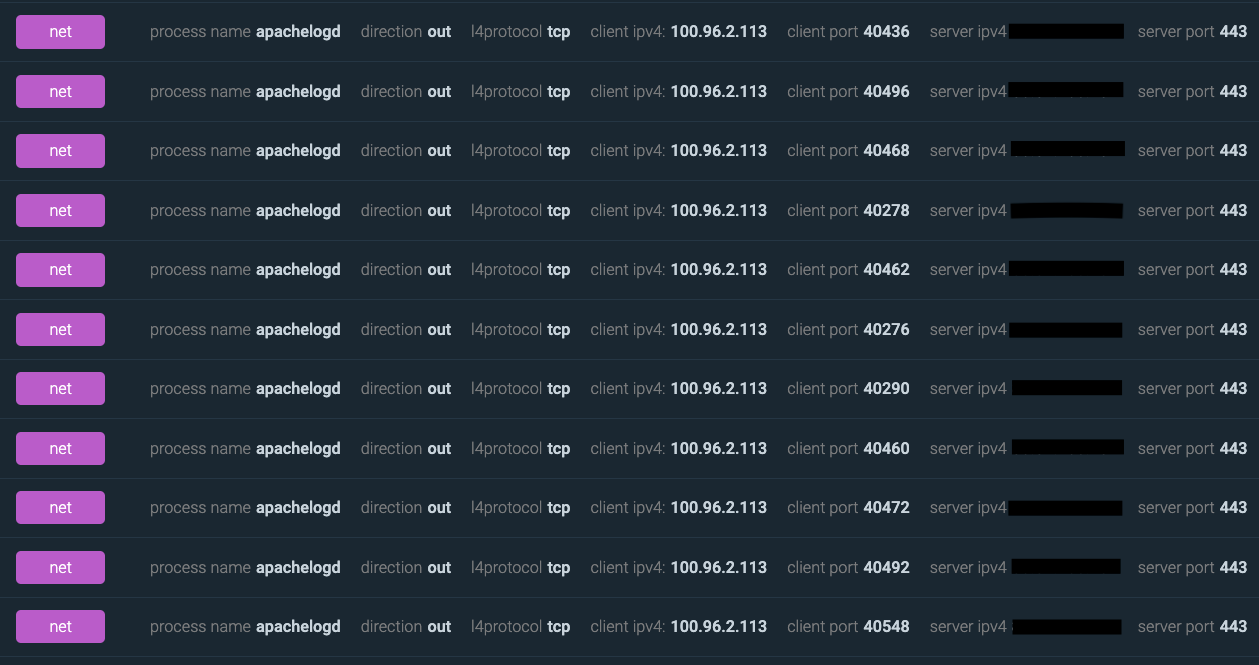
Malware analysis: Hands-On Shellbot malware – Sysdig

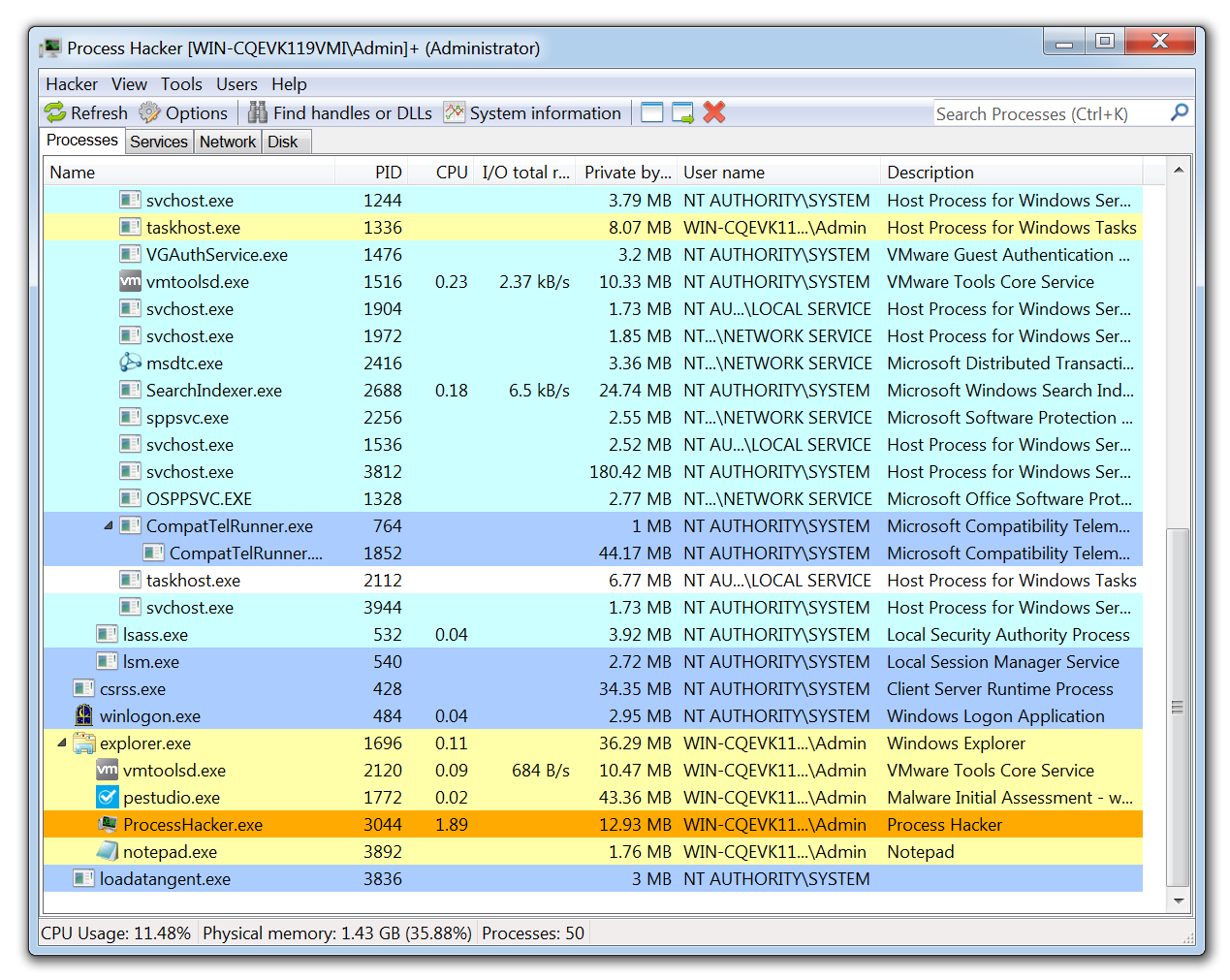
Malware Incident Response Steps on Windows, and Determining If the
How to Detect Running Malware - Intro to Incident Response Triage 2021

What Is Malware Analysis? Definition, Types, Stages, and Best
Recomendado para você
-
 What does your IP address say about you? - CNET07 abril 2025
What does your IP address say about you? - CNET07 abril 2025 -
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack07 abril 2025
-
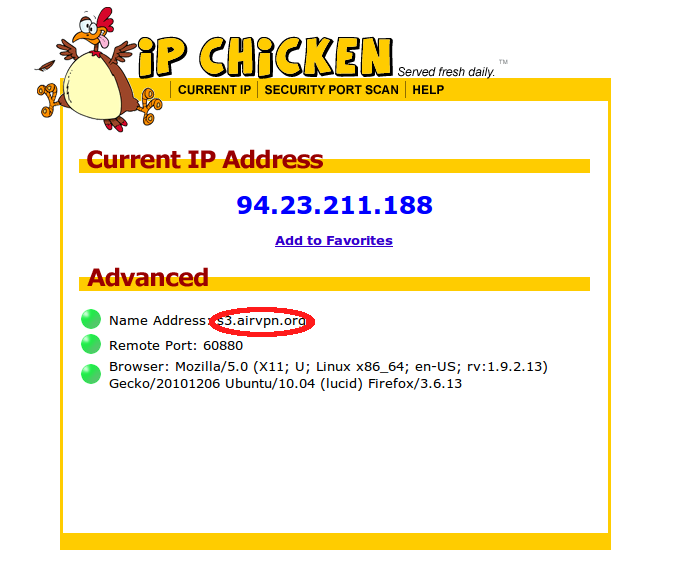 How to Bypass Internet Censorship07 abril 2025
How to Bypass Internet Censorship07 abril 2025 -
 Block ads on all your devices using pfSense, Squid & SquidGuard07 abril 2025
Block ads on all your devices using pfSense, Squid & SquidGuard07 abril 2025 -
:max_bytes(150000):strip_icc()/curl-command-ip-address-0bbe45c7243d42acaff9ddf2f117a7cb.png) How to Find Your IP Address on Windows 1007 abril 2025
How to Find Your IP Address on Windows 1007 abril 2025 -
 Anonymous Security Scanning and Browsing07 abril 2025
Anonymous Security Scanning and Browsing07 abril 2025 -
 Brisson teaches internet safety - Munising Beacon07 abril 2025
Brisson teaches internet safety - Munising Beacon07 abril 2025 -
 How to Prevent Port Scan Attacks? - GeeksforGeeks07 abril 2025
How to Prevent Port Scan Attacks? - GeeksforGeeks07 abril 2025 -
 LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community07 abril 2025
LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community07 abril 2025 -
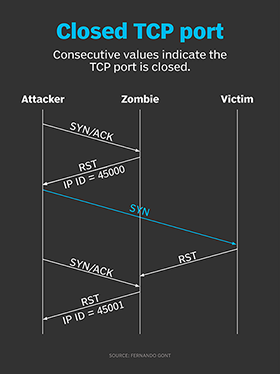 How hackers use idle scans in port scan attacks07 abril 2025
How hackers use idle scans in port scan attacks07 abril 2025
você pode gostar
-
 Hillsburgh Erin and District Soccer07 abril 2025
Hillsburgh Erin and District Soccer07 abril 2025 -
 Storm Kol Mikaelson - angel - Wattpad07 abril 2025
Storm Kol Mikaelson - angel - Wattpad07 abril 2025 -
 Primeiro Hokage Hashirama Chibi Naruto Pvc 4 Cm07 abril 2025
Primeiro Hokage Hashirama Chibi Naruto Pvc 4 Cm07 abril 2025 -
Download TWO PLAYER TANK WARS GAME 3D - 2 PLAYER TANK GAME (MOD07 abril 2025
-
 Gaara Naruto Minato Namikaze Sasuke Uchiha Sakura Haruno, naruto, child, face, hand png07 abril 2025
Gaara Naruto Minato Namikaze Sasuke Uchiha Sakura Haruno, naruto, child, face, hand png07 abril 2025 -
 January 21, 2023, Modena, Italy: Modena, Italy, Alberto Braglia stadium, January 21, 2023, Fans of Modena during Modena FC vs Cosenza Calcio - Italian soccer Serie B match. (Credit Image: © Luca07 abril 2025
January 21, 2023, Modena, Italy: Modena, Italy, Alberto Braglia stadium, January 21, 2023, Fans of Modena during Modena FC vs Cosenza Calcio - Italian soccer Serie B match. (Credit Image: © Luca07 abril 2025 -
 Wii U Launch Detailed For Japan, Arriving This December07 abril 2025
Wii U Launch Detailed For Japan, Arriving This December07 abril 2025 -
 Pokémon Counter Chart Pokemon type chart, Pokemon, Type pokemon07 abril 2025
Pokémon Counter Chart Pokemon type chart, Pokemon, Type pokemon07 abril 2025 -
 Tfw u encountered a KaeMito meme out in the wild in 2023 : r/Nijisanji07 abril 2025
Tfw u encountered a KaeMito meme out in the wild in 2023 : r/Nijisanji07 abril 2025 -
 Crunchyroll confirma la tercera temporada de Dr. Stone y el07 abril 2025
Crunchyroll confirma la tercera temporada de Dr. Stone y el07 abril 2025