Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 25 abril 2025

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Advanced Malware Detection – Signatures vs. Behavior Analysis
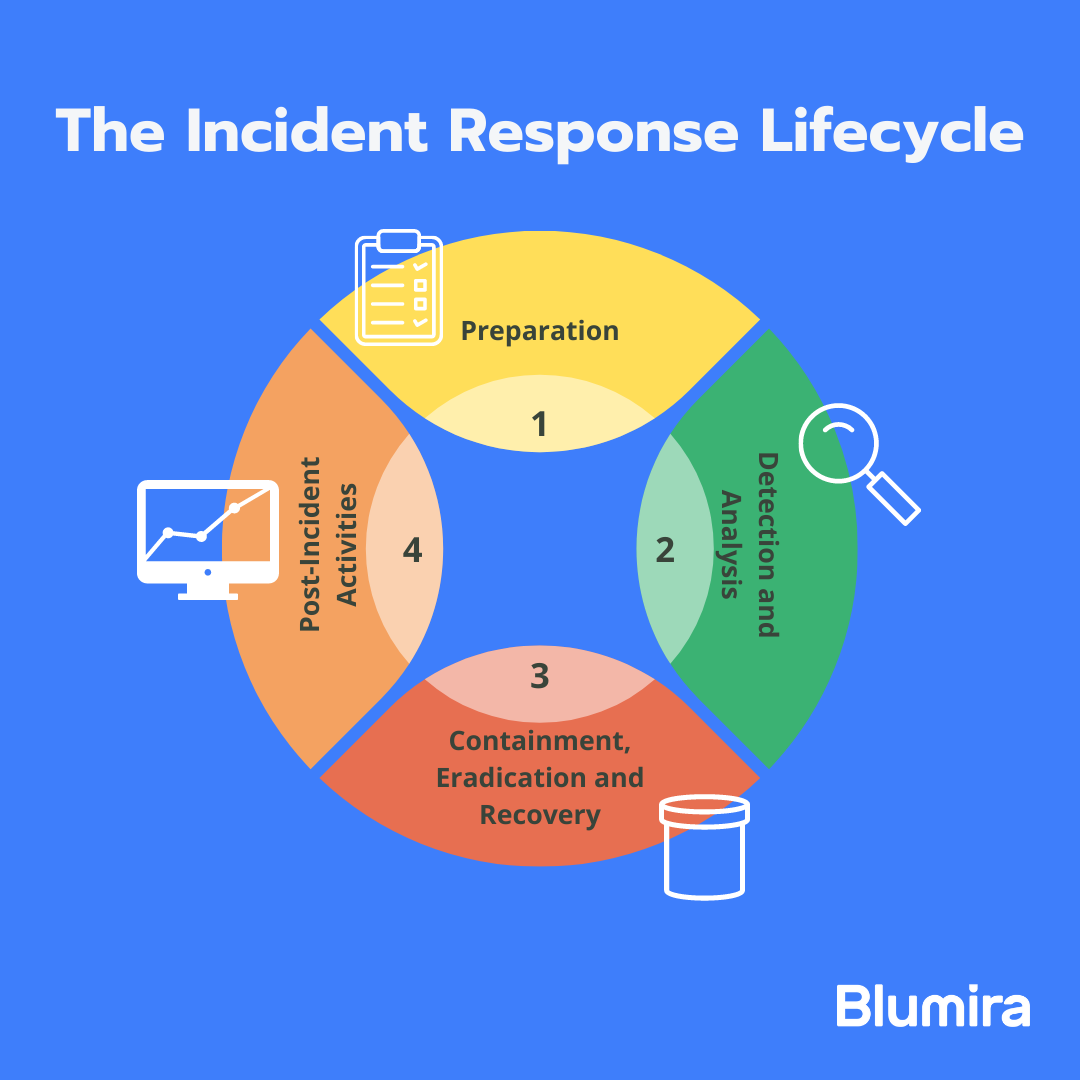
Building Effective Incident Response Procedures
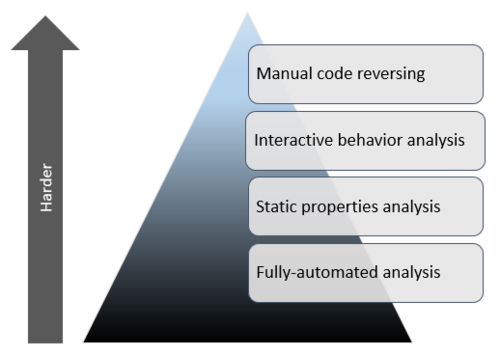
Mastering 4 Stages of Malware Analysis

Top 10 Malware Analysis Platforms & Tools
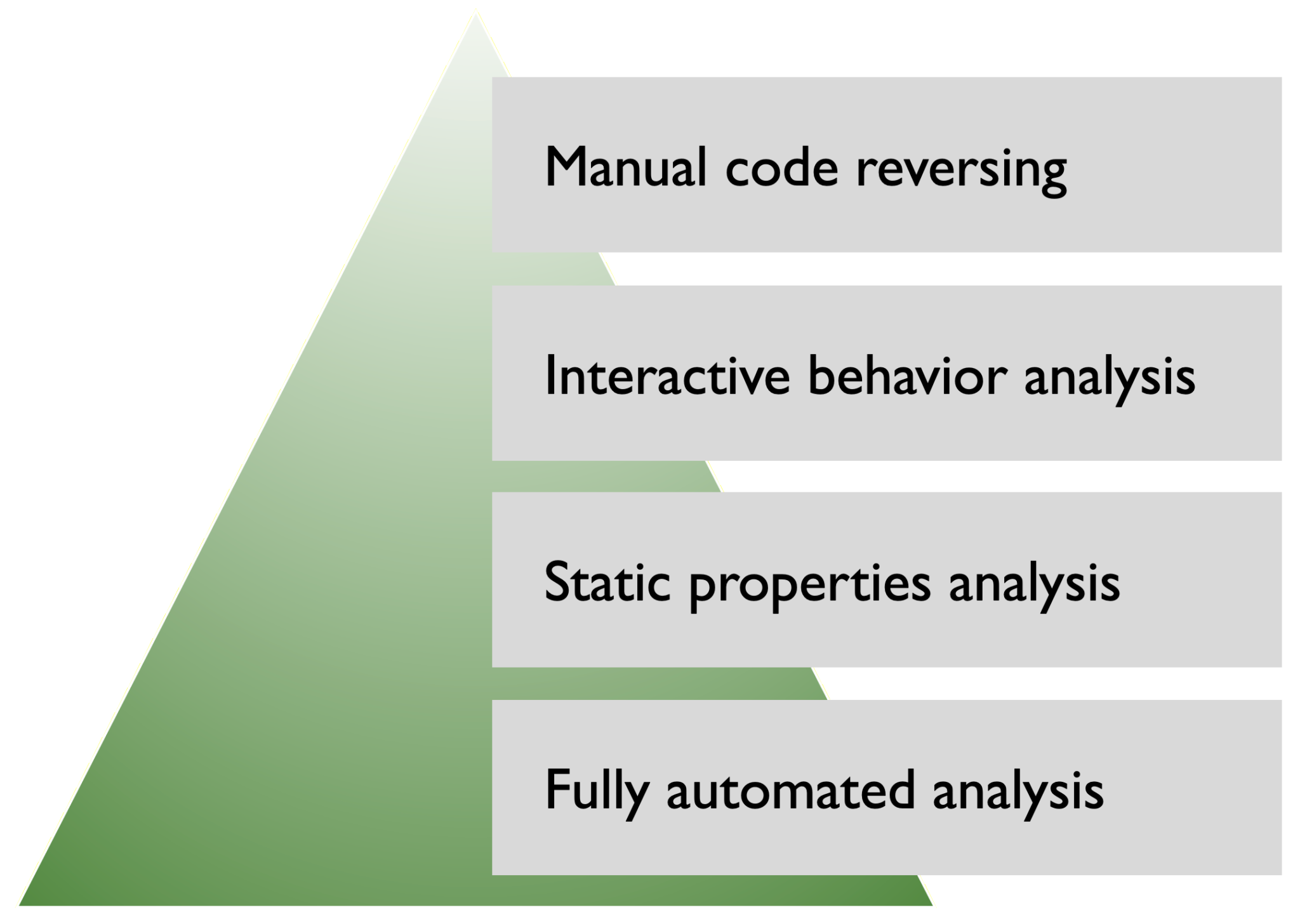
How You Can Start Learning Malware Analysis

Malware Analysis: Steps & Examples - CrowdStrike
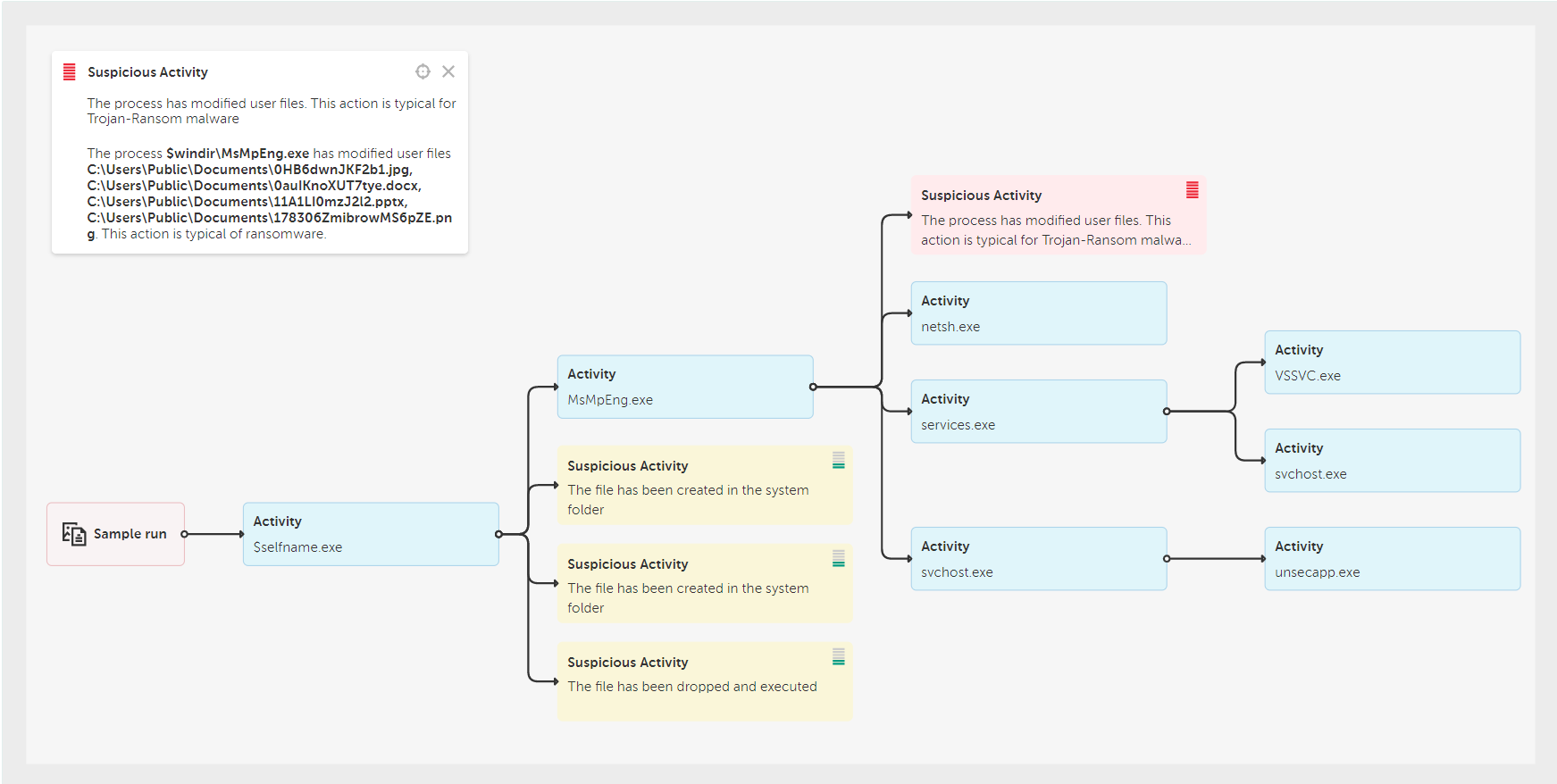
REvil ransomware attack against MSPs and its clients around the

Unusual Activity Detection – Identifying and Flagging Security

Malware Analysis: Steps & Examples - CrowdStrike
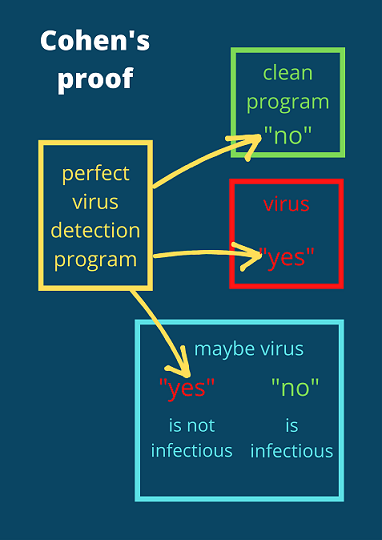
The real reason why malware detection is hard
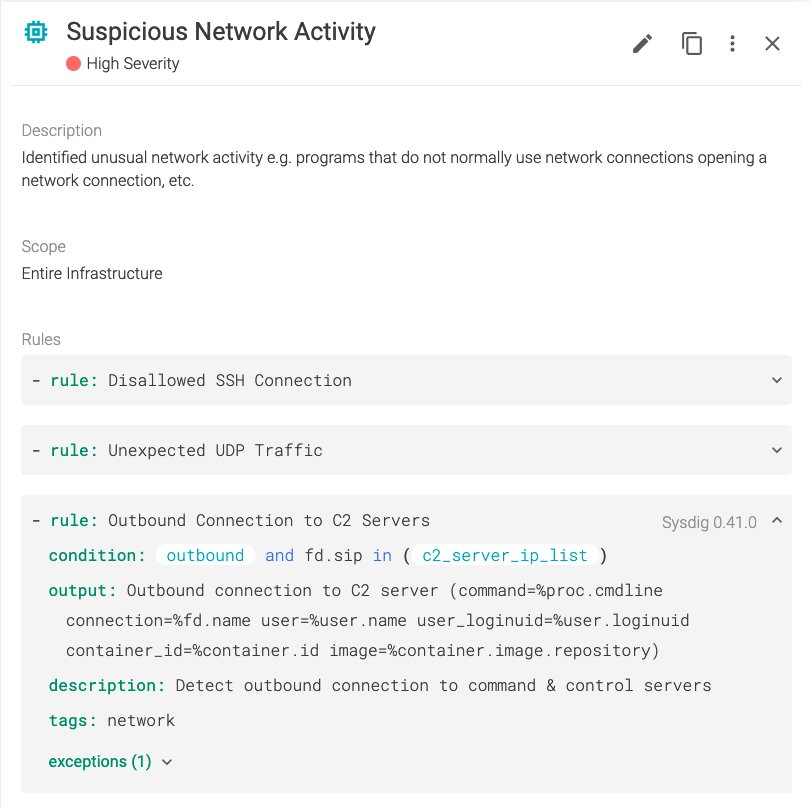
Malware analysis: Hands-On Shellbot malware – Sysdig

Malware Analysis Benefits Incident Response

How to Detect New Threats via Suspicious Activities
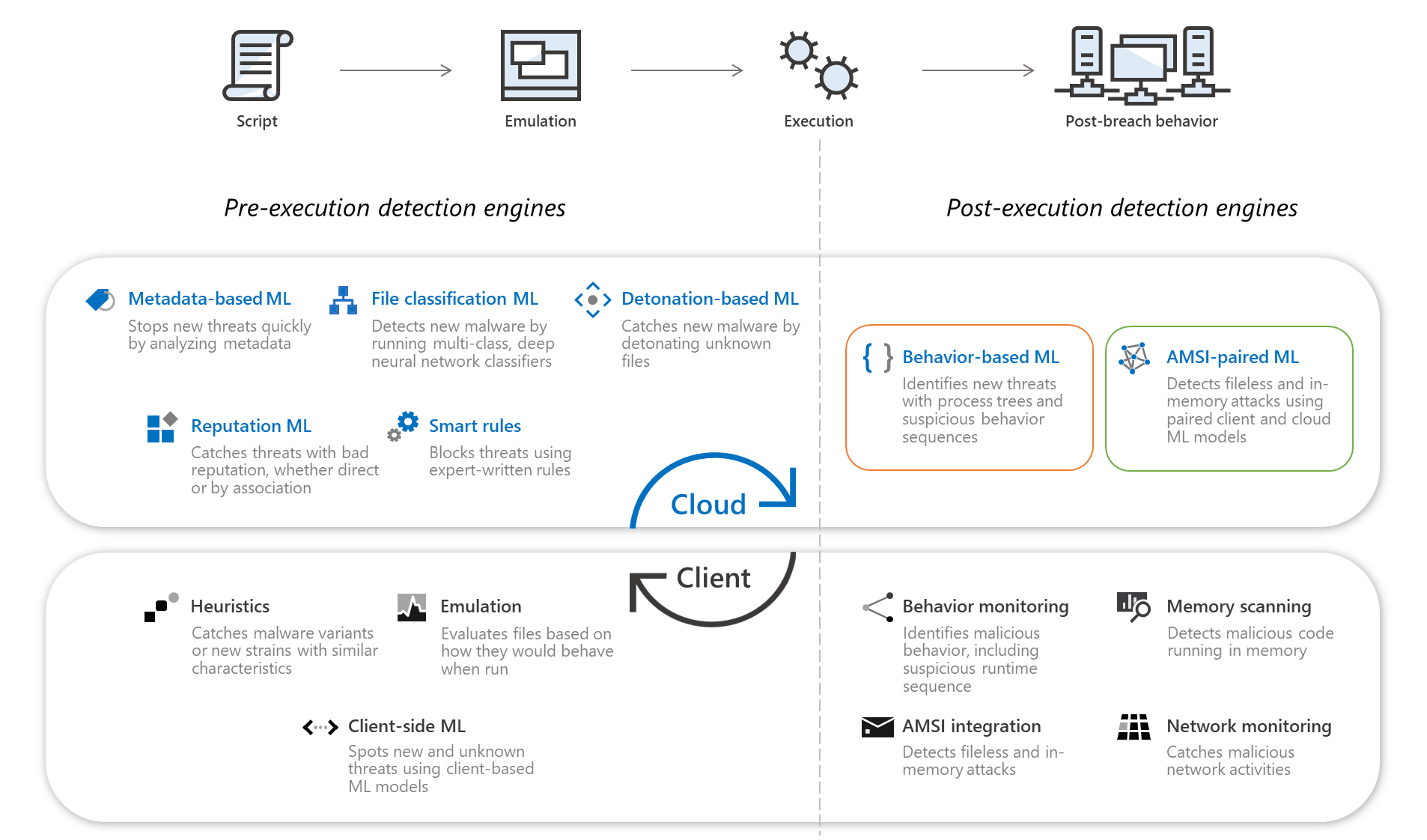
Client behavioral blocking
Recomendado para você
-
 Roblox Executor Patched, Latest Bypass Byfron25 abril 2025
Roblox Executor Patched, Latest Bypass Byfron25 abril 2025 -
 Roblox Virus - Malware removal instructions (updated)25 abril 2025
Roblox Virus - Malware removal instructions (updated)25 abril 2025 -
 Hack Week 2022: Putting Our Values into Action - Roblox Blog25 abril 2025
Hack Week 2022: Putting Our Values into Action - Roblox Blog25 abril 2025 -
 Jailbreak - Roblox25 abril 2025
Jailbreak - Roblox25 abril 2025 -
 Zeus S Executor Free, Zeus S Roblox Script 202325 abril 2025
Zeus S Executor Free, Zeus S Roblox Script 202325 abril 2025 -
 Download roblox hack25 abril 2025
Download roblox hack25 abril 2025 -
 Hack~ Roblox 64 (Nintendo 64) · RetroAchievements25 abril 2025
Hack~ Roblox 64 (Nintendo 64) · RetroAchievements25 abril 2025 -
 Roblox hack 2023 download25 abril 2025
Roblox hack 2023 download25 abril 2025 -
 Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire25 abril 2025
Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire25 abril 2025 -
 Roblox: The Movie (2014) - IMDb25 abril 2025
Roblox: The Movie (2014) - IMDb25 abril 2025
você pode gostar
-
format(webp)) Descubra mais animes dublados com a nova interface de dublagens da Crunchyroll - Crunchyroll Notícias25 abril 2025
Descubra mais animes dublados com a nova interface de dublagens da Crunchyroll - Crunchyroll Notícias25 abril 2025 -
 Isekai Babies in Another World. Conception Anime Review – LegendAqua25 abril 2025
Isekai Babies in Another World. Conception Anime Review – LegendAqua25 abril 2025 -
![Fansub Review: [gg] Code Geass: Akito the Exiled (Episode 01) –](https://i0.wp.com/crymore.net/wp-content/uploads/2012/10/gg_Code_Geass_Akito_the_Exiled_-_01_B785F404.mkv_snapshot_07.36_2012.10.01_15.45.47.jpg) Fansub Review: [gg] Code Geass: Akito the Exiled (Episode 01) –25 abril 2025
Fansub Review: [gg] Code Geass: Akito the Exiled (Episode 01) –25 abril 2025 -
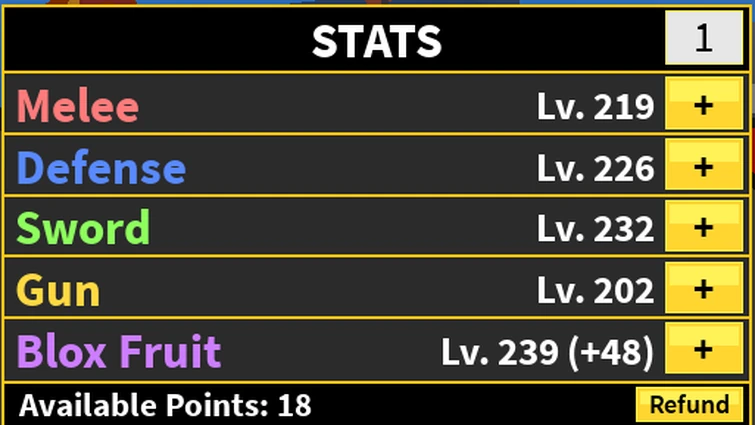
rate my stats (1-10)25 abril 2025
-
 Wesley's Substack, Wesley Sousa25 abril 2025
Wesley's Substack, Wesley Sousa25 abril 2025 -
 FIDE Certificate25 abril 2025
FIDE Certificate25 abril 2025 -
 Decided to play Gacha Life on roblox. This is the first thing I've seen. : r/GachaLifeCringe25 abril 2025
Decided to play Gacha Life on roblox. This is the first thing I've seen. : r/GachaLifeCringe25 abril 2025 -
 Another word for MISTAKE > Synonyms & Antonyms25 abril 2025
Another word for MISTAKE > Synonyms & Antonyms25 abril 2025 -
 Download do APK de Jogos De Corte De Cabelo De Meninas para Android25 abril 2025
Download do APK de Jogos De Corte De Cabelo De Meninas para Android25 abril 2025 -
 Let Go (Avril Lavigne album) - Wikipedia25 abril 2025
Let Go (Avril Lavigne album) - Wikipedia25 abril 2025