Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Last updated 13 abril 2025

[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]

Cyber Security News on LinkedIn: Incident Response
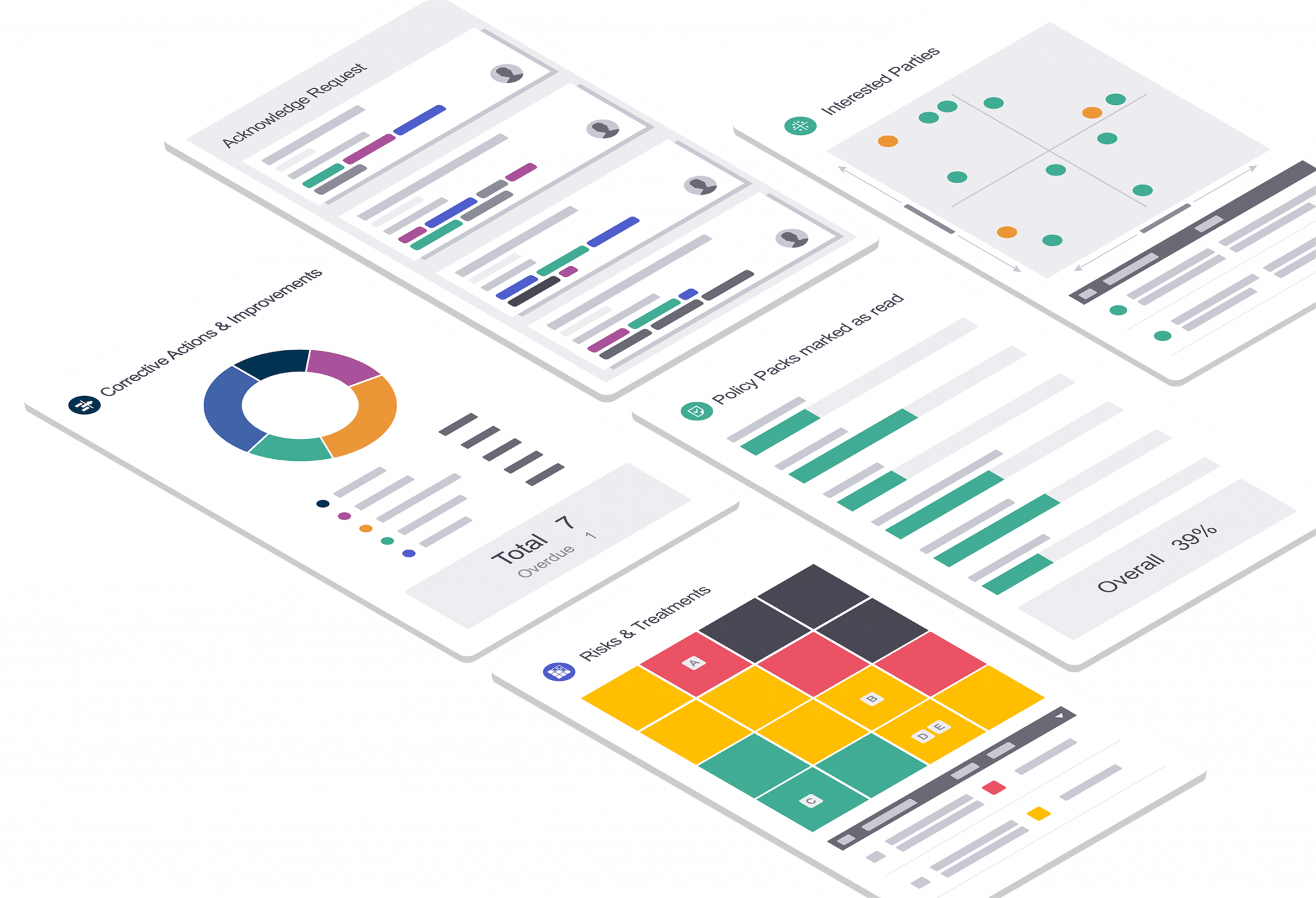
Information Security Management System (Pre-configured ISMS) Solution

The Chief Information Security Officer (CISO) Role Explained – BMC

A Comprehensive Guide to Managed Detection and Response (MDR

The Top 25 Cybersecurity Companies of 2021

Table 1 from Isfam: the Information Security Focus Area Maturity

CIS Critical Security Control 17: Incident Response and Management

Information Security Plan: Examples & Incident Response

NIST Incident Response: Your Go-To Guide to Handling Cybersecurity
Recomendado para você
-
 Learning from Incidents Questionnaire (LFIQ): The validation of an13 abril 2025
Learning from Incidents Questionnaire (LFIQ): The validation of an13 abril 2025 -
 Incident Response Phases - Lessons Learned - Halkyn Security Blog13 abril 2025
Incident Response Phases - Lessons Learned - Halkyn Security Blog13 abril 2025 -
Why Lessons Learned Is The Most Critical Step In Incident Response13 abril 2025
-
 Safety Lessons Learned Template - Construction Documents And Templates13 abril 2025
Safety Lessons Learned Template - Construction Documents And Templates13 abril 2025 -
 Learning from Incidents13 abril 2025
Learning from Incidents13 abril 2025 -
 How to Share Learning From Incidents13 abril 2025
How to Share Learning From Incidents13 abril 2025 -
 Embrace Mistakes to Build a Learning Culture13 abril 2025
Embrace Mistakes to Build a Learning Culture13 abril 2025 -
 Learning lessons from cyber security incidents13 abril 2025
Learning lessons from cyber security incidents13 abril 2025 -
 What is an Incident Response Plan and How to Create One13 abril 2025
What is an Incident Response Plan and How to Create One13 abril 2025 -
 collaboration13 abril 2025
collaboration13 abril 2025
você pode gostar
-
 Freestyle 2: projetor da Samsung agora tem suporte a jogos na nuvem - Olhar Digital13 abril 2025
Freestyle 2: projetor da Samsung agora tem suporte a jogos na nuvem - Olhar Digital13 abril 2025 -
Enderman Farm Hypixel Forums13 abril 2025
-
 Power Scaling in Anime: Can We Measure The Strength Of Anime Characters (Naruto Explained Guest Post) - Sequential Planet13 abril 2025
Power Scaling in Anime: Can We Measure The Strength Of Anime Characters (Naruto Explained Guest Post) - Sequential Planet13 abril 2025 -
Awkwafina is Nora From Queens — Heidi Unkefer13 abril 2025
-
 Throwback Thursdays: Darker Than Black – Beneath the Tangles13 abril 2025
Throwback Thursdays: Darker Than Black – Beneath the Tangles13 abril 2025 -
 Kidderminster Harriers FC vs Altrincham FC: Live Score, Stream and H2H results 3/29/2024. Preview match Kidderminster Harriers FC vs Altrincham FC, team, start time.13 abril 2025
Kidderminster Harriers FC vs Altrincham FC: Live Score, Stream and H2H results 3/29/2024. Preview match Kidderminster Harriers FC vs Altrincham FC, team, start time.13 abril 2025 -
 Sigma 🍷🗿 : r/animebrasil13 abril 2025
Sigma 🍷🗿 : r/animebrasil13 abril 2025 -
 Boneca Bebê Reborn Realista De Silicone Original Grande13 abril 2025
Boneca Bebê Reborn Realista De Silicone Original Grande13 abril 2025 -
 Modelos de Garagem: +70 Ideias para Fazer na Sua Casa dos Sonhos13 abril 2025
Modelos de Garagem: +70 Ideias para Fazer na Sua Casa dos Sonhos13 abril 2025 -
 The Devil Is A Part Timer, Wiki13 abril 2025
The Devil Is A Part Timer, Wiki13 abril 2025
