Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Last updated 14 abril 2025

The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…
Offensive Security Training - Applied Technology Academy

Low cost 3D printing of metals using filled polymer pellets - ScienceDirect
Pentesting CI/CD Methodology - HackTricks Cloud
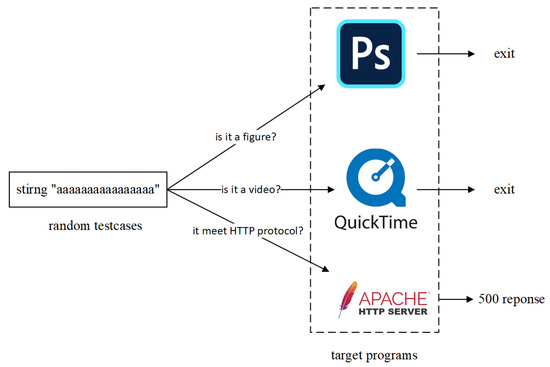
Electronics, Free Full-Text

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles

T1202: Indirect Command Execution - Red Team Notes 2.0
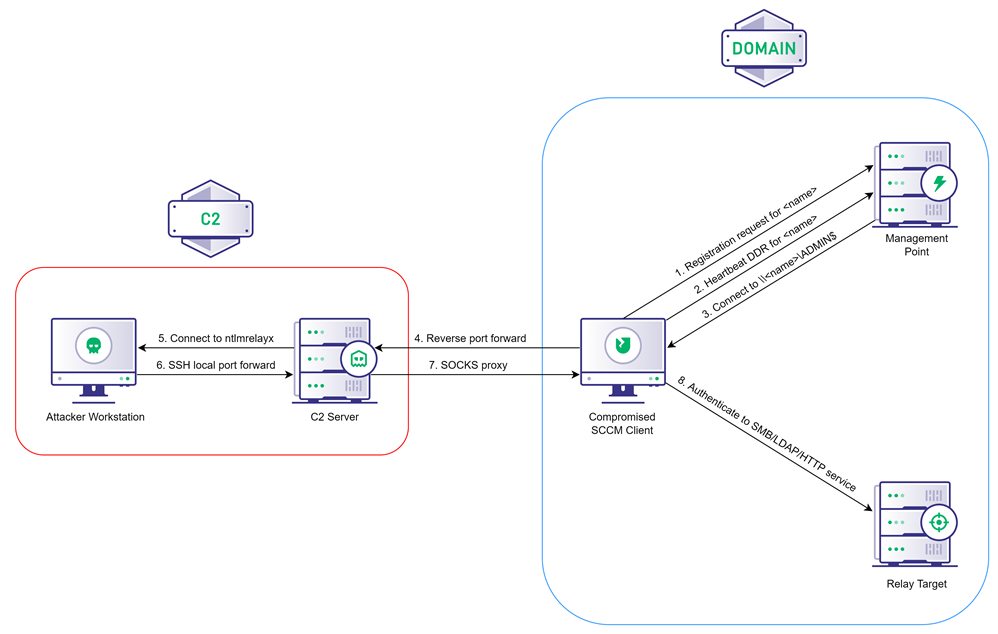
Coercing NTLM Authentication from SCCM, by Chris Thompson
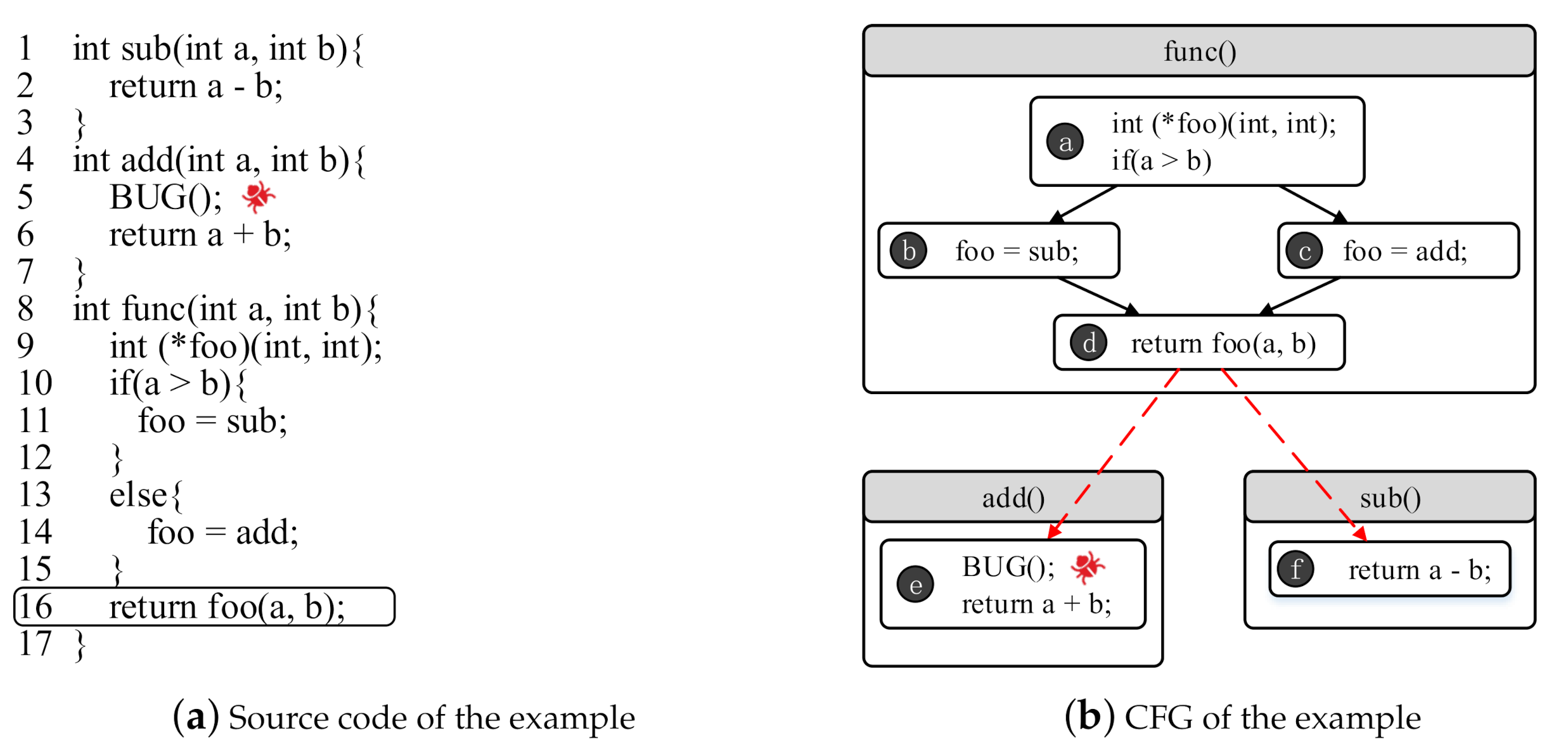
Applied Sciences, Free Full-Text

Windows Print Spooler RCE Vulnerabilities (CVE-2021-1675/CVE-2021-34527) Mitigation Guide - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Indirect Command Execution – Penetration Testing Lab
PentesterLab: Learn Web App Pentesting!

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
Linux Hacking Case Studies Part 3: phpMyAdmin

Kali Linux Web Penetration Testing Cookbook
Basic Penetration testing lab — 1 – Sahil Ahamad - Information Security Blog – Product Security at Facebook
Recomendado para você
-
 administrator - Force cmd.exe prompt to run NOT as admin - Super User14 abril 2025
administrator - Force cmd.exe prompt to run NOT as admin - Super User14 abril 2025 -
 Executing Command Prompt commands in SSIS – SQL Server Rider14 abril 2025
Executing Command Prompt commands in SSIS – SQL Server Rider14 abril 2025 -
 How to Run Program from CMD (Command Prompt) Windows 10 - MiniTool14 abril 2025
How to Run Program from CMD (Command Prompt) Windows 10 - MiniTool14 abril 2025 -
![Fix] Cannot Run Programs Without Typing the Extension (.EXE) in Command Prompt » Winhelponline](https://www.winhelponline.com/blog/wp-content/uploads/2016/07/pathext-fix-1.png) Fix] Cannot Run Programs Without Typing the Extension (.EXE) in Command Prompt » Winhelponline14 abril 2025
Fix] Cannot Run Programs Without Typing the Extension (.EXE) in Command Prompt » Winhelponline14 abril 2025 -
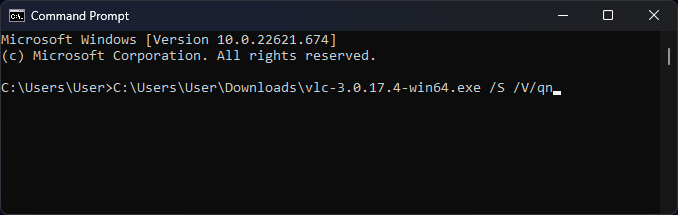 Unattended Installation - How to Silently Install your EXE using PowerShell & CMD?14 abril 2025
Unattended Installation - How to Silently Install your EXE using PowerShell & CMD?14 abril 2025 -
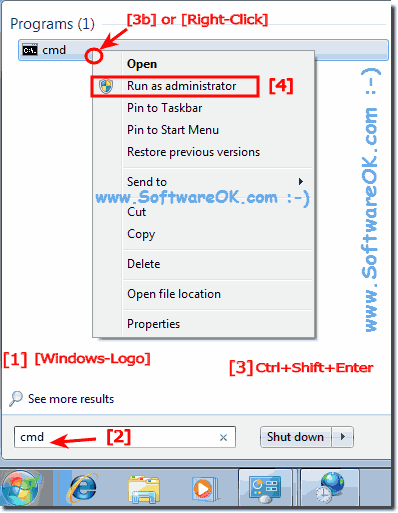 Start the Windows 7 cmd.exe in administrator mode?14 abril 2025
Start the Windows 7 cmd.exe in administrator mode?14 abril 2025 -
How to fix problem security protect running .exe and .cmd - Microsoft Q&A14 abril 2025
-
 run.exe Windows process - What is it?14 abril 2025
run.exe Windows process - What is it?14 abril 2025 -
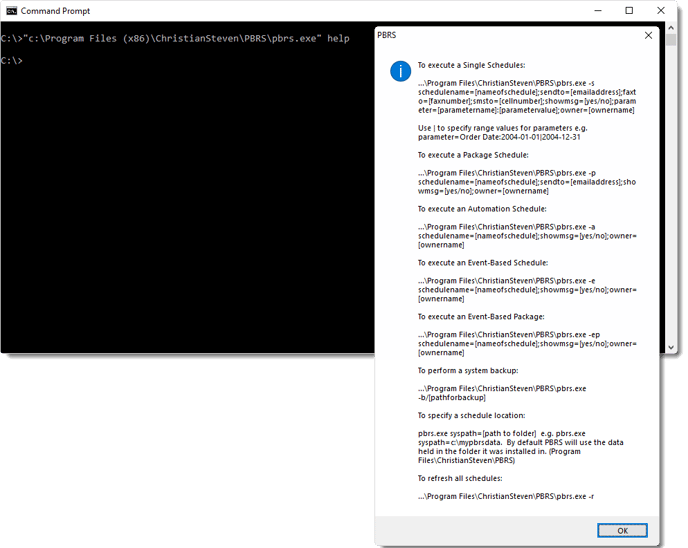 How do I use Command Line Options in PBRS?14 abril 2025
How do I use Command Line Options in PBRS?14 abril 2025 -
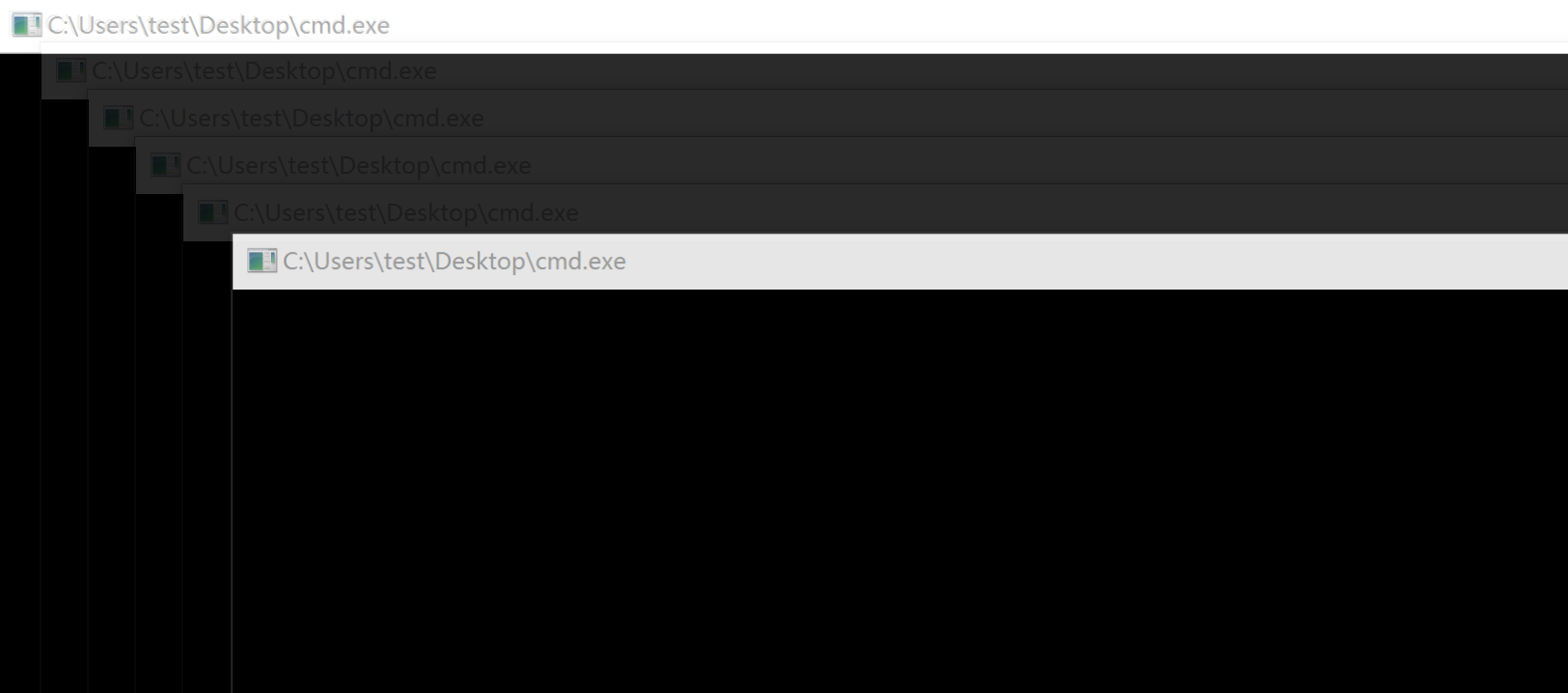 Something strange happend when I used process::Command to execute cmd - help - The Rust Programming Language Forum14 abril 2025
Something strange happend when I used process::Command to execute cmd - help - The Rust Programming Language Forum14 abril 2025
você pode gostar
-
 Brinquedo De Brincar Pj Pug-a-pillar E Bunzo Bunny Poppy De14 abril 2025
Brinquedo De Brincar Pj Pug-a-pillar E Bunzo Bunny Poppy De14 abril 2025 -
 memes that make no sense Memes & GIFs - Imgflip14 abril 2025
memes that make no sense Memes & GIFs - Imgflip14 abril 2025 -
 Tate no Yuusha no Nariagari (The Rising of the Shield Hero14 abril 2025
Tate no Yuusha no Nariagari (The Rising of the Shield Hero14 abril 2025 -
 A mí me hizo llorar piggy de roblox XD - Meme by KyoRetro2 :) Memedroid14 abril 2025
A mí me hizo llorar piggy de roblox XD - Meme by KyoRetro2 :) Memedroid14 abril 2025 -
 True Love (tradução) - SOJA (Soldiers of Jah Army) - VAGALUME14 abril 2025
True Love (tradução) - SOJA (Soldiers of Jah Army) - VAGALUME14 abril 2025 -
 About us14 abril 2025
About us14 abril 2025 -
 Inaho Kaizuka - Aldnoah Zero - Anime Characters Database Character design inspiration, Anime characters, Character design references14 abril 2025
Inaho Kaizuka - Aldnoah Zero - Anime Characters Database Character design inspiration, Anime characters, Character design references14 abril 2025 -
 Rumor - Bloodborne: Endless Nocturne, Page 314 abril 2025
Rumor - Bloodborne: Endless Nocturne, Page 314 abril 2025 -
 anime oof sound effect|TikTok Search14 abril 2025
anime oof sound effect|TikTok Search14 abril 2025 -
 Mais de 6.000 vídeos grátis em HD e 4K de Wallpaper e Natureza14 abril 2025
Mais de 6.000 vídeos grátis em HD e 4K de Wallpaper e Natureza14 abril 2025