Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace
Por um escritor misterioso
Last updated 25 abril 2025

In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.
GitHub - goldenscale/GS_GithubMirror: A Github Mirror List For GS Star Repository

First update to the RxSwift book with version 1.1 // rx_marin

An iOS zero-click radio proximity exploit odyssey - Project Zero
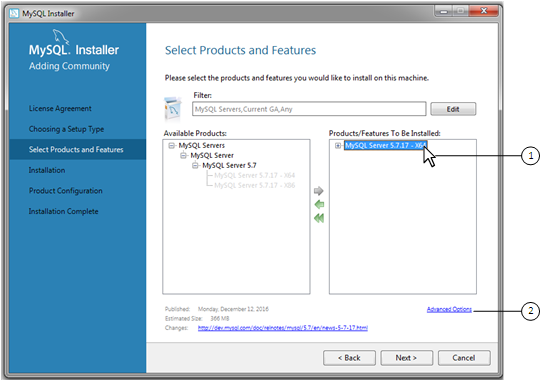
Chapter 2 Installing and Upgrading MySQL

CONFidence 2015: DTrace + OSX = Fun - Andrzej Dyjak

Evolution of the Unix System Architecture: An Exploratory Case Study

CONFidence 2015: DTrace + OSX = Fun - Andrzej Dyjak
Reverse Engineering x64 for Beginners - Windows - Checkmate

Chapter 2 Installing and Upgrading MySQL
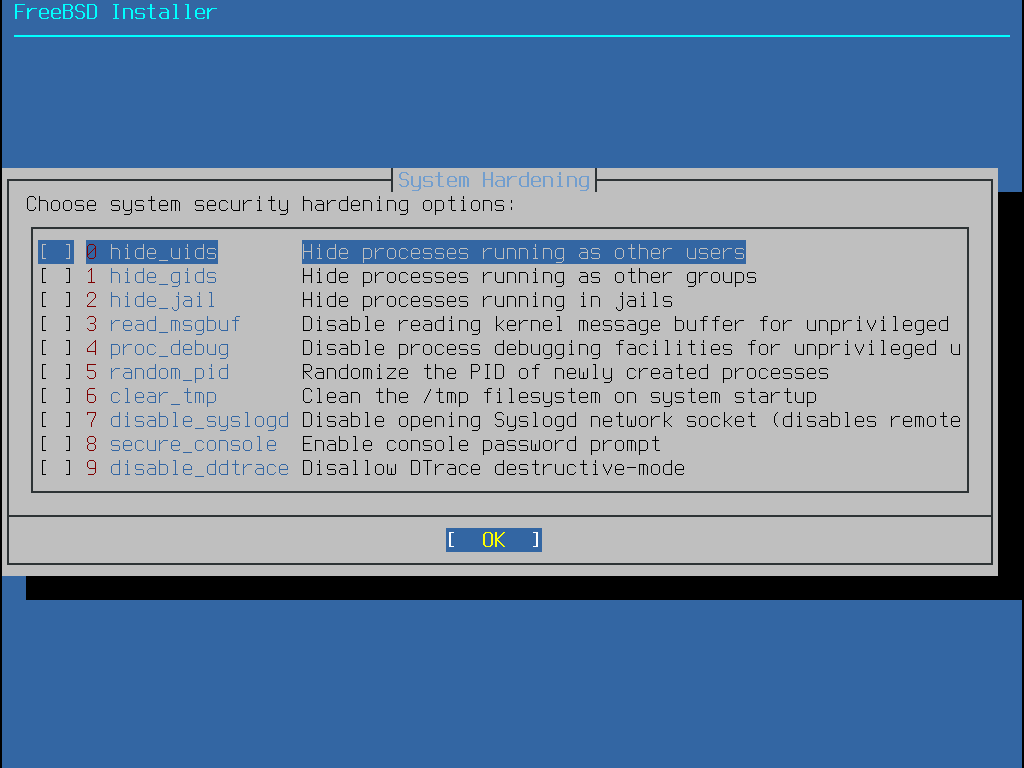
FreeBSD Handbook FreeBSD Documentation Portal

Tampering and Reverse Engineering on iOS - OWASP MASTG
Recomendado para você
-
 PLS DONATE Codes (December 2023) - Roblox25 abril 2025
PLS DONATE Codes (December 2023) - Roblox25 abril 2025 -
 Roblox: Strong Muscle Simulator Codes25 abril 2025
Roblox: Strong Muscle Simulator Codes25 abril 2025 -
BuxBack - Earn R$25 abril 2025
-
New Pet Concept25 abril 2025
-
My Entertainment (@MyEntertainmet_) / X25 abril 2025
-
 RPS_Leaks - Pet Simulator Leaks☁️ on X: New Pets Cat Ruby, Monkey Emerald ,Dragon Amethyst , Corgi Mystic View Thread (2) for a better view of the pets #PetSimulatorX /25 abril 2025
RPS_Leaks - Pet Simulator Leaks☁️ on X: New Pets Cat Ruby, Monkey Emerald ,Dragon Amethyst , Corgi Mystic View Thread (2) for a better view of the pets #PetSimulatorX /25 abril 2025 -
Cute Baby Face Roblox Item - Rolimon's25 abril 2025
-
 Seed Junky Home25 abril 2025
Seed Junky Home25 abril 2025 -
rbx gum en discord|TikTok Search25 abril 2025
-
 Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend25 abril 2025
Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend25 abril 2025
você pode gostar
-
Aventuras Narradas25 abril 2025
-
 Mario Kart Tour 'breaks mobile game launch record25 abril 2025
Mario Kart Tour 'breaks mobile game launch record25 abril 2025 -
 List of Naruto Shippuden Anime Episodes25 abril 2025
List of Naruto Shippuden Anime Episodes25 abril 2025 -
 Download Iori Yagami, Street Fighter V Wallpaper25 abril 2025
Download Iori Yagami, Street Fighter V Wallpaper25 abril 2025 -
 Nerf Roblox Viper Strike Hasbro F5483 - Juguetilandia25 abril 2025
Nerf Roblox Viper Strike Hasbro F5483 - Juguetilandia25 abril 2025 -
 Baki manga panel colored 2 (Yuhiro vs Baki) by GoldenPaint12 on25 abril 2025
Baki manga panel colored 2 (Yuhiro vs Baki) by GoldenPaint12 on25 abril 2025 -
 What do I want to be when I grow up? : r/pokemon25 abril 2025
What do I want to be when I grow up? : r/pokemon25 abril 2025 -
![ONE PIECE Devil Fruit Room Light -Op-Op Fruit- [BANPRESTO]](https://trader-akiba.com/cdn/shop/files/IMG_1996_800x.jpg?v=1696057317) ONE PIECE Devil Fruit Room Light -Op-Op Fruit- [BANPRESTO]25 abril 2025
ONE PIECE Devil Fruit Room Light -Op-Op Fruit- [BANPRESTO]25 abril 2025 -
Forever 21, Teen-Focused Retailer, Files for Bankruptcy - WSJ25 abril 2025
-
 Suárez joga: veja escalação do Grêmio no jogo contra o São Luiz25 abril 2025
Suárez joga: veja escalação do Grêmio no jogo contra o São Luiz25 abril 2025