SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 26 abril 2025

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 17 March 2023

Chinese Hackers Use New Cryptojacking Tactics to Evade Detection

Malware - Wikipedia

Telerik exploitation. Cloud storage re-up attacks. Phishing tackle. Cyber developments in Russia's hybrid war.

DAILY NEWS: Março (12/03 - 18/03) - 11 Semana de 2023
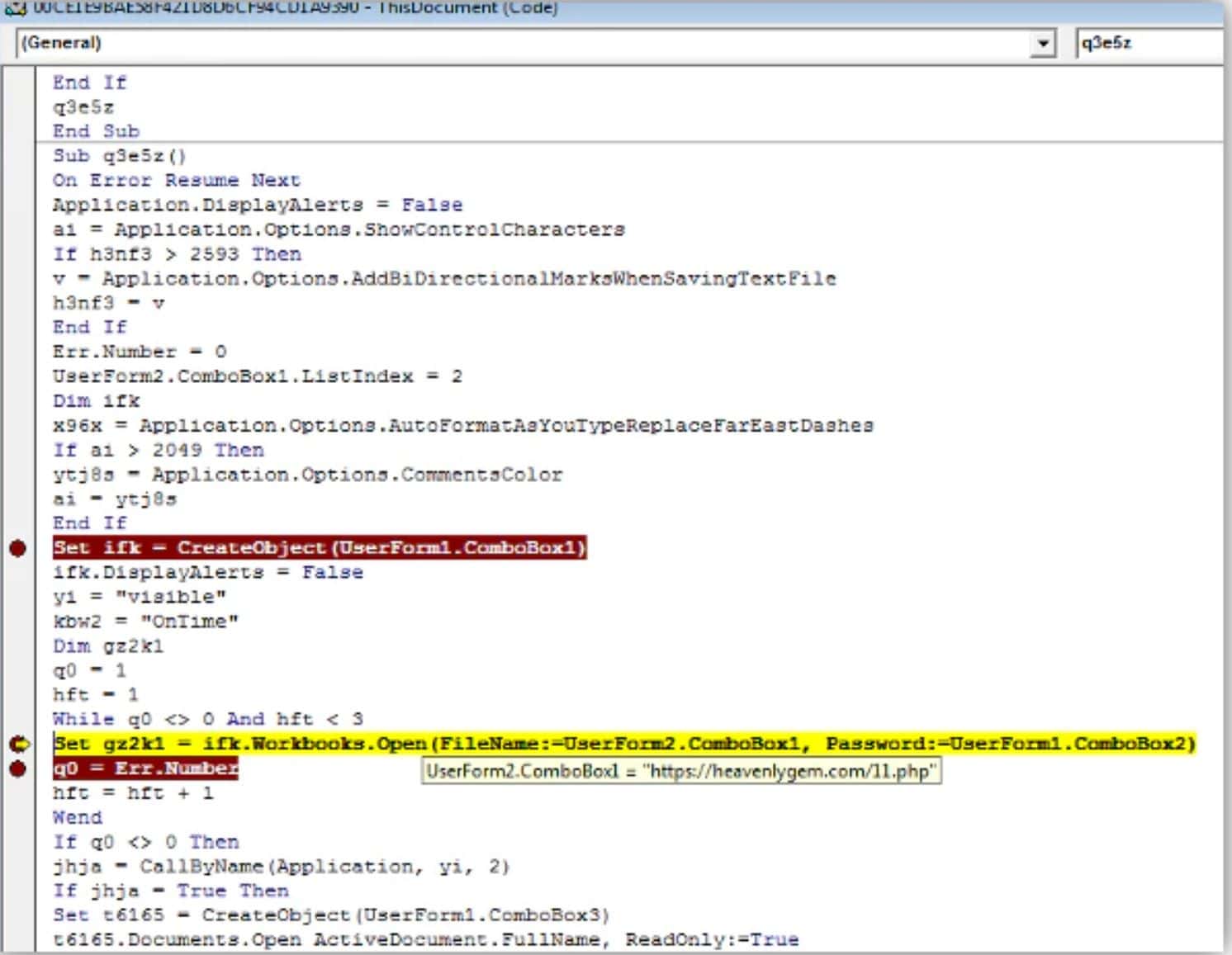
How Hackers Evade Detection

Lynx-CERT

Cyber Security for Critical Infrastructure Protection - SCADAhacker

Lynx-CERT

1-15 March 2023 Cyber Attacks Timeline – HACKMAGEDDON
Chinese hackers use new custom backdoor to evade detection
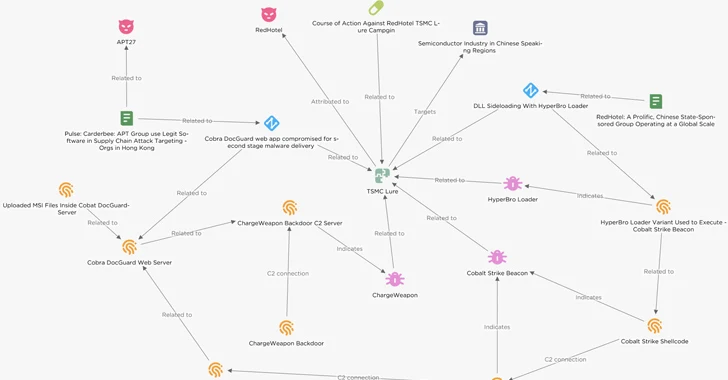
Cobalt Strike, Breaking Cybersecurity News
Recomendado para você
-
![Evade [AutoRespawn, Esp] Scripts](https://rbxscript.com/images/-KAgv5dirUs-image.jpg) Evade [AutoRespawn, Esp] Scripts26 abril 2025
Evade [AutoRespawn, Esp] Scripts26 abril 2025 -
 Evade Script Pastebin - Anti Next Bot, ESP & More26 abril 2025
Evade Script Pastebin - Anti Next Bot, ESP & More26 abril 2025 -
 NEW Evade Script GUI Hack OP (AUTOFARM, AUTO SPRINT, TELEPORTS26 abril 2025
NEW Evade Script GUI Hack OP (AUTOFARM, AUTO SPRINT, TELEPORTS26 abril 2025 -
 Evade Script Auto Farm Wins, Auto Random Vote & MORE26 abril 2025
Evade Script Auto Farm Wins, Auto Random Vote & MORE26 abril 2025 -
Snippet of Server-side script generated by ChatGPT to evade26 abril 2025
-
 2 Late 2 Evade by Script Idea26 abril 2025
2 Late 2 Evade by Script Idea26 abril 2025 -
 New ESXiArgs ransomware variant can evade CISA's recovery script26 abril 2025
New ESXiArgs ransomware variant can evade CISA's recovery script26 abril 2025 -
evade script delta|TikTok Search26 abril 2025
-
evade script template|TikTok Search26 abril 2025
-
 Evade Script GUI (God mode, bhop & Others)! – TGN Scripts26 abril 2025
Evade Script GUI (God mode, bhop & Others)! – TGN Scripts26 abril 2025
você pode gostar
-
 ✓(ATUALIZADO) como baixar e instalar directx 12 202326 abril 2025
✓(ATUALIZADO) como baixar e instalar directx 12 202326 abril 2025 -
 THE 5 BEST Pittsburgh Escape Rooms (Updated 2023) - Tripadvisor26 abril 2025
THE 5 BEST Pittsburgh Escape Rooms (Updated 2023) - Tripadvisor26 abril 2025 -
 Tim Horton Meets Wayne Gretzky in Touching New Ad26 abril 2025
Tim Horton Meets Wayne Gretzky in Touching New Ad26 abril 2025 -
 Youtooz Drops 'TrollFace' Figures26 abril 2025
Youtooz Drops 'TrollFace' Figures26 abril 2025 -
 Pokemon Pou Emo26 abril 2025
Pokemon Pou Emo26 abril 2025 -
Maze Runner26 abril 2025
-
 Camisa do Flamengo I Feminina 23/24- a partir de 159,90- Frete Grátis26 abril 2025
Camisa do Flamengo I Feminina 23/24- a partir de 159,90- Frete Grátis26 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2022/i/i/FLF2ILT9eExXywwKfXNA/valorant-pearl-new-map-layout-release-date-scaled-e1655486515836.jpg) Atualização de Valorant traz Episódio 5, novo mapa Pearl e mais26 abril 2025
Atualização de Valorant traz Episódio 5, novo mapa Pearl e mais26 abril 2025 -
 The Stormlight Archive - Wikipedia26 abril 2025
The Stormlight Archive - Wikipedia26 abril 2025 -
 Dicas Xadrez: O 5 mandamentos do xadrez de Yasser Seirawan26 abril 2025
Dicas Xadrez: O 5 mandamentos do xadrez de Yasser Seirawan26 abril 2025


