SSH Passwd, PDF, Cyberwarfare
Por um escritor misterioso
Last updated 14 abril 2025


Xiologix Security overview - Tualatin, Oregon, United States of America
100 Security Operation Center Tools.pdf

The Anomali Blog

Darkmatter Cyber Security Report June 2019, PDF, Computer Security

New Go-written GobRAT RAT targets Linux Routers in Japan
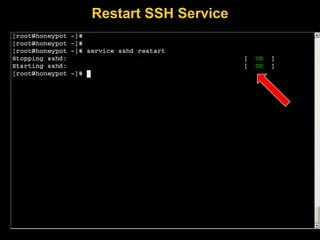
Honeypots in Cyberwar

PDF) Teaching pentesting to social sciences students using experiential learning techniques to improve attitudes towards possible cybersecurity careers

How to configure SSH access through Webmin
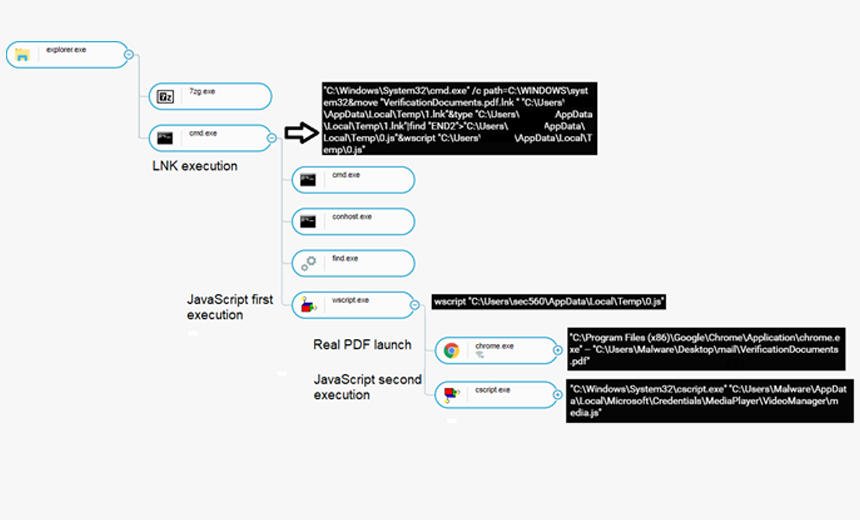
Evilnum Hackers Change Tactics for Targeting Fintech Firms

CyberArk Interview.pdf
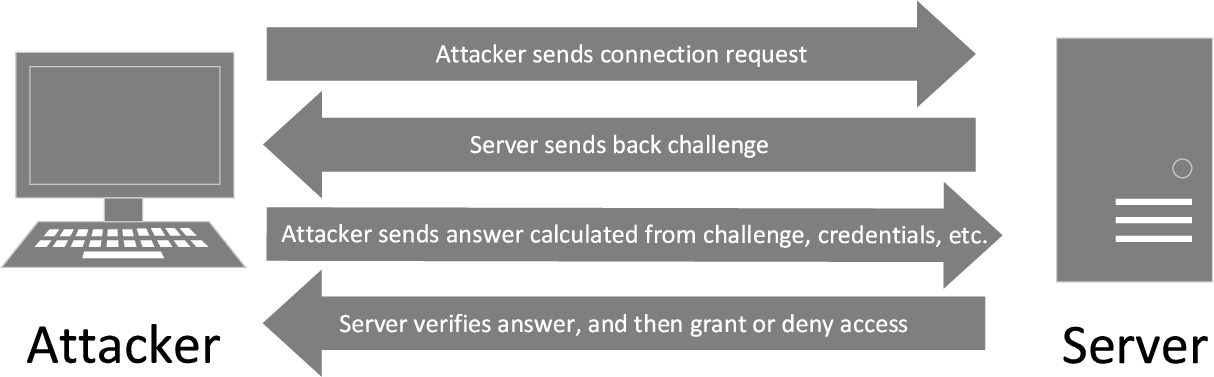
Deep learning for detecting logic-flaw-exploiting network attacks: An end-to-end approach - IOS Press

Implications of Misuse and Cyber Security.pdf
Recomendado para você
-
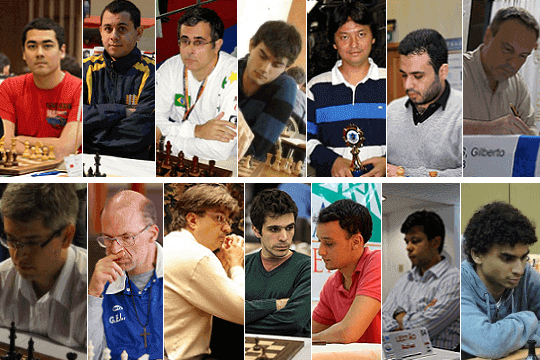 Os 14 Grandes Mestres de Xadrez Brasileiros14 abril 2025
Os 14 Grandes Mestres de Xadrez Brasileiros14 abril 2025 -
 MF Julia Alboredo e GM Supi jogam contra RAFFAEL CHESS juntos!!14 abril 2025
MF Julia Alboredo e GM Supi jogam contra RAFFAEL CHESS juntos!!14 abril 2025 -
 GM Supi jogou JUNTO COM a WIM Julia Alboredo e fizeram O MESTRE MANDOU no xadrez!14 abril 2025
GM Supi jogou JUNTO COM a WIM Julia Alboredo e fizeram O MESTRE MANDOU no xadrez!14 abril 2025 -
Luis Paulo Supi Melhores Jogadores de Xadrez14 abril 2025
-
 GM Luis Paulo Supi (LPSupi) - Chess Profile14 abril 2025
GM Luis Paulo Supi (LPSupi) - Chess Profile14 abril 2025 -
brute-dict/pass.100000 at master · santatic/brute-dict · GitHub14 abril 2025
-
 Xadrez Vencedor: 201014 abril 2025
Xadrez Vencedor: 201014 abril 2025 -
 Calaméo - Regional 83914 abril 2025
Calaméo - Regional 83914 abril 2025 -
 Revista n°189 JAN 2014 by Esporte Clube Pinheiros - Issuu14 abril 2025
Revista n°189 JAN 2014 by Esporte Clube Pinheiros - Issuu14 abril 2025 -
 Xadrez Verbal Podcast #322 – América Latina, Europa e Oriente Médio14 abril 2025
Xadrez Verbal Podcast #322 – América Latina, Europa e Oriente Médio14 abril 2025
você pode gostar
-
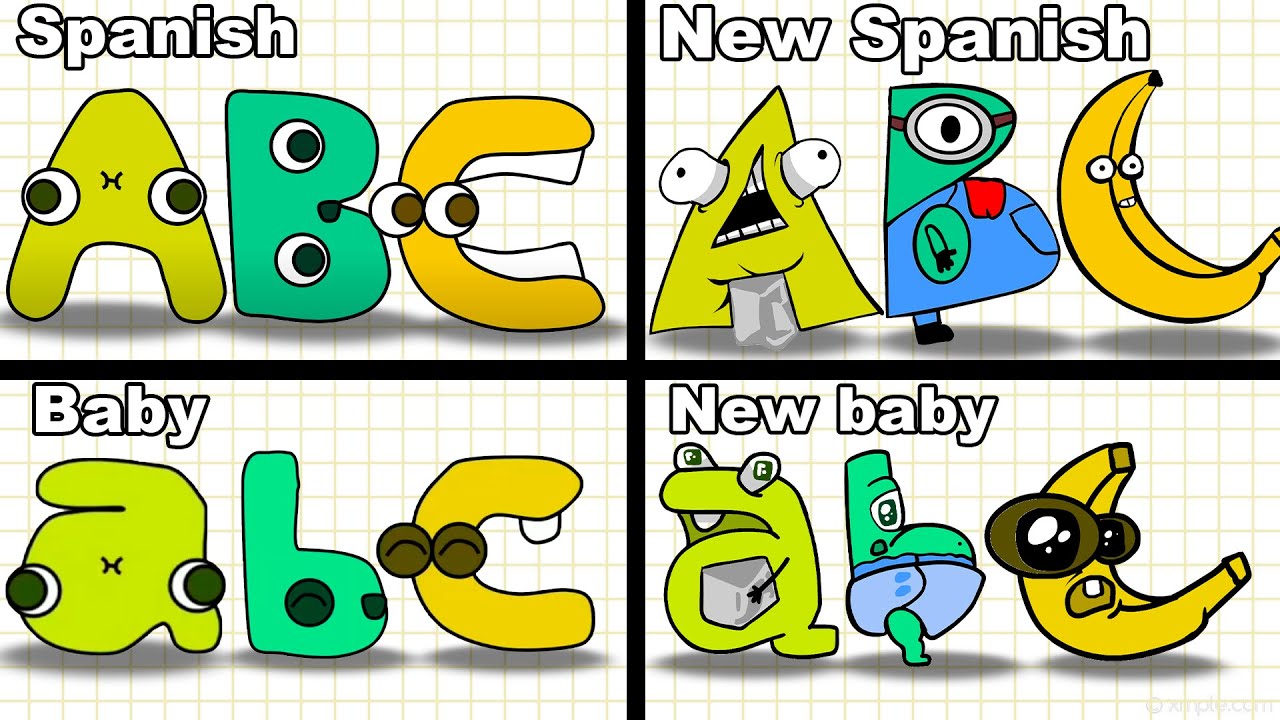 Different Spanish Alphabet Lore (Full Version A-Z)14 abril 2025
Different Spanish Alphabet Lore (Full Version A-Z)14 abril 2025 -
 Janela de Abrir Guilhotina de Madeira Imbuia - Reta - Galo14 abril 2025
Janela de Abrir Guilhotina de Madeira Imbuia - Reta - Galo14 abril 2025 -
 Street Fighter II (manga) - Wikipedia14 abril 2025
Street Fighter II (manga) - Wikipedia14 abril 2025 -
 Volvo FMX 460 6x6, Euro 6, Unused14 abril 2025
Volvo FMX 460 6x6, Euro 6, Unused14 abril 2025 -
Ludo Multiplayer – Apps no Google Play14 abril 2025
-
/i.s3.glbimg.com/v1/AUTH_e84042ef78cb4708aeebdf1c68c6cbd6/internal_photos/bs/2023/Q/U/hucrpgSbmlj659YWALYw/falando-no-grupo-as-outras-vocalistas-do-rbd-anahi-e-dulce-maria-ja-deram-os-parabens-para-a-amiga-nas-redes-sociais.png) Maite Perrone anuncia gravidez, Somos três14 abril 2025
Maite Perrone anuncia gravidez, Somos três14 abril 2025 -
 Here's When Moltres And Zapdos Are Coming To 'Pokémon GO' (And14 abril 2025
Here's When Moltres And Zapdos Are Coming To 'Pokémon GO' (And14 abril 2025 -
 Heaven Background 4 PNG Memorial Background Stairs to Heaven Heaven Memorial Background Memorial Design PNG&JPG Instant Download14 abril 2025
Heaven Background 4 PNG Memorial Background Stairs to Heaven Heaven Memorial Background Memorial Design PNG&JPG Instant Download14 abril 2025 -
 File:Akatsuki clouds shiny tiles texture.png - Wikimedia Commons14 abril 2025
File:Akatsuki clouds shiny tiles texture.png - Wikimedia Commons14 abril 2025 -
 Football Tradition - Kansas State University Athletics14 abril 2025
Football Tradition - Kansas State University Athletics14 abril 2025