Secure Code Warrior Integration
Por um escritor misterioso
Last updated 24 abril 2025
Developers can deliver secure code by connecting relevant Secure Code Warrior resources to the security vulnerabilities that are detected by a SAST tool — like Klocwork — running within their desktop tools or as part of the CI/CD pipelines. This makes software security an essential part of the software development life cycle. This tutorial explains how to set up and use the beneficial Secure Code Warrior integration.

Secure Code Warrior Reviews 2023: Details, Pricing, & Features

Klocwork + Secure Code Warrior Integration

The Best InfoSec Training Platforms in 2023 (Updated - July 2023)
Coverity Integration with Secure Code Warrior
GitHub - Contrast-Security-OSS/integrations-scw: Script to populate a Contrast environment with links to Secure Code Warrior videos and training exercises.
Okta SSO Configuration Guide – Secure Code Warrior
iTWire - Secure Code Warrior Courses helps devs write secure code
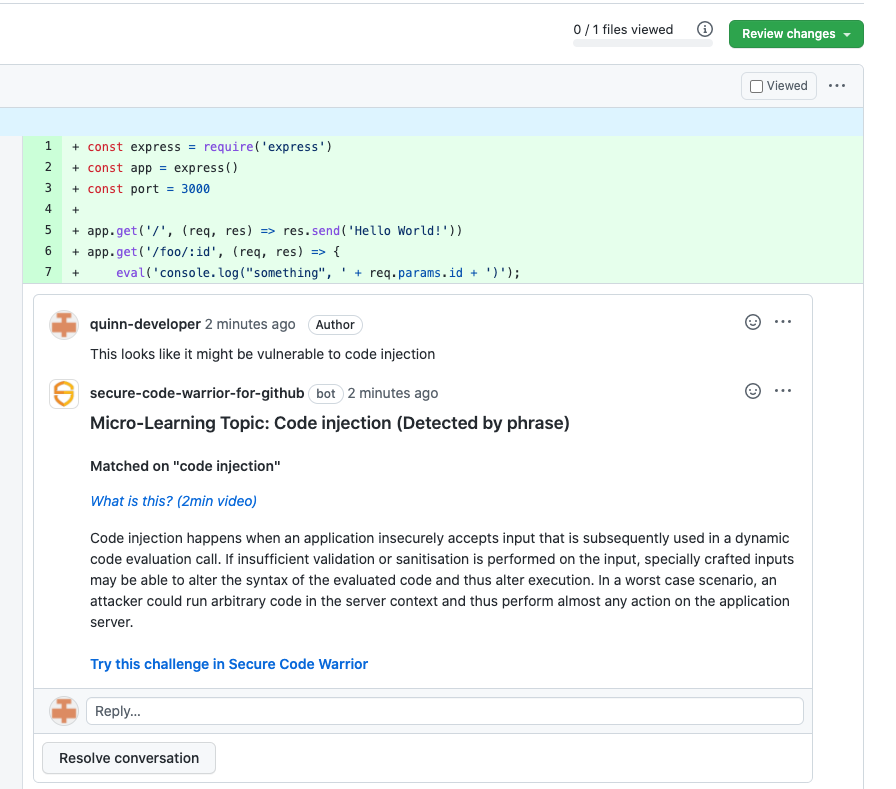
Secure Code Warrior for GitHub Issues and Pull Requests – Secure Code Warrior

Increase Developer Productivity

Competing priorities leave developers struggling to secure code

Create secure code with Secure Code Bootcamp - Rule of Tech
Recomendado para você
-
Warrior Software24 abril 2025
-
 Link to Warrior Software Downloads24 abril 2025
Link to Warrior Software Downloads24 abril 2025 -
 Field Warrior Mobile Workforce Management App24 abril 2025
Field Warrior Mobile Workforce Management App24 abril 2025 -
 CodeWarrior® for Microcontrollers-Classic IDE24 abril 2025
CodeWarrior® for Microcontrollers-Classic IDE24 abril 2025 -
 Secure Code Warrior lands $50M to educate developers on best cyber practices24 abril 2025
Secure Code Warrior lands $50M to educate developers on best cyber practices24 abril 2025 -
 Check Point Game of Clouds Cyber Range Warrior - Credly24 abril 2025
Check Point Game of Clouds Cyber Range Warrior - Credly24 abril 2025 -
 DiskWarrior Review: Is This Software Still Relevant in 2022?24 abril 2025
DiskWarrior Review: Is This Software Still Relevant in 2022?24 abril 2025 -
 Wounded Warrior Project Invites Streamers to Support Veterans During Warrior Week - Oct 30, 202324 abril 2025
Wounded Warrior Project Invites Streamers to Support Veterans During Warrior Week - Oct 30, 202324 abril 2025 -
 TrendSpider Software Update: New Indicator Release: TW Pivot by Theta Warrior24 abril 2025
TrendSpider Software Update: New Indicator Release: TW Pivot by Theta Warrior24 abril 2025 -
 Software Warrior24 abril 2025
Software Warrior24 abril 2025
você pode gostar
-
 imgflip - Imgflip24 abril 2025
imgflip - Imgflip24 abril 2025 -
 C4 Location, Location, Location: Kirstie Allsopp and Phil24 abril 2025
C4 Location, Location, Location: Kirstie Allsopp and Phil24 abril 2025 -
Galaxy Note 10 recebe atualização com pacote de segurança de julho24 abril 2025
-
 ilustração de unicórnio fofo unicórnio kawaii chibi estilo de desenho vetorial desenho de unicórnio 17048027 Vetor no Vecteezy24 abril 2025
ilustração de unicórnio fofo unicórnio kawaii chibi estilo de desenho vetorial desenho de unicórnio 17048027 Vetor no Vecteezy24 abril 2025 -
 Linha De Fundo Fino Do ícone Do Pokemon Go Foto de Stock Editorial - Ilustração de etiqueta, fundo: 17556763824 abril 2025
Linha De Fundo Fino Do ícone Do Pokemon Go Foto de Stock Editorial - Ilustração de etiqueta, fundo: 17556763824 abril 2025 -
Darci Caiado - Você sabe como o Transtorno de Personalidade Borderline se caracteriza e como identificar os sintomas!? Pessoas com o Transtorno de Personalidade Borderline apresentam as seguintes características: instabilidade emocional, medo24 abril 2025
-
 Resident Evil 4 (Nintendo GameCube, 2005) for sale online24 abril 2025
Resident Evil 4 (Nintendo GameCube, 2005) for sale online24 abril 2025 -
 baller from roblox, glowing red eyes, godly24 abril 2025
baller from roblox, glowing red eyes, godly24 abril 2025 -
 Jogo Sonic Battle no Jogos 36024 abril 2025
Jogo Sonic Battle no Jogos 36024 abril 2025 -
 The Nike Dunk Low Gets Swooshes From Space - Sneaker Freaker24 abril 2025
The Nike Dunk Low Gets Swooshes From Space - Sneaker Freaker24 abril 2025