Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
Por um escritor misterioso
Last updated 11 abril 2025
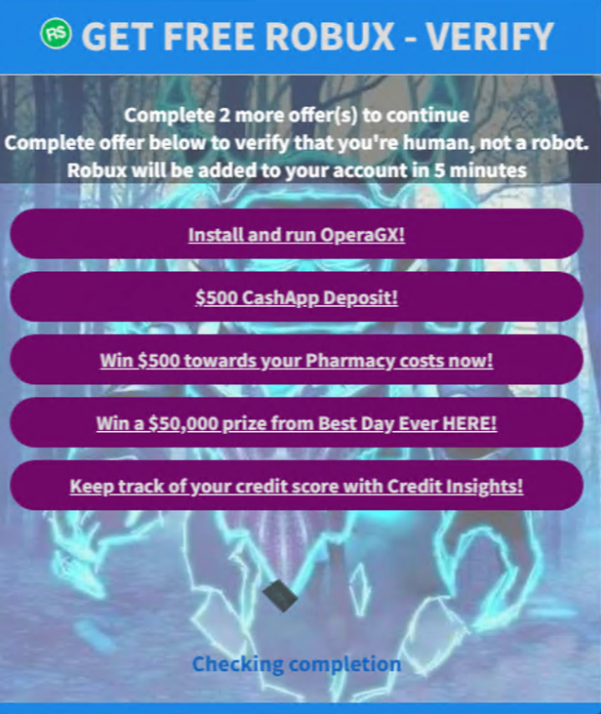
We cover two case studies of attacks hosted on malicious subdomains, including smishing and a scam Robux generator. We detail new methods in combating them.
Domain Shadowing: A Stealthy Use of DNS Compromise for Cybercrime

Attack Surface Monitoring: Two Ways to Detect Phishing Subdomains

Subdomain reconnaissance: enhancing a hacker's EASM - Labs Detectify
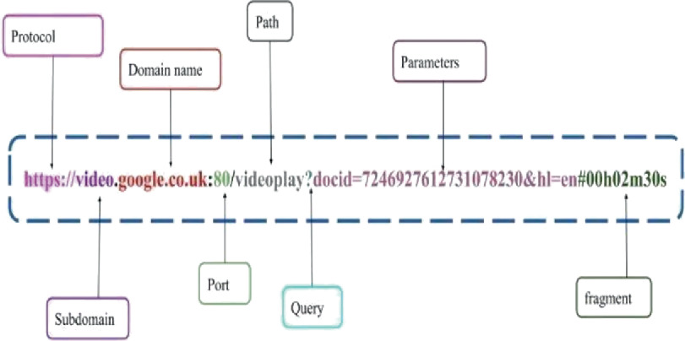
Classification of Malicious Websites Using Feature Based Machine Learning Techniques
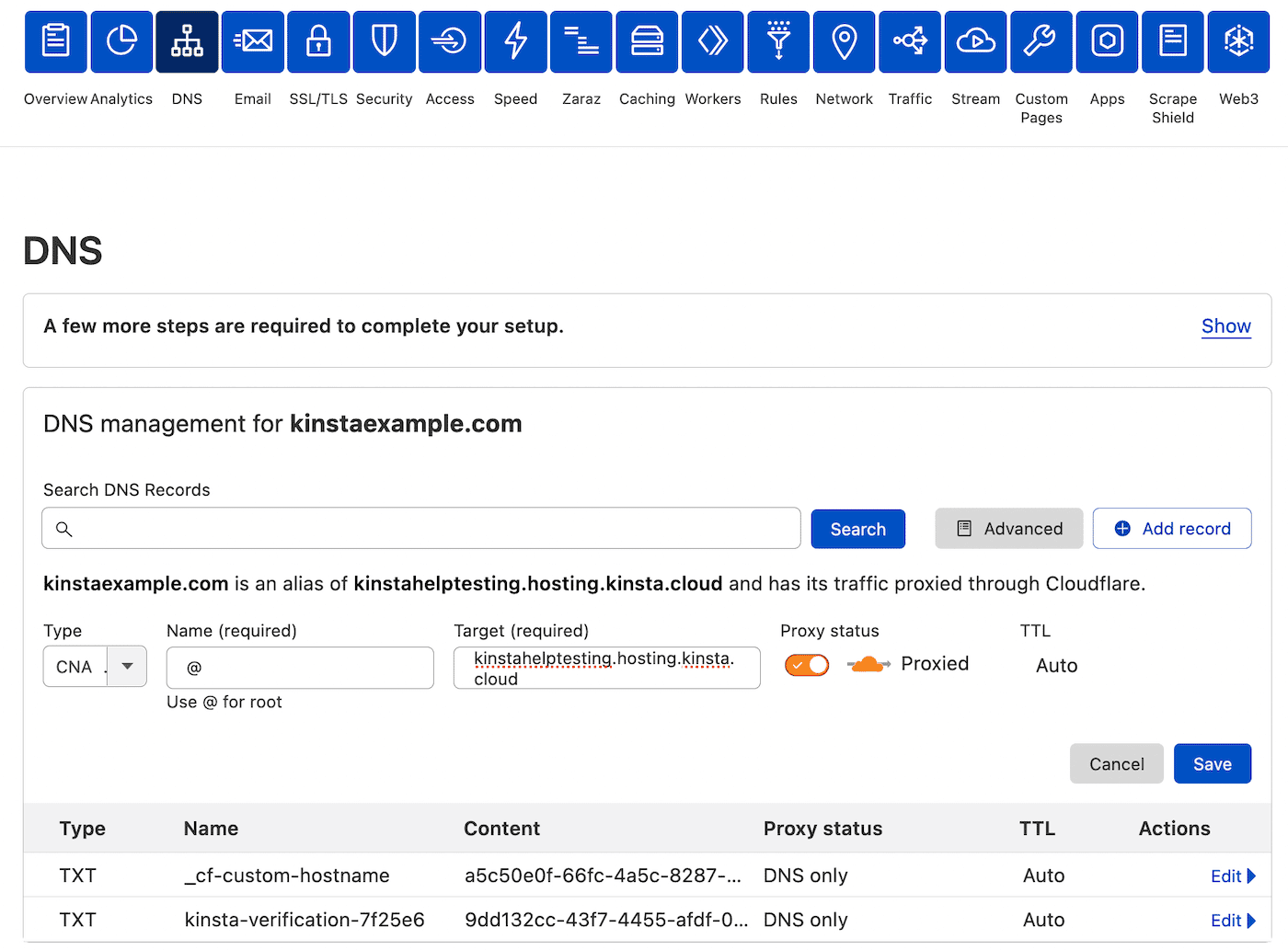
WordPress Hosting - Domains and DNS - Kinsta® Docs

Subdomain reconnaissance: enhancing a hacker's EASM - Labs Detectify
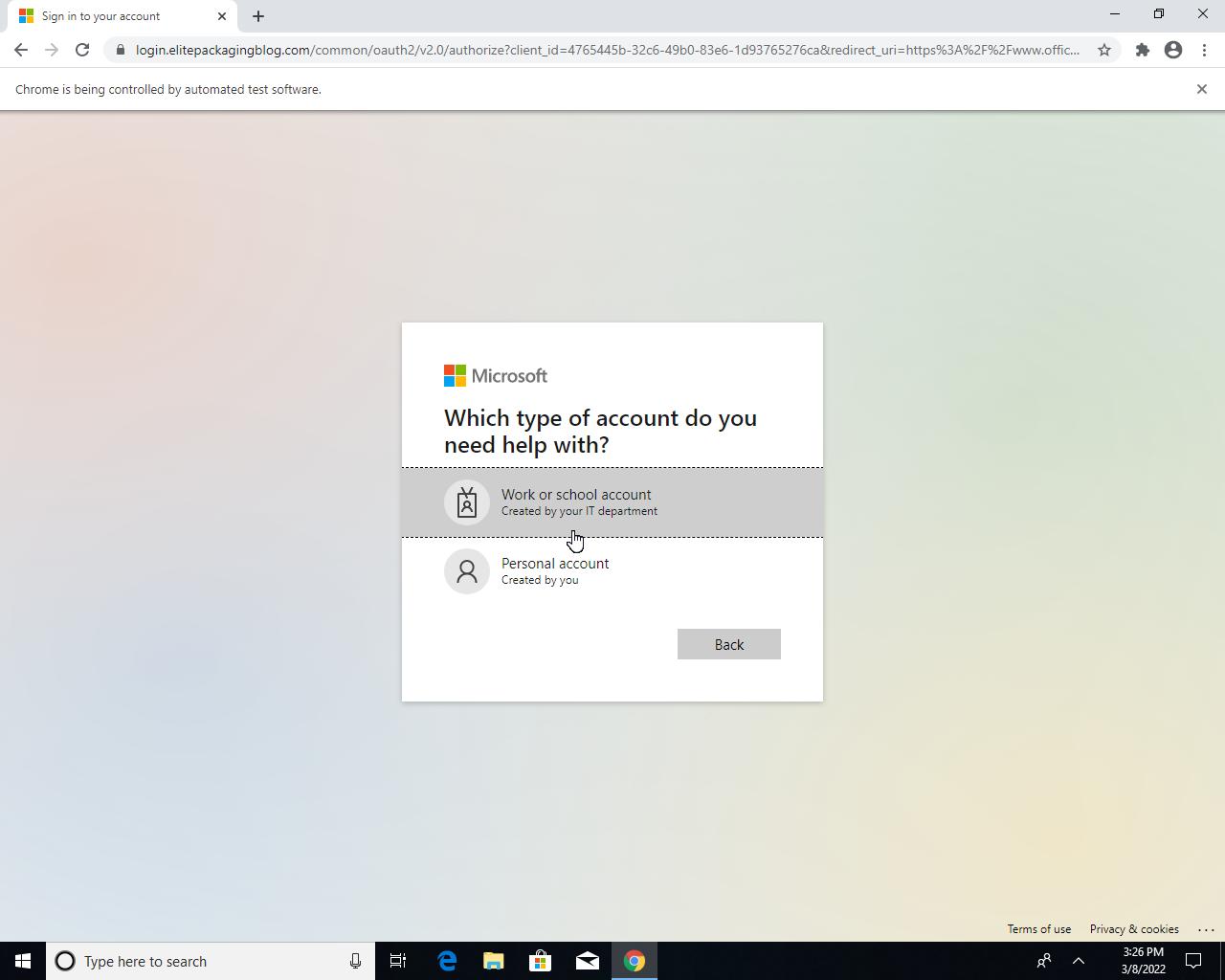
Domain Shadowing: A Stealthy Use of DNS Compromise for Cybercrime

Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains : r/CKsTechNews
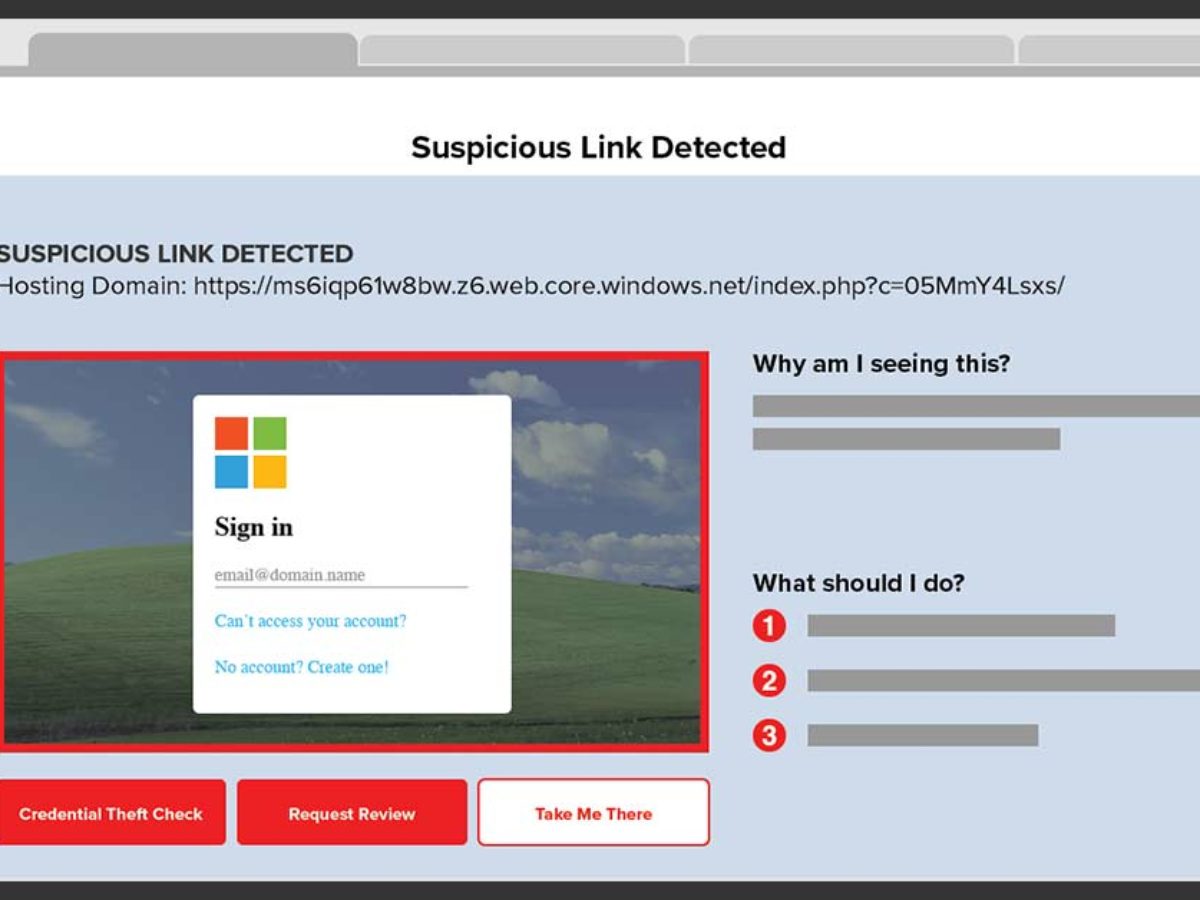
How to Protect Against Microsoft Subdomain Takeover - GreatHorn
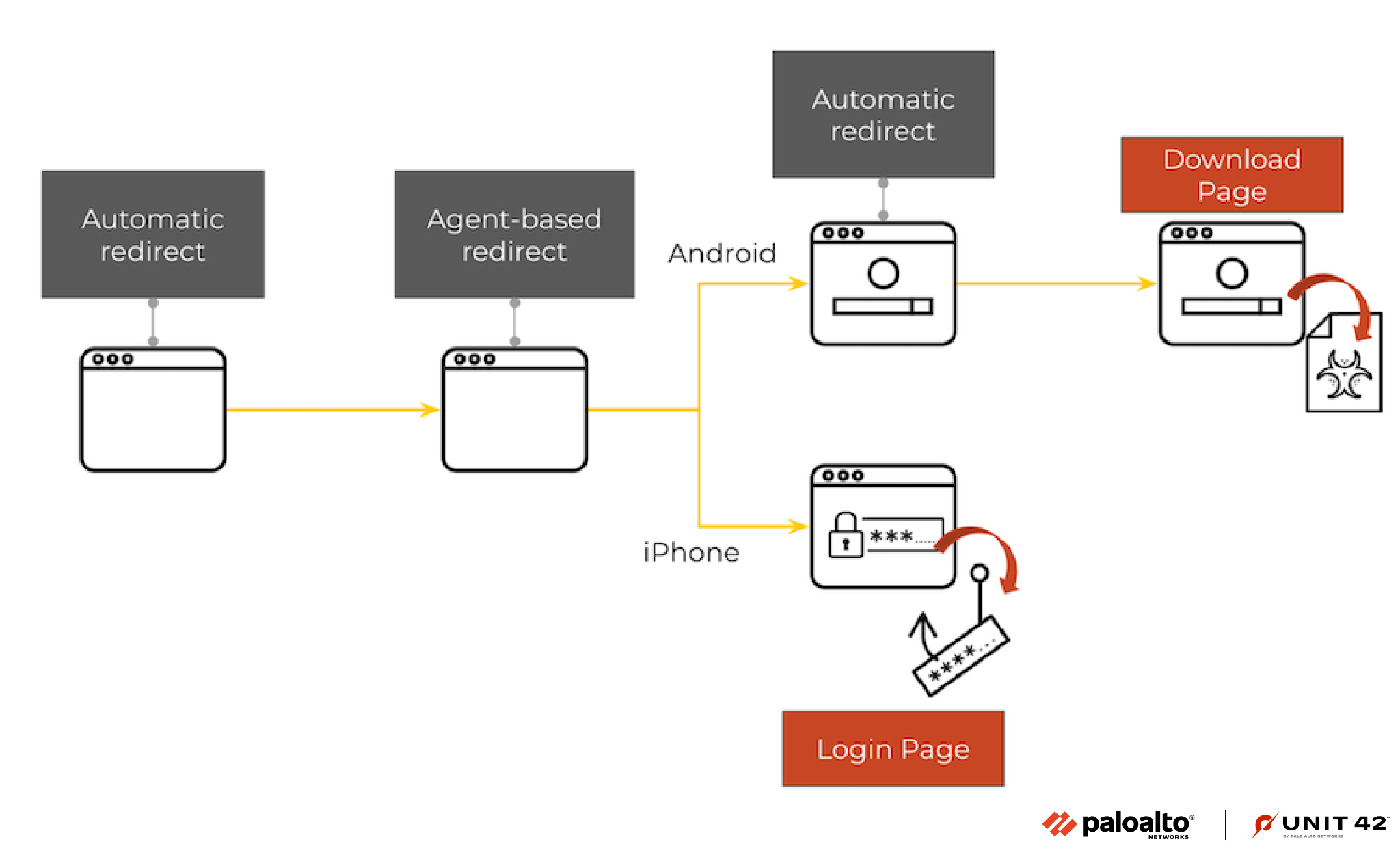
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
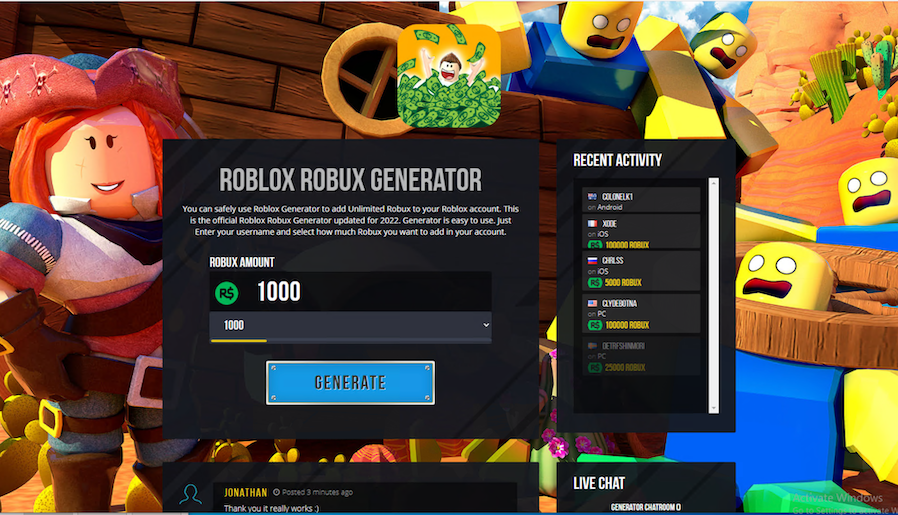
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
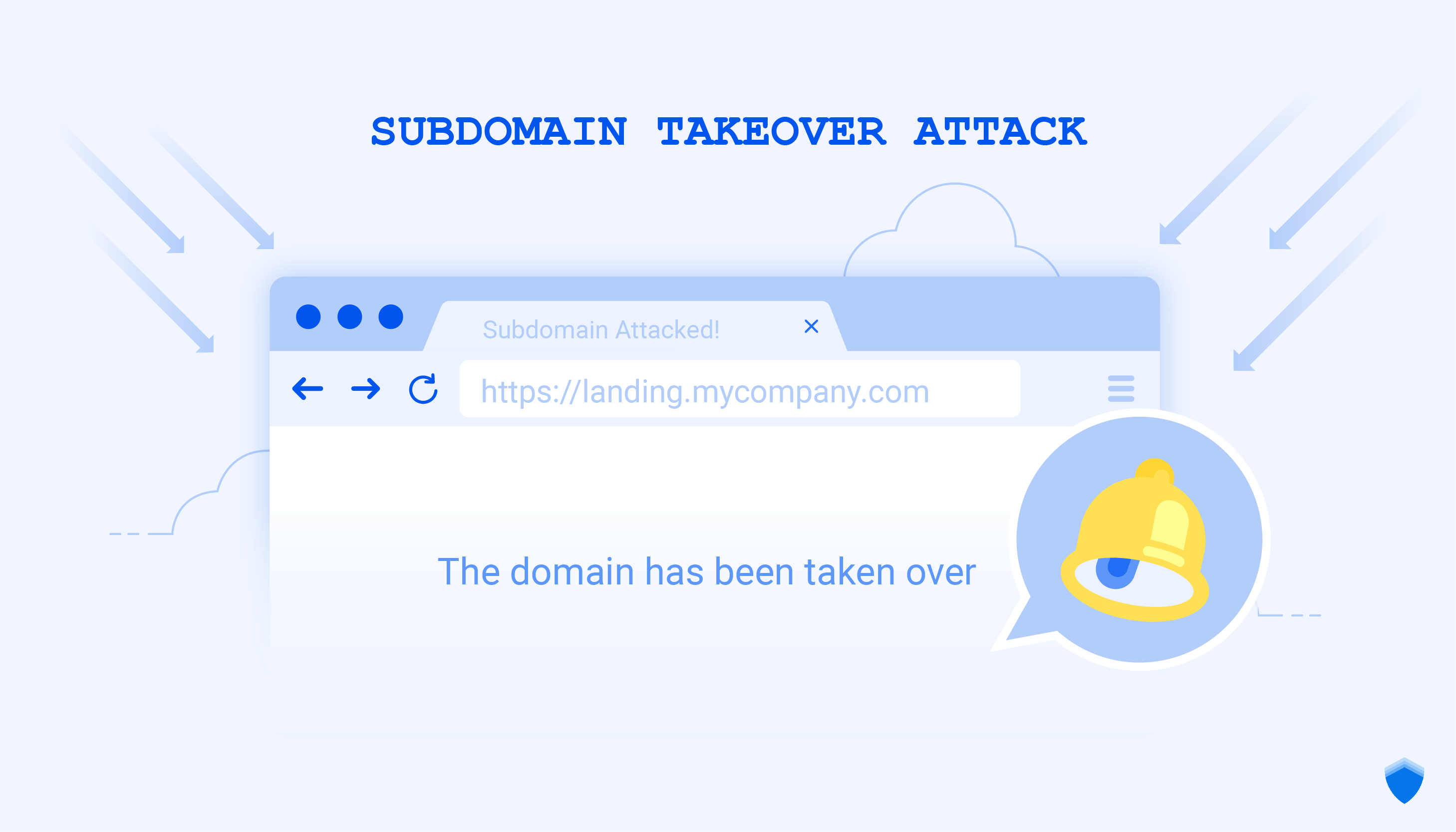
Subdomain takeover – Chapter one: Methodology
Recomendado para você
-
 Guide to Roblox – Forbes Advisor Australia11 abril 2025
Guide to Roblox – Forbes Advisor Australia11 abril 2025 -
 Robux Generator11 abril 2025
Robux Generator11 abril 2025 -
 Is Roblox safe for children - see parent's guide11 abril 2025
Is Roblox safe for children - see parent's guide11 abril 2025 -
Android Apps by Roblox Corporation on Google Play11 abril 2025
-
 Fake and 'free' game currency11 abril 2025
Fake and 'free' game currency11 abril 2025 -
 How cybercriminals attack young gamers11 abril 2025
How cybercriminals attack young gamers11 abril 2025 -
![Faster_Kids!!) Free Robux Generator 2022 Get 200K Free Robux Instantly [LAone!] - Untitled Collection #482364553](https://openseauserdata.com/files/4c1828b203628f75fe6f509ec163af41.jpg) Faster_Kids!!) Free Robux Generator 2022 Get 200K Free Robux Instantly [LAone!] - Untitled Collection #48236455311 abril 2025
Faster_Kids!!) Free Robux Generator 2022 Get 200K Free Robux Instantly [LAone!] - Untitled Collection #48236455311 abril 2025 -
Robuxgenerator Inc Launches Free Robux Generator to Get Free Robux in 2022 without Verification11 abril 2025
-
 The trouble with Roblox, the video game empire built on child labour, Games11 abril 2025
The trouble with Roblox, the video game empire built on child labour, Games11 abril 2025 -
 How to better protect your Roblox account from hackers with two-step verification (2SV) • Graham Cluley11 abril 2025
How to better protect your Roblox account from hackers with two-step verification (2SV) • Graham Cluley11 abril 2025
você pode gostar
-
Hikari 光 Video creator11 abril 2025
-
Jornal A Plateia Livramento - Santanense tem Cavalo Furtado Foi furtado hoje (03), Próximo às 17h, na rua Joaquim Álvares, n° 650 um cavalo colorado, frente aberta, com as quatro patas brancas11 abril 2025
-
 COMO FAZER UM JOGO DO PACMAN EM CASA11 abril 2025
COMO FAZER UM JOGO DO PACMAN EM CASA11 abril 2025 -
 THE HOWLER - NEW SHIP IN STARBLAST.IO Starblast.io New Update ( Team Mode 36 ) Thiện Vn11 abril 2025
THE HOWLER - NEW SHIP IN STARBLAST.IO Starblast.io New Update ( Team Mode 36 ) Thiện Vn11 abril 2025 -
 Pokémon 2 Quad Packs Origem Perdida Weavile + Regigigas11 abril 2025
Pokémon 2 Quad Packs Origem Perdida Weavile + Regigigas11 abril 2025 -
 The King's Speech - Plugged In11 abril 2025
The King's Speech - Plugged In11 abril 2025 -
 Markiplier - Wikipedia11 abril 2025
Markiplier - Wikipedia11 abril 2025 -
 Logo abaixo tiro de pessoa jogando basquete - Fotos de arquivo11 abril 2025
Logo abaixo tiro de pessoa jogando basquete - Fotos de arquivo11 abril 2025 -
 57 Romantic Shows on Netflix, 202311 abril 2025
57 Romantic Shows on Netflix, 202311 abril 2025 -
 Mashle Magic and Muscles Dublado Todos os Episódios Online » Anime11 abril 2025
Mashle Magic and Muscles Dublado Todos os Episódios Online » Anime11 abril 2025


