Suspicious User Controls
Por um escritor misterioso
Last updated 15 abril 2025


Protect Your Device Your Way with Samsung Auto Blocker – Samsung Newsroom U.K.
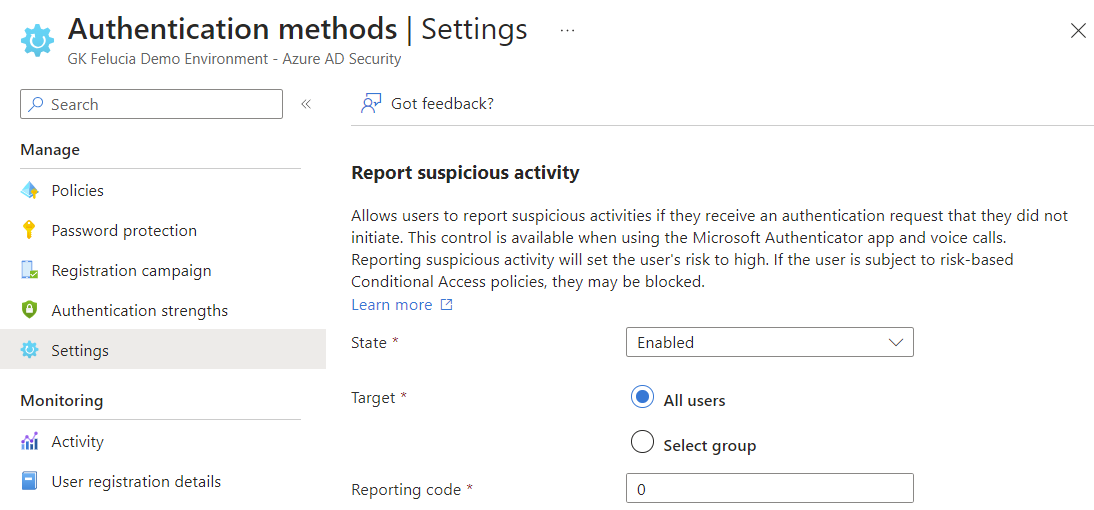
Microsoft Entra MFA Fraud Deep Dive, by Christopher Brumm

mongodb - Suspicious app name in Windows 10 permission prompt - Information Security Stack Exchange

Microsoft's Office 365 Advanced Security Management tools start rolling out
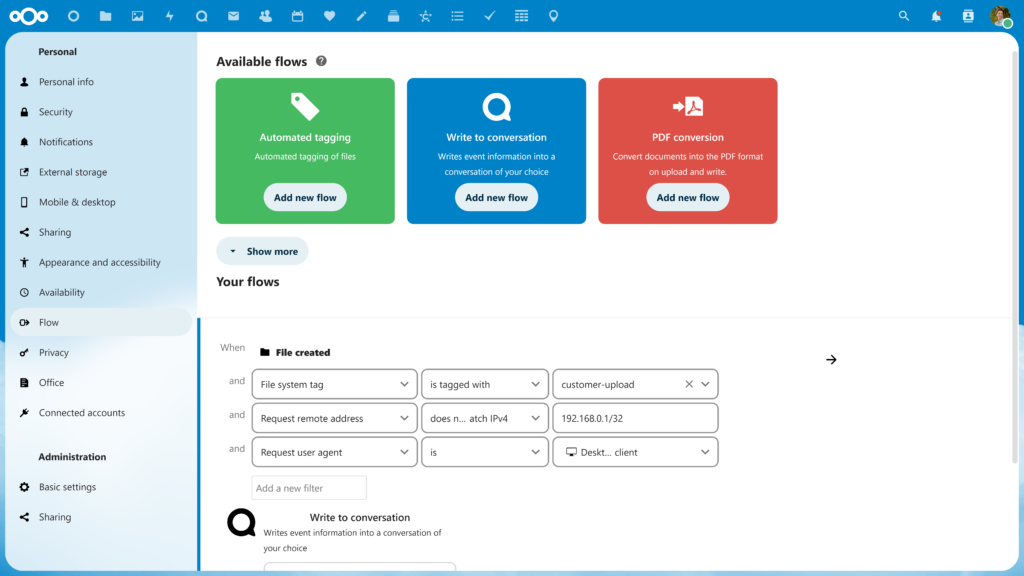
Nextcloud features that put you in control

Foxit Reader Crash Report with Suspicious Registry Change Request – Help Center
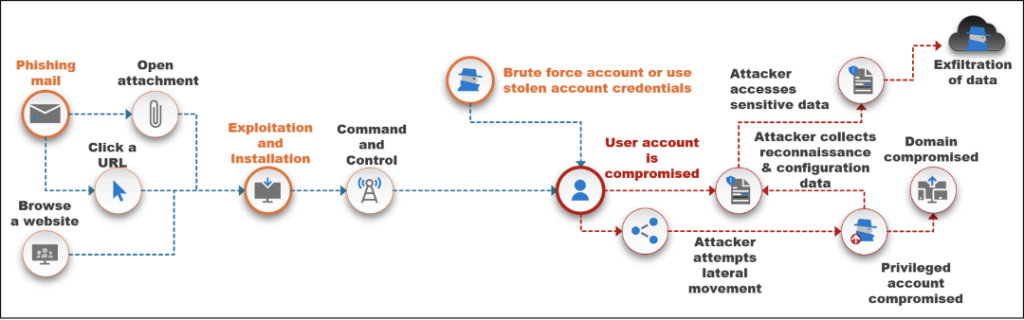
Identity is the New Perimeter - Critical Start

Workflows Tips #9 – Control Flow Execution, Avoid Case Sensitive Errors, and Using Lookup Table – Max Katz
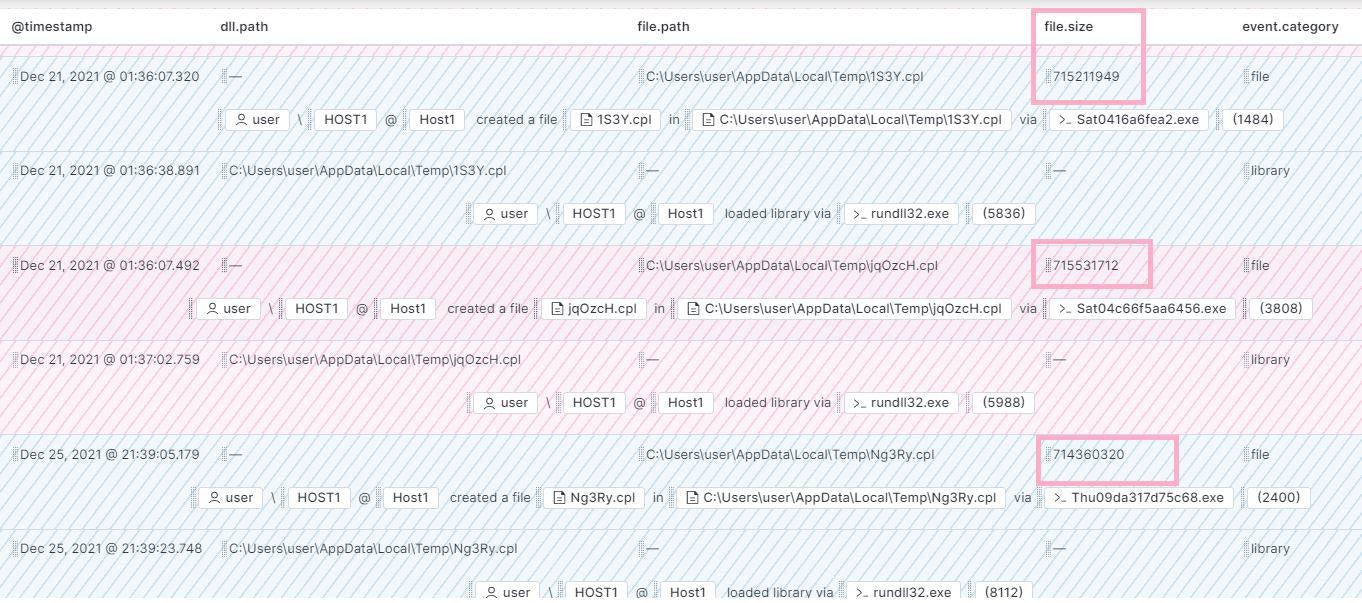
Hunting for Suspicious Windows Libraries for Execution and Defense Evasion — Elastic Security Labs

Twitch launches Suspicious User Detection to combat harassment in chat - MCV/DEVELOP
Understanding HP Wolf Identity/Credential Protection
Content control – Access to users correspondence add-on, Communications - Marketplace — PG Dating Pro
New Release: The Gorilla Guide® To… Practical Endpoint Privilege Security - Gorilla Guide
Recomendado para você
-
 Evade Roblox – What is it, How to play, Codes, and More15 abril 2025
Evade Roblox – What is it, How to play, Codes, and More15 abril 2025 -
 Evade on a keyboard sucks : r/elex15 abril 2025
Evade on a keyboard sucks : r/elex15 abril 2025 -
 Controls and Best Settings15 abril 2025
Controls and Best Settings15 abril 2025 -
 Control - A Merry Chase mission, unlocking Evade and Air-Evade powers15 abril 2025
Control - A Merry Chase mission, unlocking Evade and Air-Evade powers15 abril 2025 -
 Star Wars Jedi Survivor Controls Guide and Keybinds Recommendations15 abril 2025
Star Wars Jedi Survivor Controls Guide and Keybinds Recommendations15 abril 2025 -
 Control: How To Get The 'Evade' Ability15 abril 2025
Control: How To Get The 'Evade' Ability15 abril 2025 -
 MTGNexus - Evade15 abril 2025
MTGNexus - Evade15 abril 2025 -
 US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals15 abril 2025
US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals15 abril 2025 -
 The drama surrounding TikTok continues. Private spyware companies evade export controls.15 abril 2025
The drama surrounding TikTok continues. Private spyware companies evade export controls.15 abril 2025 -
Insect Glaive Tutorial and Controls - Monster Hunter Rise Guide - IGN15 abril 2025
você pode gostar
-
 asdasd Langports15 abril 2025
asdasd Langports15 abril 2025 -
 How To Play FIFA 23 On The Steam Deck On Steam OS With Google15 abril 2025
How To Play FIFA 23 On The Steam Deck On Steam OS With Google15 abril 2025 -
 Minecraft 1.18.1 Wurst Hacked Client Downloads15 abril 2025
Minecraft 1.18.1 Wurst Hacked Client Downloads15 abril 2025 -
 Nintendo pode remasterizar maioria dos jogos do Mario para o Nintendo Switch, diz rumor - NerdBunker15 abril 2025
Nintendo pode remasterizar maioria dos jogos do Mario para o Nintendo Switch, diz rumor - NerdBunker15 abril 2025 -
MR INCREDIBLE BECOMING UNCANNY MEME GOT ME CURSED AGAIN15 abril 2025
-
 samsung sam (samsung) drawn by kitsunearts15 abril 2025
samsung sam (samsung) drawn by kitsunearts15 abril 2025 -
Uncanny Alphabet World Band Remastered 1 10 Remix #brandonfoo #alphabe15 abril 2025
-
 Rumo à Série B? Má fase do Santos tem feito a alegria dos rivais15 abril 2025
Rumo à Série B? Má fase do Santos tem feito a alegria dos rivais15 abril 2025 -
 okay, who goofed the wikipedia page : r/slimerancher15 abril 2025
okay, who goofed the wikipedia page : r/slimerancher15 abril 2025 -
 Call of Duty: Modern Warfare II Disco do PS5 não inclui o jogo15 abril 2025
Call of Duty: Modern Warfare II Disco do PS5 não inclui o jogo15 abril 2025
