Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 12 abril 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.

FireEye veterans launch threat intelligence firm Silent Push with
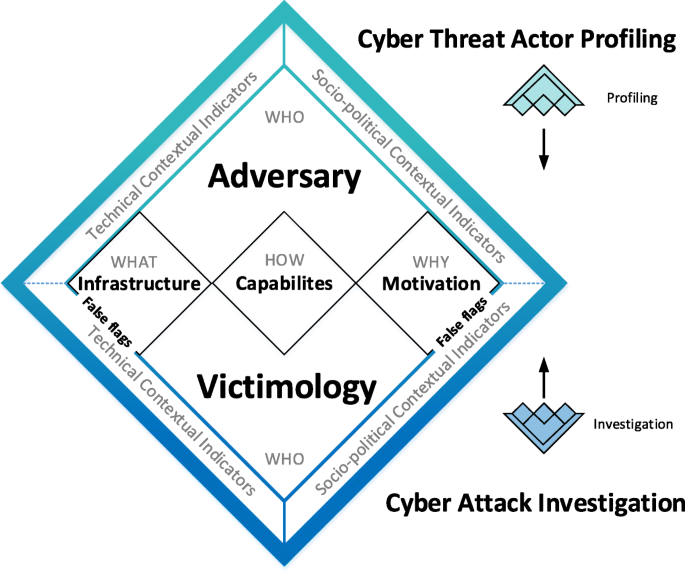
Under false flag: using technical artifacts for cyber attack
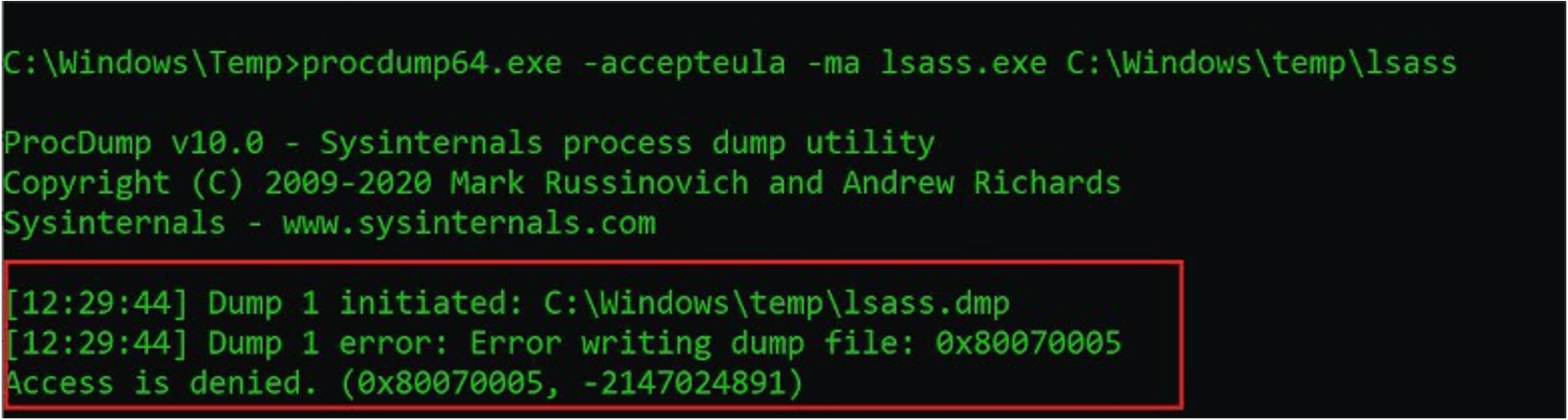
Protecting Against HAFNIUM With FireEye Endpoint Security Process

FireEye Named a Leader in IDC MarketScape for Asia/Pacific Threat

Tactics, Techniques and Procedures of FireEye Red Team Tools
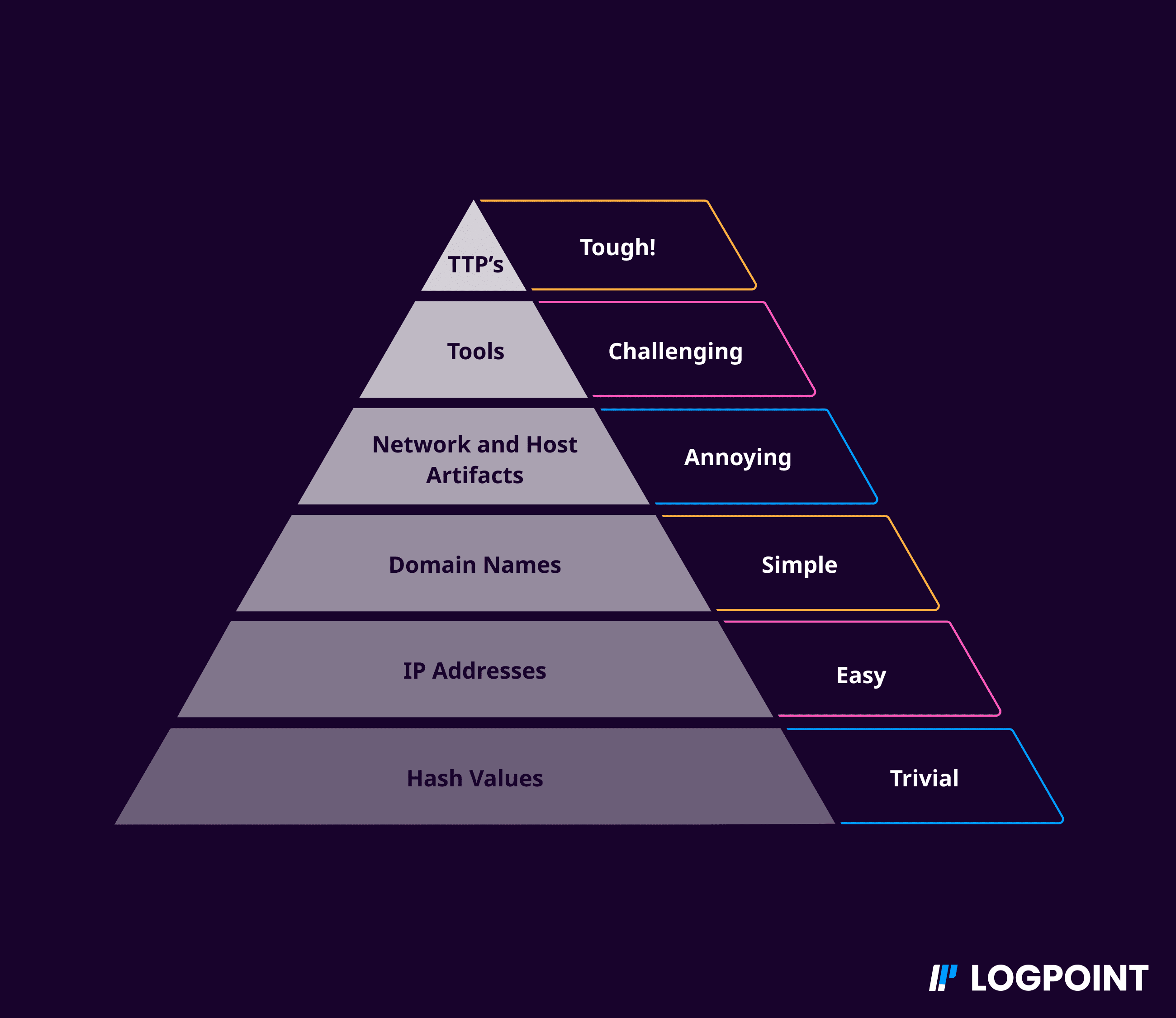
Behavioral analysis in security - Logpoint
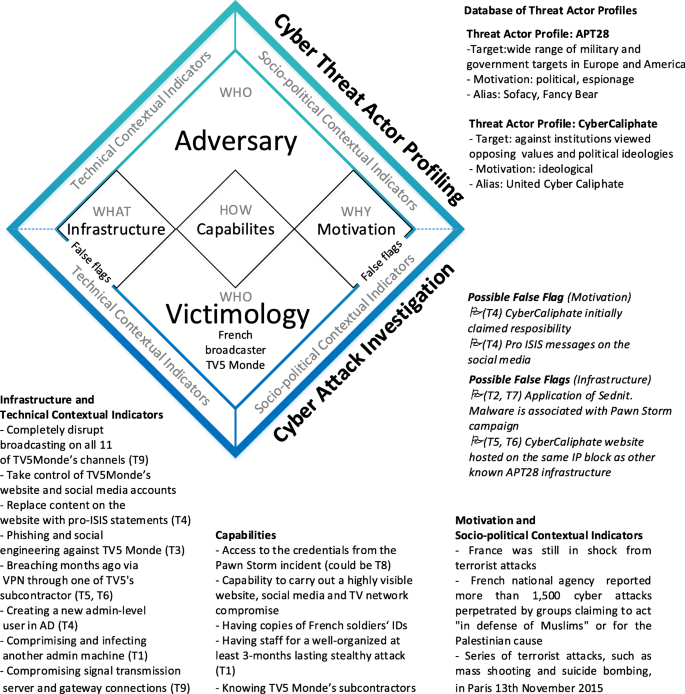
Under false flag: using technical artifacts for cyber attack

PDF] Semantic Cyberthreat Modelling
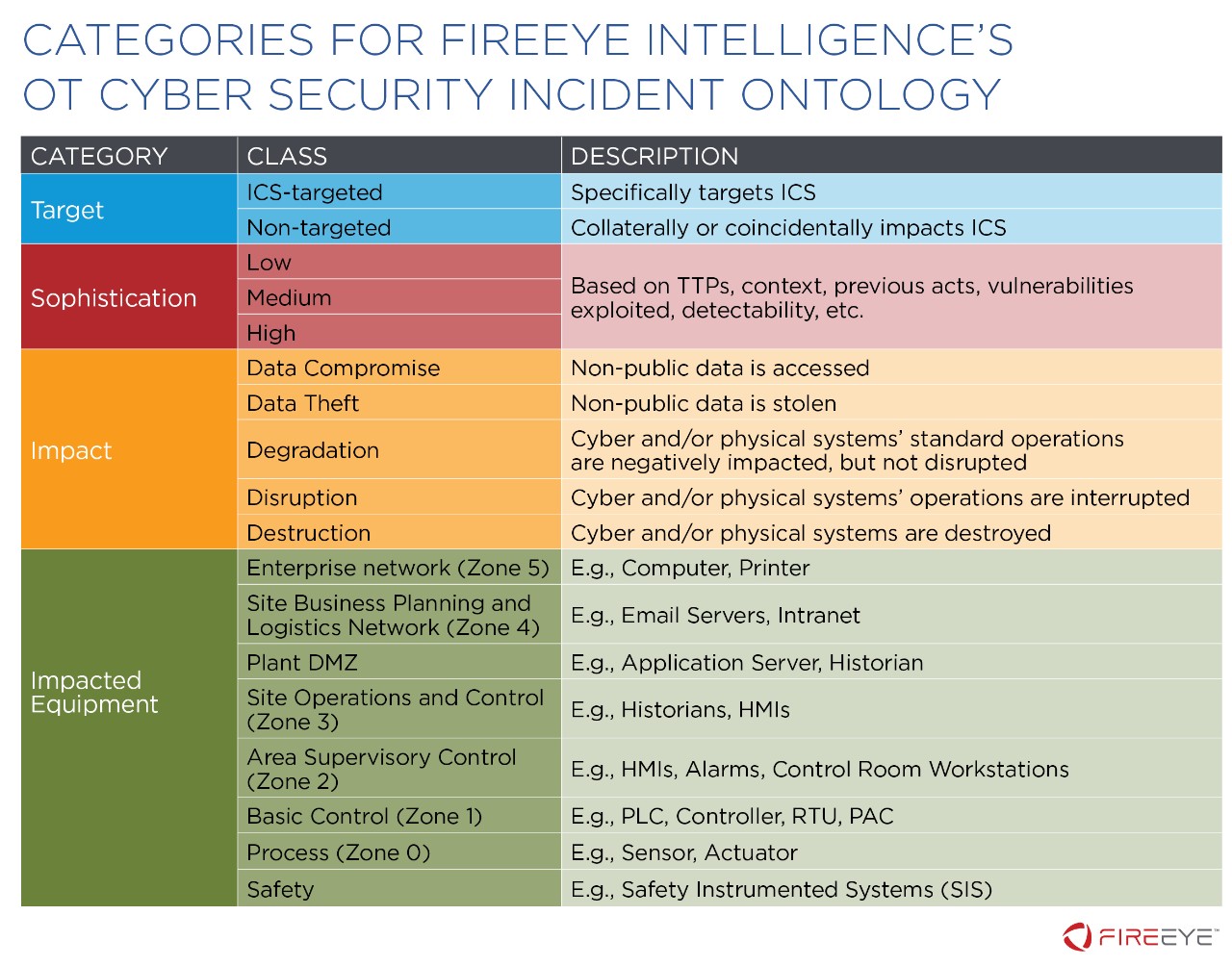
The FireEye OT-CSIO: An Ontology to Understand, Cross-Compare, and

Chinese Cyber Espionage Hackers Continue to Target Pulse Secure

Tactics, Techniques and Procedures (TTPs) to Augment Cyber Threat
Recomendado para você
-
Bbc android iplayer download12 abril 2025
-
 Airline eCommerce Software & Digital Retailing Solutions12 abril 2025
Airline eCommerce Software & Digital Retailing Solutions12 abril 2025 -
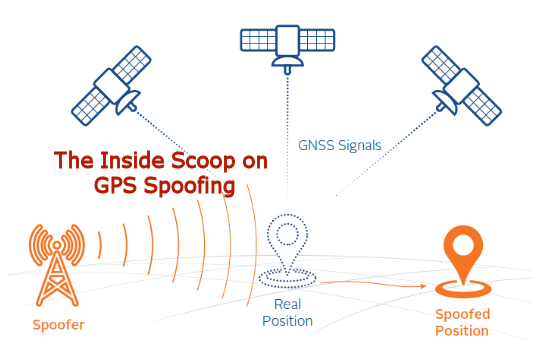
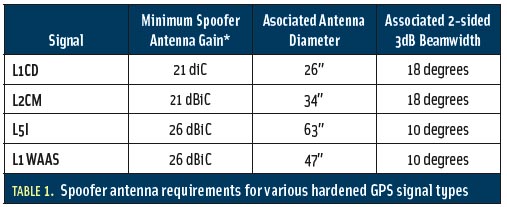 Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation12 abril 2025
Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation12 abril 2025 -
 Autonomous aerial robotics for package delivery: A technical12 abril 2025
Autonomous aerial robotics for package delivery: A technical12 abril 2025 -
 Who Killed Art Deco?: A Novel - Kindle edition by Barris, Chuck12 abril 2025
Who Killed Art Deco?: A Novel - Kindle edition by Barris, Chuck12 abril 2025 -
best fivem spoofer free|TikTok Search12 abril 2025
-
 11 Types of Spoofing Attacks Every Security Professional Should12 abril 2025
11 Types of Spoofing Attacks Every Security Professional Should12 abril 2025 -
 DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural12 abril 2025
DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural12 abril 2025 -
 Telnet Networks - Managing Network Performance - Telnet Network12 abril 2025
Telnet Networks - Managing Network Performance - Telnet Network12 abril 2025 -
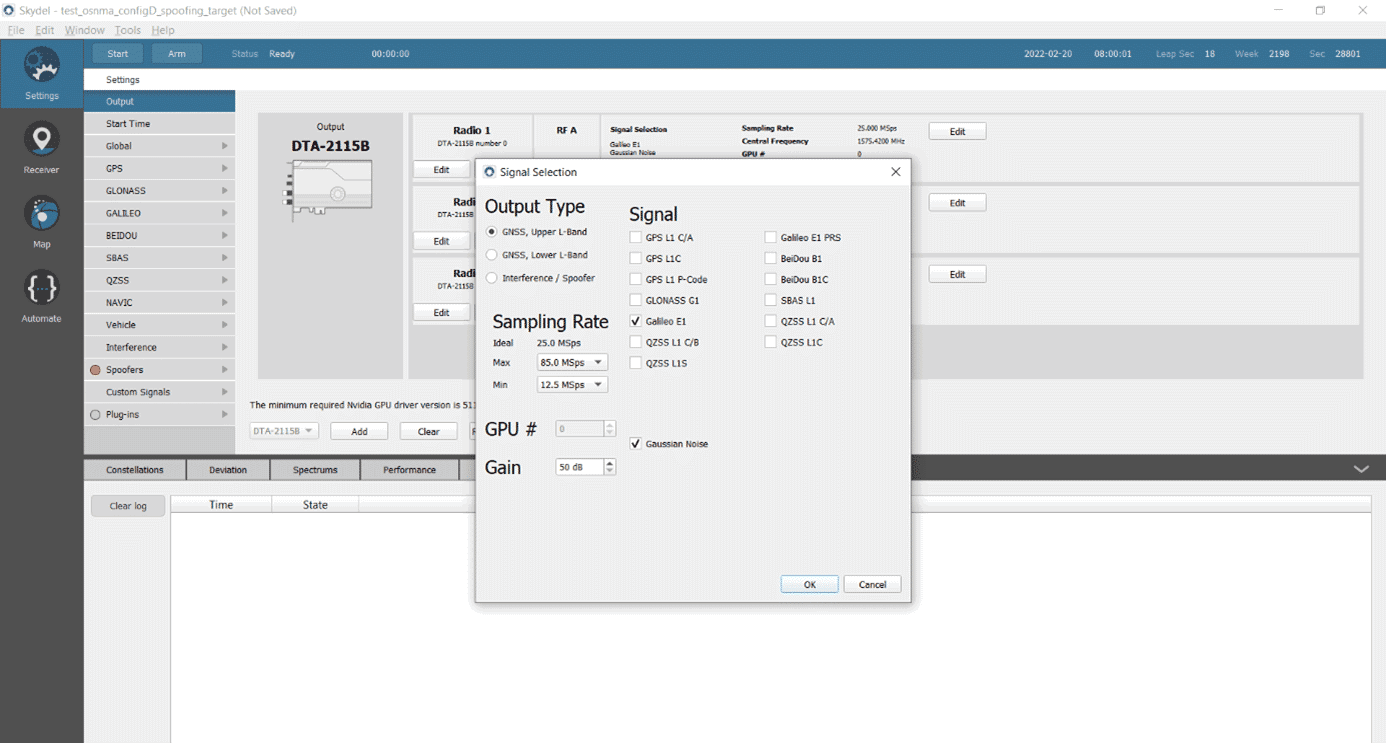 Testing a Receiver's Galileo OS-NMA Capability Using Skydel - Safran - Navigation & Timing12 abril 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel - Safran - Navigation & Timing12 abril 2025
você pode gostar
-
 Corinthians x Fluminense - AO VIVO - 15/09/2022 - Copa do Brasil12 abril 2025
Corinthians x Fluminense - AO VIVO - 15/09/2022 - Copa do Brasil12 abril 2025 -
 PATCH BORDADO AZ DE ESPADAS - BLACK SPADE JOLY ROGER12 abril 2025
PATCH BORDADO AZ DE ESPADAS - BLACK SPADE JOLY ROGER12 abril 2025 -
 Episode 12 - The Devil Carries Out His Duties12 abril 2025
Episode 12 - The Devil Carries Out His Duties12 abril 2025 -
 Mandala dos livros de colorir gratuitos para adultos - 1 - Mandalas - Coloring Pages for Adults12 abril 2025
Mandala dos livros de colorir gratuitos para adultos - 1 - Mandalas - Coloring Pages for Adults12 abril 2025 -
 Marvel, quicksilver, rule 63, female, short hair, full body, curvy body, high definition, cosplay, exposed midriff, fit, blue eyeliner, elizabeth olsen, 4k, muscular, highly detailed, stunning, detailed face, busty, wide angle12 abril 2025
Marvel, quicksilver, rule 63, female, short hair, full body, curvy body, high definition, cosplay, exposed midriff, fit, blue eyeliner, elizabeth olsen, 4k, muscular, highly detailed, stunning, detailed face, busty, wide angle12 abril 2025 -
 The NieR Automata Anime Is Airing Now On Crunchyroll In Australia12 abril 2025
The NieR Automata Anime Is Airing Now On Crunchyroll In Australia12 abril 2025 -
 20.01.31_TPH Colorado Media Day (144) - Total Package Hockey12 abril 2025
20.01.31_TPH Colorado Media Day (144) - Total Package Hockey12 abril 2025 -
 Bokura wa Minna Kawaisou Vol.11 : r/manga12 abril 2025
Bokura wa Minna Kawaisou Vol.11 : r/manga12 abril 2025 -
 Summer Time Rendering (TV Series 2022) - Episode list - IMDb12 abril 2025
Summer Time Rendering (TV Series 2022) - Episode list - IMDb12 abril 2025 -
 Ranni Elden Ring, Ranni the Witch (Elden Ring)12 abril 2025
Ranni Elden Ring, Ranni the Witch (Elden Ring)12 abril 2025
