Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Last updated 10 abril 2025


Cryptojacking: Understanding and defending against cloud compute
Detect cryptojacking with Sysdig's high-precision machine learning

What is Cryptojacking. Criminals are now using ransomware-like
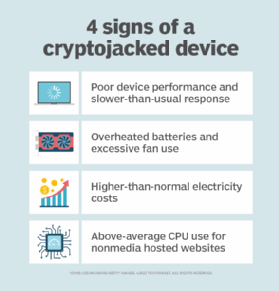
What is Cryptojacking? Detection and Preventions Techniques

Amir G. on LinkedIn: Cryptojacking: Understanding and defending

Threat Alert: Cloud Network Bandwidth Now Stolen through Cryptojacking

What is Cryptojacking & How does it work?
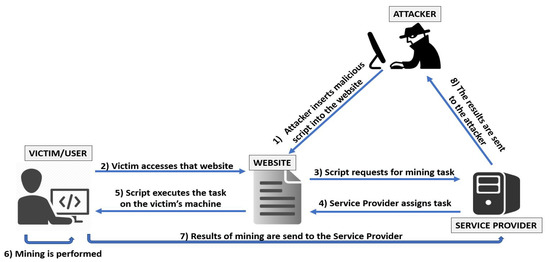
Applied Sciences, Free Full-Text
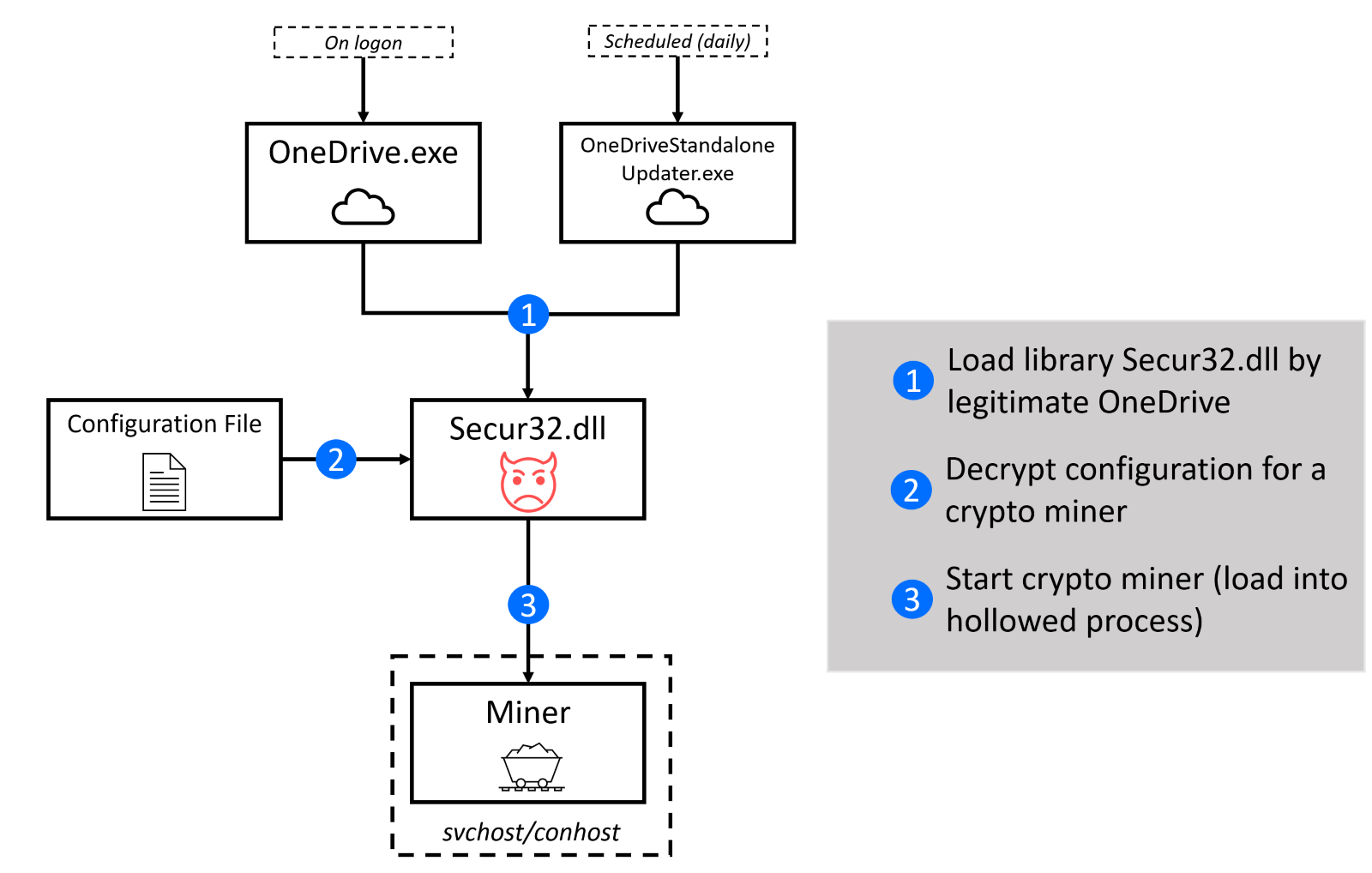
Deep Dive into a Cryptojacking Operation

Cryptojacking: Understanding and Preventing Unauthorized

Tamer Salman on LinkedIn: Cryptojacking: Understanding and

Cryptojacking: Understanding and defending against cloud compute

Deep Dive into a Cryptojacking Operation

What is Cryptojacking?
Recomendado para você
-
 Watch List 202310 abril 2025
Watch List 202310 abril 2025 -
 🔴 ( LIVE ON ) 27/05/2023 - JOGANDO - SUDDEN ATTACK 2023 ( Resenha com o Clã Pro-arms'Br's )10 abril 2025
🔴 ( LIVE ON ) 27/05/2023 - JOGANDO - SUDDEN ATTACK 2023 ( Resenha com o Clã Pro-arms'Br's )10 abril 2025 -
 45 Global DDOS Attack Statistics 2023 - Astra Security Blog10 abril 2025
45 Global DDOS Attack Statistics 2023 - Astra Security Blog10 abril 2025 -
 Global response to Operation Al-Aqsa Flood – Middle East Monitor10 abril 2025
Global response to Operation Al-Aqsa Flood – Middle East Monitor10 abril 2025 -
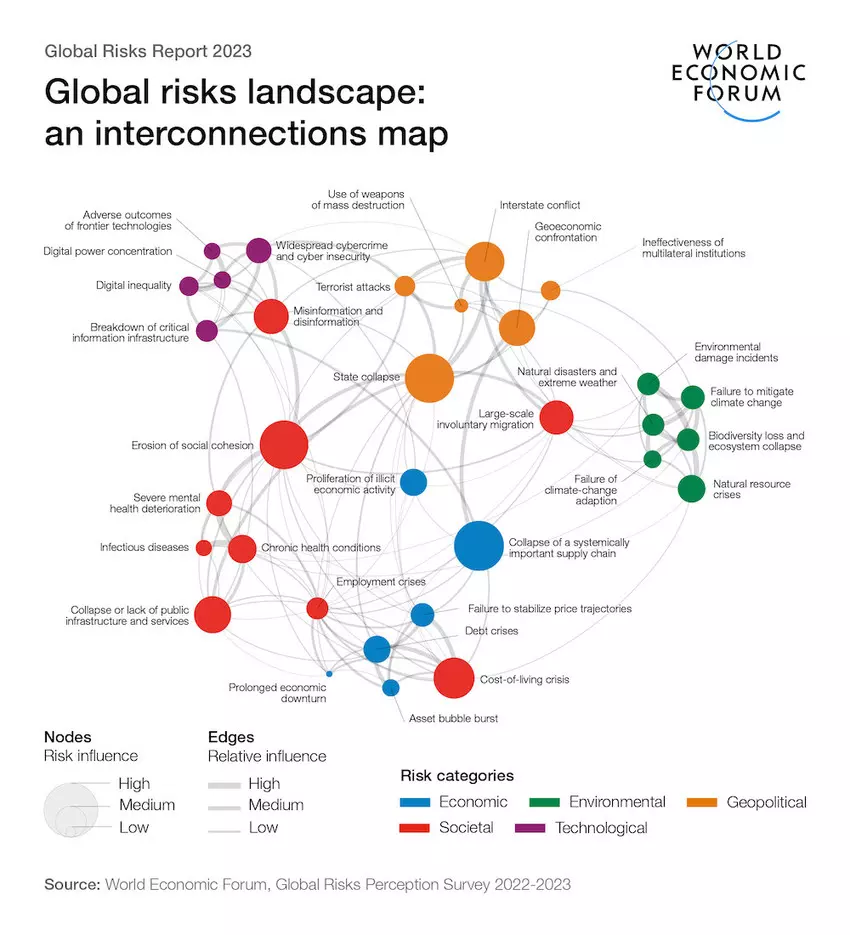 The Global Risks Report 2023 18th Edition10 abril 2025
The Global Risks Report 2023 18th Edition10 abril 2025 -
 2023 End of Year Letter10 abril 2025
2023 End of Year Letter10 abril 2025 -
 10 Conflicts to Watch in 202310 abril 2025
10 Conflicts to Watch in 202310 abril 2025 -
 Hotfixes: December 12, 2023 — World of Warcraft — Blizzard News10 abril 2025
Hotfixes: December 12, 2023 — World of Warcraft — Blizzard News10 abril 2025 -
 Wild otter attack leads to woman being airlifted to hospital, 210 abril 2025
Wild otter attack leads to woman being airlifted to hospital, 210 abril 2025 -
 Latest Statistics Sudden Cardiac Arrest Foundation10 abril 2025
Latest Statistics Sudden Cardiac Arrest Foundation10 abril 2025
você pode gostar
-
 Conversations on COVID: Is all pandemic news really bad news?10 abril 2025
Conversations on COVID: Is all pandemic news really bad news?10 abril 2025 -
 Doujinshi Mountain Path BO?IS! (Naruto Kakashi Hatake x Iruka Umino)10 abril 2025
Doujinshi Mountain Path BO?IS! (Naruto Kakashi Hatake x Iruka Umino)10 abril 2025 -
 Just Shapes & Beats Now on Android ! ! ! New Android Port 202310 abril 2025
Just Shapes & Beats Now on Android ! ! ! New Android Port 202310 abril 2025 -
 Premium Freeze Dried Space Balls Candy - Freeze Dried Candy Freeze Dry Candy - Shipped in a Sturdy Box for Protection - Dry Freeze Candy for All Ages10 abril 2025
Premium Freeze Dried Space Balls Candy - Freeze Dried Candy Freeze Dry Candy - Shipped in a Sturdy Box for Protection - Dry Freeze Candy for All Ages10 abril 2025 -
 LG UBK90 4K Ultra-HD Blu-Ray Player UBK90 Greentoe TV's & Home Theater10 abril 2025
LG UBK90 4K Ultra-HD Blu-Ray Player UBK90 Greentoe TV's & Home Theater10 abril 2025 -
 Class review: This Elite remake is top class - India Today10 abril 2025
Class review: This Elite remake is top class - India Today10 abril 2025 -
 SONIC The HEDGEHOG Comic Book Issue #241 November 2012 AMY ROSE Bagged Board NM10 abril 2025
SONIC The HEDGEHOG Comic Book Issue #241 November 2012 AMY ROSE Bagged Board NM10 abril 2025 -
 PEDRA SÃO TOMÉ CANJIQUINHA FILETE PRENSA GROSSO - AMARELO, PEDRAS DECORATIVAS10 abril 2025
PEDRA SÃO TOMÉ CANJIQUINHA FILETE PRENSA GROSSO - AMARELO, PEDRAS DECORATIVAS10 abril 2025 -
 Kirito's cameo in SAO Alternative: Gun Gale Online E06 : r/swordartonline10 abril 2025
Kirito's cameo in SAO Alternative: Gun Gale Online E06 : r/swordartonline10 abril 2025 -
 Flower Boys: Manga-inspired hairstyles for men10 abril 2025
Flower Boys: Manga-inspired hairstyles for men10 abril 2025