Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 25 abril 2025

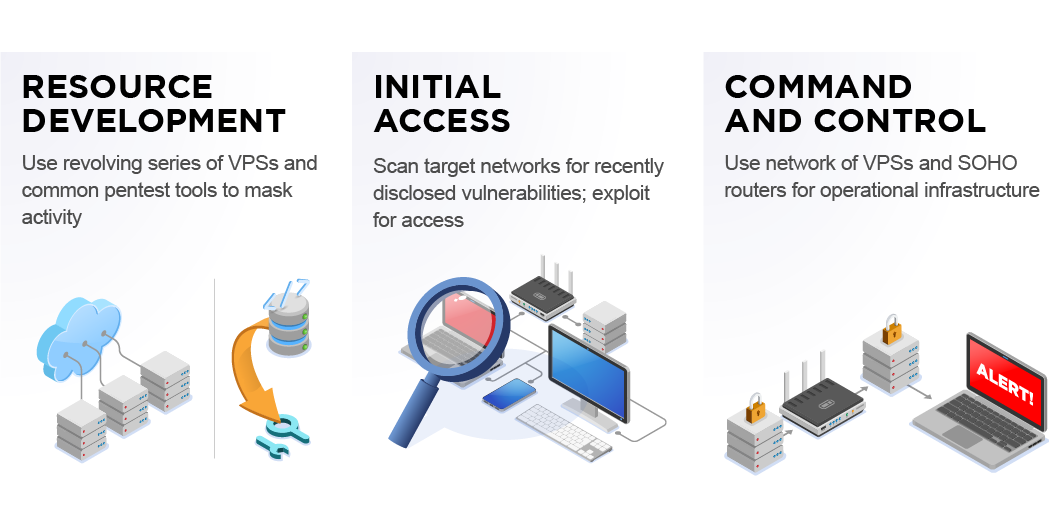
We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
It is Time to Take Action - How to Defend Against FireEye's Red

Purple Team - Work it out: Organizing Effective Adversary
Chinese State-Sponsored Cyber Operations: Observed TTPs
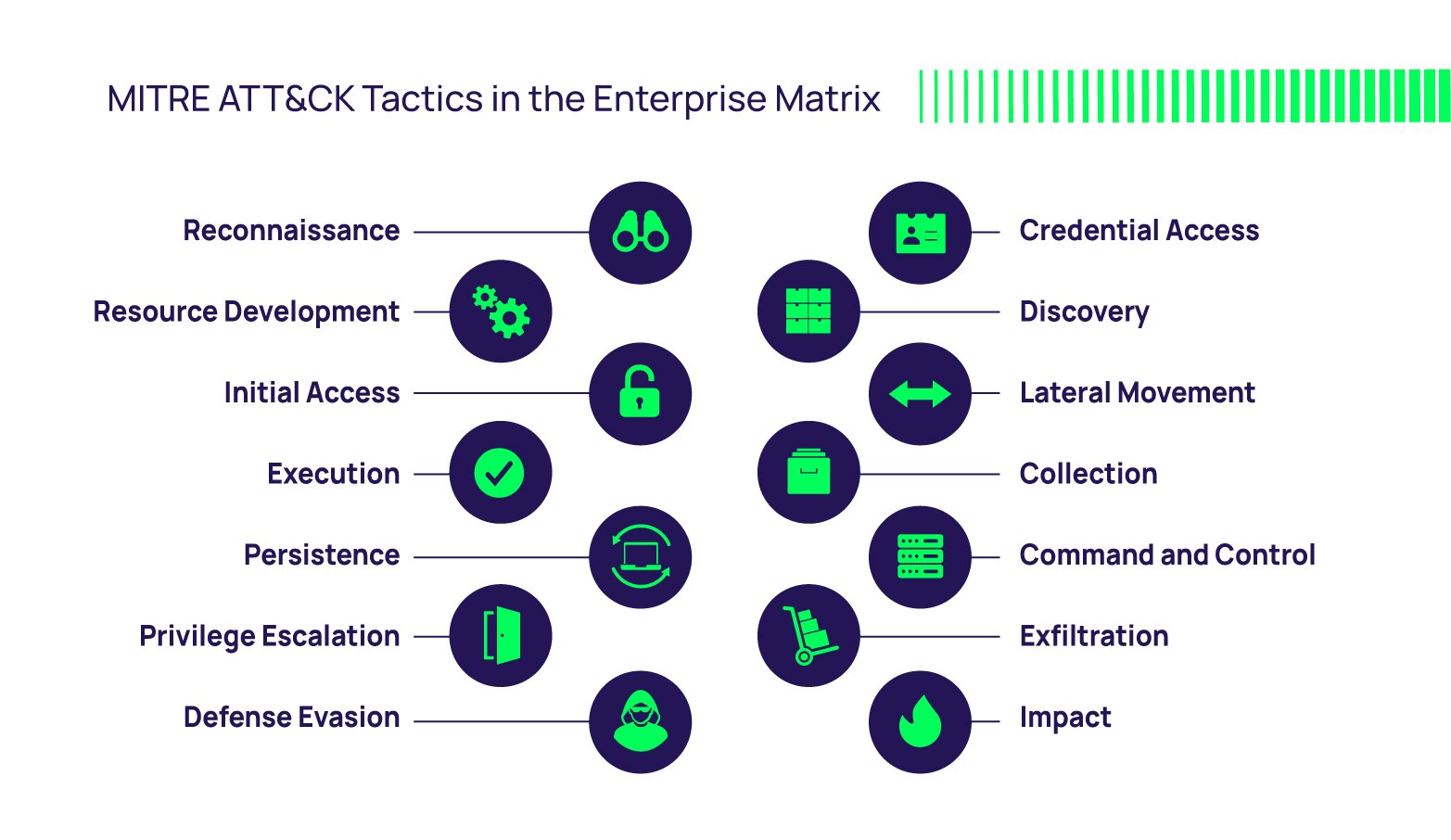
The MITRE ATT&CK Framework
Red Team Assessment, Dubai
Picus Labs analyzed all the 60 stolen FireEye red team tools and

Red Team Tools Detection and Alerting
atomic-red-team/atomics/T1105/T1105.md at master · redcanaryco
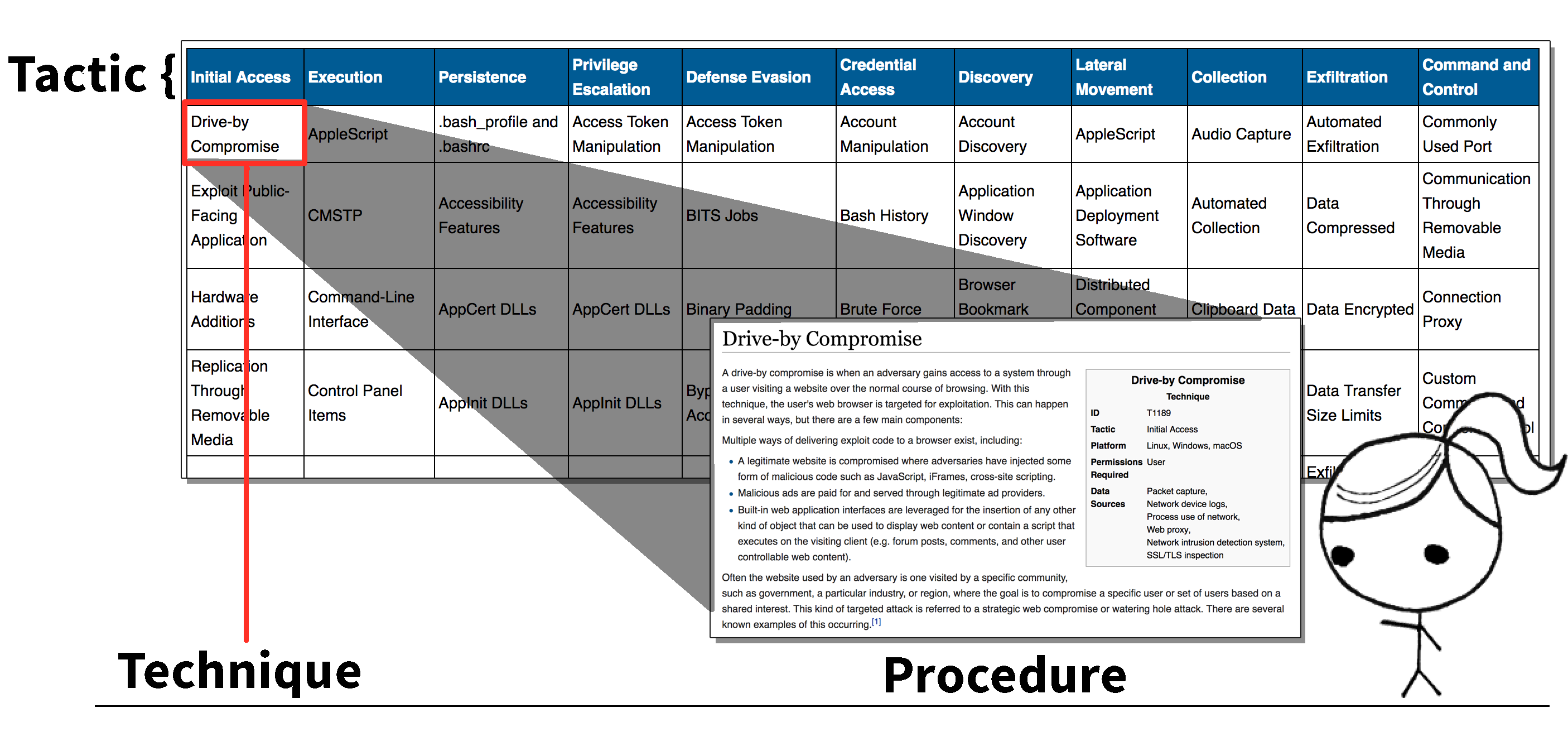
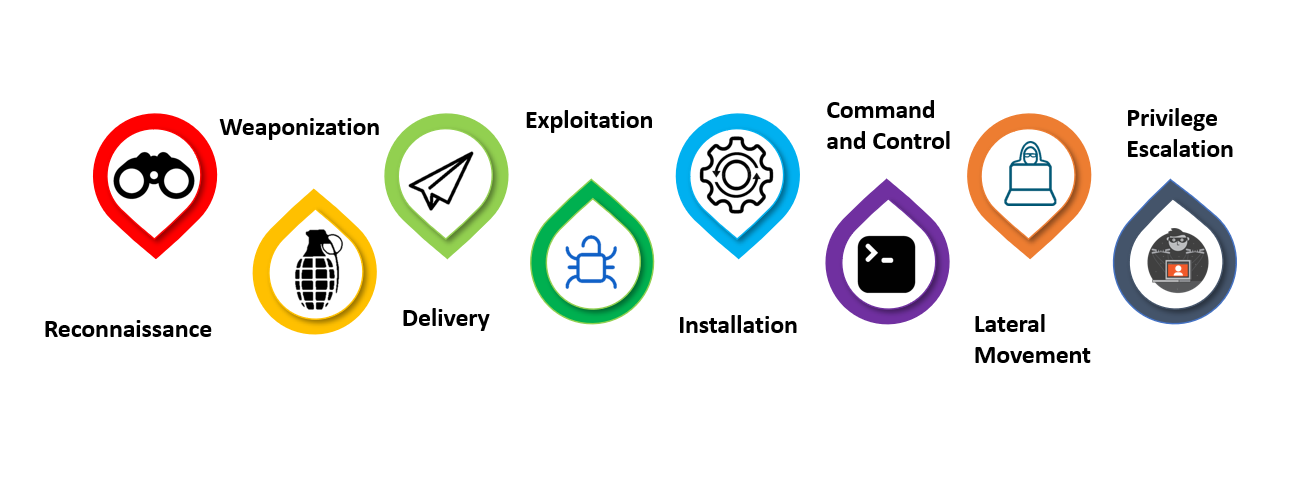
Red Teaming and MITRE ATT&CK Red Team Development and Operations
Recomendado para você
-
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE25 abril 2025
-
 Risk Intelligence & Device Fingerprinting Solution25 abril 2025
Risk Intelligence & Device Fingerprinting Solution25 abril 2025 -
 Spoofers Revealed25 abril 2025
Spoofers Revealed25 abril 2025 -
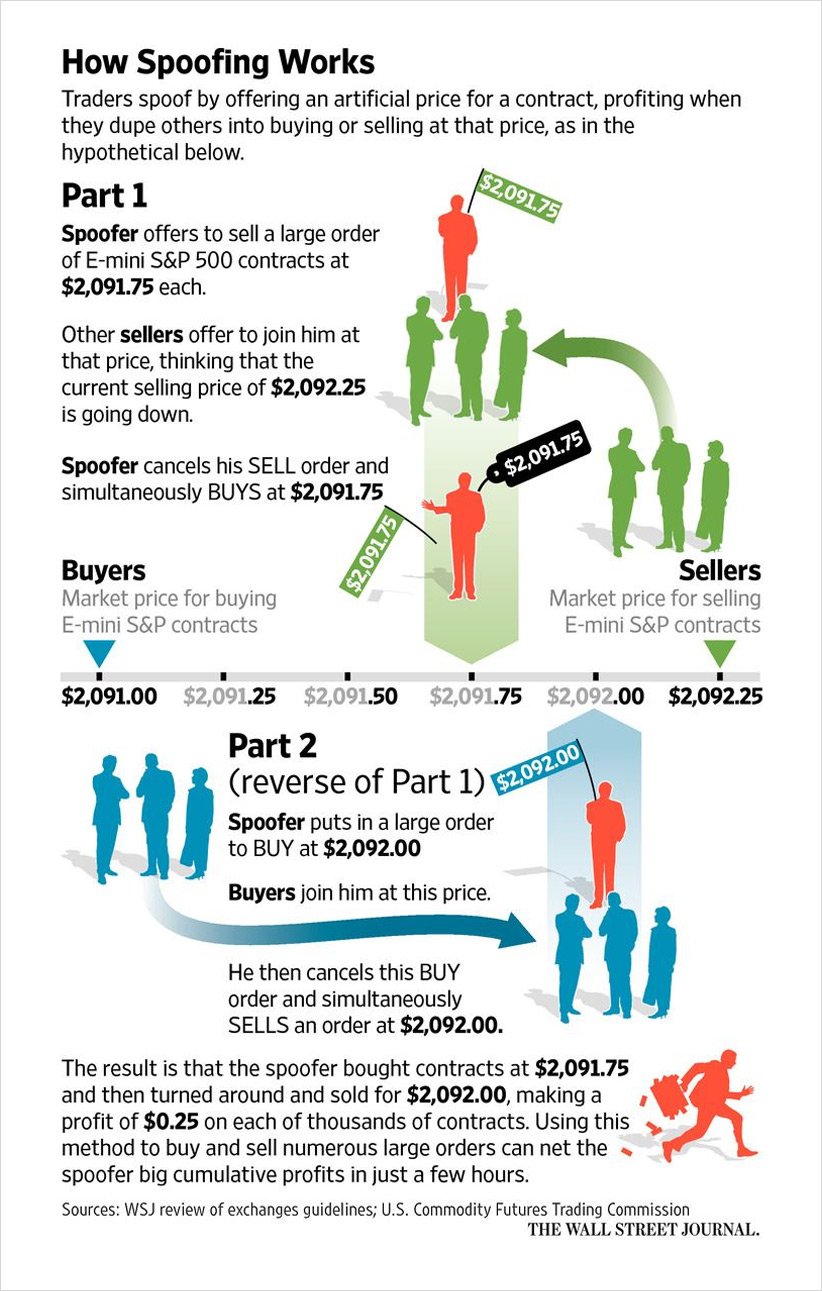 Explaining and Exploring Spoofing - Deribit Insights25 abril 2025
Explaining and Exploring Spoofing - Deribit Insights25 abril 2025 -
 A comprehensive survey on radio frequency (RF) fingerprinting25 abril 2025
A comprehensive survey on radio frequency (RF) fingerprinting25 abril 2025 -
 James the Red Engine, Movie Spoof Films Wikia25 abril 2025
James the Red Engine, Movie Spoof Films Wikia25 abril 2025 -
 Nobody's Fool: Spoofing Detection in a High-Precision Receiver25 abril 2025
Nobody's Fool: Spoofing Detection in a High-Precision Receiver25 abril 2025 -
 Spoofing SaaS Vanity URLs for Social Engineering Attacks25 abril 2025
Spoofing SaaS Vanity URLs for Social Engineering Attacks25 abril 2025 -
![Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)](https://i.imgur.com/6tS6Yxf.png) Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)25 abril 2025
Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)25 abril 2025 -
 Licensing25 abril 2025
Licensing25 abril 2025
você pode gostar
-
 Roblox Rainbow Friends Soft Plush Toy Blue Green Red Yellow Kids, Birth Gift UK25 abril 2025
Roblox Rainbow Friends Soft Plush Toy Blue Green Red Yellow Kids, Birth Gift UK25 abril 2025 -
 WMAC Masters (TV Series 1995–1996) - IMDb25 abril 2025
WMAC Masters (TV Series 1995–1996) - IMDb25 abril 2025 -
 Bubble, novo anime original Netflix ganha trailer e data de25 abril 2025
Bubble, novo anime original Netflix ganha trailer e data de25 abril 2025 -
Apeirofobia25 abril 2025
-
 Lollygag funny word design - Funny Saying - Sticker25 abril 2025
Lollygag funny word design - Funny Saying - Sticker25 abril 2025 -
 Review of Game of Thrones: Winter Is Coming - MMO & MMORPG Games25 abril 2025
Review of Game of Thrones: Winter Is Coming - MMO & MMORPG Games25 abril 2025 -
 Sans With Blue Eye - Sans Pixel Art Wink, HD Png Download - 1184x1184(#4801454) - PngFind25 abril 2025
Sans With Blue Eye - Sans Pixel Art Wink, HD Png Download - 1184x1184(#4801454) - PngFind25 abril 2025 -
 GameDesire on X: Start weekend with Bonus! ;) For every purchase25 abril 2025
GameDesire on X: Start weekend with Bonus! ;) For every purchase25 abril 2025 -
/cdn.vox-cdn.com/uploads/chorus_image/image/71155077/Steam_Deck_coop.0.jpg) Steam Deck, Switch players warned as heat waves cook Japan, Europe - Polygon25 abril 2025
Steam Deck, Switch players warned as heat waves cook Japan, Europe - Polygon25 abril 2025 -
 Arvore Natal Grande Decorada Completa 150cm Com Pisca Luxo25 abril 2025
Arvore Natal Grande Decorada Completa 150cm Com Pisca Luxo25 abril 2025
