Validating User Flows to Protect Software Defined Network Environments
Por um escritor misterioso
Last updated 10 abril 2025

Software Defined Network is a promising network paradigm which has led to several security threats in SDN applications that involve user flows, switches, and controllers in the network. Threats as spoofing, tampering, information disclosure, Denial of Service, flow table overloading, and so on have been addressed by many researchers. In this paper, we present novel SDN design to solve three security threats: flow table overloading is solved by constructing a star topology-based architecture, unsupervised hashing method mitigates link spoofing attack, and fuzzy classifier combined with L1-ELM running on a neural network for isolating anomaly packets from normal packets. For effective flow migration Discrete-Time Finite-State Markov Chain model is applied. Extensive simulations using OMNeT++ demonstrate the performance of our proposed approach, which is better at preserving holding time than are other state-of-the-art works from the literature.
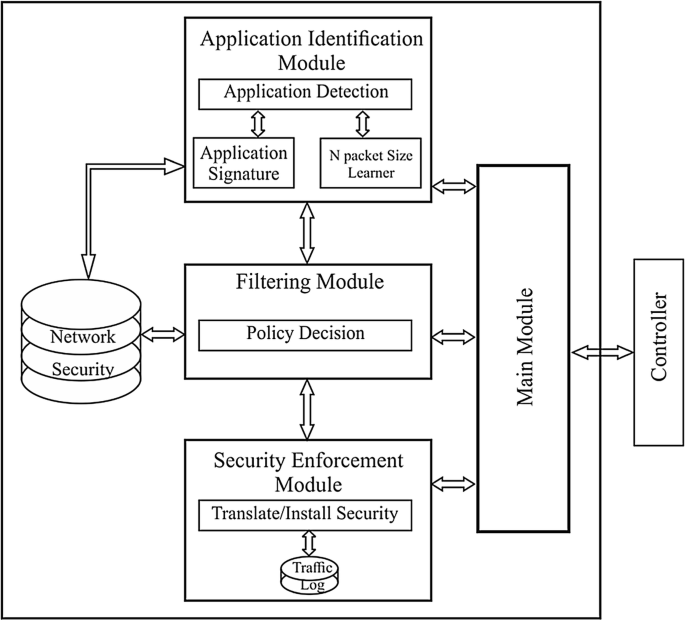
Application-Aware Firewall Mechanism for Software Defined Networks
Applied Sciences, Free Full-Text

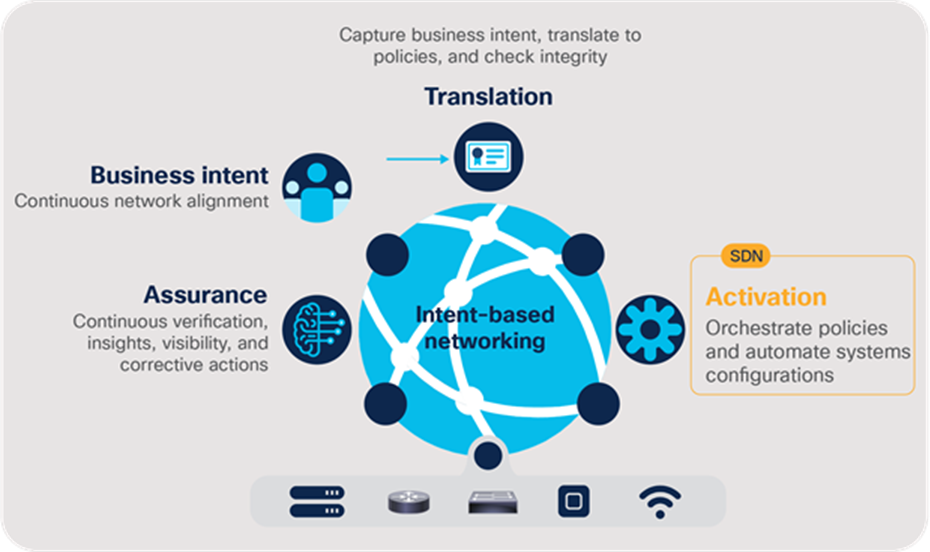
Apstra Intent-Based Networking
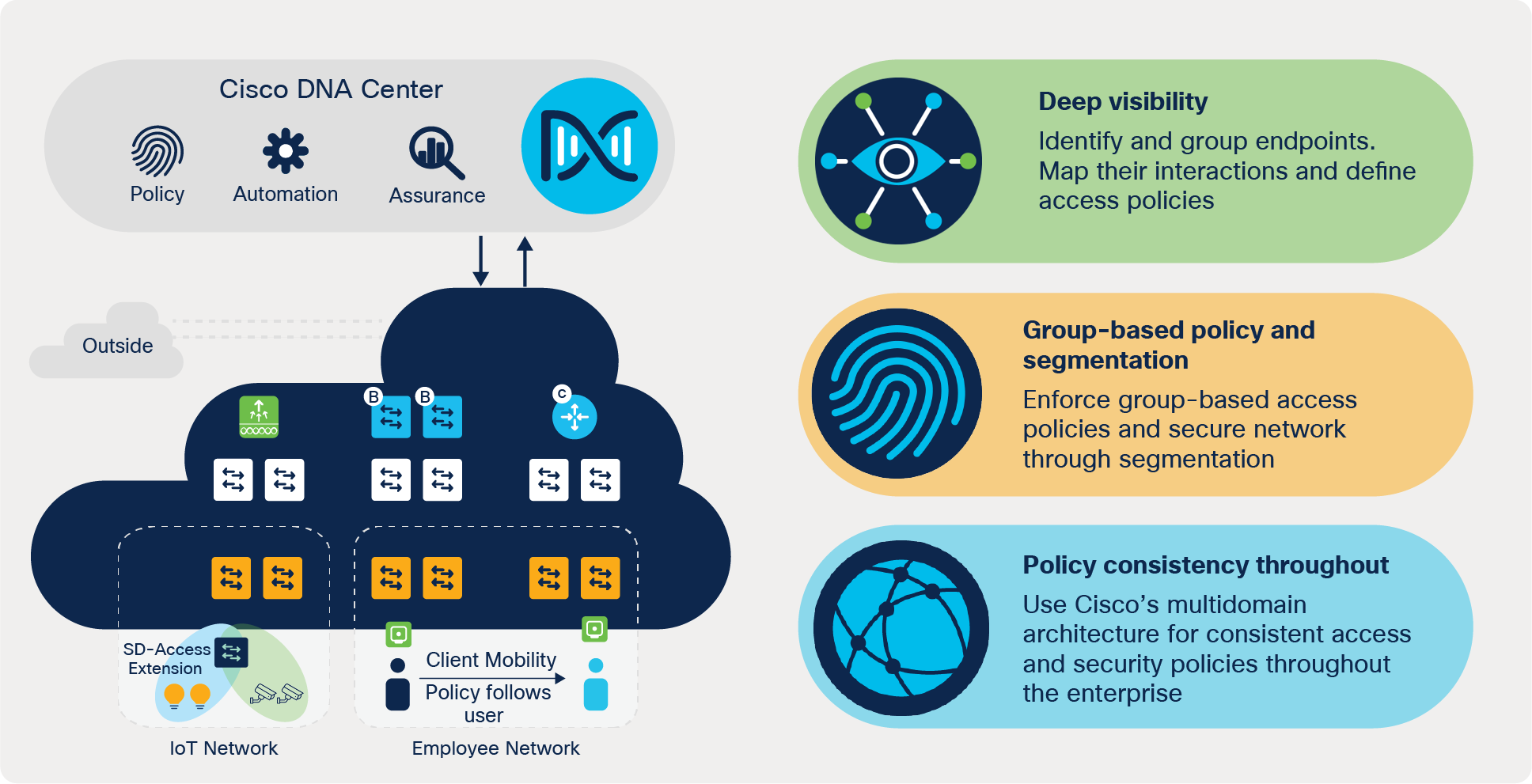
Cisco Software-Defined Access - Cisco Software-Defined Access
Application-Aware Firewall Mechanism for Software Defined Networks

Chapter 6: Maintaining a Secure Environment, Weaving a Secure Web

PDF) Validating User Flows to Protect Software Defined Network
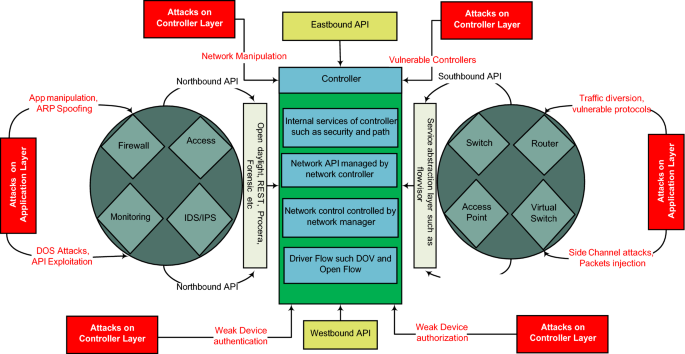
Security & Privacy in Software Defined Networks, Issues
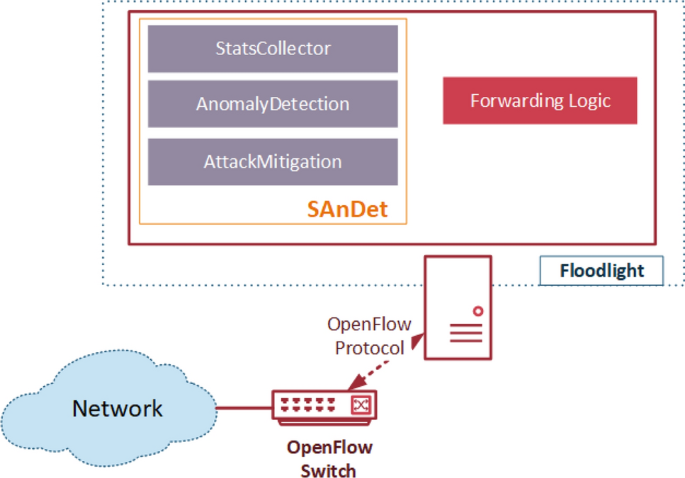
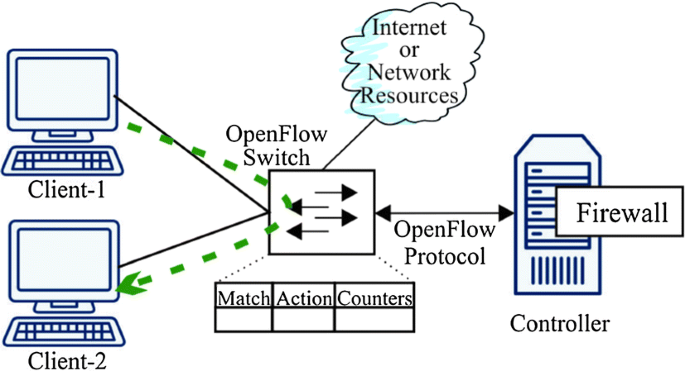
Flow-based intrusion detection on software-defined networks: a

Validating User Flows to Protect Software Defined Network Environments
Cisco Group-Based Policies for Zero-Trust Security White Paper - Cisco
Recomendado para você
-
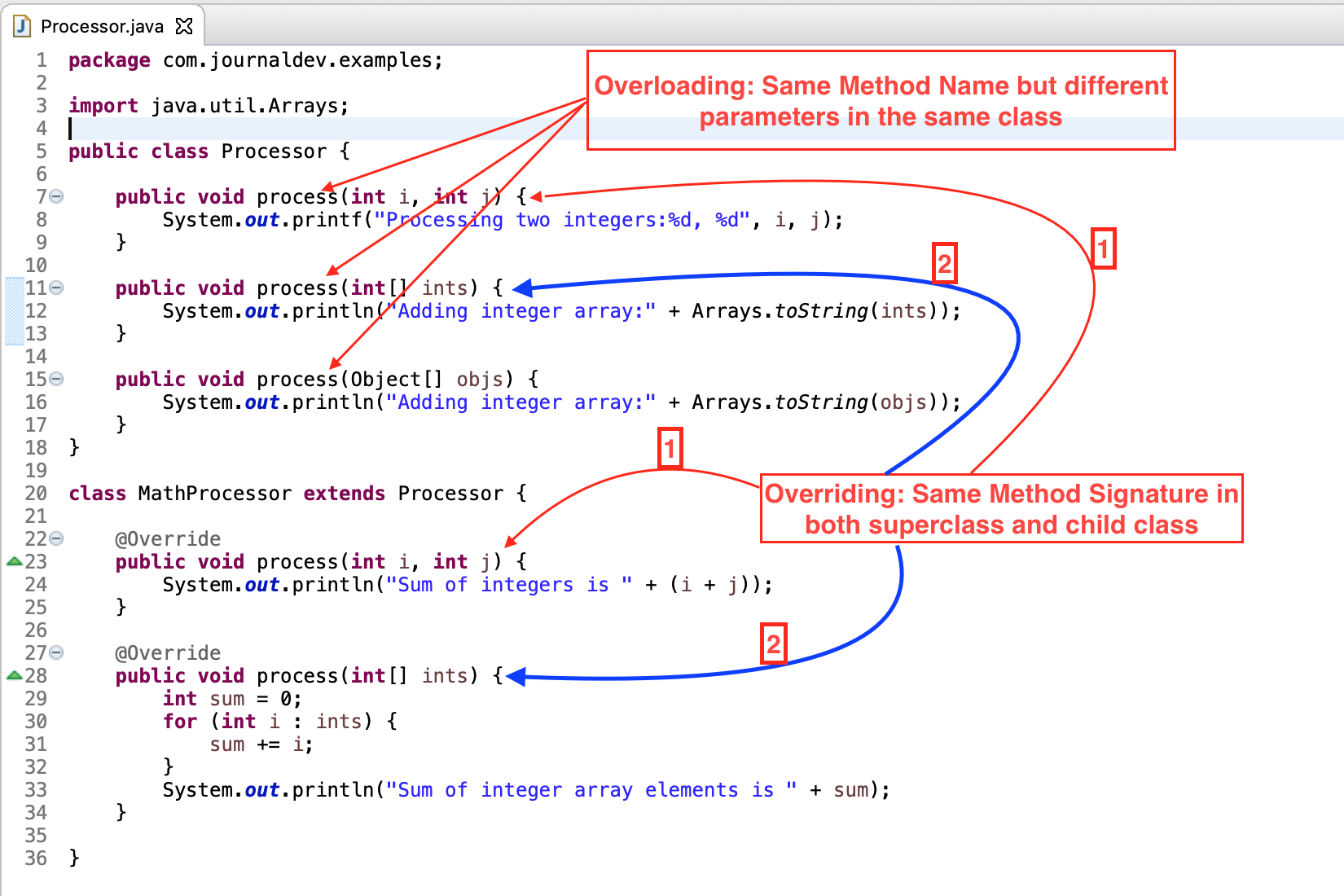 Overriding vs Overloading in Java10 abril 2025
Overriding vs Overloading in Java10 abril 2025 -
 Method Overloading vs Method Overriding in Java10 abril 2025
Method Overloading vs Method Overriding in Java10 abril 2025 -
 Overloading vs. Overriding – Hermes's Blog10 abril 2025
Overloading vs. Overriding – Hermes's Blog10 abril 2025 -
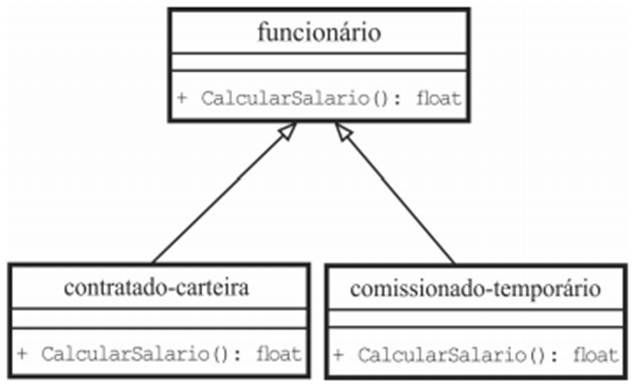 POO: Principal conceito de Polimorfismo10 abril 2025
POO: Principal conceito de Polimorfismo10 abril 2025 -
 Dog poop overloading Coquitlam, B.C. park garbage cans10 abril 2025
Dog poop overloading Coquitlam, B.C. park garbage cans10 abril 2025 -
 Soiling - ERIC10 abril 2025
Soiling - ERIC10 abril 2025 -
To Get To The Bottom Of Your Microbiome, Start With A Swab Of Poo, NPR Article10 abril 2025
-
Physio Sarah Fellows10 abril 2025
-
 Cartões: Orientação a Objetos10 abril 2025
Cartões: Orientação a Objetos10 abril 2025 -
 Cuteness Overloaded Posters for Sale10 abril 2025
Cuteness Overloaded Posters for Sale10 abril 2025
você pode gostar
-
 Buy Middle Earth : Shadow of Mordor Season Pass10 abril 2025
Buy Middle Earth : Shadow of Mordor Season Pass10 abril 2025 -
 Stockfish Dried fish. Salty fish. Smelt. Bichok. 250gram or 8,8oz10 abril 2025
Stockfish Dried fish. Salty fish. Smelt. Bichok. 250gram or 8,8oz10 abril 2025 -
 Drawing Kirby Speedrun 💫⭐, Time Lapse Drawing via Photoshop 🤩 #kirby10 abril 2025
Drawing Kirby Speedrun 💫⭐, Time Lapse Drawing via Photoshop 🤩 #kirby10 abril 2025 -
 Sonic Advance Sprites Download - Colaboratory10 abril 2025
Sonic Advance Sprites Download - Colaboratory10 abril 2025 -
 Free Fire MAX will be released globally on Sept. 28 - Dot Esports10 abril 2025
Free Fire MAX will be released globally on Sept. 28 - Dot Esports10 abril 2025 -
 Shiny Pokemon GO Articuno, Zapdos, Moltres: Back In The Game, Soon10 abril 2025
Shiny Pokemon GO Articuno, Zapdos, Moltres: Back In The Game, Soon10 abril 2025 -
total drama comic studio how to get it|TikTok Search10 abril 2025
-
Bluetooth para Opel Grijó E Sermonde • OLX Portugal10 abril 2025
-
 ArtStation - Vegeta Sacrifice10 abril 2025
ArtStation - Vegeta Sacrifice10 abril 2025 -
 Juventude anuncia o meio-campista Wesley Hudson, ex-Atlético - Superesportes10 abril 2025
Juventude anuncia o meio-campista Wesley Hudson, ex-Atlético - Superesportes10 abril 2025


