Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 14 abril 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %
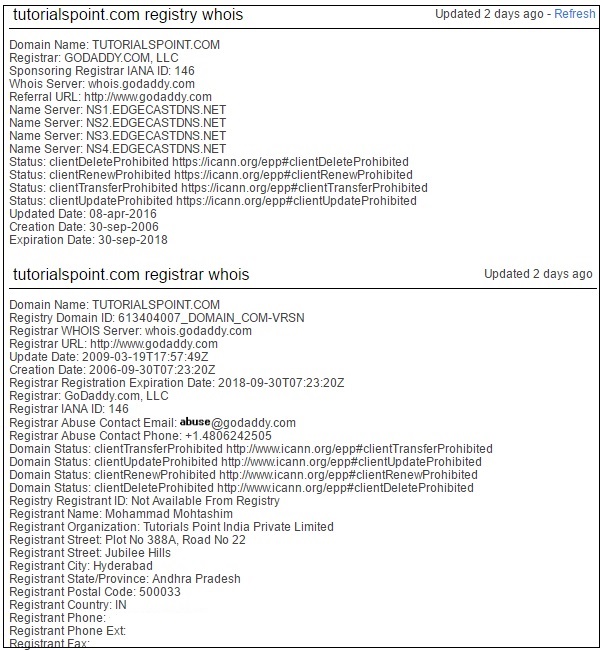
Ethical Hacking - Quick Guide
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy
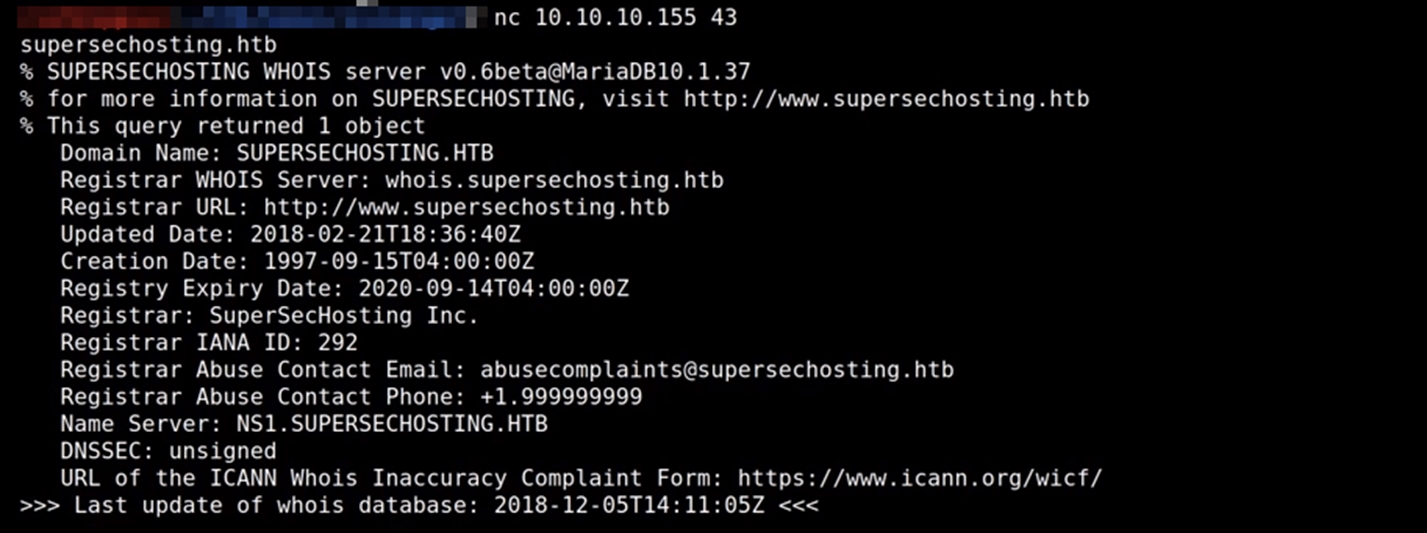
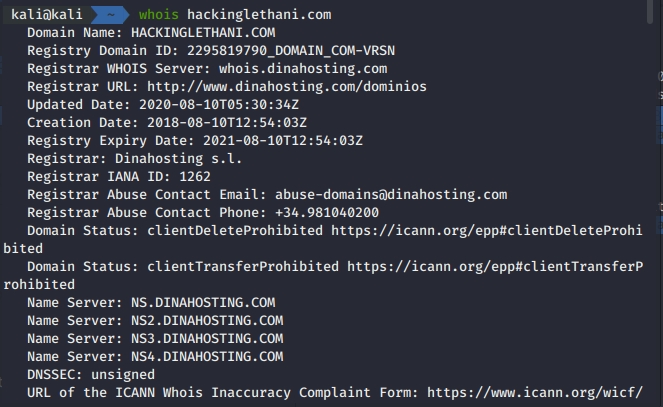
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
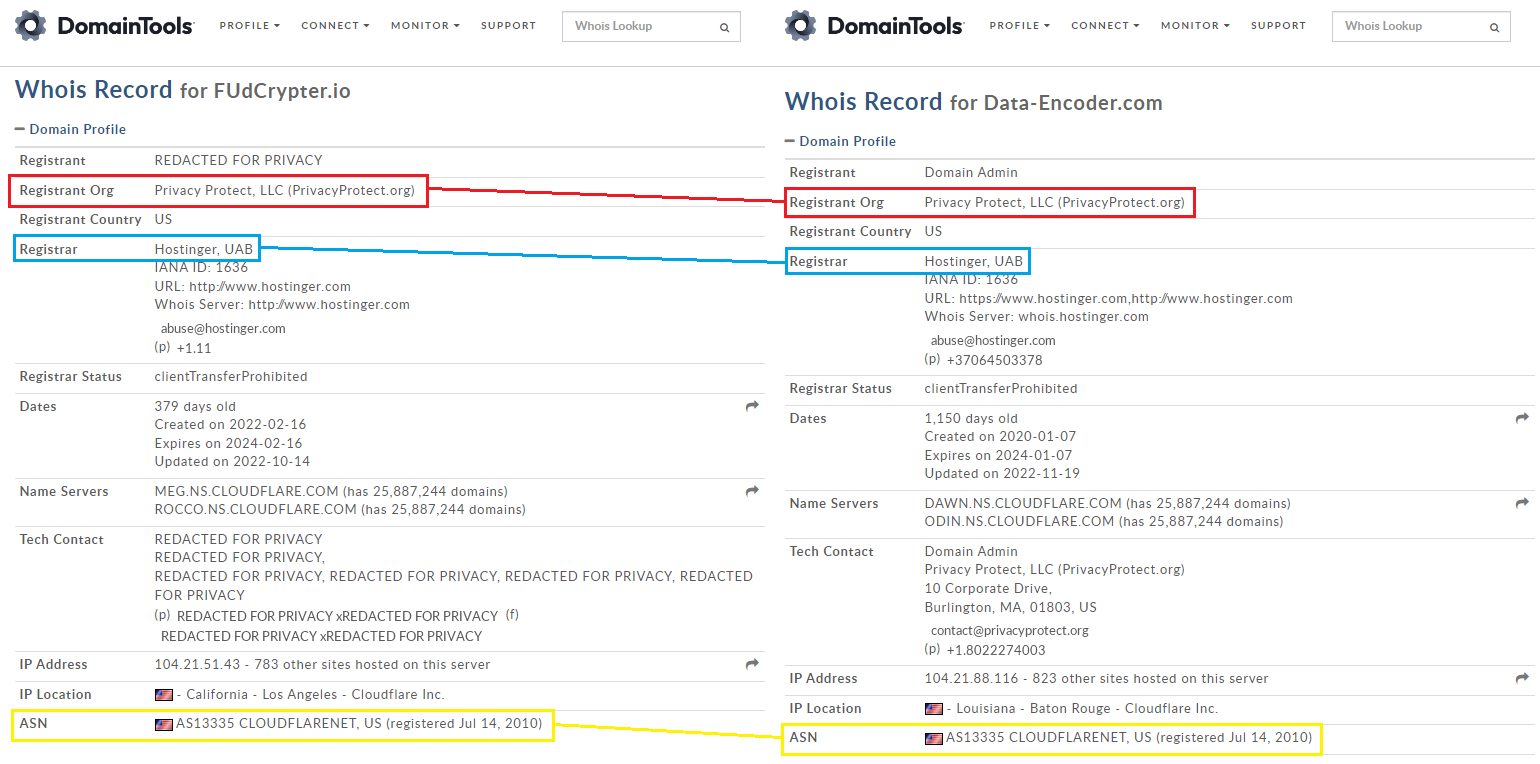
Tips for Investigating Cybercrime Infrastructure

Hackbun

Connecting All the World's Users in an Open Way: Decentralized Authentication with Brooklyn Zelenka

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

How did I create hacking rig for ethical hacking. Based on VMware with Tesla M60. #infosec #hacking #pentest #pentesting #redteam #hackthebox #tryhackme #linux4hackers #ctf #kali #parrotos #linux #godaddy #linux4hackers – Tips and

Predictable wins: designing for data breach containment - TechHQ

Killnet Claim They've Stolen Employee Data from Lockheed Martin

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Whois Lookup Ethical Hacking
Recomendado para você
-
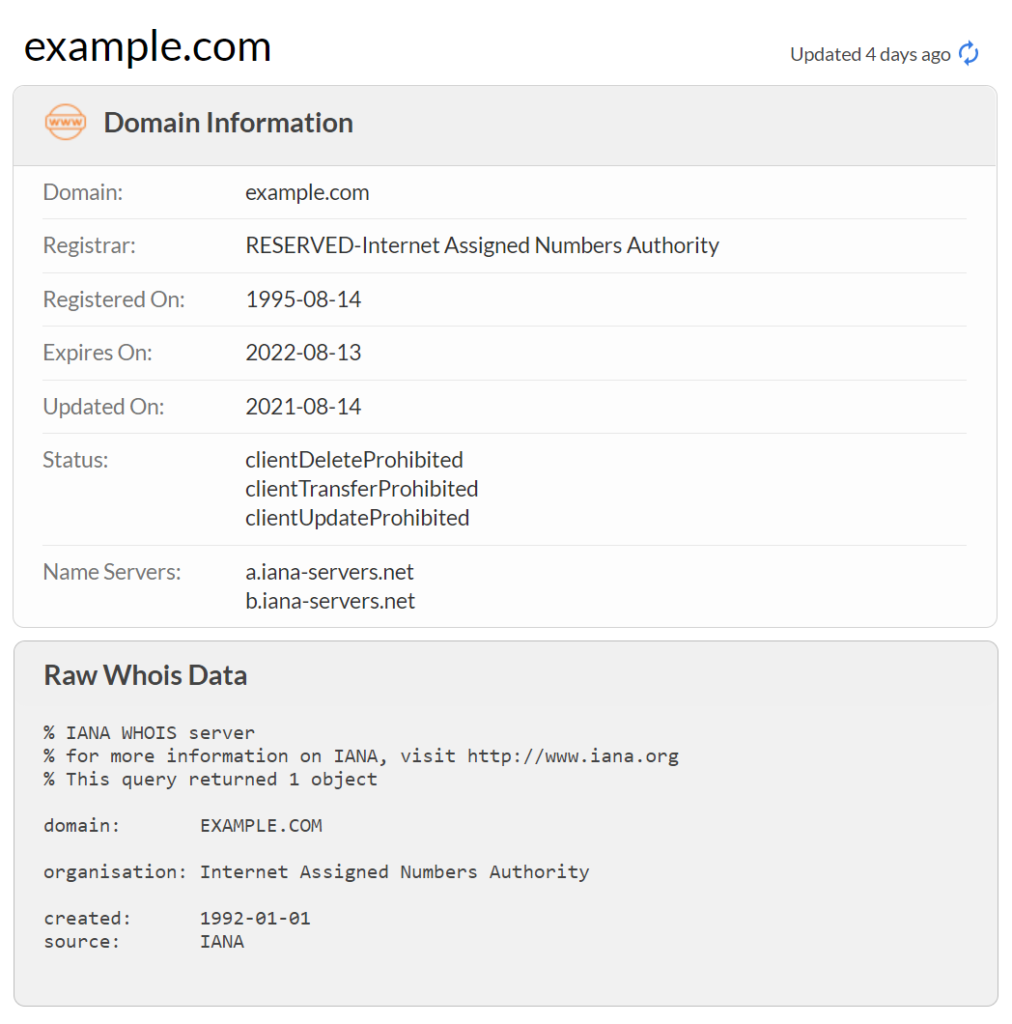 What Is WHOIS and How Does It Work? - IPXO14 abril 2025
What Is WHOIS and How Does It Work? - IPXO14 abril 2025 -
 Whois ( “who owns a domain?”), by Hacksheets14 abril 2025
Whois ( “who owns a domain?”), by Hacksheets14 abril 2025 -
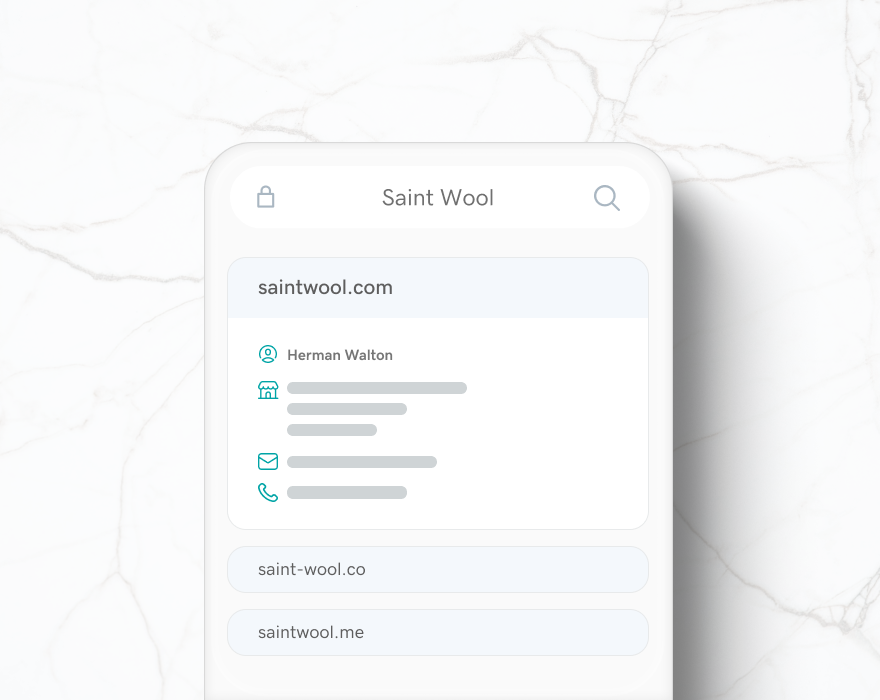 WHOIS Domain Lookup - Find out who owns a website - GoDaddy14 abril 2025
WHOIS Domain Lookup - Find out who owns a website - GoDaddy14 abril 2025 -
 What is WHOIS and How Does it Work? (+ Tips on Free Domain Privacy)14 abril 2025
What is WHOIS and How Does it Work? (+ Tips on Free Domain Privacy)14 abril 2025 -
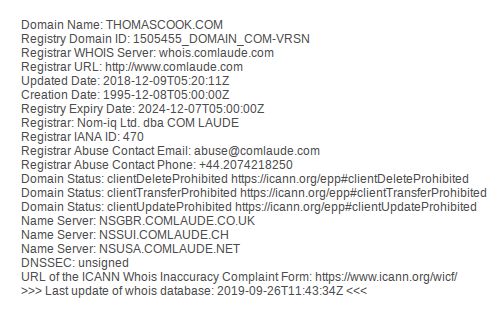 Nixintel Open Source Intelligence & Investigations Search Tip14 abril 2025
Nixintel Open Source Intelligence & Investigations Search Tip14 abril 2025 -
 How to Find a Domain Name Owner w/ WHOIS Lookup (for free)14 abril 2025
How to Find a Domain Name Owner w/ WHOIS Lookup (for free)14 abril 2025 -
 Whois IP Lookup – free online whois tool14 abril 2025
Whois IP Lookup – free online whois tool14 abril 2025 -
 macos - WHOIS in Mac OS terminal not doing anything - Stack Overflow14 abril 2025
macos - WHOIS in Mac OS terminal not doing anything - Stack Overflow14 abril 2025 -
 File:Whois Mushoku Tensei screenshot.png - Wikipedia14 abril 2025
File:Whois Mushoku Tensei screenshot.png - Wikipedia14 abril 2025 -
 Who is WHOIS?14 abril 2025
Who is WHOIS?14 abril 2025
você pode gostar
-
 First Impression: EDENS ZERO S2 – Beneath the Tangles14 abril 2025
First Impression: EDENS ZERO S2 – Beneath the Tangles14 abril 2025 -
 Love of Kill, Vol. 5 : Fe, Fe: : Livres14 abril 2025
Love of Kill, Vol. 5 : Fe, Fe: : Livres14 abril 2025 -
 50 palavras sem tradução português14 abril 2025
50 palavras sem tradução português14 abril 2025 -
 5 fatos polêmicos sobre cachorro-quente - Gastronomia Carioca14 abril 2025
5 fatos polêmicos sobre cachorro-quente - Gastronomia Carioca14 abril 2025 -
 Domestic na Kanojo Ep. 2: Shockingly dull14 abril 2025
Domestic na Kanojo Ep. 2: Shockingly dull14 abril 2025 -
Animes New World14 abril 2025
-
 Foxy, Five Nights At Freddy's Wiki14 abril 2025
Foxy, Five Nights At Freddy's Wiki14 abril 2025 -
Wild Shiny Venusaur!!!14 abril 2025
-
Bolo Masculino 💙 #boloazul #bolomasculino #bolomasculinochantilly #co14 abril 2025
-
 Teoria) A Ilha do Começo e do Fim: Laugh Tale14 abril 2025
Teoria) A Ilha do Começo e do Fim: Laugh Tale14 abril 2025