Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 11 abril 2025
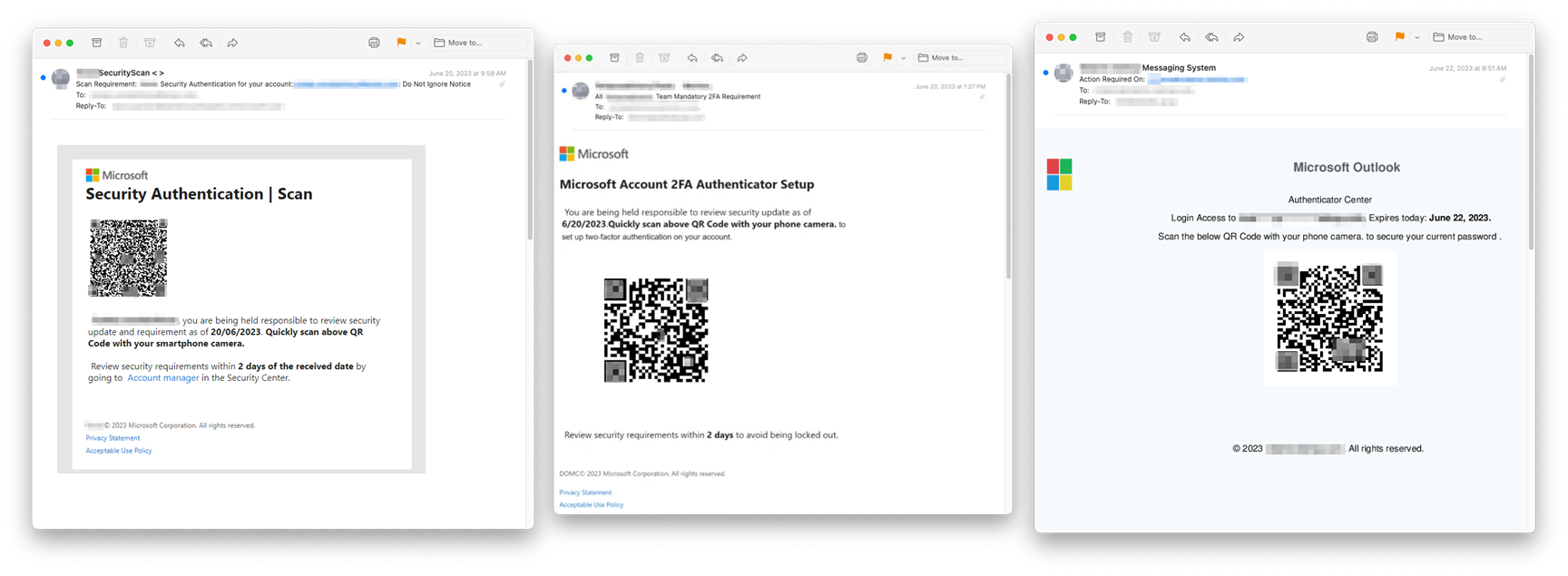
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
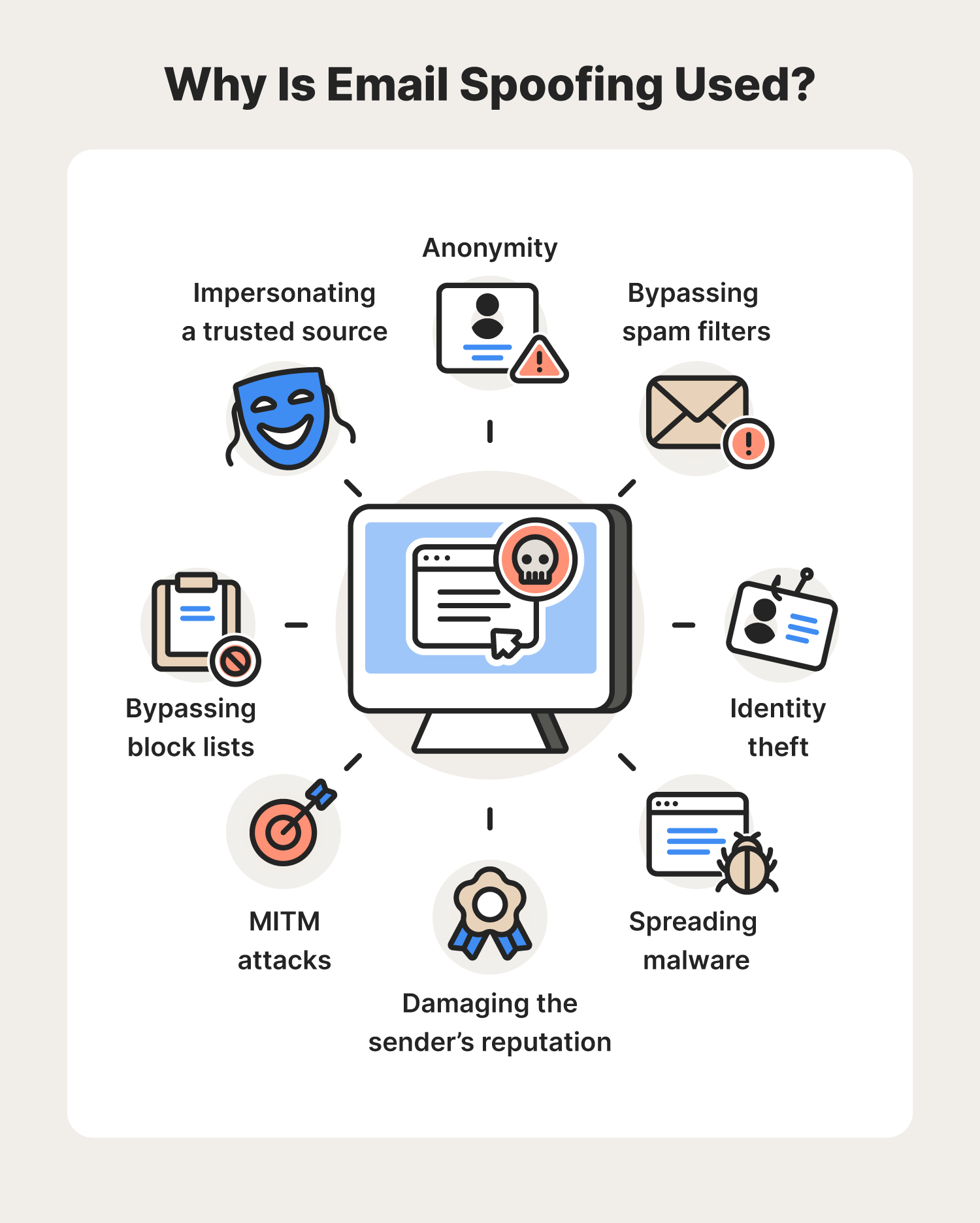
What is email spoofing? A complete guide - Norton

VIPRE finds 233.9 million malicious emails detected in Q3 2023

Four Ways Hackers are Outsmarting Retail Cybersecurity - Retail TouchPoints

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks

Fileless attacks surge as cybercriminals evade cloud security defenses

Credentials for cybercrime forums found on roughly 120K computers infected with info stealers

Cybercriminals use reverse tunneling and URL shorteners to launch 'virtually undetectable' phishing campaigns

Cybercriminals used 3 new tactics for phishing users in January 2023

9 in 10 companies have experienced AI-enhanced email attacks, and continued use of AI will open up more risks—here's what you should know - Agility PR Solutions

Fast Flux 101: How Cybercriminals Improve the Resilience of Their Infrastructure to Evade Detection and Law Enforcement Takedowns

Phishing MFA is compromising big company networks

How to avoid online scams — and how Emory can help
Recomendado para você
-
 Evade codes December 202311 abril 2025
Evade codes December 202311 abril 2025 -
 Roblox Evade – Free codes (December 2023) - Xfire11 abril 2025
Roblox Evade – Free codes (December 2023) - Xfire11 abril 2025 -
 Roblox music codes, The best song IDs to use11 abril 2025
Roblox music codes, The best song IDs to use11 abril 2025 -
 Roblox Pls Donate Codes (June 2023) - Prima Games11 abril 2025
Roblox Pls Donate Codes (June 2023) - Prima Games11 abril 2025 -
 Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT11 abril 2025
Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT11 abril 2025 -
 Roblox Baby Simulator Codes (November 2023)11 abril 2025
Roblox Baby Simulator Codes (November 2023)11 abril 2025 -
 All Evade Codes(Roblox) - Tested December 2022 - Player Assist11 abril 2025
All Evade Codes(Roblox) - Tested December 2022 - Player Assist11 abril 2025 -
Data Encoder Crypter11 abril 2025
-
 Deena So'Oteh11 abril 2025
Deena So'Oteh11 abril 2025 -
 BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis11 abril 2025
BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis11 abril 2025
você pode gostar
-
 Kit com Jogos Clássico 5x1 Dominó Ludo Loto Damas Trilha Xalingo11 abril 2025
Kit com Jogos Clássico 5x1 Dominó Ludo Loto Damas Trilha Xalingo11 abril 2025 -
 Summoner Wars11 abril 2025
Summoner Wars11 abril 2025 -
 Thor Odinson (Marvel Cinematic Universe), Heroes Wiki11 abril 2025
Thor Odinson (Marvel Cinematic Universe), Heroes Wiki11 abril 2025 -
 Alice In Wonderland Ceramic Tile Art Meets Dodo Bird Color11 abril 2025
Alice In Wonderland Ceramic Tile Art Meets Dodo Bird Color11 abril 2025 -
 The Fantastic Four: 2021-22 Championship Play-off Preview11 abril 2025
The Fantastic Four: 2021-22 Championship Play-off Preview11 abril 2025 -
 Pin by Mike Zenie on • SCP •11 abril 2025
Pin by Mike Zenie on • SCP •11 abril 2025 -
:max_bytes(150000):strip_icc()/how-to-store-peaches-ffc593efa21d4defa0abf96c21041414.jpg) How to Store Peaches11 abril 2025
How to Store Peaches11 abril 2025 -
 ZQM Hang A Picture Dragon Age Origins Dragon Canvas11 abril 2025
ZQM Hang A Picture Dragon Age Origins Dragon Canvas11 abril 2025 -
 Black Adam - Jovem Nerd11 abril 2025
Black Adam - Jovem Nerd11 abril 2025 -
 Comprar Razer Gold PIN Brazil - R$ 100 - Trivia PW11 abril 2025
Comprar Razer Gold PIN Brazil - R$ 100 - Trivia PW11 abril 2025
