Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 10 abril 2025

Describing activities of a crime group attacking Ukraine.

Vault 7 - Wikipedia
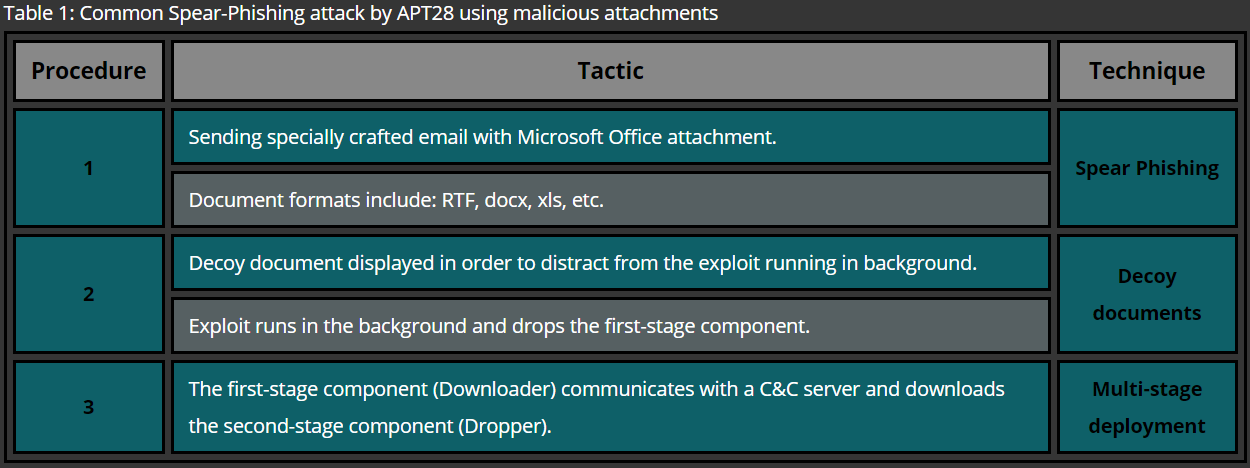
Initial Compromise

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense

What is Authentication Attack? - GeeksforGeeks

The Rise of Initial Access Brokers - ReliaQuest
US7814533B2 - Secure customer interface for Web based data management - Google Patents

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Ukraine is under attack by hacking tools repurposed from Conti cybercrime group

US6968571B2 - Secure customer interface for web based data management - Google Patents

You could be hacked and not know it - Storcom, Lombard, Illinois, United States of America

Security in product lifecycle of IoT devices: A survey - ScienceDirect

Hacking Archives - Page 7 of 15 - HaXeZ
Recomendado para você
-
![The 7 Most Useful Data Analysis Techniques [2024 Guide]](https://d3mm2s9r15iqcv.cloudfront.net/en/wp-content/uploads/2021/01/data-analysis-qualitative-quantitative.jpg) The 7 Most Useful Data Analysis Techniques [2024 Guide]10 abril 2025
The 7 Most Useful Data Analysis Techniques [2024 Guide]10 abril 2025 -
Analysis Group10 abril 2025
-
 Analysis Group Announces Senior-Level Promotions and Lateral Hires10 abril 2025
Analysis Group Announces Senior-Level Promotions and Lateral Hires10 abril 2025 -
 Analysis Group Careers and Employment10 abril 2025
Analysis Group Careers and Employment10 abril 2025 -
Analysis Group HealthEconomics.com Jobs Portal10 abril 2025
-
 Analysis Group - P&R Desjardins10 abril 2025
Analysis Group - P&R Desjardins10 abril 2025 -
 Working at Analysis Group10 abril 2025
Working at Analysis Group10 abril 2025 -
 Active North Korean campaign targeting security researchers10 abril 2025
Active North Korean campaign targeting security researchers10 abril 2025 -
 Job Listings at Analysis Group, Inc.10 abril 2025
Job Listings at Analysis Group, Inc.10 abril 2025 -
 Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts10 abril 2025
Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts10 abril 2025
você pode gostar
-
Pista Infantil Carrinho E Adesivos Pista Track Race Infantil Hot Carrinho E Adesivo Trilha Maluca Carrinho Pista De Carrinhos Com Acessórios Pista10 abril 2025
-
2D Dominus Azurelight Eyes10 abril 2025
-
 Pin de Ban kai em Tejina-Senpai Magical Sempai10 abril 2025
Pin de Ban kai em Tejina-Senpai Magical Sempai10 abril 2025 -
 Resident Evil 3 Mod Adds The Last of Us Part 2 Cast - Siliconera10 abril 2025
Resident Evil 3 Mod Adds The Last of Us Part 2 Cast - Siliconera10 abril 2025 -
AGEITANDO MINHA BONECA NO (ROBLOX)10 abril 2025
-
 Conjunto Garoando faz show na Galeria Olido10 abril 2025
Conjunto Garoando faz show na Galeria Olido10 abril 2025 -
 10 Animes que só vale a pena assistir uma vez – Geeks In Action- Sua fonte de recomendações e entretenimento!10 abril 2025
10 Animes que só vale a pena assistir uma vez – Geeks In Action- Sua fonte de recomendações e entretenimento!10 abril 2025 -
 Crypto friendly Xapo Bank launches stocks investment feature - CityAM10 abril 2025
Crypto friendly Xapo Bank launches stocks investment feature - CityAM10 abril 2025 -
 Rap Do Minato ( Naruto ) QUARTO HOKAGE TORNEIO TON HITS10 abril 2025
Rap Do Minato ( Naruto ) QUARTO HOKAGE TORNEIO TON HITS10 abril 2025 -
Vitória de Naruto contra Neji Dublado - Vídeo Dailymotion10 abril 2025


