Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 07 abril 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

How cybercriminals evade mobile app store security measures

Google says attackers are still using versioning to bypass Play

WakeUp Wednesday » Tesorion Cybersecurity Solutions

Analysis of dynamic code updating in Android with security

DLLSpy – Tighten Your Defense by Discovering DLL Hijacking Easily

Dynamic analysis and tampering
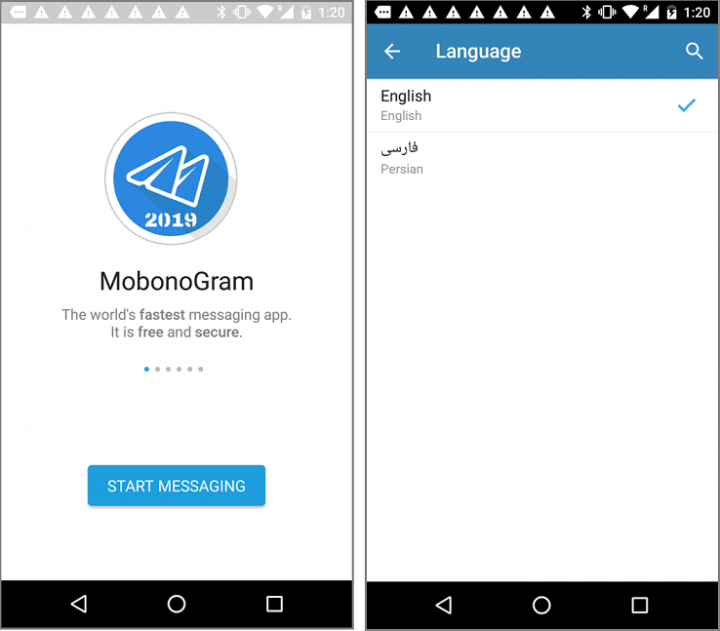
Unofficial Telegram App Secretly Loads Infinite Malicious Sites
TIB AV-Portal

Attackers uses repackaging to publish forged applications on

Basic principle of code reuse attacks. For simplicity, we
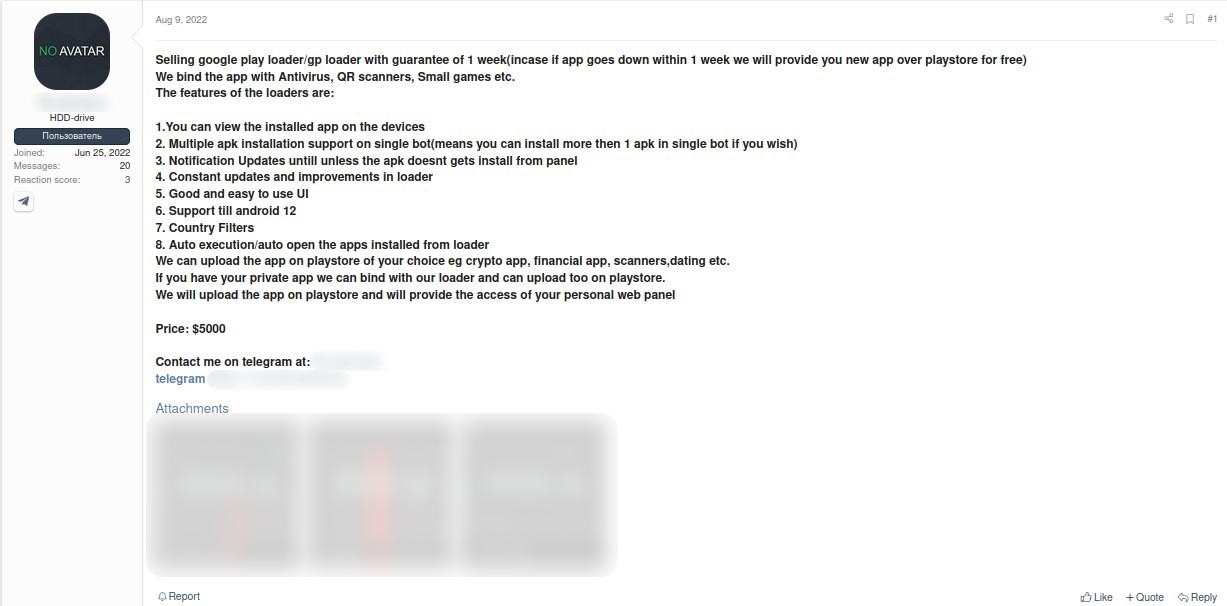
Google Play threat market: overview of dark web offers

What Is Rootkit?

ROC curve for malware detection using feature hashing on

Cybersecurity News: June 19-25 Day 2021
Recomendado para você
-
Codes, Roblox Evade Wiki07 abril 2025
-
 Evolution Evade Codes - Try Hard Guides07 abril 2025
Evolution Evade Codes - Try Hard Guides07 abril 2025 -
 Evade: Nextbbot chasing Codes in 202307 abril 2025
Evade: Nextbbot chasing Codes in 202307 abril 2025 -
 All Evade Codes For November 2023 - GameRiv07 abril 2025
All Evade Codes For November 2023 - GameRiv07 abril 2025 -
 Dodgy MFA Email Notice Uses QR Codes To Evade Detection07 abril 2025
Dodgy MFA Email Notice Uses QR Codes To Evade Detection07 abril 2025 -
 Stranger Danger - Self-Defense, Escape & Evade07 abril 2025
Stranger Danger - Self-Defense, Escape & Evade07 abril 2025 -
 NEW* ALL WORKING CODES FOR EVADE IN MAY 2023! ROBLOX EVADE CODES07 abril 2025
NEW* ALL WORKING CODES FOR EVADE IN MAY 2023! ROBLOX EVADE CODES07 abril 2025 -
Data Encoder Crypter07 abril 2025
-
 Evade codes December 202307 abril 2025
Evade codes December 202307 abril 2025 -
 Best Roblox music codes (December 2023) – How to redeem song IDs07 abril 2025
Best Roblox music codes (December 2023) – How to redeem song IDs07 abril 2025
você pode gostar
-
 Malphite · Skin Explorer07 abril 2025
Malphite · Skin Explorer07 abril 2025 -
Steam Workshop::qwertyuiop[]asdfghjkl;'zxcvbnm,./07 abril 2025
-
 Clock-tower-zelda-majoras-mask GIFs - Get the best GIF on GIPHY07 abril 2025
Clock-tower-zelda-majoras-mask GIFs - Get the best GIF on GIPHY07 abril 2025 -
/cloudfront-us-east-1.images.arcpublishing.com/gray/47ZOHHIQRVNTNABRUP27DYVC4A.jpg) The 2023 Masters Tournament 2023 Odds: Shane Lowry07 abril 2025
The 2023 Masters Tournament 2023 Odds: Shane Lowry07 abril 2025 -
 CS2 vs. CS:GO – What's new? What are the differences?07 abril 2025
CS2 vs. CS:GO – What's new? What are the differences?07 abril 2025 -
 Como usar filtros das transmissões ao vivo (lives) fora do07 abril 2025
Como usar filtros das transmissões ao vivo (lives) fora do07 abril 2025 -
 Feiticeiro do Abismo Hydro (Chamado Sagrado dos Sete)07 abril 2025
Feiticeiro do Abismo Hydro (Chamado Sagrado dos Sete)07 abril 2025 -
 Lugia Pokemon PNG Transparent Background, Free Download #18168 - FreeIconsPNG07 abril 2025
Lugia Pokemon PNG Transparent Background, Free Download #18168 - FreeIconsPNG07 abril 2025 -
 Condado, Acervo de Jogos07 abril 2025
Condado, Acervo de Jogos07 abril 2025 -
 ARTE COM QUIANE - Paps e Moldes de Artesanato : Etiquetas de Natal07 abril 2025
ARTE COM QUIANE - Paps e Moldes de Artesanato : Etiquetas de Natal07 abril 2025


![Steam Workshop::qwertyuiop[]asdfghjkl;'zxcvbnm,./](https://steamuserimages-a.akamaihd.net/ugc/1834653127246617858/8E8546BA26A464A0D8EE522A67B74E79CC0BA89A/?imw=200&imh=200&ima=fit&impolicy=Letterbox&imcolor=%23000000&letterbox=true)