11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 11 abril 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

15 Types of Cyber Attacks You Should Be Aware in 2023
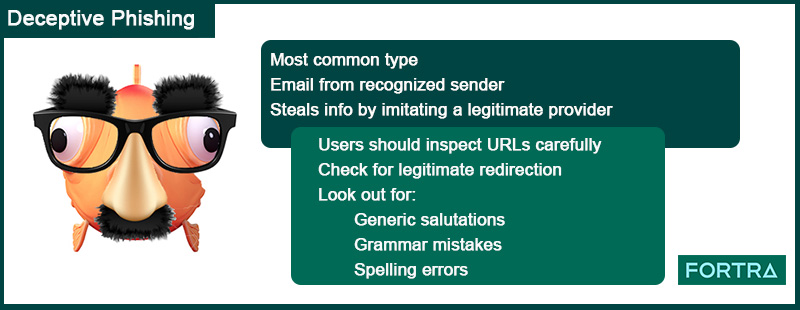
6 Common Phishing Attacks and How to Protect Against Them

What Is Spoofing? And How To Avoid An Attack - StoneLock
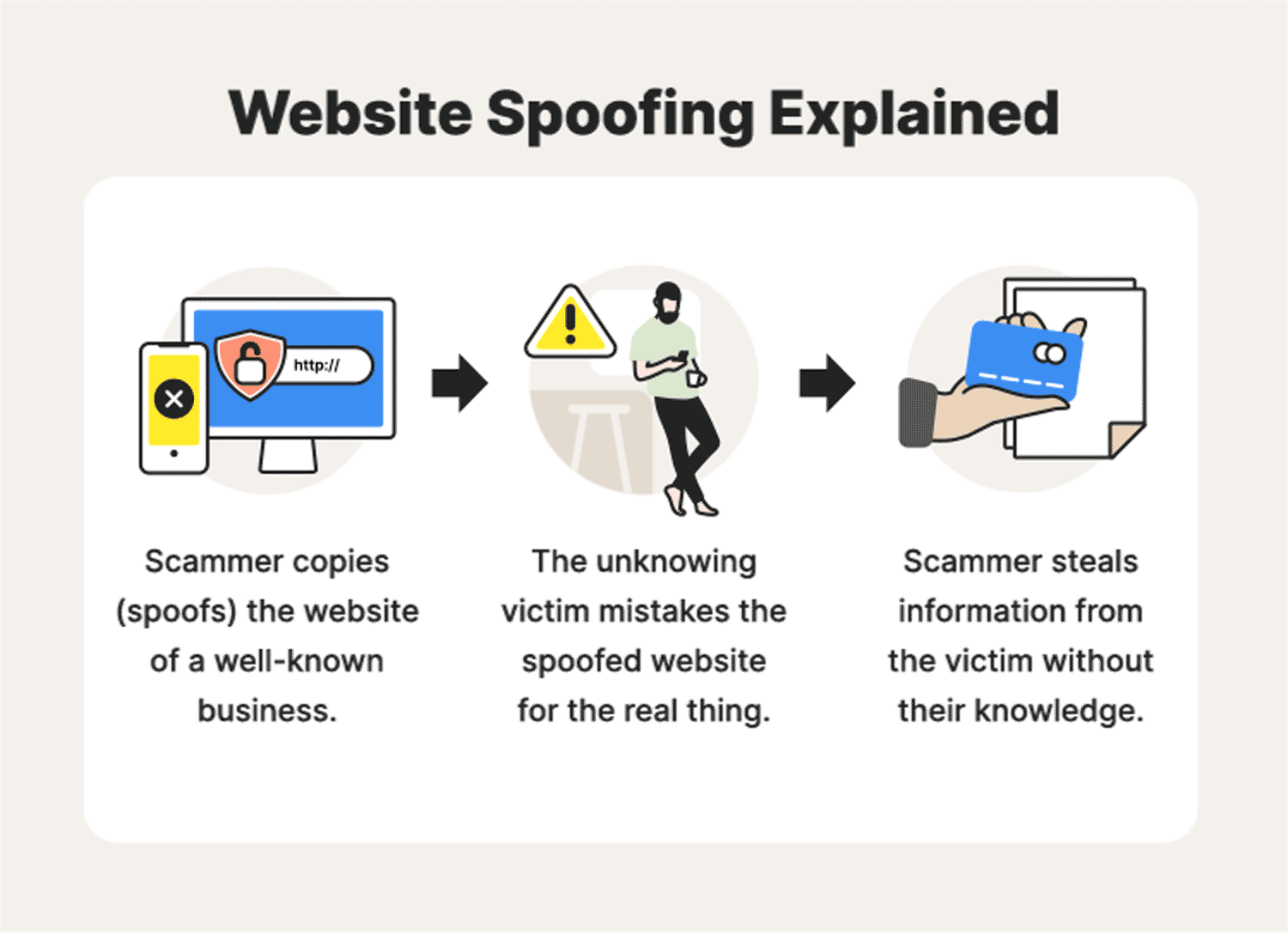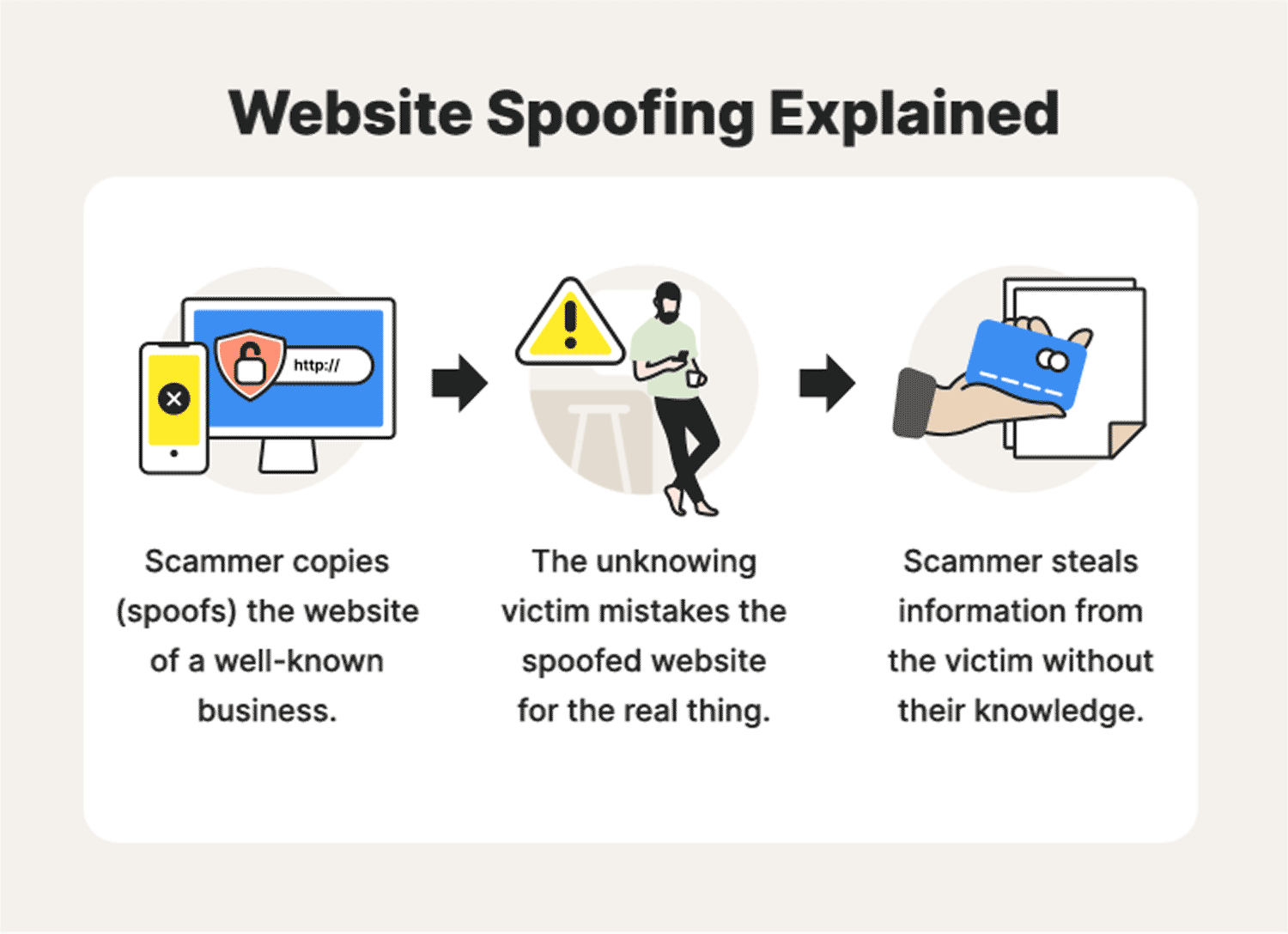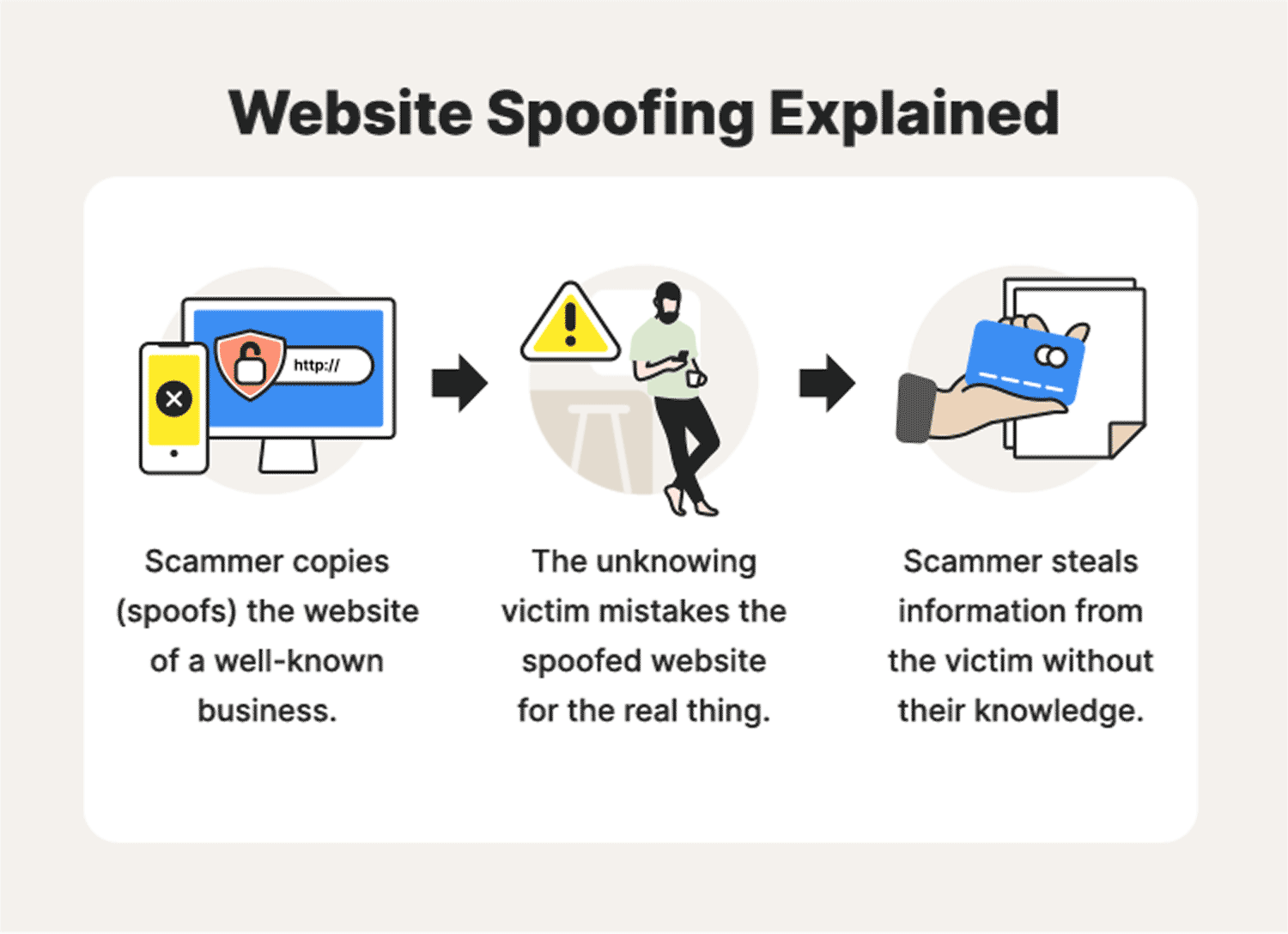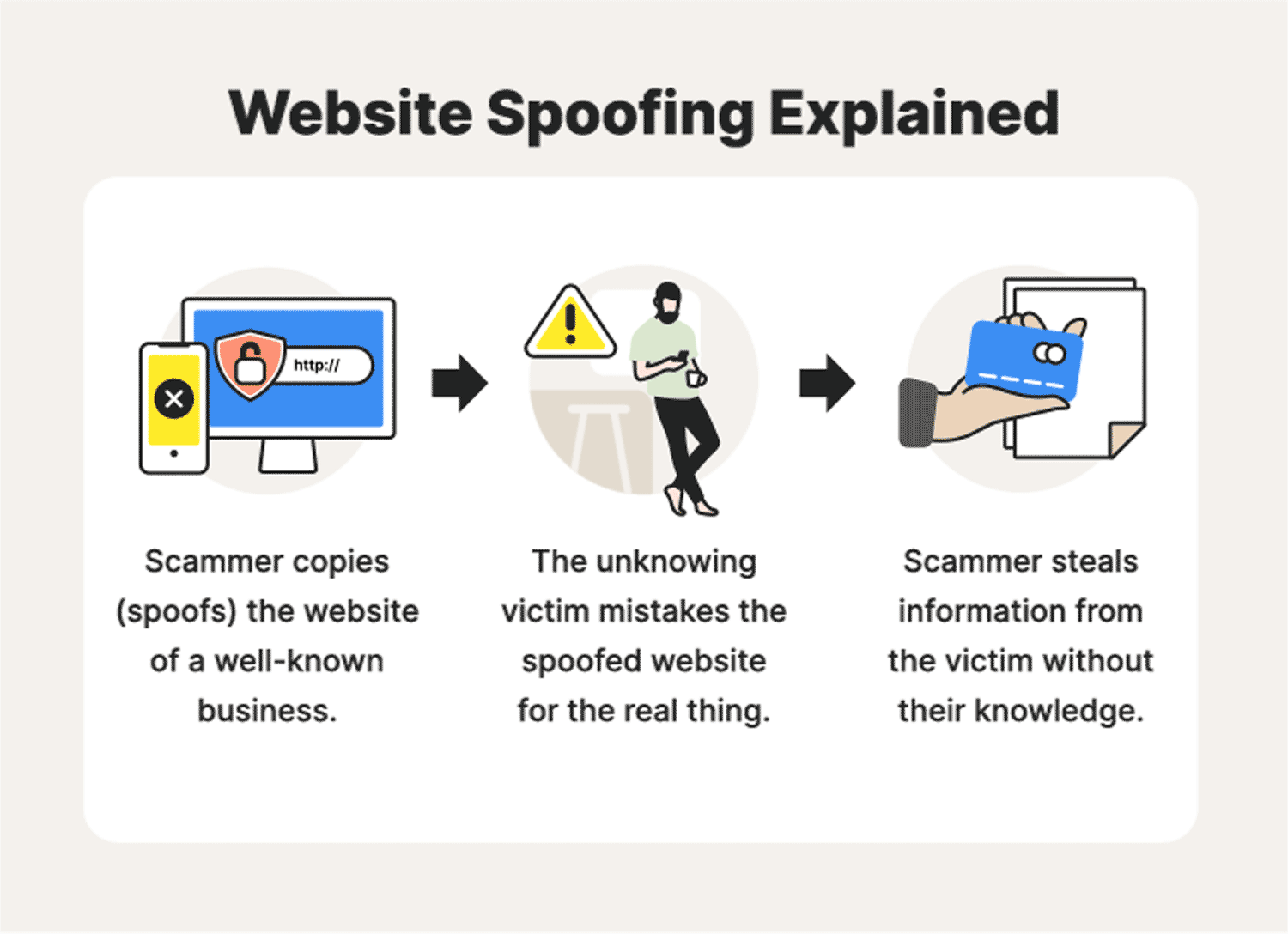
Website spoofing: A definition + how spoofing works

Phishing Statistics 2020 - Latest Report

Must Know Phishing Statistics In 2023 - Attacks And Breaches
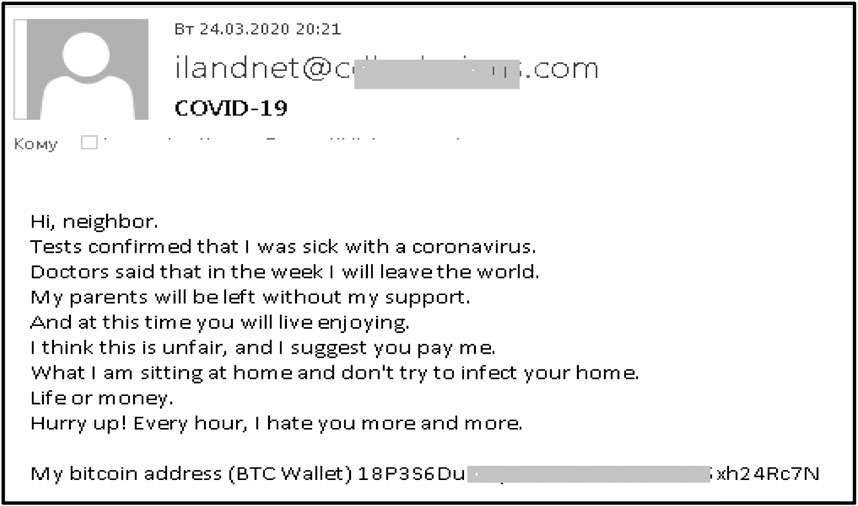
Frontiers Phishing Attacks: A Recent Comprehensive Study and a

How do Phishing and Spoofing Attacks Impact Businesses?

15 Examples of Real Social Engineering Attacks - Updated 2023

Types of Cyber Attacks You Should Be Aware of in 2024

20 types of phishing attacks + phishing examples - Norton
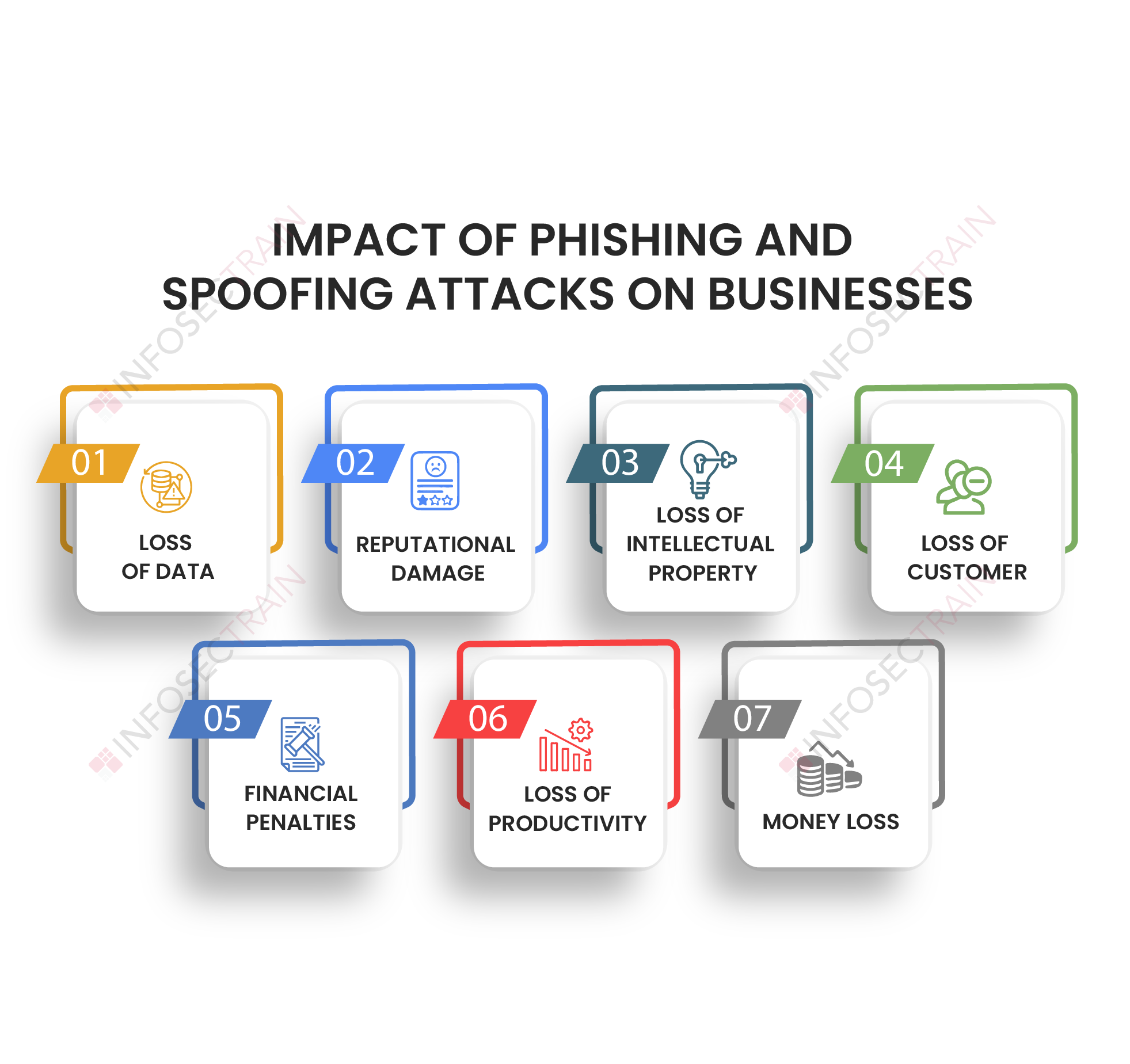
How do Phishing and Spoofing Attacks Impact Businesses?
What is IP Spoofing?

The 5 Most Spoofed Brands in the World
Recomendado para você
-
 Risk Intelligence & Device Fingerprinting Solution11 abril 2025
Risk Intelligence & Device Fingerprinting Solution11 abril 2025 -
 A comprehensive survey on radio frequency (RF) fingerprinting11 abril 2025
A comprehensive survey on radio frequency (RF) fingerprinting11 abril 2025 -
 SimGEN Simulator and PNT Product Improvements - Spirent11 abril 2025
SimGEN Simulator and PNT Product Improvements - Spirent11 abril 2025 -
 Nobody's Fool: Spoofing Detection in a High-Precision Receiver11 abril 2025
Nobody's Fool: Spoofing Detection in a High-Precision Receiver11 abril 2025 -
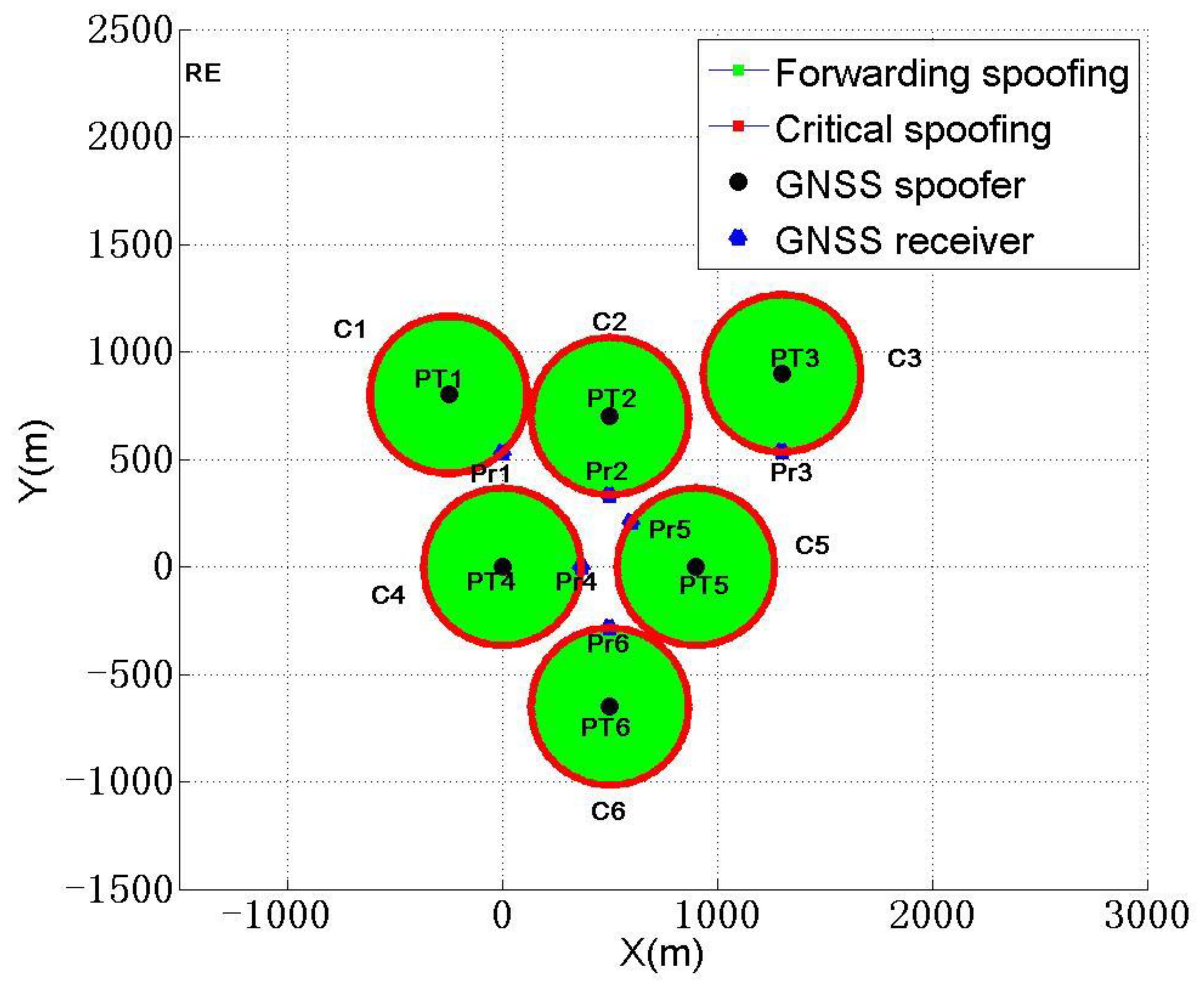 Sensors, Free Full-Text11 abril 2025
Sensors, Free Full-Text11 abril 2025 -
Eulen or redengine? #cheating #eulen #fivem #jus2rich #gaming11 abril 2025
-
 Precision Digital Webinars11 abril 2025
Precision Digital Webinars11 abril 2025 -
 Fortune India: Business News, Strategy, Finance and Corporate Insight11 abril 2025
Fortune India: Business News, Strategy, Finance and Corporate Insight11 abril 2025 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the Rounds11 abril 2025
-
 DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural11 abril 2025
DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural11 abril 2025
você pode gostar
-
 Black Clover Movie Gets Reveals Title, March 31 Premiere in Theaters and Netflix - Anime Corner11 abril 2025
Black Clover Movie Gets Reveals Title, March 31 Premiere in Theaters and Netflix - Anime Corner11 abril 2025 -
 STL file Black Bullet Kagetane Hiruko Mask 👾・3D printer model to11 abril 2025
STL file Black Bullet Kagetane Hiruko Mask 👾・3D printer model to11 abril 2025 -
 Early Ari opener sends Spartak through11 abril 2025
Early Ari opener sends Spartak through11 abril 2025 -
 Toddmomy Adereços De Baile De Tênis De Mesa Coloridos 150 Pçs Tenis Niño Bolas De Tênis Coloridas Bolas De Jogo Adereços Cápsulas Bola De Carnaval11 abril 2025
Toddmomy Adereços De Baile De Tênis De Mesa Coloridos 150 Pçs Tenis Niño Bolas De Tênis Coloridas Bolas De Jogo Adereços Cápsulas Bola De Carnaval11 abril 2025 -
 Download Fierce Baraka in Mortal Kombat Wallpaper11 abril 2025
Download Fierce Baraka in Mortal Kombat Wallpaper11 abril 2025 -
Defensa Siciliana Variante Najdorf Alberik o Kelly La11 abril 2025
-
 Roupas de boneca com estilo misto colorido 3 tamanhos, para boneca barbie, calções de renda, legging, roupas para bonecas barbie, acessórios de boneca11 abril 2025
Roupas de boneca com estilo misto colorido 3 tamanhos, para boneca barbie, calções de renda, legging, roupas para bonecas barbie, acessórios de boneca11 abril 2025 -
 First Harem Anime Club Blossom Daisuke - Anime And Manga - Posters and Art Prints11 abril 2025
First Harem Anime Club Blossom Daisuke - Anime And Manga - Posters and Art Prints11 abril 2025 -
 Hand of the Gods: Touch of Midas by Eksafael on DeviantArt11 abril 2025
Hand of the Gods: Touch of Midas by Eksafael on DeviantArt11 abril 2025 -
 Giros11 abril 2025
Giros11 abril 2025

