Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Por um escritor misterioso
Last updated 11 abril 2025

Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging

Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.

bluejacking

Bluebugging Attack: Definition and Prevention - IDStrong

Bluetooth Attack? bluebugging? bluesnarfing bluejacking? #shorts

What is BlueJacking? - The Security Buddy

Bluebugging: do you know about this Bluetooth security risk?
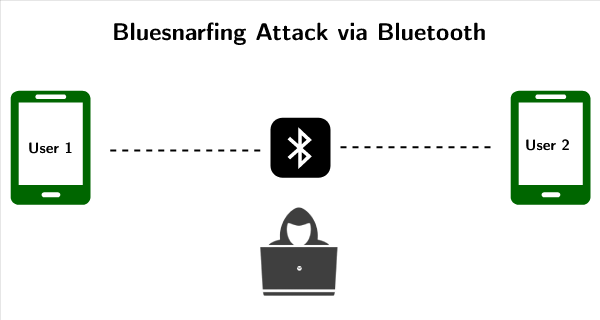
Bluesnarfing Attack in Wireless Networks - GeeksforGeeks

Brief Intro to Hardware Attacks Course

CYBERSECURITY
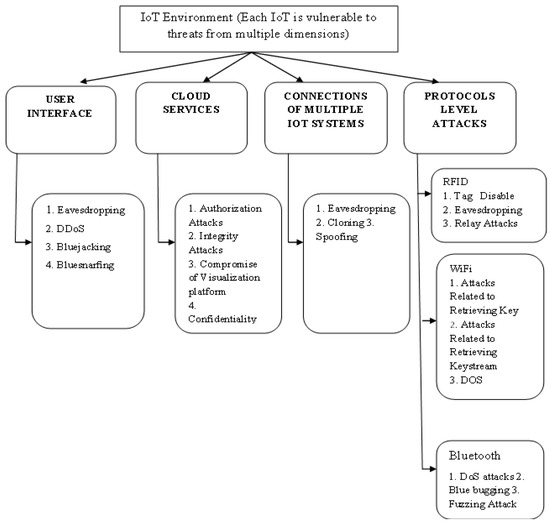
Sensors, Free Full-Text

How Secure is Bluetooth? A Full Guide to Bluetooth Safety
Introduction to How Bluetooth Surveillance Works
Recomendado para você
-
 Hacker Style Launcher - APK Download for Android11 abril 2025
Hacker Style Launcher - APK Download for Android11 abril 2025 -
Contacts Hacker - Prank App - Apps on Google Play11 abril 2025
-
prank · GitHub Topics · GitHub11 abril 2025
-
 CapCut_account hack prank fb11 abril 2025
CapCut_account hack prank fb11 abril 2025 -
 Video Call from Hacker - Fake call with Hacker - Prank Video Call & Voice Call from Hacker · (NO ADS)::Appstore for Android11 abril 2025
Video Call from Hacker - Fake call with Hacker - Prank Video Call & Voice Call from Hacker · (NO ADS)::Appstore for Android11 abril 2025 -
 Help! I Think My Phone's Been Hacked11 abril 2025
Help! I Think My Phone's Been Hacked11 abril 2025 -
 Hack IT - Its Me Spy Network on the App Store11 abril 2025
Hack IT - Its Me Spy Network on the App Store11 abril 2025 -
 Hackers' delight: A history of MIT pranks and hacks11 abril 2025
Hackers' delight: A history of MIT pranks and hacks11 abril 2025 -
 Phone Number Hacker Simulator - Free download and software reviews - CNET Download11 abril 2025
Phone Number Hacker Simulator - Free download and software reviews - CNET Download11 abril 2025 -
 Phone Number Hacker Simulator - Free download and software reviews11 abril 2025
Phone Number Hacker Simulator - Free download and software reviews11 abril 2025
você pode gostar
-
 Episodios BORUTO en Orden Cronológico (SIN Relleno)11 abril 2025
Episodios BORUTO en Orden Cronológico (SIN Relleno)11 abril 2025 -
 Jogo New Super Mario Bros. U Deluxe - Nintendo Switch Nacional11 abril 2025
Jogo New Super Mario Bros. U Deluxe - Nintendo Switch Nacional11 abril 2025 -
 Need for Speed - Xbox One11 abril 2025
Need for Speed - Xbox One11 abril 2025 -
 Toilet for Melon Playground on the App Store11 abril 2025
Toilet for Melon Playground on the App Store11 abril 2025 -
 Dragon Ball Super, Vol. 18, Book by Akira Toriyama, Toyotarou, Official Publisher Page11 abril 2025
Dragon Ball Super, Vol. 18, Book by Akira Toriyama, Toyotarou, Official Publisher Page11 abril 2025 -
 Luxury Custom Chessboard — Conifer Wood Creations11 abril 2025
Luxury Custom Chessboard — Conifer Wood Creations11 abril 2025 -
 Pokémon Ultra Sun & Ultra Moon - Serial Code Events11 abril 2025
Pokémon Ultra Sun & Ultra Moon - Serial Code Events11 abril 2025 -
 20 plantas para cultivar em ambientes fechados - Casa e Jardim11 abril 2025
20 plantas para cultivar em ambientes fechados - Casa e Jardim11 abril 2025 -
 Padrão de beleza e estereótipos inalcançáveis: entenda a11 abril 2025
Padrão de beleza e estereótipos inalcançáveis: entenda a11 abril 2025 -
 SIMULADOR SISU 2024 → Notas de Corte, Cursos, Cálculo11 abril 2025
SIMULADOR SISU 2024 → Notas de Corte, Cursos, Cálculo11 abril 2025